Security Testing
Tomaso Vasella

In my work as security consultant I’m involved in security architecture reviews and assessments. They are sometimes limited on single application other times it may involve the whole DMZ implementation or a complex framework. The goal is to evaluate the risks and propose strategies to mitigate them. But as in real life, seldom the analyzed assets are isolated from the environment. That’s why we need to define scopes to limit effort and costs, but sometimes it just doesn’t feel right. Imagine a security review/assessment of an application/service that is integrated within the Active Directory Services (ADS): How can I provide conclusive results without assessing the ADS architecture & concepts?
Unless you’re not on a complete non-Windows environment, you have to deal with ADS – In my 20+ years of Cybersecurity services I’ve seen very few environments that didn’t. ADS is almost omnipresent and plays a central role not only in authentication. My first question on such assessment usually is: “What happens when the ADS is down?” Most people answer that the ADS is redundant and high-available and in turn I say: “Well, I didn’t speak of server disruption, I meant – what if the AD is malfunctioning, corrupted or just not available – How will your business process be affected?” Usually at this stage most people realize the impact. The network may be up and running, the storage services available and even the virtual or physical infrastructure (VDI, servers, workstations) working and still you may not be able to access your workstation, check for your email.
The ADS is a critical target, by now you’ll agree that that the Cybersecurity posture of the ADS will affect any application or solution that relies on it, therefore we always suggest to also reviewing the ADS implementation for cybersecurity risks. Still, there is an issue: Normally an ADS assessment would require at least 5 days effort. You see the problem on hitting the budget.
Therefore we came with a different approach: Adapting the NIST Cybersecurity Framework for our Risk Assessment. The CSF approach is explained in this picture:
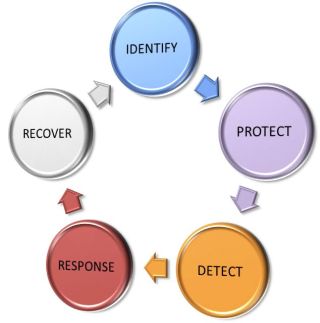
Security is a process: It starts with the identification of our critical assets and its related governance, going further to implementing controls to protect and detect cybersecurity events, and (to complete the cycle) you’ll need to have procedures and processes to respond during and recover after cybersecurity events. Our Rapid Risk Assessment is following this schema to establish information about the security controls available in each area and its maturity level.
To achieve the time-frame restriction the assessment is mainly based on interviews with ADS key stake holders and on automated information gathering (using scripted tools). Those steps should gave enough information to be analyzed and documented in 2 days.
Following categories will be of interest when assessing the Active Directory Security Controls:
| Category | Subcategories | CSF Area |
|---|---|---|
| Risk Assessment | Business Impact Analysis, Data Classification, Infrastructure Impact Analysis | IDENTIFY |
| Architecture Design | Topology, Forest, Domain, Site, DC, FSMO, DNS, Clients | IDENTIFY |
| Extended Services | Certificate, Federation, Rights Management (DRM) | IDENTIFY |
| Integration | Exchange, Skype (UC), Sharepoint, Hyper-V | IDENTIFY |
| Authentication | Local, Remote, Privileged | PROTECT |
| Administration | Local, Remote, Service Providers | PROTECT |
| Group Policies | Design, Testing, Operation | PROTECT |
| System Hardening | Baseline, Firewall, Integrity Check | PROTECT |
| Client Access | Local, Remote, Service Providers | PROTECT |
| Protocol Encryption | LDAP, Global Catalog, Kerberos, SMB | PROTECT |
| Life-Cycle | Patching, Change-Management, Backup | PROTECT |
| Logging & Audit | Policies, Collection, Archiving, Normalization | DETECTION |
| Monitoring | Network Monitoring, Intrusion Detection, Security Monitoring, Vulnerability Management | DETECTION |
| Incident Response Management | ADS Process & Procedures | RESPONSE |
| ADS Recovery | Object Restore, Function Restore, CA Certificate Restore, ADS Disaster Recovery | RECOVER |
The ADS assessment will analyze each category and report a risk level based of the information gathered during the process. Key effort of this approach is to understand the avenues for establishing a healthy ADS, implementing monitoring systems, reducing the attack surface and managing a resilient environment.
To give a rough figure of the required efforts, this table will give you a quick overview:
| Effort | What | Note |
|---|---|---|
| 3h | Interview with key stakeholders | Planned initial 2h interview – 1h as contingency and further clarification |
| 1h | Request for ADS configuration & documentation | Export GPO from DC & clients – Get available documentation |
| 4h | Automated AD information gathering | Requires a windows workstation with read privileges to the AD and a running PowerShell environment, to run our scripts |
| 4h | Data Analysis | Where the magic happens… ;) |
| 4h | Reporting | Fill the issues on a predefined Template |
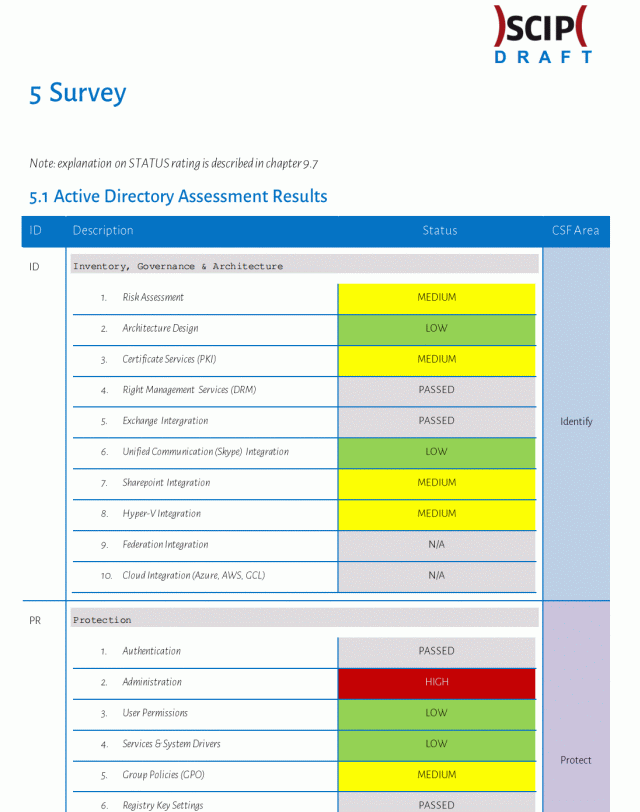
Now an overview on the deliverables, this is how the report may looks like in the overall survey matrix:
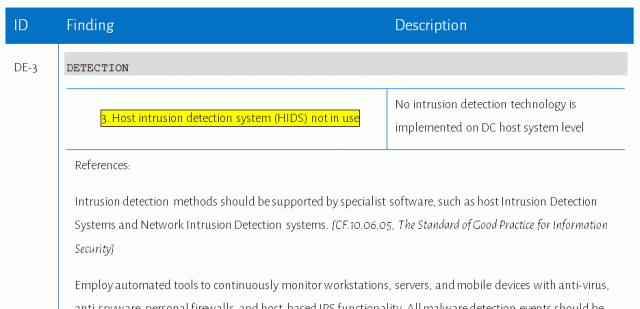
And this is how a finding may look like:
The Rapid Risk Assessment approach will not find all possible issues inside your ADS, but will surely point you in the right direction and highlight major gap that may harm your environment. Probably the final results would recommend investing more time in a specific category inspection, but at least you’ll spend precious time and resources in the most effective way.
Our experts will get in contact with you!

Tomaso Vasella

Eric Maurer

Marius Elmiger

Eric Maurer
Our experts will get in contact with you!