Security Testing
Tomaso Vasella

Coming to an end, after stripping and hardening, there is the need to keep the system secure and clean. This may be a difficult task to accomplish, because you may need to to install and use new applications and of course the attack profiles changes over time. Therefore here some hints to help you out in this matter.
Microsoft just released a tool to the public, that was deployed for the internal application audit process, which was needed to be compliant to the Microsoft Security Development Lifecycle. This tools name is Attack Surface Analyzer
Basically this tool will create a snapshot of the system parameters in a known state: for example when you’re done with the OS stripping/hardening. After the first run the tool will start a multiple scan procedure and baseline your system. The system state will be saved in a .cab file and will be used as a reference once you’ll want to compare other systems state, for example after a software installation.
Below is a list of system areas changes & permissions settings that will be baselined (analyzed):
| OS Area | Checked Items |
|---|---|
| System Information | Running Processes, Executables Memory Pages, Windows GUI, Kernel Objects, Impersonation Tokens, Kernel Objects |
| Service Information | Services, Drivers |
| ActiveX, DCOM, COM & File Registrations | Registered ActiveX Controls, Registered DCOM Servers, DCOM Default Permissions, Registered COM Controls, File Registration |
| Internet Explorer | Pluggable Protocol Handlers, Silent Elevation Entries, Preapproved Controls, Browser Helper Objects, Internet Explorer, IE Zones, IE Actions Policy |
| Network Information | Open/Used Ports (TCP/UDP), Named Pipes, RPC Endpoints, Network Shares, Network Interfaces |
| Firewall | Rules, Profiles, Service Restriction Rules & Authorized Application |
| System Environment, Users & Groups | PATH Entries, Accounts, Groups, Group Membership, Account Privileges |
There is a lot to check and to be compared, so don’t worry if it takes some time to execute all those tasks, just remember to stop all processes and programs not needed when you run the first baseline scan… Now just make the test:
You may wonder how much application and tools may change your system state and consequently the attack surface of your system!
Of course you can compare different scan status and (as you may already figure out) you can use this tool for forensics analysis, if you manage to have a clean baseline of the analyzing system.
The Attack Surface Analyzer comes free of charge and supports following OS:
You can run the scan also in command mode to create the baseline files (.cab), but unfortunately you’ll need to have the .NET Framework 4 to compare the baselines and to generate the reports. At best you’ll use a dedicated workstation for the reporting generation task.
Another way to keep your system clean and safe is to provide a known list of application that may run on your machine, this approach is known as Whitelisting. As the words says, only application listed as known (and safe) are able to execute.
It really is a possibility to achieve a very secure operation state but it also need a long tuning session where you define and configure all application needed to run and its required executables. The Application Auditing explained above really helps in this task and is a prerequisite to accomplish successful Whitelisting.
Following are key points for Application Whitelisting:
In Windows you’ll use the Group Policy Editor (GPO) to define and enforce Application Whitelisting.
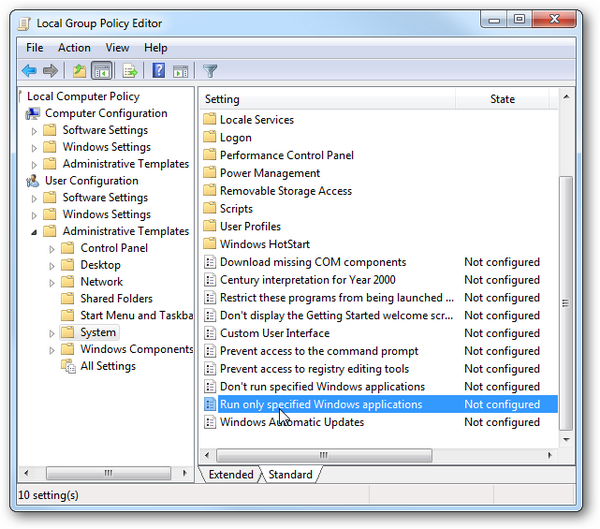
We just scratched the surface of the possibilities with Application Whitelisting, more on this item may be discussed in dedicated Lab article.
In this article we covered the security procedure on keeping a hardened system secure over time. Now this series has reached the end, but stay tuned for future labs articles.
Our experts will get in contact with you!

Tomaso Vasella

Eric Maurer

Marius Elmiger

Eric Maurer
Our experts will get in contact with you!