Security Testing
Tomaso Vasella

In Part One we’ve started our appliance configuration for an out of band remote support and covered the system and cellular module install and configuration. Now we need to make sure that the appliance will be able to connect automatically to our access (VPN) server and fine-tuning the other security related features. Therefore let’s configure the VPN framework.
The appliance should be able to boot and automatically access (via mobile provider) the Internet via the wwan0 interface by now. Now it’s time to configure our secure tunnel connection. We want our APU box to get Internet access after boot and automatically start an encrypted tunnel to our VPN server. We’ll use OpenVPN client, let’s install it using the apt-get command:
root@bluebrick:~# apt-get install openvpn Reading package lists... Done Building dependency tree Reading state information... Done The following extra packages will be installed: easy-rsa liblzo2-2 libpkcs11-helper1 opensc opensc-pkcs11 openssl Suggested packages: ca-certificates resolvconf The following NEW packages will be installed: easy-rsa liblzo2-2 libpkcs11-helper1 opensc opensc-pkcs11 openssl openvpn 0 upgraded, 7 newly installed, 0 to remove and 0 not upgraded. Need to get 2,177 kB of archives. After this operation, 5,788 kB of additional disk space will be used. Get:1 http://http.debian.net/debian/ jessie/main liblzo2-2 amd64 2.08-1.2 [54.6 kB] Get:2 http://http.debian.net/debian/ jessie/main libpkcs11-helper1 amd64 1.11-2 [45.4 kB] Get:3 http://http.debian.net/debian/ jessie/main opensc-pkcs11 amd64 0.14.0-2 [687 kB] Get:4 http://http.debian.net/debian/ jessie/main openssl amd64 1.0.1k-3 [677 kB] Get:5 http://http.debian.net/debian/ jessie/main easy-rsa all 2.2.2-1 [17.1 kB] Get:6 http://http.debian.net/debian/ jessie/main openvpn amd64 2.3.4-5 [477 kB] Get:7 http://http.debian.net/debian/ jessie/main opensc amd64 0.14.0-2 [219 kB] Fetched 2,177 kB in 4s (435 kB/s) Preconfiguring packages ... Selecting previously unselected package liblzo2-2:amd64. (Reading database ... 18953 files and directories currently installed.) Preparing to unpack .../liblzo2-2_2.08-1.2_amd64.deb ... Unpacking liblzo2-2:amd64 (2.08-1.2) ... Selecting previously unselected package libpkcs11-helper1:amd64. Preparing to unpack .../libpkcs11-helper1_1.11-2_amd64.deb ... Unpacking libpkcs11-helper1:amd64 (1.11-2) ... Selecting previously unselected package opensc-pkcs11:amd64. Preparing to unpack .../opensc-pkcs11_0.14.0-2_amd64.deb ... Unpacking opensc-pkcs11:amd64 (0.14.0-2) ... Selecting previously unselected package openssl. Preparing to unpack .../openssl_1.0.1k-3_amd64.deb ... Unpacking openssl (1.0.1k-3) ... Selecting previously unselected package openvpn. Preparing to unpack .../openvpn_2.3.4-5_amd64.deb ... Unpacking openvpn (2.3.4-5) ... Selecting previously unselected package easy-rsa. Preparing to unpack .../easy-rsa_2.2.2-1_all.deb ... Unpacking easy-rsa (2.2.2-1) ... Selecting previously unselected package opensc. Preparing to unpack .../opensc_0.14.0-2_amd64.deb ... Unpacking opensc (0.14.0-2) ... Processing triggers for man-db (2.7.0.2-5) ... Processing triggers for systemd (215-17) ... Setting up liblzo2-2:amd64 (2.08-1.2) ... Setting up libpkcs11-helper1:amd64 (1.11-2) ... Setting up opensc-pkcs11:amd64 (0.14.0-2) ... Setting up openssl (1.0.1k-3) ... Setting up openvpn (2.3.4-5) ... Restarting virtual private network daemon.:. Setting up easy-rsa (2.2.2-1) ... Setting up opensc (0.14.0-2) ... Processing triggers for libc-bin (2.19-18) ... Processing triggers for systemd (215-17) ...
The VPN client is now installed but now we need the connection profile and this must be done on the VPN server side; therefore let’s move to the server part, we’ll use the SOPHOS UTM Home Edition (formerly Astaro Security Gateway). You can have a personal license for your home environment with very few limitations and it’s just perfect as OpenVPN server in our case.
This time we’ll assume that the UTM firewall is already installed; the installation is very straight forward and well documented, for further help take a look at following references:
Let’s configure the remote access profile on the Sophos UTM, step by step:
Now we need to retrieve the OpenVPN configuration files for our Appliance (certificates, private key and OpenVPN config file).
The files are:
We need to transfer those files to the client, we’ll use an USB stick this time. Let’s move to the next step: configure the OpenVPN client on the APU appliance.
Let’s continue by configuring the remote access profile going step by step:
root@bluebrick:/# dmesg| tail -n 20 [27734.428274] usb 1-1: new high-speed USB device number 2 using ehci-pci [27734.566099] usb 1-1: New USB device found, idVendor=0951, idProduct=1689 [27734.566116] usb 1-1: New USB device strings: Mfr=1, Product=2, SerialNumber=3 [27734.566124] usb 1-1: Product: DataTraveler SE9 [27734.566132] usb 1-1: Manufacturer: Kingston [27734.566139] usb 1-1: SerialNumber: 0019E06B7114BCB107E20091 [27734.567479] usb-storage 1-1:1.0: USB Mass Storage device detected [27734.568669] scsi7 : usb-storage 1-1:1.0 [27735.651373] scsi 7:0:0:0: Direct-Access Kingston DataTraveler SE9 PMAP PQ: 0 ANSI: 4 [27735.652878] sd 7:0:0:0: Attached scsi generic sg2 type 0 [27737.152959] sd 7:0:0:0: [sdc] 15356160 512-byte logical blocks: (7.86 GB/7.32 GiB) [27737.153644] sd 7:0:0:0: [sdc] Write Protect is off [27737.153657] sd 7:0:0:0: [sdc] Mode Sense: 23 00 00 00 [27737.154269] sd 7:0:0:0: [sdc] No Caching mode page found [27737.159670] sd 7:0:0:0: [sdc] Assuming drive cache: write through [27737.192503] sdc: sdc1 [27737.200700] sd 7:0:0:0: [sdc] Attached SCSI removable disk
root@bluebrick:~# mount /dev/sdc1 /mnt/ root@bluebrick:~# root@bluebrick:~# df -h Filesystem Size Used Avail Use% Mounted on /dev/sda5 15G 710M 13G 6% / udev 10M 0 10M 0% /dev tmpfs 787M 8.5M 779M 2% /run tmpfs 2.0G 0 2.0G 0% /dev/shm tmpfs 5.0M 0 5.0M 0% /run/lock tmpfs 2.0G 0 2.0G 0% /sys/fs/cgroup /dev/sda1 114M 31M 74M 30% /boot /dev/sdc1 7.4G 3.1G 4.3G 42% /mnt
root@bluebrick:/# cp /mnt/bluebrick.config/* /etc/openvpn/ root@bluebrick:/# ll /etc/openvpn/ total 39K 4.0K drwxr-xr-x 2 root root 4.0K Aug 19 00:50 . 4.0K drwxr-xr-x 73 root root 4.0K Aug 18 21:36 .. 4.0K -rwxr-xr-x 1 root root 625 Aug 19 00:50 bluebrick.ovpn 8.0K -rwxr-xr-x 1 root root 4.3K Aug 19 00:50 ca.crt 4.0K -rwxr-xr-x 1 root root 1.3K Dec 1 2014 update-resolv-conf 8.0K -rwxr-xr-x 1 root root 4.7K Aug 19 00:50 user.crt 4.0K -rwxr-xr-x 1 root root 1.7K Aug 19 00:50 user.key root@bluebrick:/# umount /mnt/
root@bluebrick:/etc/openvpn# mv bluebrick.ovpn bluebrick.conf root@bluebrick:/etc/openvpn# ll total 39K 4.0K drwxr-xr-x 2 root root 4.0K Aug 19 00:55 . 4.0K drwxr-xr-x 73 root root 4.0K Aug 18 21:36 .. 4.0K -rwxr-xr-x 1 root root 625 Aug 19 00:50 bluebrick.conf 8.0K -rwxr-xr-x 1 root root 4.3K Aug 19 00:50 ca.crt 4.0K -rwxr-xr-x 1 root root 1.3K Dec 1 2014 update-resolv-conf 8.0K -rwxr-xr-x 1 root root 4.7K Aug 19 00:50 user.crt 4.0K -rwxr-xr-x 1 root root 1.7K Aug 19 00:50 user.key
/etc/default/openvpn
# This is the configuration file for /etc/init.d/openvpn # # Start only these VPNs automatically via init script. # Allowed values are "all", "none" or space separated list of # names of the VPNs. If empty, "all" is assumed. # The VPN name refers to the VPN configutation file name. # i.e. "home" would be /etc/openvpn/home.conf # # If you're running systemd, changing this variable will # require running "systemctl daemon-reload" followed by # a restart of the openvpn service (if you removed entries # you may have to stop those manually) # AUTOSTART="bluebrick" #AUTOSTART="none" #AUTOSTART="home office" #
The file should look similar to this:
dev tun proto tcp remote vpn.acc.lab 8000 tls-remote "C=ch, L=Zurich, O=ACC, CN=vpn.acc.lab, emailAddress=andrea@acc.lab" route remote_host 255.255.255.255 net_gateway resolv-retry infinite nobind persist-key persist-tun ca ca.crt cert user.crt key user.key auth-user-pass cipher AES-256-CBC auth SHA512 comp-lzo route-delay 4 verb 3 reneg-sec 0 auth-user-pass user.pwd
root@bluebrick:/etc/openvpn# vi user.pwd
bluebrick password
The file has only two lines the first one is the username (bluebrick in this case); the second one is the password used for creating the user account on the Sophos UTM admin interface.
Unfortunately having the requirement of The appliance must boot unattended you have to do it this way, therefore make sure to secure the file permission of the critical files:
root@bluebrick:/etc/openvpn# chmod 600 user.pwd user.key bluebrick.conf root@bluebrick:/etc/openvpn# ll total 40K 4.0K drwxr-xr-x 2 root root 4.0K Aug 19 01:17 . 4.0K drwxr-xr-x 73 root root 4.0K Aug 18 21:36 .. 4.0K -rw------- 1 root root 405 Aug 19 01:15 bluebrick.conf 8.0K -rwxr-xr-x 1 root root 4.3K Aug 19 00:50 ca.crt 4.0K -rwxr-xr-x 1 root root 1.3K Dec 1 2014 update-resolv-conf 8.0K -rwxr-xr-x 1 root root 4.7K Aug 19 00:50 user.crt 4.0K -rw------- 1 root root 1.7K Aug 19 00:50 user.key 4.0K -rw------- 1 root root 24 Aug 19 01:12 user.pwd
Of course you can define a configuration that has file encryption or just require the user password; but then you need user interaction ether booting the Appliance or every time you start the VPN tunnel – Usability would become a no-go in our scenario.
root@bluebrick:/etc/openvpn# openvpn bluebrick.conf Wed Aug 19 01:20:56 2015 DEPRECATED OPTION: --tls-remote, please update your configuration Wed Aug 19 01:20:56 2015 OpenVPN 2.3.4 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [PKCS11] [MH] [IPv6] built on Dec 1 2014 Wed Aug 19 01:20:56 2015 library versions: OpenSSL 1.0.1k 8 Jan 2015, LZO 2.08 Wed Aug 19 01:20:56 2015 Socket Buffers: R=[87380->131072] S=[16384->131072] Wed Aug 19 01:20:57 2015 Attempting to establish TCP connection with [AF_INET]80.218.88.202:8000 [nonblock] Wed Aug 19 01:20:58 2015 TCP connection established with [AF_INET]80.218.88.202:8000 Wed Aug 19 01:20:58 2015 TCPv4_CLIENT link local: [undef] Wed Aug 19 01:20:58 2015 TCPv4_CLIENT link remote: [AF_INET]80.218.88.202:8000 Wed Aug 19 01:20:58 2015 TLS: Initial packet from [AF_INET]80.218.88.202:8000, sid=696cfd8e 72c64322 Wed Aug 19 01:20:58 2015 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Wed Aug 19 01:21:22 2015 VERIFY OK: depth=1, C=ch, L=Zurich, O=ACC, CN=ACC VPN CA, emailAddress=andrea@acc.lab Wed Aug 19 01:21:22 2015 VERIFY X509NAME OK: C=ch, L=Zurich, O=ACC, CN=vpn.acc.lab, emailAddress=andrea@acc.lab Wed Aug 19 01:21:22 2015 VERIFY OK: depth=0, C=ch, L=Zurich, O=ACC, CN=vpn.acc.lab, emailAddress=andrea@acc.lab Wed Aug 19 01:21:27 2015 Data Channel Encrypt: Cipher 'AES-256-CBC' initialized with 256 bit key Wed Aug 19 01:21:27 2015 Data Channel Encrypt: Using 512 bit message hash 'SHA512' for HMAC authentication Wed Aug 19 01:21:27 2015 Data Channel Decrypt: Cipher 'AES-256-CBC' initialized with 256 bit key Wed Aug 19 01:21:27 2015 Data Channel Decrypt: Using 512 bit message hash 'SHA512' for HMAC authentication Wed Aug 19 01:21:27 2015 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 2048 bit RSA Wed Aug 19 01:21:27 2015 [vpn.acc.lab] Peer Connection Initiated with [AF_INET]80.218.88.202:8000 Wed Aug 19 01:21:29 2015 SENT CONTROL [vpn.acc.lab]: 'PUSH_REQUEST' (status=1) Wed Aug 19 01:21:34 2015 SENT CONTROL [vpn.acc.lab]: 'PUSH_REQUEST' (status=1) Wed Aug 19 01:21:39 2015 SENT CONTROL [vpn.acc.lab]: 'PUSH_REQUEST' (status=1) Wed Aug 19 01:21:44 2015 SENT CONTROL [vpn.acc.lab]: 'PUSH_REQUEST' (status=1) Wed Aug 19 01:21:49 2015 SENT CONTROL [vpn.acc.lab]: 'PUSH_REQUEST' (status=1) Wed Aug 19 01:21:50 2015 PUSH: Received control message: 'PUSH_REPLY,route 10.242.2.1,topology net30,ping 10,ping-restart 120,route 10.10.5.0 255.255.255.0,ifconfig 10.242.2.14 10.242.2.13' Wed Aug 19 01:21:50 2015 OPTIONS IMPORT: timers and/or timeouts modified Wed Aug 19 01:21:50 2015 OPTIONS IMPORT: --ifconfig/up options modified Wed Aug 19 01:21:50 2015 OPTIONS IMPORT: route options modified Wed Aug 19 01:21:50 2015 ROUTE_GATEWAY 10.149.210.211/255.255.255.248 IFACE=wwan0 HWADDR=02:80:37:ec:02:00 Wed Aug 19 01:21:50 2015 TUN/TAP device tun0 opened Wed Aug 19 01:21:50 2015 TUN/TAP TX queue length set to 100 Wed Aug 19 01:21:50 2015 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0 Wed Aug 19 01:21:50 2015 /sbin/ip link set dev tun0 up mtu 1500 Wed Aug 19 01:21:50 2015 /sbin/ip addr add dev tun0 local 10.242.2.14 peer 10.242.2.13 Wed Aug 19 01:21:54 2015 /sbin/ip route add 80.218.88.202/32 via 10.149.210.211 Wed Aug 19 01:21:54 2015 /sbin/ip route add 10.242.2.1/32 via 10.242.2.13 Wed Aug 19 01:21:54 2015 /sbin/ip route add 10.10.5.0/24 via 10.242.2.13 Wed Aug 19 01:21:54 2015 Initialization Sequence Completed
Looks good! Now, hit CTRL+C to stop the tunnel and this test
^CWed Aug 19 01:23:26 2015 event_wait : Interrupted system call (code=4) Wed Aug 19 01:23:26 2015 /sbin/ip route del 10.10.5.0/24 Wed Aug 19 01:23:26 2015 /sbin/ip route del 10.242.2.1/32 Wed Aug 19 01:23:26 2015 /sbin/ip route del 80.218.88.202/32 Wed Aug 19 01:23:26 2015 Closing TUN/TAP interface Wed Aug 19 01:23:26 2015 /sbin/ip addr del dev tun0 local 10.242.2.14 peer 10.242.2.13 Wed Aug 19 01:23:26 2015 SIGINT[hard,] received, process exiting
We are finally ready to test if the appliance boots in unattended-mode and connects automatically to our VPN server. Reboot and wait two to three minutes and then login and check the interfaces:
# ifconfig
...
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.242.2.14 P-t-P:10.242.2.13 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
wwan0 Link encap:Ethernet HWaddr 02:80:37:ec:02:00
inet addr:10.146.202.177 Bcast:10.146.202.183 Mask:255.255.255.248
inet6 addr: fe80::80:37ff:feec:200/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:3 errors:0 dropped:0 overruns:0 frame:0
TX packets:11 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:684 (684.0 B) TX bytes:1674 (1.6 KiB)As you can see in the tun0 interface info, we received an IP (10.242.2.14) in the VPN-POOL range for our point-to-point (P-t-P) connection. We can state now that the configuration is working as expected. Now let’s test the access our internal network (10.10.5.0/24 in this case):
root@bluebrick:~# ping 10.10.5.252 PING 10.10.5.252 (10.10.5.252) 56(84) bytes of data. 64 bytes from 10.10.5.252: icmp_seq=1 ttl=64 time=420 ms 64 bytes from 10.10.5.252: icmp_seq=2 ttl=64 time=380 ms 64 bytes from 10.10.5.252: icmp_seq=3 ttl=64 time=400 ms 64 bytes from 10.10.5.252: icmp_seq=4 ttl=64 time=370 ms 64 bytes from 10.10.5.252: icmp_seq=5 ttl=64 time=410 ms 64 bytes from 10.10.5.252: icmp_seq=6 ttl=64 time=530 ms ^C --- 10.10.5.252 ping statistics --- 7 packets transmitted, 6 received, 14% packet loss, time 6001ms rtt min/avg/max/mdev = 370.204/418.452/530.190/52.751 ms Everything is fine here, let's move to the next part.
To access our appliance we need to verify the connection on our VPN server (Sophos UTM). So connect to the administration dashboard. On the lower right quadrant you should see (in the Current System Configuration tab) Remote Access is active with 1 online users – Now click on it and you’ll get following view:
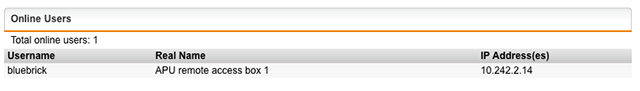
There is the username (bluebrick) and its assigned IP address (10.242.2.14) – Let’s connect to the SSH server on the APU appliance:
SilverSkull:~ andrea$ ssh root@10.242.2.14 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Wed Aug 19 10:31:35 2015 from 10.10.5.41 root@bluebrick:~#
Access is granted, from here on we can access our APU Appliance and do any required support task.
We need to secure our Appliance on the network layer, as we don’t have a multiuser operation here. We’ll secure the network layer configuring IPtables to limit access:
For this to happen, we need to configure the IPv6 and IPv4 iptables configuration files
root@bluebrick:~# apt-get install iptables-persistent Reading package lists... Done Building dependency tree Reading state information... Done The following extra packages will be installed: netfilter-persistent The following NEW packages will be installed: iptables-persistent netfilter-persistent 0 upgraded, 2 newly installed, 0 to remove and 0 not upgraded. Need to get 18.9 kB of archives. After this operation, 147 kB of additional disk space will be used. Do you want to continue? [Y/n] Get:1 http://http.debian.net/debian/ jessie/main netfilter-persistent all 1.0.3 [8,036 B] Get:2 http://http.debian.net/debian/ jessie/main iptables-persistent all 1.0.3 [10.8 kB] Fetched 18.9 kB in 1s (18.2 kB/s) Preconfiguring packages ... Selecting previously unselected package netfilter-persistent. (Reading database ... 19298 files and directories currently installed.) Preparing to unpack .../netfilter-persistent_1.0.3_all.deb ... Unpacking netfilter-persistent (1.0.3) ... Selecting previously unselected package iptables-persistent. Preparing to unpack .../iptables-persistent_1.0.3_all.deb ... Unpacking iptables-persistent (1.0.3) ... Processing triggers for man-db (2.7.0.2-5) ... Processing triggers for systemd (215-17+deb8u1) ... Setting up netfilter-persistent (1.0.3) ... update-rc.d: warning: start and stop actions are no longer supported; falling back to defaults Setting up iptables-persistent (1.0.3) ... Processing triggers for systemd (215-17+deb8u1) ... root@bluebrick:~#
During the installation you’ll be asked following question:
|============================== Configuring iptables-persistent =================================| | | | Current iptables rules can be saved to the configuration file /etc/iptables/rules.v4. | | These rules will then be loaded automatically during system startup. | | | | Rules are only saved automatically during package installation. | | See the manual page of iptables-save(8) for instructions on keeping the rules file up-to-date. | | | | Save current IPv4 rules? | | | | <Yes> <No> | | | |================================================================================================|
Select YES
# An example for an IPtables ruleset (IPv4) # Default rules *filter :INPUT DROP [0:0] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [0:0] # FW Incoming Policy # Accept input traffic on trusted interfaces (localhost and VPN tunnel device) -A INPUT -i lo -j ACCEPT -A INPUT -i tun0 -j ACCEPT # Allow incoming data that is part of an already established session -A INPUT -m state --state ESTABLISHED -j ACCEPT # Allow data that is related to an existing session -A INPUT -m state --state RELATED -j ACCEPT # Accept responses to DNS queries -A INPUT -p udp -m udp --dport 1024:65535 --sport 53 -j ACCEPT # Accept responses to our pings -A INPUT -p icmp -m icmp --icmp-type echo-reply -j ACCEPT # Accept notifications of unreachable hosts -A INPUT -p icmp -m icmp --icmp-type destination-unreachable -j ACCEPT # Accept notifications to reduce sending speed -A INPUT -p icmp -m icmp --icmp-type source-quench -j ACCEPT # Accept notifications of lost packets -A INPUT -p icmp -m icmp --icmp-type time-exceeded -j ACCEPT # Accept notifications of protocol problems -A INPUT -p icmp -m icmp --icmp-type parameter-problem -j ACCEPT # Allow connections to SSH server from trusted sources (our internal network and localhost) -A INPUT -s 10.10.5.0/255.255.255.0 -p tcp -m tcp --dport 22 -j ACCEPT -A INPUT -s 127.0.0.1 -p tcp -m tcp --dport 22 -j ACCEPT # Respond to pings -A INPUT -p icmp -m icmp --icmp-type echo-request -j ACCEPT COMMIT
For IPv6 edit its config file with vi /etc/ip6tables and should look like this:
# Example for IPtables ruleset IPv6 # Drop all (IPv6 Traffic) *filter :INPUT DROP [0:0] :FORWARD DROP [0:0] :OUTPUT DROP [0:0] COMMIT
Once you reboot the settings are active and can be verified with:
root@bluebrick:~# iptables -L Chain INPUT (policy DROP) target prot opt source destination ACCEPT all -- anywhere anywhere ACCEPT all -- anywhere anywhere ACCEPT all -- anywhere anywhere state ESTABLISHED ACCEPT all -- anywhere anywhere state RELATED ACCEPT udp -- anywhere anywhere udp spt:domain dpts:1024:65535 ACCEPT icmp -- anywhere anywhere icmp echo-reply ACCEPT icmp -- anywhere anywhere icmp destination-unreachable ACCEPT icmp -- anywhere anywhere icmp source-quench ACCEPT icmp -- anywhere anywhere icmp time-exceeded ACCEPT icmp -- anywhere anywhere icmp parameter-problem ACCEPT tcp -- 10.10.5.0/24 anywhere tcp dpt:ssh ACCEPT tcp -- localhost anywhere tcp dpt:ssh ACCEPT icmp -- anywhere anywhere icmp echo-request Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination
and
root@bluebrick:~# ip6tables -L Chain INPUT (policy DROP) target prot opt source destination Chain FORWARD (policy DROP) target prot opt source destination Chain OUTPUT (policy DROP) target prot opt source destination
The network layer security is done now and we have at least a basic security control in place. More security is always possible but at the moment is a good starting point.
root@bluebrick:~# apt-get install yasat Reading package lists... Done Building dependency tree Reading state information... Done The following NEW packages will be installed: yasat 0 upgraded, 1 newly installed, 0 to remove and 0 not upgraded. Need to get 105 kB of archives. After this operation, 719 kB of additional disk space will be used. Get:1 http://http.debian.net/debian/ jessie/main yasat all 755-1 [105 kB] Fetched 105 kB in 3s (27.7 kB/s) Selecting previously unselected package yasat. (Reading database ... 19315 files and directories currently installed.) Preparing to unpack .../archives/yasat_755-1_all.deb ... Unpacking yasat (755-1) ... Processing triggers for man-db (2.7.0.2-5) ... Setting up yasat (755-1) ... root@bluebrick:~#
The help is nice and clear:
root@bluebrick:~# yasat --help Found /etc/yasat/yasat.conf ===================================== == YASAT == == Yet Another Stupid Audit Tool == == == == Copyright (C) 2008-2014 == == LABBE Corentin == ============================================================ |Available options | | | | --standard (-s) Do standard test ===== | --list (-l) List plugins available | | --debug (-d) print debug informations | | --help (-h) show this help ===== | --html (-H) export YASAT 's results in html | | default to ~/yasat/yasat.html | | --html-output PATH PATH is the name of html file to write | | --advice-lang LANG LANG is the 2letter digit of the lang | | (default is EN ) | | --full-scan (-f) Do extra (long) tests (lots of find) | | --plugins-dir PATH (-P) Set the path to the plugins to use | | (default is ./plugins ) | | --nopause (-a) Do not make a pause after plugin's end | | --plugin PATH (-1) Just use the plugin pointed by PATH | | --Plugin NAME (-p) Just use the plugin named NAME | | --scanroot PATH (-r) Scan PATH instead of / (WorkInProgress)| | --compliance type Check for a specific compliance. | | type could be cce, nsa or all | | --print-level X Just print infos equal or above the | | level X (All = 0 (default), infos = 1 | | warnings(orange) = 2, errors(red) = 3 | | --skip Test(s) to skip, without the .test | | (ex: --skip nfs,ntp) comma separated | | --check-update Check if an update of YASAT exists | | --send-support Same as --check-support but you will | | send also your OS version as parameter | | | | Thanks for using YASAT. | | | ====================================================================
Just run it with the standard flag (-s) and check the output:
root@bluebrick:~# yasat -s
Found /etc/yasat/yasat.conf
Using YASAT version [ 755 ]
Using YASAT with UID=0 [ OK ]
Using YASAT without SELinux [ OK ]
Detecting OS... [ DONE ]
Debian Linux Linux 3.16.0-4-amd64
Detecting TERM width... [ 137 ]
Color chart
GREEN is for good configuration or information
RED is for configuration that must be corrected
ORANGE is for optional configuration that can be done
BLUE is for information
At the end of the audit, the report will be available at /root/.yasat//yasat.report
=== Check accounting and audit configuration ===
/var/log/wtmp [ FOUND ]
/var/log/btmp [ FOUND ]
/var/log/faillog [ FOUND ]
/var/log/lastlog [ FOUND ]
accounting is not enabled [ WARNING ] Enable the accounting with accton
Found sha512 in pam.d [ OK ]
cracklib [ NOTFOUND ]
/etc/shadow [ FOUND ]
password hash method for root [ SHA512 ]
default password encryption [ sha512 ]
audit is installed by package [ GOOD ]
...Hopefully you have color support for your terminal… ;) I guess we’re done here. Except for the last but not least section: monitoring
First and foremost: you should activate log on your APU Appliance and make sure you keep local logs as much as possible, better would it be to send an (encrypted) copy to a remote syslog-collector. Another good hint is to install a local monitor agent that will alert and take action automatically if needed, I recommend Monit.
apt-get install monit
Here are a few examples of possible monit monitoring jobs for our project:
Now let’s apply the above job requirements into the configuration – Edit the config file /etc/monit/monitrc like this:
###############################################################################
## Monit control file version 20150819_110
###############################################################################
###############################################################################
## Global section
###############################################################################
set daemon 60
set logfile syslog facility log_daemon
set idfile /var/lib/monit/id
set statefile /var/lib/monit/state
set mailserver mail.domain.ch USERNAME alarm@domain.ch PASSWORD password
with timeout 30 seconds
using HOSTNAME bluebrick
set eventqueue
basedir /var/lib/monit/events # base directory where events will be stored
slots 100 # optionally limit the queue size
set mail-format {
from: $HOST@domain.ch
subject: monit alert -- $EVENT $SERVICE
message: $EVENT Service $SERVICE
Date: $DATE
Action: $ACTION
Host: $HOST
Description: $DESCRIPTION
}
set alert andrea@acc.lab
set httpd port 8000 address 127.0.0.1
allow localhost # allow localhost to connect to the server and
allow admin:monit # require user 'admin' with password 'monit'
###############################################################################
## CHECK System & Services
###############################################################################
##
##=============================================================================
## Check System
check system bluebrick
if loadavg (1min) > 4 then alert
if loadavg (5min) > 2 then alert
if memory usage > 85% then alert
if swap usage > 80% then alert
if cpu usage (user) > 85% then alert
if cpu usage (system) > 50% then alert
##=============================================================================
## Check openSSHd
check process sshd with pidfile /var/run/sshd.pid
start program = "/etc/init.d/ssh start"
stop program = "/etc/init.d/ssh stop"
if failed host localhost port 22 with proto ssh then alert
if failed host localhost port 22 with proto ssh then restart
if 5 restarts with 5 cycles then timeout
##=============================================================================
## Check VPN Tunnel (OpenVPN)
check process openvpn matching openvpn
start program = "/etc/init.d/openvpn start"
stop program = "/etc/init.d/openvpn stop"
if does not exist then alert
if 5 restarts with 5 cycles then timeout
##=============================================================================
## Check filesystem
check filesystem system with path /dev/sda1
if space usage > 80% for 5 times within 15 cycles then alert
##=============================================================================
## Check Configuration & Log Files
check file user_key path /root/openvpn/user.key
if failed permission 600 then alert
if failed uid root then alert
if failed gid root then alert
check file user_credentials path /root/openvpn/user.pwd
if failed permission 600 then alert
if failed uid root then alert
if failed gid root then alert
check file openvpn_config path /root/openvpn/bluebrick.conf
if failed SHA1 checksum expect c1a0a376f19b3e7f70c26b6305c8042163818f18 then alert
##=============================================================================
## Check VPN Tunnel is up and running
check host vpn.acc.lab with address 10.242.2.1
if failed icmp type echo count 3 with timeout 3 seconds then alertRestart the monit daemon and check it’s working as expected with:
root@bluebrick:~# /etc/init.d/monit restart Restarting monit (via systemctl): monit.service. root@bluebrick:~# root@bluebrick:~# monit summary The Monit daemon 5.9 uptime: 0m System 'bluebrick' Running Process 'sshd' Running Process 'openvpn' Running Filesystem 'system' Accessible File 'user_key' Accessible File 'user_credentials' Accessible Remote Host 'vpn.acc.lab' Online with all services root@bluebrick:~# Monit possibilities are huge! Take a look on its "documentation":https://mmonit.com/monit/documentation/monit.html online; there is room for an article on its own... Maybe next time ;).
The APU is a great piece of hardware and this is only one of the possible use cases. The Out of Band Remote Support configuration is expandable to other scenarios like a Remote Scan Appliance… Still, we only scratched the surface here, more effort is required to fine-tune the specific requirements. Hope you enjoyed the ride so far and I’ll encourage you to take a deeper dive in the matter… Cheers!
Our experts will get in contact with you!

Tomaso Vasella

Eric Maurer

Marius Elmiger

Eric Maurer
Our experts will get in contact with you!