Security Testing
Tomaso Vasella

The recent election of Donald Trump as the 45th President of the United States has given Twitter, one of the older social networks to still be around, an unexpected boost: With Instagram Stories and Snapchat garnering a significant amount of approval from younger demographics, Twitter was losing relevance at a steady pace – but the frequent, unfiltered ranting of the newly elected POTUS brought the attention back, at least for now.
Even though the circumstances might be somewhat absurd, Twitter does deserve this boost. Few other social media outlets are so versatile regarding possible use cases, adoption throughout different industries and accessibility. Twitter manages to build bridges between people who might otherwise be unable to ever connect: Between consumers and brands, celebrities and fans, politicians and citizens. Twitter has been crucial as a tool to spread information during the Arab spring, its limited requirements regarding bandwidth being only one of the reasons.
However, using Twitter is not without risk. In a network that is, by design, intended to be fairly liberal regarding public sharing, taking precautions is essential.
Of course, the key piece of advice here should be Be mindful of what you share, advice often neglected by celebrities and soon-to-be-fired disgruntled employees venting alike. In 2013, a PR executive named Justine Sacco got on a long plane ride after sending the tweet “Going to Africa. Hope I don’t get AIDS. Just kidding. I’m white!” just to find herself out of a job upon landing. The tweet had taken off and caused global outrage. This case is thoroughly documented in Jon Ronson’s 2015 book So You’ve Been Publicly Shamed, along with other examples of bad jokes made publicly backfiring in a horrible way.
So with Do not post things that will get you fired out of the way, let us focus on the technical aspects of being safe on Twitter. There is a surprising amount of mechanisms attackers can use to gather data about their targets using Twitter or associated services. Some of them can be disabled by properly configuring your account, some of them are just to be acknowledged and kept in mind. The following paragraphs will mention some of the basic things to note.
Regular readers of our publications, or any security-relevant outlets, have read this before, but it bears repeating: Two-Factor Authentication is important, effective and moderately easy. Twitter does support verification by SMS and should be on for every single account. Alternately, a code generator app, such as Google Authenticator, can be used, but for most people SMS might be the simpler way to go, with limited drawbacks. It is possible to enroll multiple accounts to Login Verifications using the same phone number, so there are few excuses to not do it.
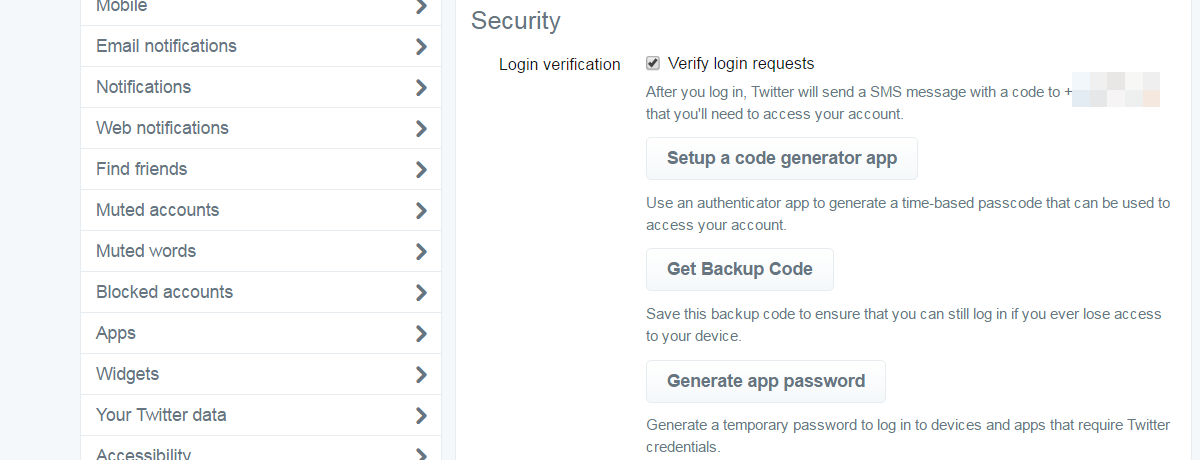
With login verifications enabled, an attacker should not be able to log into your account without also gaining access to your secondary authentication factor, your phone. So even if an attacker manages to successful phish your password (which is likely), you won’t be compromised immediately. This is particularly important for corporate Twitter accounts, which might otherwise be abused to launch attacks against its own followers or to post undesired content that will inevitable launch to considerable reputational damages.
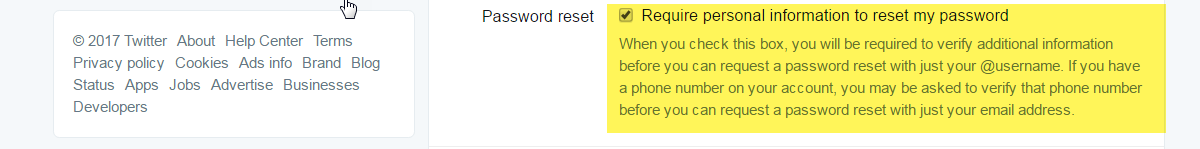
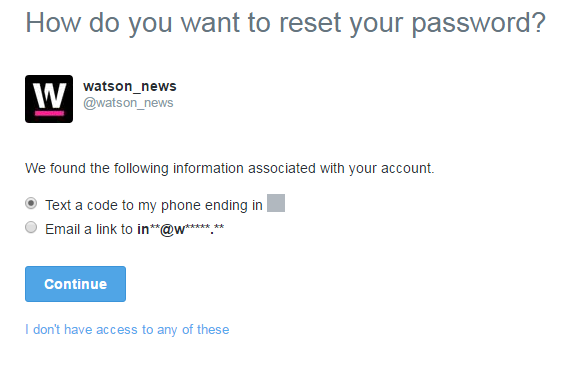
The setting Require personal information to reset my password should be activated for every and each account. Twitter requires accounts to be tied to a primary email address. It also encourages users to add a phone number, which is also crucial for the aforementioned login verifications to work. If this box is not checked in an account’s settings, it will lead to an undesirable information disclosure: When an attacker initiates the password reset for an account, Twitter will present options on the next steps to go through with the reset. This includes sending a text message or an email. In both cases, parts of the contact information are displayed, but redacted. In a lot of cases, a little bit of research and imagination can go a long way to piece together the actual email account associated with an account and even the two last digits of a cell phone number can be crucial in a social engineering scenario.
Here is an example: Our friends at Watson use, presumable, info@watson.ch to run their account @watson_news and have an unknown phone number, the last two numbers of which are displayed publicly, associated with the account. Especially the latter information is most likely not considered to be public, so it could likely be used by an attacker to lend credibility to the claim that he is, in fact, calling in an official capacity of the Twitter support, security or ads sales team.
A common, somewhat bold move used in such scenarios, is to flip the script on the victim and ask him to confirm a data set by querying him with the known bit of information:
Before we can proceed, I need to ask some quick authentication questions: Your account associated with info@watson.ch has a phone number ending with the digits XX. Can you please read out the entire phone number, digit by digit?
Not only does this establish credibility for the rest of the call, it already extracts an additional bit of information, the full phone number used for the account, from the victim.
There are numerous scenarios in which any information leakage can lead to follow-up attacks or other embarrassing moments. After Donald Trump took office, his administration took over the coveted @POTUS account after Barack Obama’s tweets were archived to the account @POTUS44. An observer used the functionality outlined above shortly after and was surprised to find that the Trump administration had linked the account to a Gmail address, leading to a significant amount of media coverage illustrating the irony of this practice considering earlier shots the campaign fired against their opponent, Hillary Clinton, and her usage of non-official email infrastructure.
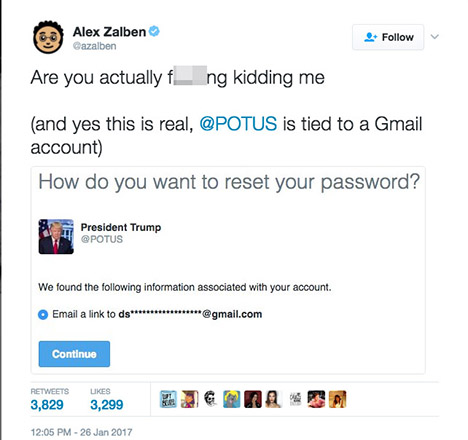
By securing password resets using the Require personal information to reset my password feature, the valid email and/or phone number must be provided by the inquirer to go on with the process, the available channels are not proactively offered by Twitter, so information leakage is prevented.
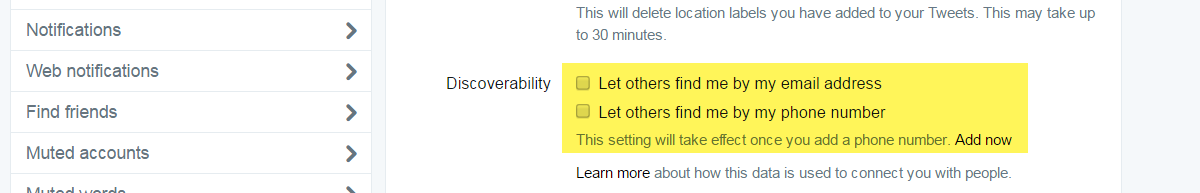
In addition to both of these measures, it is often advisable to use a dedicated, unpublished email address for social media accounts, such as smaccounts@yourdomain.com to set up your accounts and forwarding it to your main address. In theory, the same would apply to phone numbers, but practical reasons often outweigh the benefits of this option.
A tweet is way more than the maximal 140 characters of its content. The date and time a tweet is sent is public, as is the client used to send it. All these bits of information can be harvested and analyzed easily.
Taking a look at the past 5000 tweets of famous Swiss satirist Victor Giacobbo (@viktorgiacobbo) reveals a lot about his usage of Twitter. For example that he wrote 59% of his tweets using Twitter’s web client and another 28% using the app TweetCaster for Android, giving us a good idea on how and where he uses Twitter.
This leaves the aspect of time when tweets are being sent. Since neither TweetCaster nor Twitter’s web interface prominently offers the option to schedule tweets, unlike tools like Buffer or HootSuite, we can assume that tweets were composed and sent manually at the reported timestamp. If we analyze that dataset, we can see that tweets were sent almost exclusively between 7 am and 2 am. We also see a majority of tweets are being sent between 10 am and 2 pm, peaking over the lunch hours. An attacker could derive various conclusions from this: Maybe, Mr. Giacobbo likes to have a good night’s sleep and is easily distracted during lunch meetings. Maybe not. We do not want to engage in too much speculation of his personal life for the sake of this demonstration.
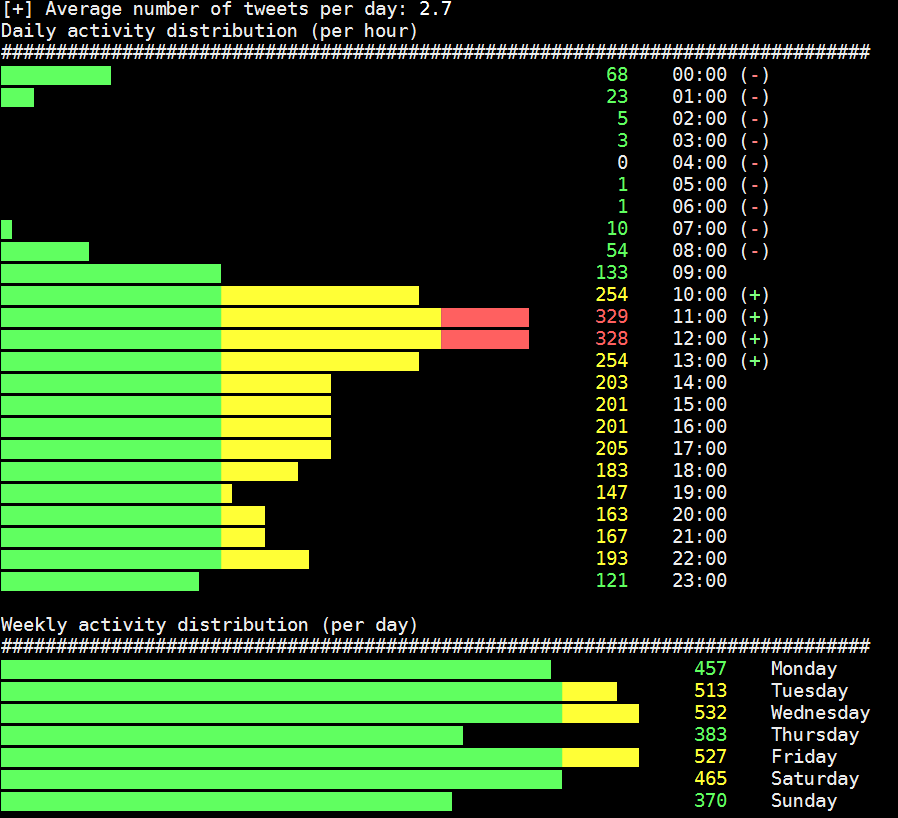
Again, all of this gives us information that might be useful in a social engineering context, but there is more: We also see that he sent 34 tweets using IFTTT, a popular automation tool that allows, for example, to automatically tweet new items from an RSS feed or a plethora of other sources. This directly implies that he has authorized IFTTT to access his Twitter account, most likely along with other tools he is using, which would give an attacker an excellent target to attack Mr. Giacobbo.
Acquiring and analyzing this data is trivial and has been implemented in the form of various tools over the years. tweets_analyzer by GitHub user x0rx is an excellent python utility also used in the screenshot above.
Defending against this type of analysis is non-trivial at best. A strategy that works quite well is to use a (comparably expensive) tool like Hootsuite or Buffer to draft, schedule and send all tweets. Since the respective platforms will send the tweets at a pre-defined, but non real-time point in time and will use a non-specific client name, the dataset will be obscured to a certain degree, making analysis harder. But even these measures will only defy basic analysis. More sophisticated approaches include linguistic analysis of the actual tweet content and cannot be mitigated for obvious reasons.
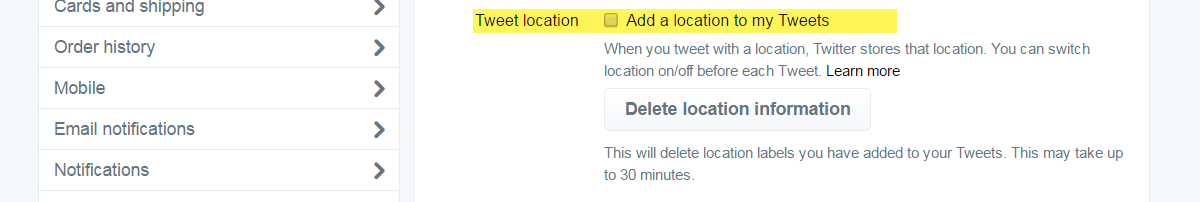
While metadata is hard to eliminate, geotagging on Twitter is a choice. In a nutshell, geotagging allows a user to embed the location where a tweet is sent from into the tweet, making it easier for people in the area to see tweets nearby. Obviously, sharing your location can be dangerous, much depending on who you are and what your personal risk situation looks like. Generally, it is considered a wise solution to turn geotagging off for general usage.
Twitter allows external application to interface with an account directly by authorizing them permanently. It is what happens when you connect your Instagram account to a Twitter account in order to share pictures directly to your timeline. And it is this type of interface the aforementioned IFTTT requires in order to be able to post automated messsages on behalf of a user.
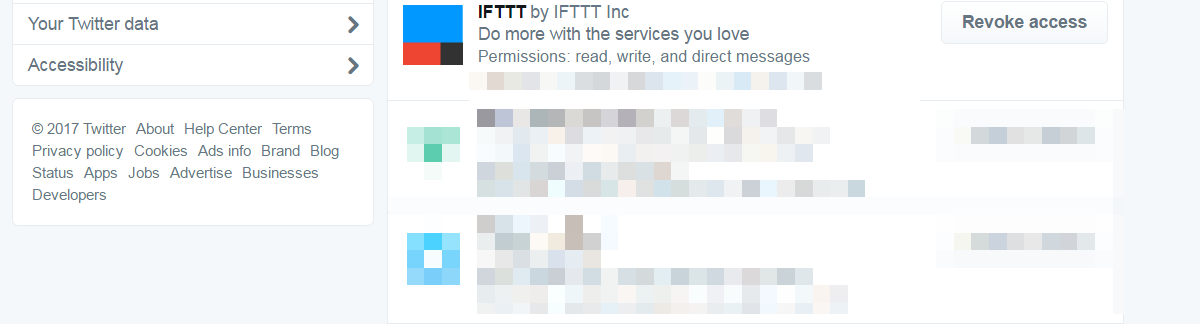
This functionality, while highly useful, has its own set of risks. For example, a lot of Twitter-specific apps such as Fake Follower Checks will be used at a point in time, but probably never again afterwards. Yet, the authorization for this application remains intact indefinitely until it is revoked by the user.
Just a few weeks ago, a large number of popular accounts were tweeting Turkish extremist content after the application Twitter Counter was compromised. Based on the access tokens granted to Twitter Counter, the attackers were able to post tweets to all of the affected accounts, spreading questionable content on accounts belonging to UNICEF, the BBC, Forbes and a large number of other influential organizations and individuals.
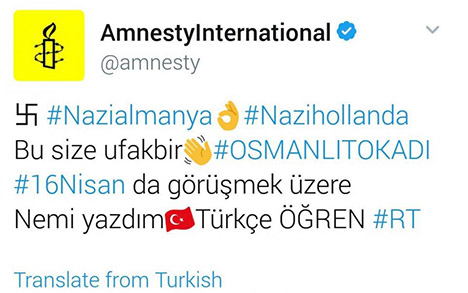
While using applications that require authorization of your Twitter account is not inherently bad – some of them are really useful -, the awareness that you are giving significant amounts of control over your account to these application is essential. It is highly recommended that you check the list of applications with these privileges frequently and revoke privileges where they no longer are required.
Twitter offers the option to protect your tweets and share them only with approved followers. It counteracts the inherent purpose of Twitter, which includes the public aspect of what is being written, but it is an option to keep a certain amount of control about who gets to see your content. While it might be a better option to just not tweet at all under these circumstances, it might be an option for people who just want to share non-critical information with a limited user group.
Considering that Twitter is, for a lot of people, a casual tool to communicate, it offers a lot of options to potential attackers to gather information and to identify target assets. While these are highly dependent on the behavior of the single user, it’s worth noting that being aware of these possibilities goes a long way towards acting in a safer way. Implementing the measures outlined in this text will not magically mitigate all problems, but it will make it harder for an attacker to gain significant information easily and make your Twitter experience a bit more secure.
We are going to monitor the digital underground for you!

Tomaso Vasella

Eric Maurer

Marius Elmiger

Eric Maurer
Our experts will get in contact with you!