Specific Criticism of CVSS4
Marc Ruef
RFID has come to attention with the introduction of the electronic passport used in many a country. Security concerns are justified but latent. In this article, I want to illustrate the effective dangers of simple RFID tags.
Note: RFID is not internationally standardized. Standards and recommendations vary from country to country and from industry to industry. This leads to variations in functionality and use of RFID technology, depending on the user’s location. Attempts at standardization are made with ISO/IEC 18000: Information technology – Radio frequency identification for item management.
RFID is an abbreviation for Radio Frequency Identification. The technology is being used in order to wirelessly exchange data between a transponder (also known as tag) and a reader. Passive transponders do not have their own dedicated source of energy, but get their energy from the high frequency field that the reader generates. Active transponders have a dedicated energy source and are usually powered by batteries.
Every tag has its unique tag ID that is stored in its read only area. The ID is transmitted in every case in order to identify the transponder. This is the main functionality of RFID. A tag leads to identification in a system. This can be used for personal identification, credit card theft, inventory of goods or access to buildings.
It is noteworthy that RFID tags usually do not contain any data other than the ID. Associating the ID with other data such as a user name happens only when the tag ID is processed further, for example in a SQL database:
SELECT user_id, user_name FROM tbl_user WHERE user_id=$tag_id
Spoofing an identity is therefore dependent on faking the tag ID. Simple authentication systems often use HID Proximity- or EM41XX-Tags.
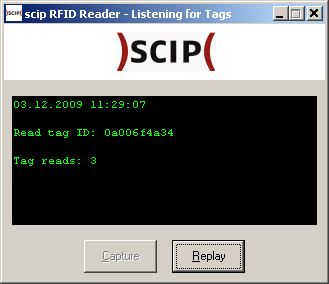
Attacks on these systems are, therefore, rather primitive: If you’re able to simulate a target’s tag ID using a cloned transponder or an emulation, then you can gain elevated privileges in a system and therefore access information you’re not authorized to access. This way, you’re able to fake an identity and gain access to all their privileges. This is called spoofing. Spoofing can happen using interception of communication during a Replay Attack or by using Brute Force methods.
Next to read only transponders, there are those with writable areas. There are two variants: write once and read-write/write-many. In case of the latter, the tag is equipped with memory that can be accessed using additional hardware. The read only area remains in these tags and still can’t be changed.
The information stored in the writable areas of the tag depend on the application. There have been cases of storing user certificates or a passport photo stored remotely.
The issue with read-write areas is that it allows for manipulation. In RFID Viruses and Worms written at the Universiteit Amsterdam, the authors describe a scenario in which the writable area of the tag can be used to distribute a virus.
Up until now, everyone working on RFID technology has tacitly assumed that the mere act of scanning an RFID tag cannot modify back-end software, and certainly not in a malicious way. Unfortunately, they are wrong. In our research, we have discovered that if certain vulnerabilities exist in the RFID software, an RFID tag can be (intentionally) infected with a virus and this virus can infect the backend database used by the RFID software. From there it can be easily spread to other RFID tags.
Problems like this one are older than RFID technology. The writable area of the RFID tag is only used as a carrier. Faulty processing in a program’s backend leads to an attacker gaining elevated rights and therefore the ability to manipulate data he should not have access to. This ability can be used to infect further tags that are processed by the backend. In an example the Dutch researchers use SQL injection to replicate a Quines virus. So basically, it’s a problem of interfacing systems that do not validate input which, in this case, is a data carrier that can be accessed using RFID technology. A similar scenario has been demonstrated using a RFID tag implanted in researcher Mark Gasson’s hand.
RFID unites the general problems of wireless communication – radation, interference and more – and the basic issues of data entry systems such as corrupt entries. Extensive architecture of a high quality system can mitigate these issues. But, as it’s seen in VoIP telephony, the advantages of a cheap solution are being negated to an extent. Finding a compromise between economy and security is paramount when implementing RFID technology.
Our experts will get in contact with you!

Marc Ruef

Marc Ruef

Marc Ruef

Marc Ruef
Our experts will get in contact with you!