Ways of attacking Generative AI
Andrea Hauser

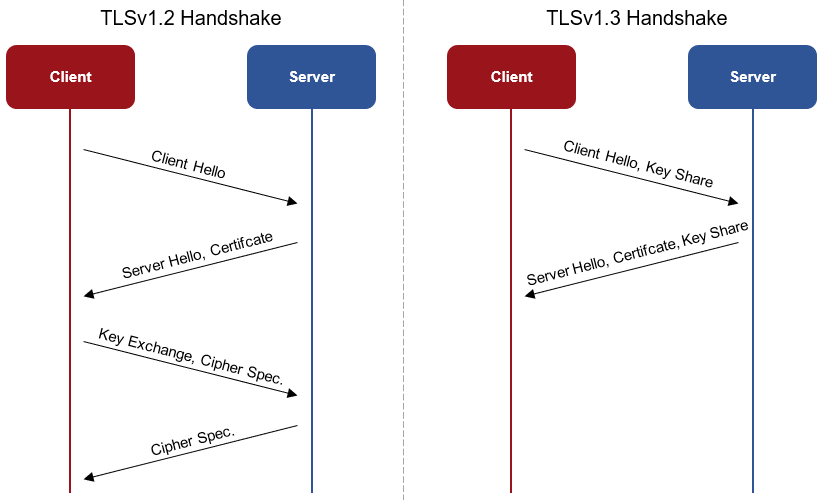
This is new in TLS 1.3
The last time we wrote articles about TLS/SSL or encryption was in 2014 and 2015. Most of the recommendations have not changed, but there are still some updates and outdated ciphers and protocols that are discussed in this article. Finally, this article summarizes which TLS settings should currently be implemented from a security perspective.
This section looks at the new protocols and security measures introduced since 2015.
A new version of the TLS protocol has been published. It is called TLSv1.3 and is defined in RFC 8446. The two most important areas in which TLSv1.3 differs from the previous protocol are security and speed. This is because TLSv1.3 removes several weak and obsolete features from TLSv1.2. The speed gain is due to a new handshake that can be performed in one round-trip instead of two.
OCSP stands for Online Certificate Status Protocol and is a standard for checking the revocation status of certificates. With OCSP-Stapling, an extension of the original OCSP, the revocation status is delivered directly by the server as part of the TLS handshake. Accordingly, the browser itself does not need to contact an OCSP server to check the status of the certificate. This reduces the total time required to establish the TLS connection and no information about a user’s browsing behavior is sent to the OCSP server.
This section looks at the protocols, ciphers and other security measures removed since 2015.
It is only about ciphers that use RSA for key exchange. All these ciphers are affected by the ROBOT attack or similar attacks and are classified as weak. The vulnerabilities mean that an attacker who can passively record the data traffic can later decrypt it. Anyone who would like to read more details about the ROBOT attack can find them on the website created for the vulnerability robotattack.org.
Back in March 2020, modern browsers such as Chrome, Firefox and Safari stopped supporting the TLSv1.0 and TLSv1.1 protocols. This is mainly because several aspects of the design of these protocols are not robustly implemented. For companies in the financial sector, it is also of interest that the PCI DSS has also required that TLSv1.0 should no longer be supported as early as the end of June 2018.
Public-Key-Pinning was developed to counteract the fact that any CA can issue a certificate for any website. However, the correct implementation of public key pinning is complex and requires a lot of expertise. In addition, there is the risk of completely blocking the website for visitors if a bad configuration were to be implemented. For this reason, most browsers have removed support for Public-Key-Pinning.
As an alternative, the concept of Certificate Transparency is now available. Newly issued certificates are recorded in publicly maintained CT-logs. Anyone can now monitor these logs for their domains and recognize a falsely or maliciously created certificate.
The following checklist contains the mentioned recommendations for a secure TLS configuration as well as those still valid from the last article (as of July 2021):
If the settings suggested in the TLS configuration checklist have been enforced, then a system is well protected with the current security recommendations in the area of TLS. However, fully protecting a system involves more than just implementing secure TLS settings. In our archive of all labs you will find all articles on topics that our Red team, our Blue team as well as our Research team have focused on recently.
Our experts will get in contact with you!

Andrea Hauser

Andrea Hauser

Andrea Hauser

Andrea Hauser
Our experts will get in contact with you!