Keypoints
This is how cybercriminals break into your home
- Among the grand visions promised by the IoT are smart buildings and smart homes
- Electronic sensors are designed so automatisms can behave proactively and reactively
- This can include adaptive adjustments to the ventilation system or shades
- When designing and implementing smart buildings, cybersecurity must be considered from the outset
- In the future, building IT engineers will offer an important professional service when it comes to safeguarding homes against virtual and physical attack
The Internet of Things (IoT), along with all its pros and cons, has been a topic of discussion for years now. These discussions have focused on specific devices and device types. But what often gets ignored is that smart buildings and smart homes have already been around for a long time in the form of electronically controlled and networked buildings. This article discusses the effect future developments will have on the way we live and the impact they will have on digital security.
What are Smart Buildings?
Smart buildings or smart homes are buildings equipped with electronic sensors and networking functions to offer a maximum level of comfort and efficiency. The data collected by the sensors is used to react to dynamic situations. When the weather changes, the heating can be adjusted (heating curve), or lights and ventilation can be turned on when someone enters a room.
This dynamism requires that the sensors deliver accurate data and are able to transmit and process this data freely so that the proper action can be performed.
A hacker can exploit these dynamics, for example, by profiling the inhabitants and their habits for the purpose of planning a break-in. Compromised devices can make this sort of spying easier. Criminals can also use manipulation for purposes of extortion, threatening occupants with damage in order to get what they want.

Building with a Focus on Cybersecurity
Because smart buildings have led to more complex networking requirements, it is becoming increasingly important to consider cybersecurity aspects during planning, construction and management. In the future, this will be a major aspect of the still relatively new field of building informatics (GIN).
The association Bauen digital Schweiz has formed a focus group to study this very topic. The Netzwerk Digital network convenes regularly to coordinate projects among its various members. Members include SIA (regulatory), CRB (standardization) and KBOB/IPB (public and private building developers).
Bauen digital Schweiz is also a member of buildingSMART International, an international organization that deals with new and ongoing developments in the field of smart buildings.
Cybersecurity for building IT Engineers
Building informatics is a highly multifaceted profession. On the one hand, it includes traditional aspects, such as energy utility installation. This includes modern technologies like solar power, smart meters and heating, ventilation systems, air conditioning, blinds, etc. Even here security is not a foreign concept, as access and gate control systems, alarm systems, video surveillance, etc. are just as important.
Obviously, intruders can make a lot of headway by manipulating these elements. So it is essential to protect the individual components and their integration into the network:
- End devices: End devices must be securely configured and hardened. It is also important to make sure the latest updates and patches are installed. If there are no official procedures in place you will need to take a complementary approach. Keeping a device secure over a longer period of time or, in other words, beyond the lifecycle guaranteed by the manufacturer can be very complex.
- Communication: Communication with devices must be secure, which begins with secure wiring or setting up a protected wireless connection (shielding). Traditional networking concepts, such as segmentation and firewalling must be taken into account as well in order to safeguard a building’s internal network. Fortunately, there are decades of networking experience to fall back on. However, these are of little use if they are not applied consistently from the outset.
It is important to remember cybersecurity starts with the design of the building. As with conventional computer and network security, it is considerably more difficult to retrofit security than simply doing it right to begin with. Performing upgrades after the fact always involves additional technical construction and costs.
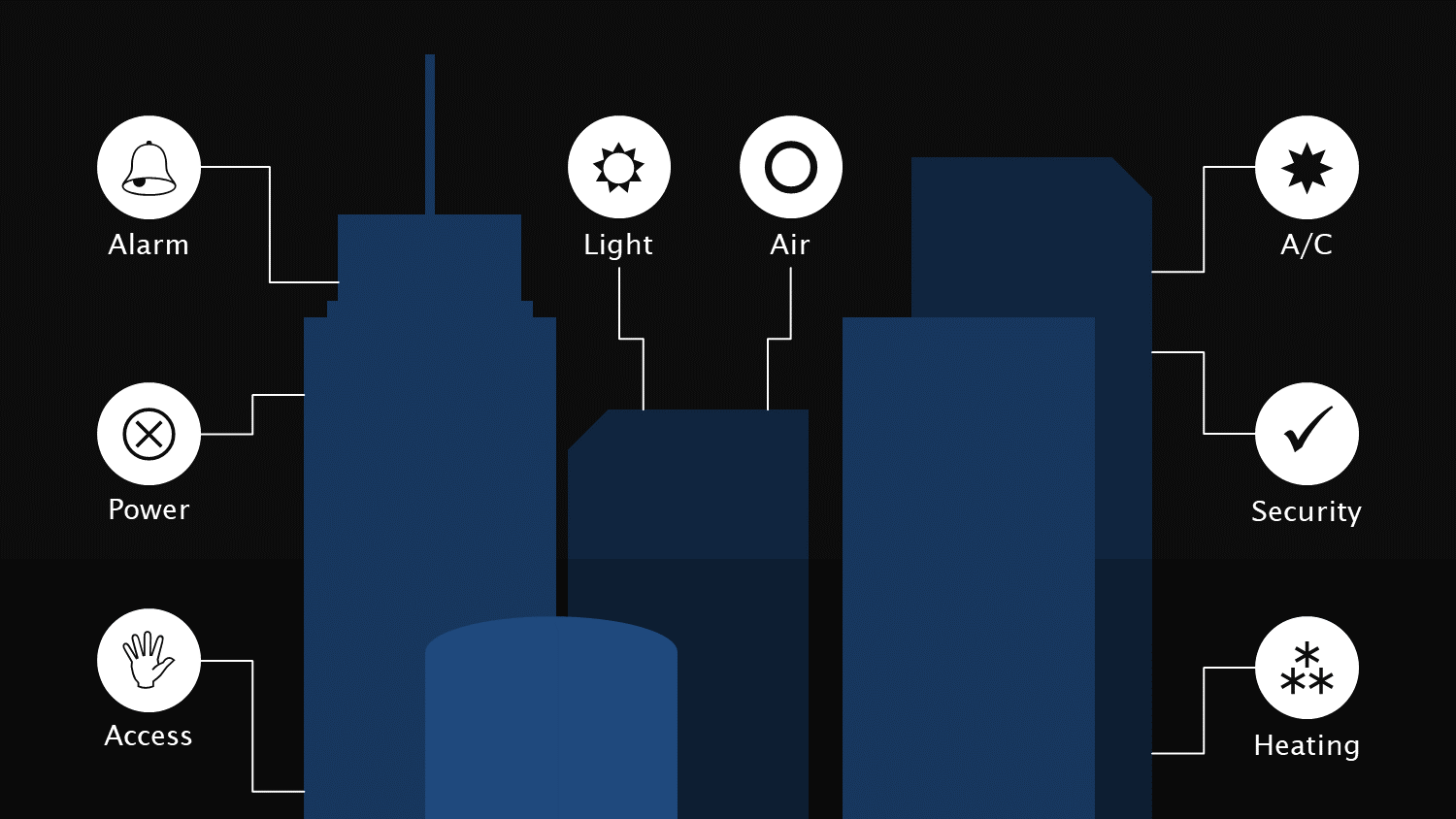
Devices and their Risks
A variety of device classes are used in smart buildings, and each is associated with its own unique risks. These include:
- Physical access: Modern access systems can be programmed centrally, which requires a sophisticated authorization concept that defines who has access to what areas. A faulty authorization concept can end up granting more privileges than necessary to a certain user.
- Alarm: Alarm systems must be able to access sensor data in order to detect suspicious activities (such as opening doors, broken glass, motion). The communication between sensors and the base station must be secured to prevent tampering.
- Heating, ventilation, air conditioning: Networked heating, ventilation and air conditioning systems also rely on sensors to enable dynamic responses. An error in data collection and transfer can have unpleasant or even harmful outcomes. If an outdoor sensor (thermostat) shows an extremely low temperature, a steep heating curve can consume large capacities or cause overloading (in the compressor, for instance) and excessive heating. The latter example can damage parquet flooring, for example. At worst, it could cause a fire.
- Power: Having smart meters dynamically monitor power consumption can help energy suppliers adjust the flow of power to the grid. In turn, this allows them to them offer flexible pricing models. Hackers can exploit this statistical data to identify and respond to activities in a building (e.g. break-ins during holiday absences). Electronic systems can be manipulated as well, potentially resulting in power outages and service interruptions.
- IoT devices: Various companies have started to network their devices (refrigerator, ovens, coffee makers, etc.), so that they can be monitored and controlled over the network.
- Smart home gateways and servers: Older, non-networked devices that are still in use can sometimes be upgraded with smart home gateways. For example, conventional lamps can be controlled over the network, or heating can be turned down temporarily when a window is opened.
Many providers of these solutions rely on cloud-based mechanisms to provide convenient, user-friendly interfaces for controlling them. This cloud connection is a key part of the solution, and safeguarding it (or at least performing a risk assessment) is essential.
Conclusion
IoT is not a brand-new topic. But in some areas awareness of IoT is only just beginning. In the field of medical technology it has become clear that cybersecurity is now a central issue. This awareness must now be extended to smart buildings. Networked buildings and devices can be exploited and, at worst, cause real damage.
Yet with all of these new possibilities, the question still remains:
Is a given function really necessary?
The risk associated with manipulation of a heating system may outweigh the advantage of being able to control it over the Internet. If so, this sort of integration might be best avoided.
About the Author
Marc Ruef has been working in information security since the late 1990s. He is well-known for his many publications and books. The last one called The Art of Penetration Testing is discussing security testing in detail. He is a lecturer at several faculties, like ETH, HWZ, HSLU and IKF. (ORCID 0000-0002-1328-6357)
Links






