Privileged Identity Management (PIM) is a domain of Identity Management. It focuses on the particular requirements of privileged accounts in the IT environment of a company. Among them are admin, root and super-user. PIM is also referred to as an information security and governance instrument in order to support companies to fulfil legal and regulatory compliance requirements (such as FINMA in Switzerland, PCI-DSS and so on). In addition to that, PIM helps to hinder attackers from using privileged accounts in order to misuse internal data. And if that doesn’t work, then PIM should at least help to detect and document the misuse.
Typical regulations for handling privileged identities and users as well as accounts are, depending on the branch you work in, stated in specific standards and regulation documents as well as laws. The list at the end of this article serves as a basic list of what could be important for your environment when it comes to laws.
Terminology
Vendors talk about these products using various terms. Subsequently, there is a lot of confusion when it comes to PIM. These days, the term P x M has established itself, whereas x is often used as a placeholder for Access, User, Account, Identity or Password.
- Privileged Access Management
- Privileged User Management
- Privileged Account Management
- Privileged Identity Management
- Privileged Password Management
A subset of PIM is Privileged Account Management which is what we’ll talk about in this article.
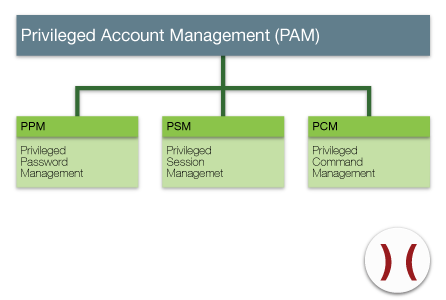
- Privileged Password Management (PPM) enables secure and encrypted saving and control over changes to privileged passwords in a heterogenous environment of systems and applications. A privileged password management replaces embedded passwords that are coded into scripts, processes and programs.
- Privileged Session Management (PSM) offers control, surveillance and recording of sessions of high risk users, including administrators and remote support services.
- Who checked in or out? Username/ID
- Which role was requests and used? Audit Trail
- What did the user do? Session Recording
- When did the privileged ID check in and out? Timestamps
- Which application or system was used by the privileged ID?
- Where was the check out requested from? IP address
- Other factors
- Privileged Command Management (PCM) enables you to delegate granularly. This applies to programs, tasks and commands across several platforms. It creates command controls that enable the delegation of privileges.
Privileged access and the control of the administrator account is a permanent field of interest and a constant source of worry in a company. Constantly rising requirements in terms of compliance require even more attention to this. They demand that companies force measures that protect, manage and control critical accounts and passwords.
Unmonitored root, admin and superuser accounts as well as other privileged accounts can lead to loss or theft of sensitive company data. And these accounts can be used to get malware into the system that compromise security. Increasingly tight laws and regulations require the aggregation of data and event management information. This requires the ability to identify and elimination of internal threats that can appear with the use of privileged accounts.
This means that companies have to be able to provide privileged access on request using a least privileges and need to know basis. This in turn requires a basis of specific roles. Generally, access should only be given to necessary systems for a predetermined amount of time.
The optimal approach to PAM solutions has accountability and granular access control at its core.
- Traceability
- Accountability
- Granular access
This creates a framework of least privileges. Administrators only gain access to necessary tools. And only by request and only when they need said access.
This requires checks and balances:
- Encrypted password vault
- Command control
- Granular delegation
- Extensive protocolling including session recording
This process requires some steps as a preset before a PAM tool can be considered:
- There needs to be a policy. It specifies how privileged accounts are managed and what the owners are permitted to do
- The development and integration in a security management framework. The frameworks defines people responsible for keeping in line with the policy
- Systematic and consequent inventory of privileged accounts. This gives overview over:
- Accounts
- Roles
- Groups
- Functions
- Persons
- Use tools suitable to management and implement sensible and pragmatic processes that are based on everyday practises.
This way a company can better protect their data and systems from privileged access and avoid security breaches. Failing that, the breaches are at least identified and comprehensibly documented. In addition to that, the rising requirements can be met.
This is a rough summary of PAM. It is a combination of:
- Processes
- Methods
- Technologies
This takes care of Audit Trail and Session Recording when privileged users access a system on the basis of least privileges. In short: PAM can reestablish control over an un-culture of privileged access.
This un-culture has quite some risks:
- Total loss of accountability due to lack of monitoring and control of privileged access
- Too many workers and administrators with limited responsibilities gain access to
admin, superuser and root accounts. They have unnecessary access to functions that they don’t need - Lack of control of privileged passwords that are often shared insecurely.
- Failure to detect data leaks. Especially those concerning sensitive data and critical systems
- Introduction of malware into critical infrastructure
- Sabotage
A sensibly implemented PAM system can be a means to lessen the risk or to even eliminate it. It does this by paying attention to the following points:
- Specific rights for administrators
- Based on roles
- Delegated based on role
- Providing a policy engine that rules access
- Complete Audit recording ensuring
- Details of access
- Performed activities
Overview Main Functions
In a PAM, the following core functionalities need to be considered:
- Password vault
- Centrally stored
- Secure
- Encrypted
- Limiting access
- Controlling
- Monitoring
- Ability to follow all activity by privileged users
- Privileged account access control
- Ability to follow all activity by shared users. Attributes for generic shared accounts:
- Personalisation
- Securing
- Tracking of use
- Control of dual or multi release
- Workflow with requestor and approver
- Privilege Elevation
- On-demand Privileges
- Role based access on demand to shared and privileged accounts
- Automated password reset
- Automated password change based on time and last use
- Synchronised password changes
- Shared accounts
- Between database and application
- Generation of strong passwords
- Enforcing of guidelines and rules for passwords with defined criteria
- Length
- Strength
- Uniqueness
- Frequency of Change
- Support of multi factor authentication (transparent login for shared accounts and strong authentication for privileged accounts that only offer single-factor username/password logins by default)
- Protects against application-to-application access misuse
- Access regulated on application level
- Ability to follow all activity of individual users
- Logging of all activity by root and administrator accounts
- Recording of remote sessions, including keyboard entries, mouse movement and all changes on screen (session recording)
- Session proxy: No direct connection to back end server, accounts and applications
- Clientless secure an encrypted communication
- Encryption both at rest and in transit
- Vendor and support accounts as well as other critical external accounts
- Surveillance
- Commanding
- Limiting
This is how privileged password management and privileged session management works:
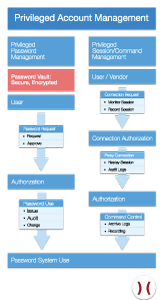
Context of functions and users in connection with a PAM system. Here’s how accounts in a PAM environment can be structured:
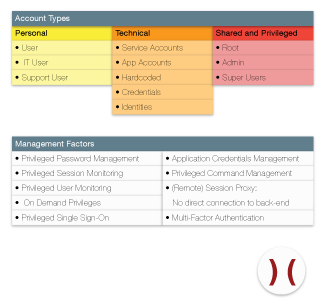
PAM Technology has to adapt to the needs of the privileged account. This include:
- Availability
- Life cycle management
- Authentication
- Password management
- Surveillance
- Access control
A Note Concerning Session Recording
Session Recording has found its way into many companies. It is popular in the frame of PAM solutions. However, session recording brings its own share of problems that are often ignored which is why I want to mention them specifically. Because the trend to record sessions extensively can have its disadvantages:
- Disinformation by Data Quantity: There is no guarantee that the people responsible will be able to filter unnecessary information within reasonable amounts of time when session recording is being used extensively. Also, effort in connection with storage and backup as well as archiving is often underestimated.
There is a significant risk of disinformation by the exponential growth of amounts of data as well as a steadily rising use of storage. Costs and use can exceed the use of the recorded data. The affinity for classic system logging can be used to find the relevant data in records
- Surveillance Culture, Data Protection Law and Sensibility: The question if and how data records can be used in a court of law is a question that is a constant debate and is rarely being accounted for in IT departments of companies. It is important, though, to educate workers and inform them properly. A message upon login should alert users that admin sessions are being recorded. Because session recording is quite invasive it is advisable to educate and sensitise users. Experience has shown that recording measures like these are often seen as a threat or a deterrent or as a proof of mistrust.
Summary
There’s rising pressure in daily practice to log who did what when and why precisely and succinctly. This is even more of a pressing issue when it comes to privileged accounts. Add to that the rising requirements regarding revision safety of IT activity as well as the current laws and regulatory requirements such as FINMA, PCI-DSS et cetera. It is not enough to deploy a technical solution without systematically and specifically plan internal and external requirements. Validating primary drivers needs to be enforced before deployment of a PAM framework. As usual, the technology the PAM is based on needs to be taken into account. But even more important is the proper implementation of processes to control a PAM solution. Do not underestimate the initial effort.
Annex
- ISO27002:
- A.15.1 Compliance with legal requirements
- A.15.1.3 Protection of organizational records
- A.15.1.4 Data protection and privacy of personal information
- A.15.1.5 Prevention of misuse of information processing facilities
- A.15.3.2 Protection of information systems audit tools
- A.7.1.2 Ownership of assets
- A.7.1.3 Acceptable use of assets
- A.7.2.2 Information labeling and handling
- A.8.3.3 Removal of access rights
- A.10.10 Monitoring
- A.10.10.2 Monitoring System Use
- A.10.10.3 Protection of log information
- A.10.10.4 Administrator and operator logs
- A.10.1.3 Segregation of duties
- A.11.2.2 Privilege management
- A.11.2.4 Review of user access rights
- A.13.2 Management of information security incidents and improvements
- COBIT:
- Management of user accounts
- Management of user identities and logical access
- OR728a / OR729a:
- Requirement to assess risks and the implementation of an internal controlling system
- DSG
- Art.4: Basics, legality, adequacy
- Good Faith, Binding to purpose
- Art.5: Correctness
- Art.7: Data security
- FINMA
- Circular 2008/10: Self-regulation as a minimum standard
- Circular 2008/21: Operational risks at banks
- Circular 2008/24: Supervision and internal control – banks
- PCI
- Especially PCI-DSS requirement 8: Identify access to system components and authentication
- Decrees, among other things, that every person with system access must have a unique ID. Demands that no account and no password can be used by a group or even more than one person at a time. This secures that each user is identifiable. The goal of this is that all activity connected to critical data or systems will only be performed by authenticated personell.
- Also takes into account management of external service providers that use remote access. These have to be monitored as well and they are to be active only as long as they’re needed. Adding to that is the requirement that service providers with remote access have to use unique information of authentication.
About the Author
Flavio Gerbino has been in information security since the late 1990s. His main areas of expertise in cybersecurity are the organizational and conceptual security of a company.
Links




