Specific Criticism of CVSS4
Marc Ruef

This is how you handle Ransomware
A large number of companies are confronted with this threat and the damage it causes. In the heat of the moment, the affected parties often react wrongly. This article discusses the correct strategic and tactical approach to a ransomware attack. Many aspects of this can also be applied to extortion via traditional DDoS attacks (Distributed Denial of Service).
Ransomware is a special class of malware. Ransomware strives to infect a system in order to extort money through further measures. Traditionally, this is done by encrypting the data. The data owners cannot access it again until an appropriate ransom is paid. After a successful transaction, which often wants to be realized through Bitcoin or alternative cryptocurrencies, the victim is handed the key for decryption. If a payment is not made, the data remains “encrypted forever” or is even actively deleted at some point.
In the case of a double-extortion, the data is stolen before it is encrypted. This allows the perpetrator to establish additional leverage: If the ransom payment does not take place – because, for example, the data can be accessed thanks to a previously made backup – the threat is made to publish it. This is particularly problematic if sensitive (e.g. financial data, intellectual property) or personal data (e.g. customer information) is involved.
Based on such data theft, a triple extortion can also be approached. If personal data is included, the affected persons are additionally blackmailed. This can involve both employees and customers. Problematic relationships (e.g. with banks) or compromising information (e.g. patient data) can be used to turn the data into money. The data might be published on the data leak sites of the ransomware gangs, in data trading forums, on file sharing platforms or through public torrents.
The first thing to do is to discover a ransomware attack. Ideally, this is done through existing and functioning technical tools. These typically include:
Ransomware is mostly implemented with standard products that can be detected by appropriate security solutions such as AV, FW, and IDS. In addition, if an exfiltration of unusually large amounts of data takes place, DLP, logging, and monitoring may alert. If such mechanisms are not in place, incorrectly implemented, or misconfigured, detection may not occur, making compromise possible in the first place. However, some or even all of these mechanisms are considered good practice today.
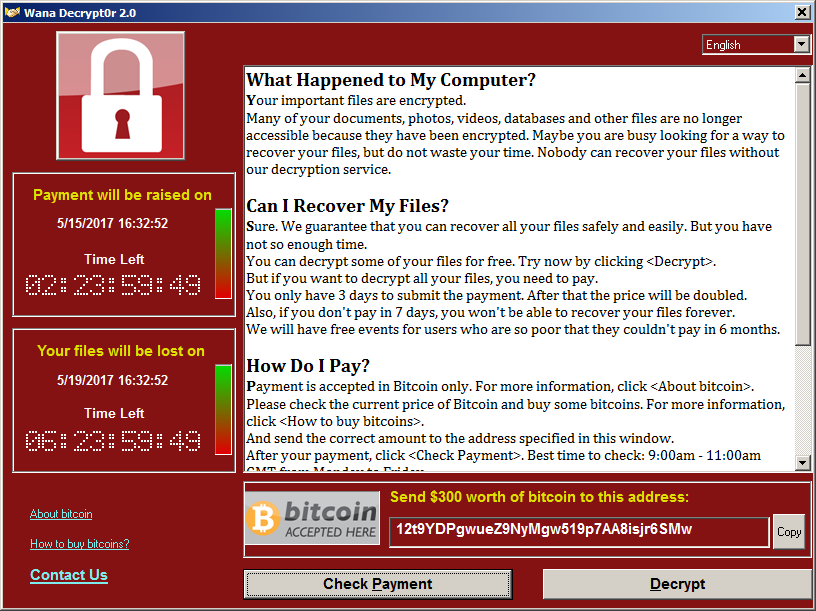
After a ransomware has successfully implemented the infection, privilege escalation, compromise and exfiltration of the data, it usually makes itself noticed. This typically happens through a popup message on the screen of the affected systems. However, some ransomware gangs also use to contact victims via email.
In any case, at least at the beginning, it is important to avoid contact and exchange with the blackmailers. There should be no reaction of any kind. This also includes a friendly: “Thank you, we’ll clarify and get back to you.”
The point is that the perpetrators do not know for the time being whether the infection was really successful, whether it was able to cause concrete damage, whether their concern for the extortion and whether it was really perceived as a concrete threat. Thereby time can be gained as well as the perpetrators can be forced to further clarifications and a renewed contact.
The time gained can be used to work out and implement further measures. In addition, tough communication makes the victim a less worthwhile target for attack. The perpetrators have to invest more effort to reach their target. However, for the sake of economy, they want negotiating partners who cooperate quickly and easily.
However, it is important to be sure that the ransomware’s capabilities and the compromise steps carried out so far can be understood beyond doubt. By evaluating the logs for file accesses and network transfers, it must be possible to prove that no exfiltration of data has been carried out. This can prevent the risk of a double or triple exfiltration. If one does occur, it will still be necessary to exchange information with the extortionists.
A payment should always be refrained from. If one is executed, ideally the extortion can be finished. It is not impossible, however, that such may be merely postponed and a new demand made instead in the foreseeable future. In contrast, in the case of a hostage situation, an exchange may remove the concrete danger to the life of the hostage. In the case of encryption and data theft, one is not sure – at least for the time being – whether the danger has really been permanently eliminated when a payment is made: Isn’t the system still infected, are the copies of the stolen data really destroyed, is going to the media refrained from? In most cases, the danger has not been averted and cannot be guaranteed as such with absolute certainty. By making a payment, one first and foremost shows willingness to respond to claims.
Payments are only advisable, if by these forcibly needed time can be won. That is, when the window of opportunity to destroy or publish the data is closing, but sustainable measures have not yet been extensively established. A ransom payment must always be embedded in a far-reaching plan. In the U.S., there is currently discussion about whether ransomware payments should be criminalized.
Most ransomware gangs operate reliably when it comes to payments and data releases purchased with them. After all, if it becomes known that a payment made cannot avert the threats, their business model is immediately eliminated. From now on, no one will be willing to make such payments without value in return.
The defensive cybersecurity community is always trying to reverse engineer the ransomware to understand how it works and generate its own decryption keys. It is not uncommon that after weeks or at the latest months, corresponding decryption keys are created on their own for known ransomware families.
Individual ransomware gangs threaten to cause concrete damage if the authorities or cybersecurity firms are called in. Accordingly, a discreet and targeted approach is advised.
At the latest when an infection reveals itself to be an extortion attempt, the appropriate authorities must be informed. The company’s cybersecurity department should contact the National Cyber Security Center (Nationalen Zentrum für Cybersicherheit, NCSC) in Switzerland or the Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik, BSI) in Germany.
These are usually aware of ongoing ransomware campaigns and can assess the situation and perpetrators. Through them, coaching can take place on how to proceed on a technical and negotiation level. External cybersecurity firms should be called in to professionally implement the recommended course of action.
In addition, a report to the police should be filed at a later stage (only after phase 4 has successfully started). This can be done regularly at a police station. Do not be discouraged by the officers that such a report is pointless and will not bring any results to light. Following this legal instruction will first and foremost help the perpetrators. The filing of a report against unknown persons is not subject to any preconditions. It may also be necessary, for example, to make use of the coverage provided by a cyber insurance policy.
Ransomware extortion can only work if it has been able to manifest itself successfully at the technical level. Accordingly, it becomes immediately important that it can be countered at the technical level.
First, an identification of the malware family, its functioning and capabilities must be implemented. Many ransomware products identify themselves with unique names. It is easy to find out exactly what they do by searching the Internet. It is not uncommon for malware to be given different names by different antivirus manufacturers.
Through identification, it is possible to deduce what damage exists or threatens: What and how is something affected? The affected systems and data can usually be located quickly. Now it must be decided what value should be attached to this data. If they are not required or can be easily replaced, there will be no need to deal directly with the extortionists. It is advisable that a well thought-out backup concept is brought to bear, ideally including offline backup.
In any case, it must be found out how the infection and compromise could take place. Which systems are affected, how was the ransomware introduced. Often it is missing patches, misconfigurations or mismanipulations by users (e.g. opening a mail attachment or inserting an infected USB stick). The identified gaps must be closed to rule out recurrence and future compromise. If infected systems infect surrounding systems on the same network via a worm, the affected systems must be isolated (disconnected from the network).
The compromised components, namely the modified or encrypted data, should be rescued. The easiest way to do this is to restore a previously created backup. It is important to make sure that a flawless backup has been imported that has not already been compromised. This allows the normal operating state to be restored.
The final step is to take care of the communication of the incident. Legal regulations may require that authorities and/or customers must be informed about the incident within a predefined period of time. Namely, this is controlled by the Federal Act on Data Protection (FADP) in Switzerland and the General Data Protection Regulation of the European Union (GDPR). Failure to provide such notification may result in legal expenses and financial damages.
With a law firm specializing in data protection, an assessment of the tangential data must be made to determine and plan the legal responses. Communication with affected customers must be timely and honest. These people have been harmed due to the fault of the provider or face future risks of data misuse. Upsetting them with marketing-driven platitudes will lead to loss of trust and resentment. Never claim that personal data is not really sensitive. Your customers will definitely see it differently.
Art. 33 (1) GDPR provides for documentation and notification to the competent supervisory authority. In case of a risk to “rights and freedoms”, this has to be done within 72 hours. Art. 34 (1) GDPR regulates that customers must also be informed. If it affects their “rights and freedoms”, this must be done without delay. And according to Art. 34 (2c) GDPR, a public announcement must be made. If the requirements of the GDPR are not complied with, Art. 58 and Art. 83 GDPR come into play. Defaulters will then be fined up to 20 million euros or 4% of the previous year’s turnover, the higher benchmark being taken as the starting point.
If possible, active publicity of the incident in the media should be avoided in the absence of public interest. However, in doing so, one runs the risk that if the case is brought to public attention elsewhere, the crisis communication will be called into question. The same principle of honest communication must therefore be followed when dealing with the media. Statements must be professional. Contentless platitudes, technical misjudgements or even arrogant ignorance will lead to lasting reputational damage.
A PR consulting firm can be called in to drive the communication. However, this company must be specialized in crisis communications in the IT sector. Otherwise, the professionalism requirements outlined above cannot be achieved by a long shot. There have been plenty of bad examples in the past.
It must always be remembered that the affected company is partly to blame for the incident. It was missing or faulty security measures that made a successful attack possible in the first place. Art. 7 (1) FADP clearly shows the complicity:
Personal data must be protected against unauthorised processing through adequate technical and organisational measures.
Whether strategic, technical or personnel errors have led to the problem is not relevant in the context of communication. However, to deny this and instead to attest the perpetrators an “undefendable professionalism” can and will be perceived as impertinence by both customers and the media.
Instead, one should focus on the facts. Only that which is also of use to the public should be communicated. The disclosure of information must not result in any damage to the company. For example, if a ransom payment was made, it must under no circumstances be disclosed. If it becomes public, you become a worthwhile target for copycats.
Ransomware attacks are a looming threat that has been able to establish itself as a lucrative business model. Complexities and dependencies lead to an increase in corresponding compromises. It is important to proceed according to the described 5-phase plan in order to be able to pursue a far-sighted and thus professional approach at any point in time. This starts with the technical analysis of the ransomware and ends with the communication with customers and the media. Strategic and tactical mistakes can take revenge and lead to more damage.
We are going to monitor the digital underground for you!

Marc Ruef

Marc Ruef

Marc Ruef

Marc Ruef
Our experts will get in contact with you!