Security Testing
Tomaso Vasella

This is how you handle Sextortion
Sextortion is a portmanteau derived from the words sex and extortion. It defines the act of creating pressure on a victim by using aspects of sexuality as leverage. Often, criminals threaten the victim with being exposed to public shaming for not paying a fee to make their threats going away.
Recently there was a worldwide wave of sextortion that involved a form of credential stuffing. This means that real passwords gathered from past breaches were used to lend credibility to the threats. The entire thing was fake. But it was successful enough because a lot of people have a limited amount of passwords, so knowing one password (or, sadly, even THE one password) is credible.
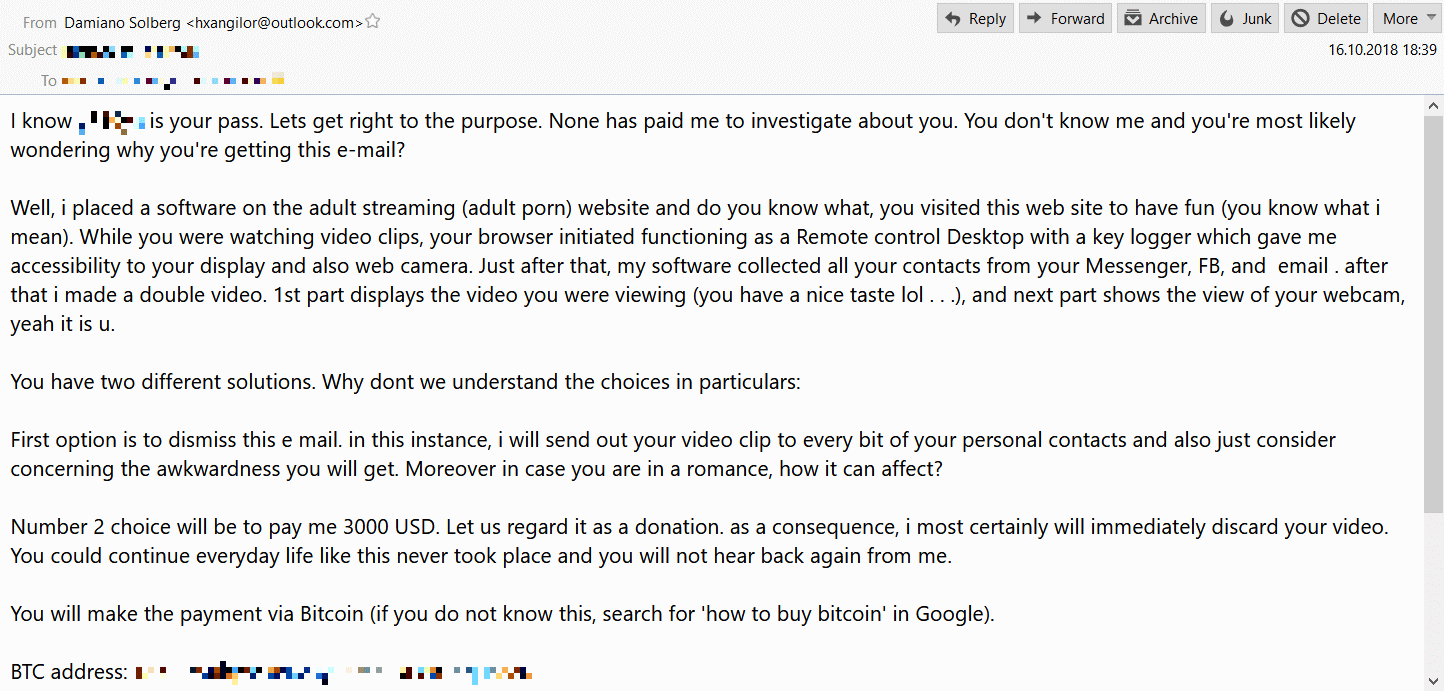
That is the short version. Now let’s unpack Sextortion a bit more in depth.
In a nutshell, sextortion works because sexuality is still something a large part of the population treats as something private, sometimes even dirty or shameful. This notion rings especially true for the consumption of Internet pornography. Yet, probably a surprise to no one reading this, explicit material is highly prevalent on the web. Pornhub registered 28.5 billion visits from every possible continent in 2017 and served an average of 118 GB of adult content per second. Yes, you read that right: While you were reading this sentence, Pornhub probably served about a terabyte of porn.
Even if the popularity of adult content is an open secret in a lot of places, the stigma associated with it is still ingrained in most of the population. And this is exactly where criminals use sextortion to make bank.
We have to distinguish two forms of sextortion: Actual sextortion and sextortion scams. They differ in one specific aspect: In cases of actual sextortion, there is real compromising material that has been acquired either from breaking into the victim’s data storage, such as iCloud or Dropbox. Or by tricking the user into creating and sending such material directly to the criminals, usually by posing as an attractive potential sexual companion in a video chat or on an instant messenger.
Sextortion scams are the more prevalent type more recently. Essentially, this is a mixture of very mundane spam emails, mixed with assumptions about the target group, occasionally with a dash of credential stuffing. The victim will receive an email informing him that his device was backdoored and that he has been observed and recorded enjoying a porn site. To give this claim credibility, the criminals will often include passwords disclosed in previous breaches (such as the Adobe or Dropbox incidents) as well as a tight deadline to make a payment to make this threat go away. The effectiveness of this type of scam depends on a variety of questions:
The likelihood of the victim being terrified and willing to pay is increased with every Yes answer to the questions above. The same is true for real sextortion cases where the victim knows very well that they have exposed themselves to this threat and now seeks a way out. That being said, when compromising material is available to the threatening party, the situation becomes significantly more tricky. It is, however, important to keep in mind that, no matter what the leverage might be and where it originates from, that the victim is, at this point, not to blame for being extorted. Yes, bad judgment might have led to this unfortunate situation, but it is the extortionist who is committing the crime at this point.
According to the Swiss news outlet Watson, 161 cases of sextortion were reported in the previous year. The Swiss Federal Police (fedpol) states clearly that putting pressure on a victim and extorting them with sensitive material will be pursued and punished as a serious crime.
The internet has given the risk of exposure to the public a completely new order of magnitude. In his book So you’ve been publicly shamed, author Jon Ronson illustrates at length how Internet Justice scales very heavily to a degree where a single person can be overwhelmed with ridicule and threats. In most cases, being exposed to full-scale public shaming is some of the most extreme forms of negative feedback modern society knows.
That’s the bad news. On the bright side: Spreading sensitive material to a degree where it goes viral is not easy, even reaching a critical mass of people in the victim’s social circle would be a laborious task for an extortionist. Especially in cases where threats are somewhat unspecific and potentially without merit, they are just that: Threats, aimed at the insecure, weak target that would rather pay than to see what actually happens.
This obviously rings true in particular for sextortion scams, wherein the majority of cases, there simply is no compromising material. These attacks, using passwords from previous dumps and threatening users with consequences on a short timeline are nothing but smoke and mirrors. And as such, they can and should be ignored.
That being said: If you are directly threatened, especially in a targeted and personalized way, go to the police. Don’t become a victim, get help and fight back.
Our experts will get in contact with you!

Tomaso Vasella

Eric Maurer

Marius Elmiger

Eric Maurer
Our experts will get in contact with you!