Transition to OpenSearch
Rocco Gagliardi

This article is an update to the prior one Docker – Continuous Build Security Assessment. In addition to the tools listed in that lab, in the last few months, we made some experience with another tool: Anchore
Anchore is a tool that provides visibility in the Docker container’s world. It can analyze, scan, or inspect the Docker image manually or through automation. It is possible to integrate this tool within a CD/CI pipeline, configure security toll-gates for each build, and leave them allowing, warning, or blocking the pipeline automatically.
Anchore is available as Docker image; just follow this guide to prepare the environment.
Anchore can be used interactively for container’s analysis purposes. We will see how to use Anchore to:
Let’s take a look at the images present on the system:
[root@tst-jenkins-01 nodejs-jendoc-01]# docker images REPOSITORY TAG IMAGE ID CREATED SIZE ... alpine-nikto-01 16251627082017 91e011e8e68d 5 weeks ago 56.1MB nikto latest 91e011e8e68d 5 weeks ago 56.1MB ... anchore/jenkins 1.1.2 37324139ce3e 6 months ago 325MB citizenstig/dvwa latest c8312743bc09 2 years ago 478MB
We will analyse the images:
The first is an ad-hoc created image running the Nikto scanner. The second is a publicly available image exposing many vulnerabilities, normally used for testing purposes.
We start with the analysis of alpine-nikto-01:
[root@tst-jenkins-01 nodejs-jendoc-01]# anchore analyze --image 91e011e8e68d Analyzing image: 91e011e8e68d 7328f6f8b418: analyzing ... 7328f6f8b418: analyzed. 91e011e8e68d: analyzing ... 91e011e8e68d: analyzed.
Once analyzed, we are ready to query some information and create a report:
[root@tst-jenkins-01 nodejs-jendoc-01]# anchore audit --image 91e011e8e68d report +--------------+------+----------------------+----------------------+-------------+-------------+--------------------+--------------------+ | Image Id | Type | Current Tags | All Tags | Gate Status | Size(bytes) | Counts | Base Diffs | +--------------+------+----------------------+----------------------+-------------+-------------+--------------------+--------------------+ | 91e011e8e68d | None | alpine-nikto-01:1625 | alpine-nikto-01:1625 | UNKNOWN | 56079797 | PKGS=21 FILES=2720 | PKGS=10 FILES=2247 | | | | 1627082017,nikto:lat | 1627082017,nikto:lat | | | SUIDFILES=0 | SUIDFILES=N/A | | | | est | est | | | | | +--------------+------+----------------------+----------------------+-------------+-------------+--------------------+--------------------+ [root@tst-jenkins-01 nodejs-jendoc-01]# anchore query --image 91e011e8e68d show-distro all +--------------+--------------+--------+---------+ | Image Id | Repo Tag | Distro | Version | +--------------+--------------+--------+---------+ | 91e011e8e68d | nikto:latest | alpine | 3.6.2 | +--------------+--------------+--------+---------+
We can extract some information, like the Dockerfile and the packages installed:
[root@tst-jenkins-01 nodejs-jendoc-01]# anchore query --image 91e011e8e68d show-dockerfile all +--------------+--------------+---------+-------------------------------------------+ | Image Id | Repo Tags | Mode | Dockerfile Line | +--------------+--------------+---------+-------------------------------------------+ | 91e011e8e68d | nikto:latest | Guessed | FROM scratch | | 91e011e8e68d | nikto:latest | Guessed | ADD file:4583e12bf5caec40b861a3409f2a1624 | | | | | c3f3556cc457edb99c9707f00e779e45 in / | | 91e011e8e68d | nikto:latest | Guessed | CMD ["/bin/sh"] | | 91e011e8e68d | nikto:latest | Guessed | LABEL maintainer=Rocco Gagliardi | | | | | mail=roga@scip.ch web=https://www.scip.ch | | | | | version=20170813 description=Nikto | | | | | scanner based on Alpine 3.6. Supports SSL | | | | | scanning. Runs with unprivileged user | | | | | 'nikto'. | | 91e011e8e68d | nikto:latest | Guessed | RUN /bin/sh -c apk update && apk add | | | | | --no-cache nikto perl perl-net-ssleay ca- | | | | | certificates && rm -f /tmp/* | | | | | /etc/apk/cache/* && mkdir /work && | | | | | adduser -D -s /bin/sh nikto nikto && | | | | | chown -R nikto /work | | 91e011e8e68d | nikto:latest | Guessed | USER [nikto] | | 91e011e8e68d | nikto:latest | Guessed | VOLUME [/work] | | 91e011e8e68d | nikto:latest | Guessed | WORKDIR /opt/nikto | | 91e011e8e68d | nikto:latest | Guessed | ENTRYPOINT ["nikto.pl"] | | 91e011e8e68d | nikto:latest | Guessed | CMD ["-h"] | +--------------+--------------+---------+-------------------------------------------+ [root@tst-jenkins-01 Anchore_policy]# anchore query --image 91e011e8e68d list-packages all +--------------+--------------+-----------------------+-------------+ | Image Id | Repo Tags | Package | Version | +--------------+--------------+-----------------------+-------------+ | 91e011e8e68d | nikto:latest | busybox | 1.26.2-r5 | | 91e011e8e68d | nikto:latest | libressl | 2.5.5-r0 | | 91e011e8e68d | nikto:latest | libpcap | 1.8.1-r0 | | 91e011e8e68d | nikto:latest | libc-utils | 0.7.1-r0 | | 91e011e8e68d | nikto:latest | musl | 1.1.16-r10 | | 91e011e8e68d | nikto:latest | nmap | 7.40-r1 | | 91e011e8e68d | nikto:latest | musl-utils | 1.1.16-r10 | | 91e011e8e68d | nikto:latest | zlib | 1.2.11-r0 | | 91e011e8e68d | nikto:latest | perl-net-ssleay | 1.81-r1 | | 91e011e8e68d | nikto:latest | libressl2.5-libssl | 2.5.4-r0 | | 91e011e8e68d | nikto:latest | perl | 5.24.1-r2 | | 91e011e8e68d | nikto:latest | libstdc++ | 6.3.0-r4 | | 91e011e8e68d | nikto:latest | ca-certificates | 20161130-r2 | | 91e011e8e68d | nikto:latest | alpine-keys | 2.1-r1 | | 91e011e8e68d | nikto:latest | libgcc | 6.3.0-r4 | | 91e011e8e68d | nikto:latest | libressl2.5-libcrypto | 2.5.4-r0 | | 91e011e8e68d | nikto:latest | alpine-baselayout | 3.0.4-r0 | | 91e011e8e68d | nikto:latest | apk-tools | 2.7.2-r0 | | 91e011e8e68d | nikto:latest | scanelf | 1.2.2-r0 | | 91e011e8e68d | nikto:latest | libressl2.5-libtls | 2.5.5-r0 | | 91e011e8e68d | nikto:latest | nikto | 2.1.5-r2 | +--------------+--------------+-----------------------+-------------+
We can also check if a specific package is installed:
[root@tst-jenkins-01 Anchore_policy]# anchore query --image 91e011e8e68d has-package wget +----------+----------+-------------+---------+---------+ | Image Id | Repo Tag | Query Param | Package | Version | +----------+----------+-------------+---------+---------+ +----------+----------+-------------+---------+---------+ [root@tst-jenkins-01 Anchore_policy]# anchore query --image 91e011e8e68d has-package libgcc +--------------+--------------+-------------+---------+----------+ | Image Id | Repo Tag | Query Param | Package | Version | +--------------+--------------+-------------+---------+----------+ | 91e011e8e68d | nikto:latest | libgcc | libgcc | 6.3.0-r4 | +--------------+--------------+-------------+---------+----------+
To get the list of available queries or the specific tools to inspect the images, use:
[root@tst-jenkins-01 admin]# anchore query [root@tst-jenkins-01 admin]# anchore toolbox
The interactive inspection of the image may be useful in case of debugging, forensic analysis, or just to look inside the image.
Finally, we can scan the image for known vulnerabilities. In order to CVE scan images, the first step is to update the feeds:
[admin@tst-jenkins-01 nodejs-jendoc-01]$ anchore feeds sync
syncing data for subscribed feed (vulnerabilities) ...
syncing group data: debian:unstable: ...
syncing group data: ubuntu:16.04: …
...Once the feeds are updated, we can restart the analysis of the images:
[root@tst-jenkins-01 nodejs-jendoc-01]# anchore analyze --image 91e011e8e68d Analyzing image: 91e011e8e68d 7328f6f8b418: analyzing ... 7328f6f8b418: analyzed. 91e011e8e68d: analyzing ... 91e011e8e68d: analyzed.
Then we can query the Anchore database about CVE vulnerabilities found:
[root@tst-jenkins-01 nodejs-jendoc-01]# anchore query --image 91e011e8e68d cve-scan all +--------+----------+-----------------+--------------------+---------------+------------+----------------+-----+ | CVE ID | Severity | *Total Affected | Vulnerable Package | Fix Available | Fix Images | Rebuild Images | URL | +--------+----------+-----------------+--------------------+---------------+------------+----------------+-----+ +--------+----------+-----------------+--------------------+---------------+------------+----------------+-----+
The alpine-nikto-01 looks pretty good: no vulnerabilities.
We can now analyze the second image, the vulnerable one. We start the scan for CVE High vulnerabilities:
[root@tst-jenkins-01 nodejs-jendoc-01]# anchore analyze --image c8312743bc09 ... [root@tst-jenkins-01 ~]# anchore query --image c8312743bc09 cve-scan High +------------------+----------+-----------------+---------------------+--------------------+---------------------+----------------+---------------------+ | CVE ID | Severity | *Total Affected | Vulnerable Package | Fix Available | Fix Images | Rebuild Images | URL | +------------------+----------+-----------------+---------------------+--------------------+---------------------+----------------+---------------------+ | CVE-2017-1000367 | High | 1 | sudo-1.8.9p5-1ubunt | 1.8.9p5-1ubuntu1.4 | c8312743bc09(citize | None | http://people.ubunt | | | | | u1 | | nstig/dvwa:latest) | | u.com/~ubuntu-secur | | | | | | | | | ity/cve/CVE-2017-10 | | | | | | | | | 00367 | | CVE-2016-6313 | High | 1 | libgcrypt11-1.5.3-2 | 1.5.3-2ubuntu4.4 | c8312743bc09(citize | None | http://people.ubunt | | | | | ubuntu4 | | nstig/dvwa:latest) | | u.com/~ubuntu-secur | ...
Anchore, in this case, finds multiple HIGH vulnerabilities. We can repeat separate scans for MEDIUM and LOW or scan for ALL and get the complete list.
Aside from the interactivity, Anchore can be executed as part of an automation process. A specific policy must be passed, in order to define which check must be performed and what should happen in case of OK, WARN, or STOP.
Anchore provides a policy-based mechanism to define the checks and the actions. The policy has the following format:
Gate name : Trigger : Action : Optional Parameters
Where the Gate and Triggers are the checks, the Action is the action, Parameters are specific for Gate/Triggers. To get the complete list of gates, triggers and options, use the following commands:
[root@tst-jenkins-01 Anchore_policy]# anchore gate --show-policytemplate [root@tst-jenkins-01 Anchore_policy]# anchore gate --show-gatehelp
Basically, the gates can be grouped in the following areas:
| Control’s area | Gates |
|---|---|
| Vulnerability | ANCHORESEC |
| Dockerfile | DOCKERFILECHECK |
| Inspection | IMAGECHECK, FILECHECK, FILEPARSE_PASSWD, SUIDDIFF |
| Libraries | GEMCHECK, NPMCHECK |
| License | LICBLACKLIST |
| Packages | PKGBLACKLIST, PKGCHECK, PKGDIFF |
For each gate, many triggers are defined.
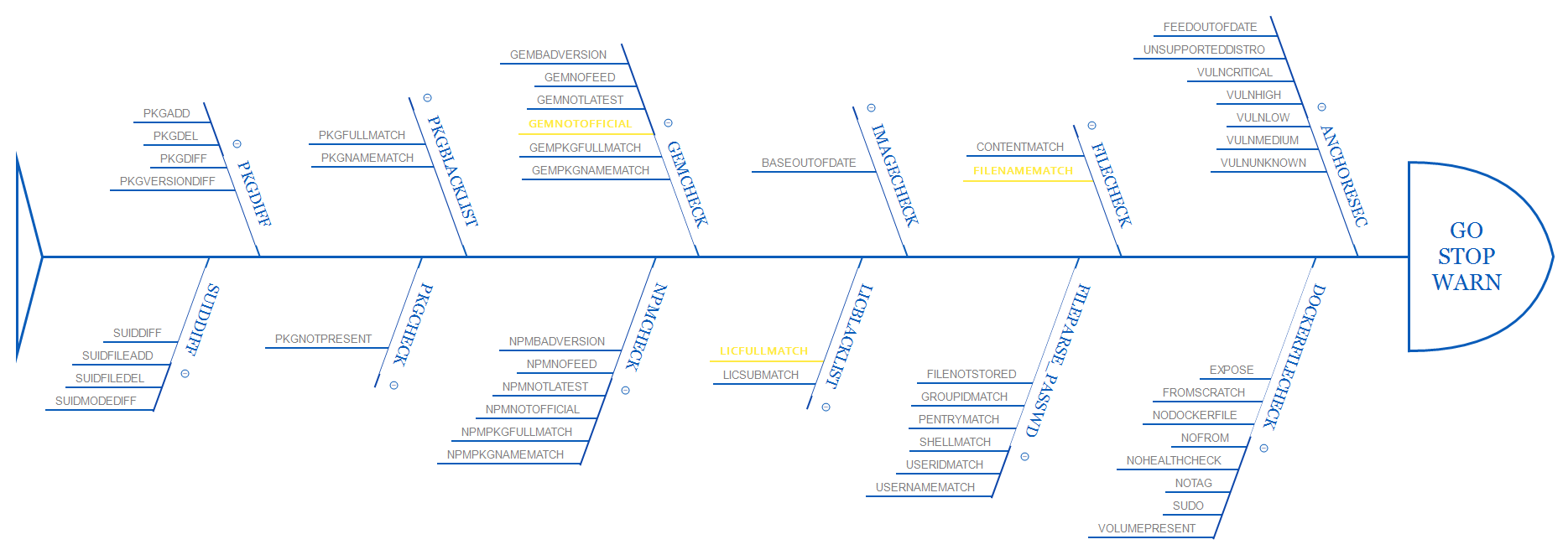
With all this Gates/Triggers, we can define a very granular policy to assess and – if required – stop the image deployment process.
In the next example, we define a policy that:
Note the FINAL state: STOP.
[root@tst-jenkins-01 Anchore_policy]# cat policy-nikto-01.pol DOCKERFILECHECK:VOLUMEPRESENT:WARN PKGBLACKLIST:PKGNAMEMATCH:STOP:BLACKLIST_NAMEMATCH=perl-net-ssleay [root@tst-jenkins-01 Anchore_policy]# anchore gate --policy policy-nikto-01.pol --image 91e011e8e68d 91e011e8e68d4d2822d353d3091de98fa3a9048a84337031b11228682ed9a8ab: evaluating policies... 91e011e8e68d4d2822d353d3091de98fa3a9048a84337031b11228682ed9a8ab: evaluated. 91e011e8e68d: evaluated. +--------------+--------------+-----------------+---------------+-------------------------+-------------+ | Image Id | Repo Tag | Gate | Trigger | Check Output | Gate Action | +--------------+--------------+-----------------+---------------+-------------------------+-------------+ | 91e011e8e68d | nikto:latest | DOCKERFILECHECK | VOLUMEPRESENT | Dockerfile contains a | WARN | | | | | | VOLUME line: VOLUME | | | | | | | [/work] | | | 91e011e8e68d | nikto:latest | PKGBLACKLIST | PKGNAMEMATCH | Package is blacklisted: | STOP | | | | | | perl-net-ssleay | | | 91e011e8e68d | nikto:latest | FINAL | FINAL | | STOP | +--------------+--------------+-----------------+---------------+-------------------------+-------------+
In this case, there is no interactivity required: once the policy is defined, a job can assess the image and react accordingly.
For integration in CD/CI pipelines, Anchore is available as Jenkins plugin.
The Anchore Jenkins plugin enables Jenkins users the ability to add a build step to a Jenkins job that automates the process of running an Anchore analysis, evaluating custom Anchore policies against images, and performing image Anchore security scans.
Following steps are performed:
STOP action.Anchore has become my favorite tool to assess Docker images. The open-source version is highly customizable and (re-)usable for different tasks, ranging from CD/CI control gate, to forensic analysis or to inspection/debugger tool: it is a must for every container’s user.
Our experts will get in contact with you!

Rocco Gagliardi

Rocco Gagliardi

Rocco Gagliardi

Rocco Gagliardi
Our experts will get in contact with you!