Keypoints
This is how to use Web-Shell
- Shells are malicious scripts for remote access via command line
- Attackers interact with their web shells via the browser
- The web shell must fit the target host in terms of size and technology
- To avoid third-party access, web shells should have authentication
Already as a small boy I was fascinated by shells of all kinds. I could spend hours on the beach looking for the most beautiful shell. I never would have thought that this would also grab me again later as an adult, even if in a slightly different way. But now I sit here and look for the right shell for my current target.
A command shell is a malicious script that allows an attacker to remotely access the target system as a command line. However, a shell is not suitable for the first attack step, but is only used if a web application/server has already been compromised. So once the attacker has access to the web application/server, be it through an SQL injection, remote file inclusion, social engineering attack or other attack techniques, he uploads a suitable shell to gain long-term access. A web shell is a special type of shell that uses the browser to interact with the shell. As long as a web shell remains undetected on the server, the attacker can always connect to the system. Besides web shells, there are other types of shells.
Overview of Different Shells
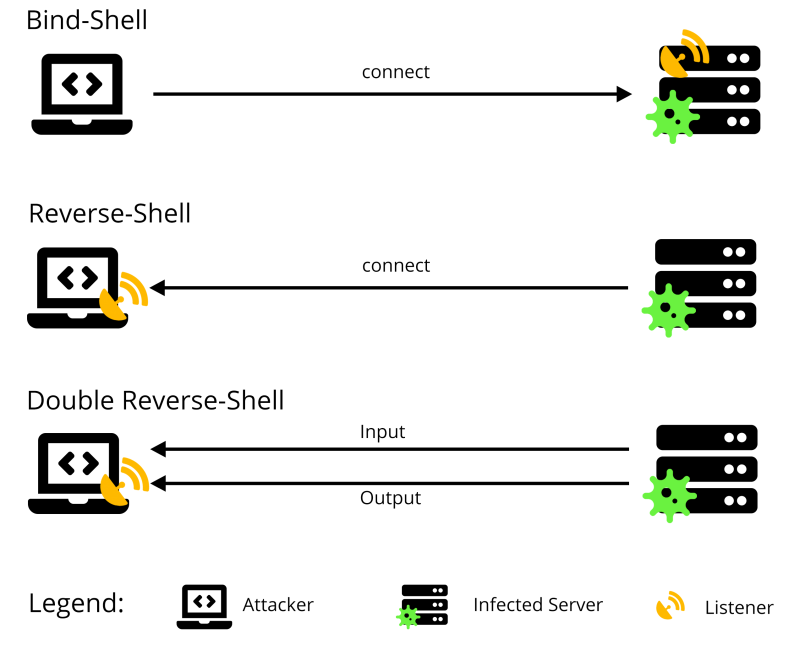
- Bind shell: The listener runs on the target host and the attacker connects to it to run a remote shell. The following problems exist with a Bind-Shell: Anyone can connect to it, and there is the possibility of a firewall in front of the target host, which does not allow a connection.
- Reverse shell: In reverse shell, the listener runs on the attacker’s computer and the target host connects back to the attacker. This fixes the above-mentioned problems with the Bind-Shell. On the other hand, the target host must have an IP address of the attacker, otherwise no connection can be established.
- Double reverse shell: This is a reverse shell, which separates the standard input and output channels. So two connections to the same port are created to the attacker’s computer.
- Encrypted shell: In contrast to the other presented shells, the Encrypted-Shell is the only one where the communication remains hidden and therefore it is not possible to trace what the attacker is planning. Encryption works with a bind- or reverse-shell by using SSL/TLS.
- Meterpreter: Meterpreter is a payload especially developed for the Metasploit Framework, which brings many useful features like migrating to another process of the target system. Meterpreter sets a high value on not being recognized. Therefore nothing is written to disk except the stager, the shell lives only in memory. In addition, existing processes are compromised instead of creating new ones, which can often prevent alarms from being triggered.
A web shell, like a bind shell, is accessible to third parties, unless it is protected by authentication in the form of a password, a special HTTP header or other parameters.
How to find a suitable Web-Shell?
Technologically, the web shell must fit on the desired host. The type of web server and the appropriate technologies must be determined in the reconaissance phase. PHP web shells are very popular and accordingly frequently used because PHP itself is widely spread and because the common content management systems are also written in PHP.
Further limitations exist in the size of the shell, as it is sometimes not possible to upload a web shell with full functionality. In this case you should rather use a minimal shell and in a next step upload a more extensive shell.
Some Examples
First practical experience
To gain first practical experience with shells, we recommend the Metasploit Framework. Rapid7 also offers a suitable environment to improve your skills in this area: The Metasploitable VM is available for download.
Other recent Pentesting Frameworks
The Metasploit framework has been around for several years, and the manufacturers of anti-virus software have reacted accordingly. They detect attacks with Metasploit very often. Here are some other current frameworks that are worth knowing:
- Cobalt Strike is a very up-to-date pentesting framework. It contains an agent, called Beacon, which is smuggled to the target host. The agent has a lot of functions like executing commands, file transfer, Mimikatz and port scans to name a few. Unlike Metasploit, Cobalt Strike is hardly recognized by modern antivirus systems. This has two main reasons: Obfuscation of shellcode and the use of the domain-specific language Malleable C2, which allows communication with the beacon to take place undetected. There are several Malleable C2 profiles that resemble common services like Gmail, Bing or Amazon.
- Empire was in 2019 with 22% still the second most used penetration testing tool behind Metasploit with 73% according to Sophos. Empire is the combination of PowerShell Empire and Python EmPyre. Therefore there are Python 3 agents besides PowerShell agents. Empire uses encrypted communication, has easy to deploy modules and in the latest version (3.4) also support for Malleable C2.
- TrevorC2 is a command and control framework that controls the communication between the target host and C2 server via a pre-cloned web page using a pre-configurable parameter and is therefore very difficult to detect.
- Koadic refers to itself as C3, which stands for COM Command & Control. Koadic is a Windows post-exploitation rootkit that performs most operations via Windows Script Host (JScript/VBScript). This has several advantages: Broad support from the standard installation of Windows 2000 up to the current Windows 10, and PowerShell does not need to be installed on the target host.
- Merlin is a cross platform post-exploitation HTTP/2 C2 server and agent written in Golang. Merlin is in development since 2017 and is currently in beta status. The unique feature of Merlin is its support for HTTP/2, because the combination of encryption and the lack of HTTP/2 protocol support in inspection tools of WAF, IDS and IPS products made it easy to get past their protection measures for a long time.
Conclusion
A web shell is a very useful tool in the post exploitation phase to maintain permanent access to a host without having to apply an exploit each time. To prevent access by third parties, it is recommended to use one of the described authentication methods.
About the Author
Ralph Meier completed an apprenticeship as an application developer, with a focus on web development with Java, at a major Swiss bank and then completed a Bachelor of Science in Computer Science UAS Zurich at the ZHAW School of Engineering. His primary task is doing security-related analysis of web applications and services. (ORCID 0000-0002-3997-8482)
Links





