Security Testing
Tomaso Vasella


Has it already been a year? Apparently, because two weeks ago I found myself in the middle of the Nevada desert once more to attend what has recently has been affectionaltely named Hacker Summer Camp the week when Black Hat, BSides Las Vegas and DEFCON happen back to back and most mailing lists get oddly silent because almost everyone is out in Vegas anyway. And as in previous years (for example 2012 – Part 1, Part 2 and 2011), I had the pleasure of attending myself, too.

The original Security BSides is still going strong and is, one might argue, probably the most original and innovative conference happening in this packed week. I skipped the annual madness last year and with it, I missed the move BSides made from the Artisan to the Tuscany, but I think that the move helped the event a lot when it comes to coping with the massive amount of people wanting to attend. While no official numbers have been published to date, there were probably about 1500 people in attendance – a massive feat for a conference that charges attendees an exact amount of zero dollars for a ticket and finances itself completely with the help of sponsors and donations without degenerating into a sales event. In fact, BSides – again – managed to offer a variety of highly sophisticated technical talks on many topics.
Before I give a couple of examples to illustrate the content presented at BSides, let me point out that all the videos are already available online should you wish to catch up. I can only compliment Adrian Irongeek Crenshaw on his professional dealing with the video and the quick uploads.
That being said, I really enjoyed Meredith L. Patterson’s talk Strategies Without Frontiers that essentially deals with game theory in terms of threat modelling.
Another talk that I enjoyed, primarily due to my own affinity for travelling comfortably while not spending an absurd amount of money, is TProphet’s talk Travel Hacking With The Telecom Informer. As the title implies, it’s not strictly related to information security, but it illustrates nicely that hacking is not necessarily to be considered something that has to do with computers.
If you prefer more specific information security content, you might enjoy this talk on ATM Malware by Daniel Regalado.
These are only a couple of examples to illustrate the fantastic content available to BSidesLV this year. Apart from a select few, all talks were posted. One of them is the infamous closing ceremony with a surprise appearance by John McAfee, mostly known for his recent escapades including a wide variety and large quantity of drugs.
Again, while I didn’t get to spend as much time at BSides as I’d have liked to, I can only compliment Banasidhe and her entire team on all their hard work and the results they achieved. And, of course, all the compliments that they deserved.

Partially coinciding with BSidesLV, the titan of security conferences, Black Hat USA happened for the first time in one of my favorite venues in Las Vegas, the Mandalay Bay, probably because the event outgrew Caesar’s Palace or just wanted something a bit more modern. Black Hat is always a bit tricky. On one side, the conference has a solid reputation for bringing out some of the best researchers and giving them all the limelight they can to present important findings to the InfoSec industry and the general public. On the other side, Black Hat has a very corporate feel to it that seems to deter a steadily increasing amount of the hardcore security folks.

That being said, Black Hat did feature some very profound and interesting talks, including Dan Geer’s keynote titled Cybersecurity as Realpolitik. The transcript of the talk can be found here and it’s an interesting read, since one Geer’s key points suggested that the US government should buy all available vulnerabilities, at ten times the price every other interested party would offer. He suggests this because it would be an extra incentive for people to get into the field and it would lead to very high transparency, because he suggests that all vulnerabilities should also be published. This would also devalue vulnerabilities and increase willingness to disclose them. It’s a radical suggestion that became a fertile grounds for a lot of discussion, including this elaborate answer by Bill Blunden.
In a less controversial talk, Nils and Jon Butler discussed the potential flaws of Mobile Point-of-Sale (mPOS) systems, featuring some pretty cool proof-of-concepts. The video of talk, as embedded below, is one of the few already available online for free and I’d recommend checking out the list on Black Hat’s official channel.
Another tradition that has established itself in the past couple of years at Black Hat are the Pwnie Awards. They’re a tongue-in-cheek award that seeks to recognize the feats the industry has accomplished this past year and it’s handed out for several categories. While not of giant educational value, it’s usually good for a couple of laughs, so I would not want to keep this information from our readers. First, here are the winners for best bugs and research:
On a more humorous note, AVG managed to win the award for “Lamest Vendor Response” by spectacularly claiming that various vulnerabilities identified by a third party are in fact by design.
| Date | Event |
|---|---|
| 2014-01-15 | Contacting AVG via online support form and requesting security contact. |
| 2014-01-15 | Support forwards us to “Jürgen Jakob Software-Entwicklung, AVG Authorized Distributor” (sales representative!) |
| 2014-01-21 | AVG support requests technical information. |
| 2014-01-22 | Requesting contact to discuss security issues. |
| 2014-01-29 | Requesting contact to discuss security issues (2nd try). |
| 2014-02-10 | Requesting contact to discuss security issues (3rd try). |
| 2014-02-12 | AVG support explains lack of response because they were “experiencing a higher than usual volume of e-mail messages from customers” and requests technical information. |
| 2014-02-24 | Requesting encryption keys (S/MIME or PGP). |
| 2014-03-05 | Requesting encryption keys (2nd try). Announcing that advisory will be sent via plaintext if no keys are provided. |
| 2014-03-11 | (No response) Sending security advisory and responsible disclosure policy as plaintext. Setting deadline to 2014-04-30. |
| 2014-03-11 | Opening a new ticket – referring to previous ticket, advisory and proof of concept exploits. |
| 2014-03-31 | (No response) Contacting AVG CTO via LinkedIn, referring to previous tickets and requesting encryption key. |
| 2014-03-31 | CTO responds, provides encryption key. |
| 2014-03-31 | Sending advisory and responsible disclosure via encrypted channel. |
| 2014-04-04 | CTO responds with AVG risk assessment: #1 low risk “This is by design” #1 low risk “This is by design” #2 high risk #3 medium risk “This attack is difficult to set up” #4 low risk “The cipher is used here just for the obfuscation of the traffic, it was not meant to protect any private data” CTO further mentions that Remote Administration is “no longer available for sale for new customers” – this was never substantiated! Even the FAQ on the website says differently: Even the FAQ on the website says differently: http://www.avg.com/us-en/faq.num-5125 |
| 2014-04-25 | Shifting release deadline to 2014-05-08. |
| 2014-04-28 | CTO responds, announcing that patch for remote code execution (issue #2) will be released on 2014-04-29. |
| 2014-05-06 | Requesting confirmation that only remote code execution will be fixed. |
| 2014-05-06 | CTO confirms that only remote code execution is fixed. |
| 2014-05-08 | SEC Consult releases security advisory & proof of concept videos. |
The remaining awards in short form:

Last but not least, running for its 22nd year, DEFCON happened. Defying rumours claiming for it to be definitely and undeniably cancelled, the event happened at the Rio Convention center as it did in previous years. It is a significant problem to try and describe DEFCON in a couple of written sentences since there is so much to see, do and learn usually. For a general impression, I wholeheartedly recommend the DEFCON 20 documentary:
There is so much going on at DEFCON, it’s hard to point out specific points without missing out on a lot of others at the same time. But for example, the Blackphone, according to its vendor being the “the world’s first smartphone to put privacy and control ahead of everything else”, got rooted within five minutes because the application in charge for remote wipe had debugging enabled, so attaching a debugger would give a potentially unauthenticated user an instant system shell.
Another entertaining side-story happening at DEFCON was a person using the pseudonym ihuntpineapples to pursue people using Hak5’s WiFi Pineapple. The device used to launch attacks using wireless networks was sold at the event and people trying to set it up on location experienced an instant surprise:
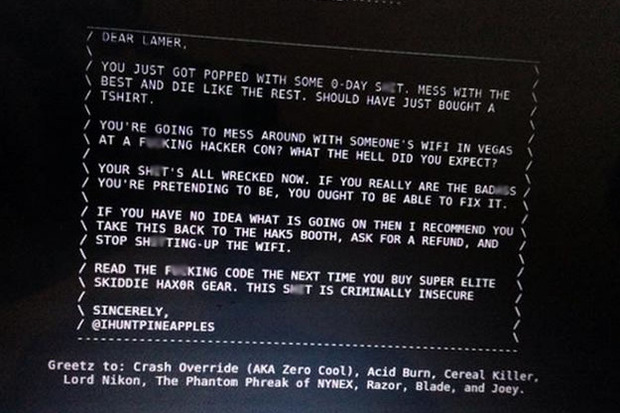
Apparently, someone tried to teach people a lesson by using a 0day vulnerability on the device to compromise them when used at the local DEFCON network. To be fair, using any sort of non-hardened device (or any device at all, frankly) in the DEFCON network is usually a bad idea, but this got viral really quickly and became an amusing topic of discussion throughout the con, causing Hak5 to issue multiple firmware updates mitigating the vulnerabilities used to conduct the attack.
As DEFCON came to a close on Sunday, TheDarkTangent announced that this will be the last event to happen at the Rio. The 2015 DEFCON will happen in the Paris and in the Harrah’s, which should make for an interesting experience. Not only is this going to be the largest DEFCON to date, but it’s also going to be right in the middle of the strip, potentially causing a considerable lot more mayhem than at the slightly off-strip Rio.
That being said, we settle back into our normal everyday life, where you can actually use a WLAN with only a slight possibility of being viciously attacked. It’s pretty relaxing. But we will probably be back anyway.
Our experts will get in contact with you!

Tomaso Vasella

Eric Maurer

Marius Elmiger

Eric Maurer
Our experts will get in contact with you!