Specific Criticism of CVSS4
Marc Ruef

The Darknet is a hidden area of the Internet. It is only accessible using special software and relationships of trust. During extensive research various areas of the Darknet have been investigated. Part of this research is presented in this article.
The term Darknet presents a problem in itself that can be found in so many areas of IT: It’s a buzzword that is used often but rarely understood. The reasoning behind this has many layers. Basically, very few people have found their way into the Darknet that are willing to talk about it. Journalists copy each others’ articles without verifying what they write. Due to this, a lot of misinformation has accumulated over the years that is difficult to disentangle.
What also helped this confusion is an infographic that is actually satire, but few people actually get it. There’s a point where one realizes that some writer has no idea what he or she is on about when the text says that the some parts of the Darknet can only be navigated using a quantum computer. Articles based on this misinformation are published monthly. The following graphic corrects this image.

During our analysis we’ve compartmentalized the Internet into areas. The suffix net refers to something that offers any kind of service, such as Darknet. Many publications use the suffix web as in Darkweb, which refers to Darknet resources that are offered by a web server and can be access using a web browser. The Freenet, also known as Visible Net or Visinet, is the Internet as we all know it. It is made up of freely accessible websites that are being indexed by search engines.
As soon as search engines don’t have direct access to the information anymore, we speak of the Deepnet or Invisible Net. This is the case when a website in the Deepweb requires authentication or is only known to a small group of people. Or when alternate network protocols or topologies are used that hinder indexing. The latter is used in Peer-to-Peer Networks (P2P) that require the use of dedicated software in order to be usable. This can’t be referred to as the Deepweb as the usual web mechanisms do not apply.
One step further, we enter the Darknet. Here, special P2P networks are run, among other things. In Friend-to-Friend networks (F2F) data is only stored and distributed decentralized and among select friends. To access this data, a user needs a circle of friends on the Darknet. Furthermore, there are private forums that can only be accessed after receiving an invitation and after being given permission to. As long as nobody’s vouching for a user, said user can’t access anything.
Finally, there are temporary chat servers that are neither persistent nor archived. They disappear after a transaction has been completed and they’re used for highly illegal activity, often the orchestration or conducting of a transaction. The technology used for this is typically IRC or Jabber/XMPP. Communication is encrypted and chats are not stored in logs.
The complexity and the effort to navigate the lower levels of the Darknet keep increasing. Comfort is neglected in favour of security, which is why these areas are unsuitable for regular activity. Therefore, dubious people prefer them.
A large part of Darknet activity happens on websites that are only accessible by Tor. These Darkweb pages are described as Hidden Services due to the fact that they’re theoretically hidden from search engines. There are a few indexing search engines in the Darknet that can’t compare to the efficiency, quality and coverage that Google and its competitors have.
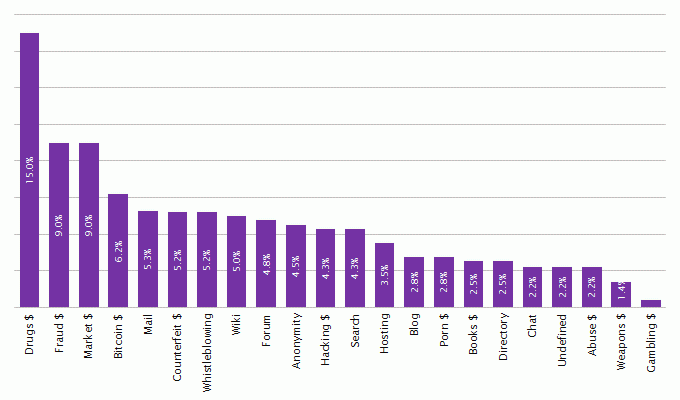
There are various analyses of Hidden Services. The first extensive one was conducted by security specialist Gareth Owen who didn’t mention exact figures in his presentation Tor: Hidden Services and Deanonymisation. Still, this vague data was the basis for the analysis of the often-cited List of TOR Hidden Services. The problem is that the sum of percentages exceeds the 100%, making the entire list useless.
Therefore, we have conducted an extended analysis of Hidden Services and have reached the results displayed below. The categorization shows that almost half of the Hidden Services have a commercial background. There, data, information or products are exchanged for money in order to generate profit. The conclusion: The Darknet is mainly used to make profit.
Respecting all laws, we participate in select activities on the Darknet in order to understand the markets’ structures and the behaviour of participants. We will present the main markets and conclusions drawn from observing them. Our research did not just focus on generalist markets (similar to eBay) but also included dedicated sites. In order to protect the identities of our sources and analysts, no personal data about them has been recorded.
A large part of the goods traded on the Darknet are drugs and medication. The Global Drug Survey 2015 reached many interesting conclusions by systematic questioning of drug addicts and drug dealers on the Darknet. The main reason why exchanges have moved to the Darknet is the increase in personal security. The people around Ross Ulbricht, also known as the Dread Pirate Roberts, who ran one of the largest drug trafficking sites on the Darknet called Silk Road, claim that this leads to profit for all people involved. Additional factors: The participants’ identities remain hidden and drug abuse can be hidden from the personal surroundings.
Most, if not all, drugs are being dealt with on the Darknet. Especially popular are Cannabis (weed as well as hashish), MDMA, cocaine and heroin.
The price range of various drugs varies. A gram Kratom costs between USD 0.06 and USD 0.12. Opium has a much wider range from USD 1.30 to USD 6.00. The biggest range can be observed in Xanax trading, where prices range from USD 35.50 to USD 330. Prices for LSD start at USD 3265.
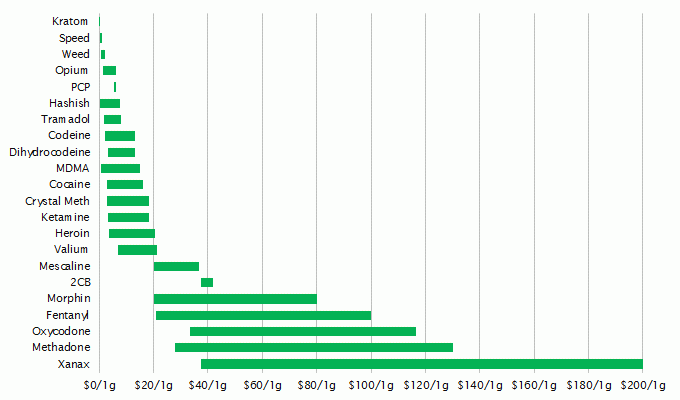
These ranges have several reasons. The rule of thumb is that most dealers grant bulk discounts. If a buyer is only interested in a sample, the costs are disproportionally high. Kilograms of cocaine are much cheaper when compared to small quantities. A systematic analysis shows that certain dealers miscalculate when they grant bulk discounts. It happens that buying two kilograms of opium is cheaper per gram compared to buying five kilograms. Automated analyses of transactions lead to the suspicion that other vendors are not noticing mistakes of this kind systematically and also do not exploit it (cheap purchases, more expensive reselling).
Furthermore, the quality of the product is a deciding factor. Crystal meth that is as pure as possible is more expensive than unclean product. Some vendors add purity grade to their offers. They’re typically exaggerated in order to justify high sales prices. It is this factor that makes it very difficult to compare seemingly similar prices. Most professional markets offer rating and comment features for buyers based on which the quality can be gauged.
Ultimately the shipping conditions are a deciding factor for the price of a product. Depending on its origin and its destination, an order can carry various risks that directly influence the price of a product. An effect that can also be observed in weapons trade.
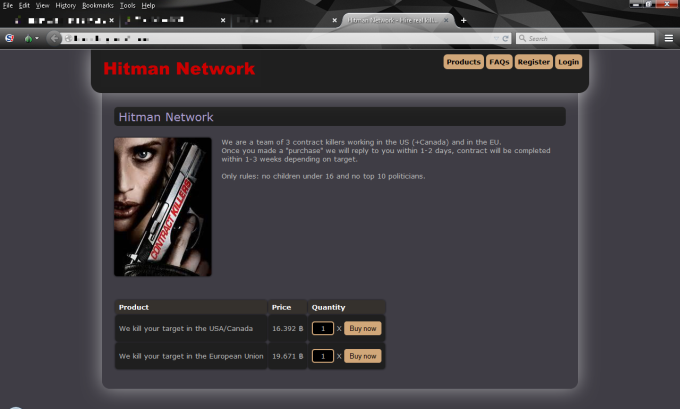
A very special market is contract killings. Traditionally, assassins, killers, or guns for hire can be tasked with murdering one person or several people in exchange for money. Payment is usually done in advance or in instalments before and after the contract is fulfilled.
A special kind of contract killings are so called bidding contracts. In one of these contracts, anyone can put a name on a list and people bid Bitcoin on the killing of that target person. The killer who fulfils the contract gets all the money. These lists are mostly populated by famous names such as Barack Obama.
Assassin networks see killers offer their services with a personal profile. On these profiles, they typically include their conditions:
Our research indicates that many of the services on offer aren’t real. The profiles and price structures contradict some of the common operations in the field. Often, these offers are nothing but provocation and trolling.
We have compared several sources in order to, among other things, gauge the price range of a contract killing per country. We’ve only taken into account verified prices. A price is verified when there’s been a confirmed transfer of funds or either the killer or the person who hired the killer has talked about the price after being arrested. We also only took into account professional killers. Opportunists that acted once out of impulse were discarded.
David Wilson, professor at Birmingham City University, has analysed murders in the United Kingdom between 1974 and 2014 in order to identify statistical markers. He was able to determine price structures and conditions of contract killings. The data we compiled was compared to the offers on the Darknet in order to determine authenticity and price range.
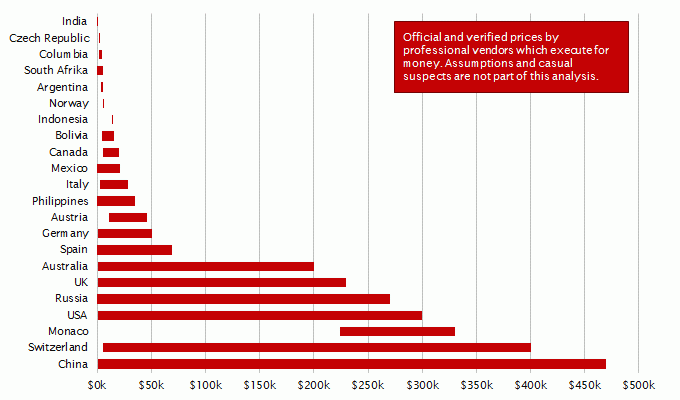
As expected, the prices for murders in developing countries are much lower than in first world countries. The maximum prices are also much higher than in third world countries. This has two reasons:
This and other information is used by us to create risk profiles for high-profile employees of our clients. This way we can recommend not performing certain activities or taking certain journeys and we can consult on the strength on the local security force.
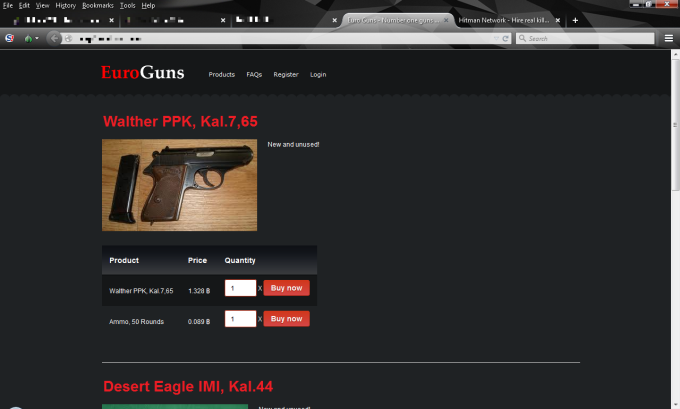
Dealing with weapons on the Internet, primarily on the Darknet, is becoming more and more common. There are various sources of weapons. Often, it’s private collectors and dealers that want to sell or exchange guns and ammunition. The scene in Germany and Austria is surprisingly motivated.
In these circles there are primarily old and modified guns. Usually, it’s enthusiasts who simply take pleasures in the devices. Contacting vendors has shown that they treat the subject lightly. A gun is a sports accessory or a tool. The fact that it might kill a person is either being tuned out or the responsibility for such an act is being deferred to the client.
The terror attacks of November 13, 2015, in Paris have led to immediate effects on the Darknet. The two popular markets Agora and Nucleus have ceased the sale of weapons as a result of the attacks. It amazes that these platforms do have a certain moral compass.
Large calibre guns and explosives that are for sale or for trade originate in warzones and civil wars. Here, very old weapons as well as new versions can be gotten in large quantities.
Many vendors prefer to deliver within the target country. Inside the European area, many offers oftentimes include notes that they are not delivering outside of said area. This aims to avoid the expensive and dangerous customs declaration. A behaviour that is also being observed in drug trades, even if not to this extent.
In the Information Age, data trade plays an increasingly important role. There are many sets of information that are traded. For corporations and official offices, we curate price lists that are reviewed every day in order to see movement in the market. For example when prices for credit card information change in big ways, it’s predictable that somewhere a big data leak has been exploited. This can lead to something akin to a seismographic observation of the market. The following table shows some benchmarks for data.
| Data Type | Details | Price USD |
|---|---|---|
| E-Mail Account Information | 1000 entries, random, not verified | 0.50 |
| E-Mail Account Information | 1 entry, per defined domain, verified | 5 |
| Credit Card | number only, no personal data, not verified | 0.60 |
| Credit Card | number only, no personal data, verified | 7.50 |
| Credit Card | plastic, incl. PIN, verified, guaranteed coverage | 80 |
| Passport | France, scan only | 7 |
| Passport | Switzerland, scan only | 38 |
| Passport | USA, complete forgery | 160 |
| Identification | Generation with templates | 34 |
| Identification | Australia, driver’s license, scan | 20 |
| Identification | UK, driver’s license, modified copy | 10 |
| Identification | Canada, identification documents, scan | 5 |
| Identification | USA, Social Security Card, Scan | 20 |
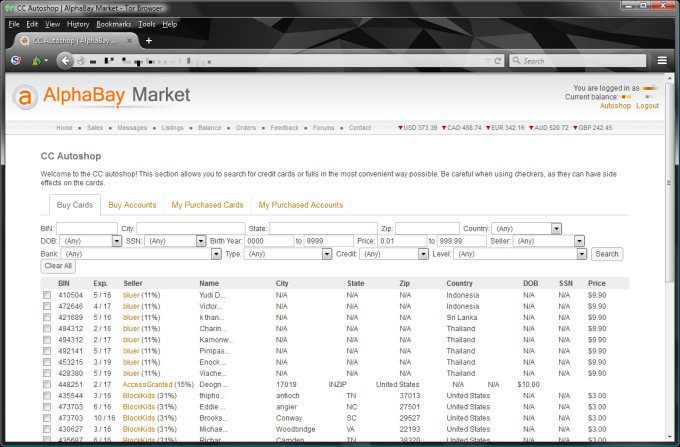
Credit cards have been traded in the underground since the beginning. This has only become marginally more frequent in recent years. What does stand to note is that the credit card trade has become increasingly professional: The vendors prepare and present the data better. Leader in terms of ease of use, comfort and offer is currently CC Autoshop by AlphaBay: Here, credit card data can be filtered, sorted and searched (expiry date, origin, date of birth).
Health data become increasingly subject of interest. Social Security Numbers (SSN) are an important element in the USA to identify a person and to be able to get certain services. Basic information about a person as well as a corresponding SSN make it easy to steal an identity. Subsequently the trade with SSN is rather popular. Those are sometimes offered as package deals with other documents such as passports or medical files.
In the European area, there’s nothing comparable. Identification documents are traded and sold. Oftentimes, these are just copies of documents. Or there are templates that offer to create fake identification at the click of a button. The buyers have to print it themselves, though. Crossing a border won’t be possible without hassle using these. Many online services, especially in the field of finances, require the sending of a picture of identification. With good copies, these services could be used under an assumed identity. Laundering money in small quantities is possible, as are other misdemeanours.
What stands out is that more concrete data of companies is on offer. This includes client data, internal documents and patents. These are rarely on the big markets, but in smaller circles they’re being exchanged. Also, there are reports that access to compromised systems is on sale. This indicates that there are not just external attackers that try to earn money off of these marketplaces – instead, corrupt administrators of affected systems sell access data. For an attacker wanting to penetrate and undermine a corporation, this is a good starting point. And oftentimes, this is a lot cheaper than to use own means to gain access. Professional hackers and qualitatively high-carat exploits can be much more expensive.
Exploits are pieces of software that automate the exploitation of a vulnerability partially or entirely. We use exploits in our work to prove the existence and extent of a vulnerability during security testing. The client receives a concrete image of what he can expect in which form from an exploitation.
The development of exploits is a lot of effort. There’s a lot of understanding for the vulnerability the exploit is based on needed. This makes it impossible to have a developer who doesn’t focus on IT security program the exploit. In addition to that, the exploit has to respect countermeasures and unique features of the target environment. These are primarily input validation and encoding of the target application. But this could include additional security measures such as anti-virus software and firewalling.
Due to this situation, a well-frequented exploit market has developed. On the marketplaces there are agitators with various backgrounds but similar goals:
Exploits are sometimes traded on the usual markets on the Darknet. In addition to those, there are specialized markets that have – for reasons speculated about – not been able to persist. This includes a marketplace named The Real Deal (TRD). It disappeared without a trace after a few short months of existence. Another few months later, it appeared again without a verifiable explanation for its lengthy disappearance. Press and industry representatives accuse the people running the site of an Exit Scam and to have escaped with the money of unfinished transactions.
Vulnerability brokers or direct transactions based on established relationships of trust make up a large part of this market.
The price of an exploit is influenced by several factors:
Based on market observations lasting several years we were able to develop a model to predict prices of exploits. We base our estimate on a 0-day Exploit whose existence and vulnerability are unknown. It is being sold only once and exclusively to one buyer until the vulnerability is public or an alternate exploit has been published. The price is also dependent on events such as the publication of the vulnerability or the availability of an alternate exploit or a patch as well as the temporal development. The following graphic illustrates some examples for price ranges of known software components.

Payment usually happens in several phases:
The market for exploits is growing exponentially. This affects the number of exploits available as well as the prices that are being paid these days for high-quality exploits. It’s predicted that the coming years will see prices that surpass the 1.5 million USD marker. We estimate the market volume for 0-day Exploits 2015 at 155 million USD. This is a 67% growth compared to 2014.
On the Darknet, there are very dubious and odd people. During our research, we’ve often encountered disturbing individuals or activities. Some situations are so exaggerated that their being real is doubted.
Over time, our analysts have developed a sense for which content could be real and which aren’t. Many sides or contents are only published to provoke a reaction. This is particularly evident in the field of contract killings. There are sites with structures and contents that are far off any market reality. However, they look exciting and are therefore preferred quoting material by journalists. We conclude that we’re dealing with a special kind of trolling.
Generally, there’s a large building of legend on the Darknet, so-called creepypasta. Fictitious or exaggerated stories are told over and over again and, with every iteration, the folklore of the Darknet gets expanded. There are incredibly brutal tales that might shake those who are easily offended. Especially because they might carry a kernel of truth in them – or in some cases end up being sad reality.
A typical example for the kind of myth building that happens on the Darknet is the so-called Red Room. There is the legend of a special chat room where logged in users can watch a live stream of a person being abused, injured or even killed. The participants in this snuff chat can influence the goings-on. There are various people reporting about Red Rooms. The stories are reminiscent of the movie Hostel but remain unconfirmed.
Many commercial offers have a fraudulent background. For example, many watch replicas are never delivered after the first instalment has been paid. A typical scam that isn’t just happening on the Darknet.
Arguably the most popular and most successful scam on the Darknet are Exit Scams. These happen when a marketplace is shut down without warning and the money that has been paid but the transactions have not been completed disappear as well. Many marketplaces offer an escrow service. They act as brokers and mediate when differences between buyer and seller arise. The buyer has to make a pre-payment to the marketplace. The marketplace’s escrow service only transfers the funds to the seller once the buyer verifies reception and quality of the product. Big marketplaces constantly handle large sums of money that disappear in an Exit Scam. The big advantage of this form of fraud is that the victims of it are highly unlikely to go to the police because they themselves are usually involved in illicit activity.
Often, it’s not possible to distinguish between Exit Scam and a marketplace having been raided by law enforcement. The effect for buyers is the same. Markets suddenly re-appear, sometimes even run by the same people. If it’s a continuation of the Exit Scam or a honeypot by law enforcement can’t be determined.
If a Bitcoin address is made public online tools such as BitRef can view the balance of the Bitcoin wallet. Using this method, market places and traders can be verified, at least when it comes to cash flow. Many areas on the Darknet can be revealed to be a fake this way.
Persecution on the Darknet is not an easy task. First, there’s the technological hurdle: The needs to provide infrastructure for surveillance and analysis in order to recognize illegal activity and to understand it. In addition to that, there needs to be understanding for the implemented mechanisms. Among them are:
These aspects can be brought under control. However, it is more difficult to persecute due to the inability to interact with target persons on a whim. In all places where illegal activity takes place, the people involved are very shy and discrete. Just striking up a conversation is not possible.
In order to get into conversations, a user needs to have built up a reputation and a relationship of trust to individuals. This costs a lot of time and effort. In addition to this, an investigator needs to be acquainted with the etiquette of the Darknet, speak the right language. This is easy for us in the area of exploits, because we develop, analyze and use exploits every day. We are familiar with the terminology, the technology and the background. In other areas, we find it much more difficult to find our way in.
Often, a user builds his or her own legend, a fictional persona with a completely invented life. In intelligence communities, the recommendation is to have as little variations to the persona’s inventor’s own life. The steady upkeep of a complex net of lies is cumbersome and prone to error. This is why legends are kept simple and authentic. Doing this, a user runs the risk of accidentally exposing too much about their real lives. It is a tightrope-walk between lies and truths. Depending on what circles a user is involved in, mistakes can have dire consequences.
The biggest hurdle for persecution is the legal system in and of itself. Investigations using false identities are either not allowed or are legal and social grey areas and heavily debated. In many areas, it is expected from buyers to prove their authenticity. When buying large amounts of credit cards, it’s required to show that a user is in possession of stolen credit cards already. Sellers know that law enforcement is not allowed to distribute stolen credit cards. If they enforce the buyers to show some to them, they can be certain that the buyer is legit. Similar mechanisms are employed when dealing drugs or child pornography.
If investigators are able to gather evidence, then requests for international legal aid have to be dealt with. They are time-consuming and often aren’t followed up on by the governmental agencies that are being requested to help. Especially in war zones and third world countries the priority for cases related to cybercrime is very low. Investigations often fizzle out.
The Darknet is a dedicated and often specially segregated area of the Internet. It offers platforms and services that are either very odd or even dubious.
Based on examples from markets trading in drugs, contract killings, weapons, data and exploits, we illustrated which peculiarities are encountered in these communities.
In order to navigate those communities with ease and without fault, the code of conduct of said communities needs to be respected. Only by following that code is it possible to establish users in a scene and build relationships of trust with agents in these. This takes time and effort.
This effect and the fact that technological understanding is required as well as the pushing of legal limitations, makes investigations and persecution on the Darknet very difficult. Therefore, it can’t be denied that the future of illegal activities on the Internet will be moved to the Darknet. Law enforcement must mobilize more resources in order to be able to meet the legal demands of this shadow economy.
We are going to monitor the digital underground for you!

Marc Ruef

Marc Ruef

Marc Ruef

Marc Ruef
Our experts will get in contact with you!