Security Testing
Tomaso Vasella

![]()
Microsoft has developed several tools that help security professionals in the difficult task to keep Windows operating systems safe, like the Microsoft Baseline Security Analyzer (MBSA) or the Security Compliance Manager (SCM). This time we like to give an overview of another interesting piece of windows security software: the Enhanced Mitigation Experience Toolkit (EMET).
EMET is an utility to help protect the Windows operating system platforms against exploitation of vulnerabilities through a series of security mitigation technologies. As any other security tools, EMET does not replace other information security solutions; it is meant to add an additional layer of defence in the existing security framework.
While it may not prevent all possible security exploits, the mitigation technologies implemented by EMET make exploitation significantly more difficult if configured properly.
EMET supports client and server based operating system. The current version (4.0 beta) allows security mitigation technologies to be configured for the system and applications. Mitigations applied to the system will impact the entire system while mitigations applied to the applications will only impact the specified applications. This provides following key benefits:
Further, following are the most interesting new features in EMET 4.0:
Below is a table listing the used mitigation technologies:
| Area | Technology | Description |
|---|---|---|
| SYSTEM / APPLICATION | Data Execution Prevention | The DEP mitigation is a memory protection mitigation that marks the stack and heap for a process as non-executable. Attempting to execute malicious code from these regions will be denied at the processor level |
| SYSTEM / APPLICATION | Structured Exception Handler Overwrite Protection | The SEHOP mitigation protects against currently the most common technique for exploiting stack overflows in Windows |
| SYSTEM | Address Space Layout Randomization | ASLR randomizes the addresses where modules are loaded to help prevent an attacker from leveraging data being loaded at predictable locations in memory. Exploits relying on data at fixed addresses will fail |
| APPLICATION | Null Page pre-allocation | The NullPage mitigation is designed to prevent potential null dereference issues in user mode. Currently there are no known ways to exploit them and thus this is a defence in depth mitigation technology |
| APPLICATION | Common heap spray address pre-allocation | The HeapSpray mitigation is designed to pre-allocate common memory addresses in an attempt to block heap spraying attacks. Please note that it only aims to break current exploit that take advantage of common addresses |
| APPLICATION | Export Address Table Access Filtering | The EAF mitigation blocks the most common approach used by exploits to look up the location of a function (exposed by Windows) which involves scanning the export address table of loaded libraries. It is highly effective at blocking exploits currently being used |
| APPLICATION | Mandatory Address Space Layout Randomization | The MandatoryASLR mitigation forces all modules to be loaded at randomized addresses regardless of what flags they were compiled with. Exploits relying on data at fixed addresses will fail |
| APPLICATION | Bottom-Up virtual memory randomization | The BottomUpASLR mitigation randomizes (8 bits of entropy) the base address of bottom-up allocations (including heaps, stacks, and other memory allocations) |
| APPLICATION | Loadlibrary | Checks LoadLibrary calls to load library and prevents loading libraries from UNC path (i.e. \\evilsite\bad.dll) |
| APPLICATION | Memory Protection Checks | Disallows making the stack area executable. Such activity is usually used by shellcode or ROP gadgets |
| APPLICATION | Caller Checks | Makes sure that when a critical function is reached, it is reached via a call instruction rather than a RET. This is a very useful mitigation and breaks many ROP gadgets. This mitigation may be incompatible with some programs. Internet Explorer on a fresh Windows Installation works fine with this mitigation |
| APPLICATION | Stack Pivot | Tries to detect ROP gadgets following a call to a critical function. Like the Caller checks, this feature may not be compatible with all programs |
| APPLICATION | Simulate Execution Flow | This mitigation is used to detect if the stack has been pivoted. It is compatible with most programs. |
For more information please refer to the well written EMET 4.0 user manual available via Help menu on the EMET GUI.
Not all mitigation option are supported on all operating systems and application, but Microsoft is continuously improving the software and providing support for all important platforms and application executables.
Here a short overview on supported features on platform and executables:
| Area | Mitigation | XP | W2003 | Vista | W2008 | Win7 | W2008 R2 | Win8 | W2012 |
|---|---|---|---|---|---|---|---|---|---|
| SYS | DEP | OK | OK | OK | OK | OK | OK | OK | OK |
| SYS | SEHOP | – | – | OK | OK | OK | OK | OK | OK |
| SYS | ASLR | – | – | OK | OK | OK | OK | OK | OK |
| APP | DEP | OK | OK | OK | OK | OK | OK | OK | OK |
| APP | SEHOP | OK | OK | OK | OK | OK | OK | OK | OK |
| APP | NULL page | OK | OK | OK | OK | OK | OK | OK | OK |
| APP | HEAP Spray | OK | OK | OK | OK | OK | OK | OK | OK |
| APP | mASLR | – | – | OK | OK | OK | OK | OK | OK |
| APP | EAF | OK | OK | OK | OK | OK | OK | OK | OK |
| APP | LoadLibrary | OK | OK | OK | OK | OK | OK | OK | OK |
| APP | Mem Protection | OK | OK | OK | OK | OK | OK | OK | OK |
| APP | Bottom-up | OK | OK | OK | OK | OK | OK | OK | OK |
| APP | SimExecFlow | OK | OK | OK | OK | OK | OK | OK | OK |
Another limitation is bound to the web Certificate Trust, it works only with following browsers:
Unsupported are by now following versions:
EMET is not a fire and forget toolkit, it requires you to carefully configure the policy and thoroughly test it before it can be used for production environment; also EMET is not an end-user tool like an anti-virus.
After the installation (that requires .NET Framework 4 and eventually a restart) you can begin using EMET by starting its GUI. It will the show something like this:
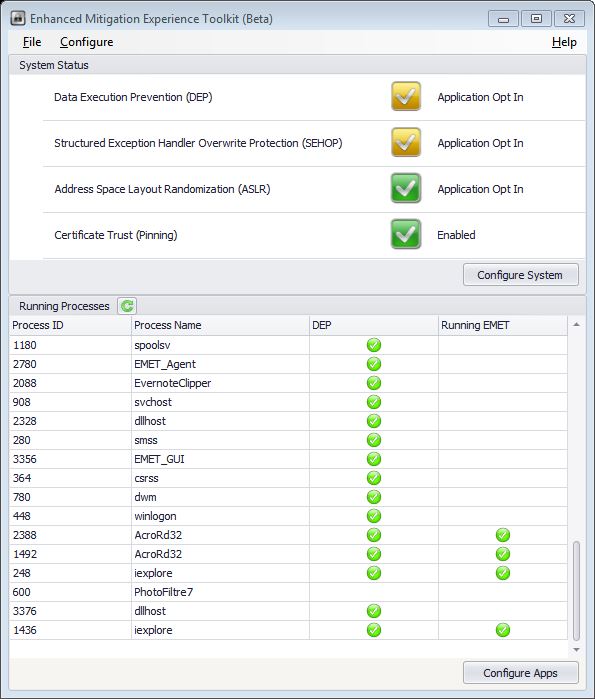
In the first window half you’ll see the available system features and its related status: Enabled, Application Opt-In, Application Opt-Out or Disabled; in the second half the are the systems running processes and related active mitigation features. The system mitigation settings are configurable via this panel:
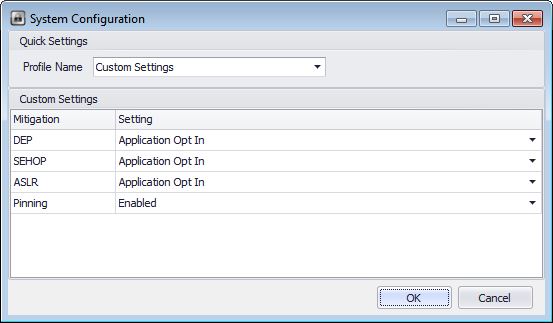
The application mitigation settings are configurable on this other panel:
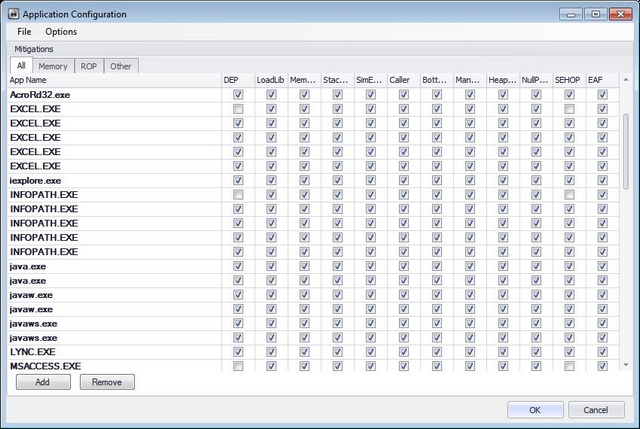
To add an application specific mitigation settings just push to the add button or right-click in the list of running processes, you’ll then be able to select the mitigation settings checkbox.
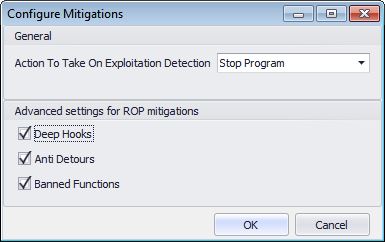
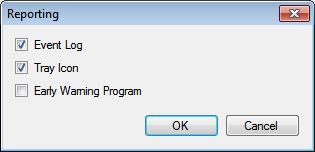
All action are written into the Windows application log and reported by the tray icon so if you need to analyze what happens you can filter for EMET log source there; this is important if you are running in audit mode and don’t kill processes that are violating the policy. By default processes are killed here are the configuration settings:
EMET 4 provides a crypto extension module that will add additional checks during the certificate chain trust validation process. When browsing to an HTTPS website, EMET will validate the end-entity SSL certificate and the Root CA that issued that certificate against the rule configured.
Depending on the rules configured for a specific domain, EMET will detect when a variation of the issuing Root CA for a specific SSL certificate occurs. In this case EMET will only detect the anomaly, but the connection will not be stopped. Exceptions can be also configured on some properties of the Root CA certificate, such as key size, hashing algorithm, and issuer country. For example you can rise a warning if the certificate key length is lower that 2048 bit.
As a short test we can define a pinning policy that has following settings in CONFIGURE/CERTIFICATE TRUST/PINNING RULES/ADD:
TRUSTED.SSL2048N/AMD2,MD4,MD5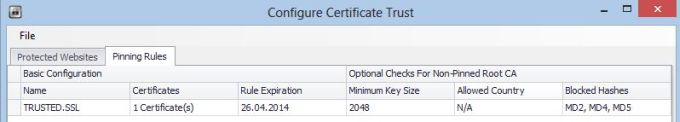
Now go to Protected Web Site tab and add a site to test:
www.google.comTRUSTED.SSLActive checkbox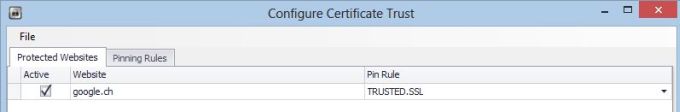
Well, this will ensure that Man in the middle attacks will generate an EMET agent warning message. Now if you like to test it just change a parameter in the pinning rule, like the key length from 2048 to 4096 or just change the Trusted Root CA.
After the changes try to access the site again and a message like this should pup up:
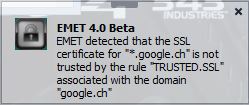
And the following entry inside the application log:
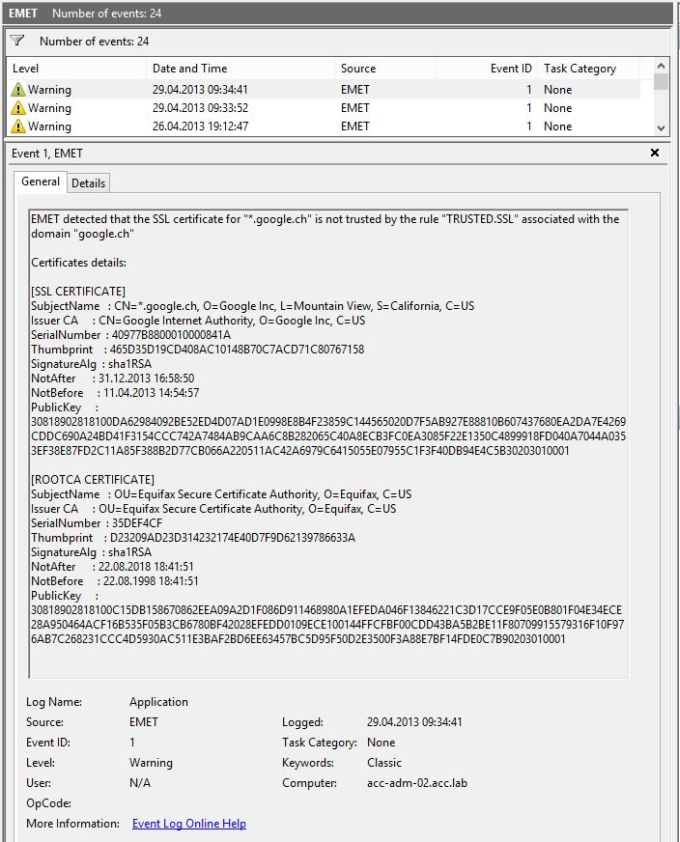
EMET is a powerful toolkit but need to be well configured and tested before going to production. Security on this level is pretty much the last layer of defense. We would recommend to use EMET to finalize your security strategy on very critical components like:
| Area | Component |
|---|---|
| Enduser Workstations | Internet Bowsers |
| Internet Services / Gateways | Web Servers and Email Gateways |
| Critical internal services | Domain Controllers, DNS servers, Exchange Servers |
Invest time to create a policy that fits the specific machine usage; don’t try to. Once it’s done, you’ll get a very useful toolkit against Malware… and all for free!!
Our experts will get in contact with you!

Tomaso Vasella

Eric Maurer

Marius Elmiger

Eric Maurer
Our experts will get in contact with you!