Security Testing
Tomaso Vasella

These are the Changes of CIS Controls v8
These developments also lead to an increasing number of security standards, regulations, guidelines and tools to help organizations of all sizes to assess risks correctly and to take effective measures for adequate protection. On the one hand, this is welcome, but on the other hand, there are now almost too many security standards, making it sometimes difficult to identify the essential or minimally necessary precautions, especially for smaller organizations (the referenced standards in the Secure Controls Framework illustrate this quite well).
It is one of the primary objectives of the CIS Controls to address precisely this challenge and to provide guidance for all sizes of organizations and different security needs. The CIS controls are a collection of concrete, prioritized security measures (called safeguards) that serve to defend against the most common cyberattacks on systems and networks. Especially for organizations that do not yet have a security program in place, they provide valuable guidance and assistance to start their own security program. The CIS controls reference various recognized frameworks such as the NIST CSF, ISO 27000, PCI DSS, and others, and consist of concrete measures that can be implemented pragmatically. The CIS controls exist for many years already and are continuously evolving and adapting to new developments and insights.
The CIS controls in the current version 8 (formerly: CIS Critical Security Controls or CIS Top 20) were published in May 2021. They have been adapted to better keep up with modern systems and current software. The still ongoing shift to cloud computing, increasing mobility, teleworking and home office, and also changing attack tactics prompted the update. The following figure shows an overview of all 18 CIS controls.

Since version 7.1, the CIS controls define three Implementation Groups (IG) that build upon each other. These groups are primarily used to prioritize the implementation of the security measures, but also address different security needs. IG1, for example, groups together those measures that should be implemented by all organizations to achieve a minimal level of security and can be implemented with limited resources and little expertise.
An organization must decide for itself which other Implementation Groups should be implemented. This decision should include the following considerations:
IG1 includes 56 measures to achieve a minimum level of information security. These measures include basic topics and precautions such as asset management and inventory, secure configurations, access controls, backup, and so on. They represent the absolute minimum set of security measures that every organization should implement and are accordingly also referred to as basic cyber hygiene.
IG2 includes 74 additional measures and builds upon IG1. The goal of this Implementation Group is to support somewhat larger organizations that have to consider more complexity and that may have multiple departments with different risk profiles. Some of the measures require solutions and tools that are more likely to be deployed in large environments and may require specialists to configure and operate. Examples include automated solutions for hardware and software inventory, vulnerability management solutions, or centralized logging and monitoring.
IG3 includes 23 additional measures and builds on IG2. They are designed to help larger organizations with more resources and security expertise achieve better protection, even against more sophisticated attacks. Topics covered by this group include improved detection capabilities for security-related events and more comprehensive security testing.
The most obvious change compared to the previous version is the reduction to a total of 18 controls with 153 measures (version 7.1: 20 controls and 171 measures). On the one hand, this is due to a stronger focus on what is essential today; on the other hand, topics have been partially merged.
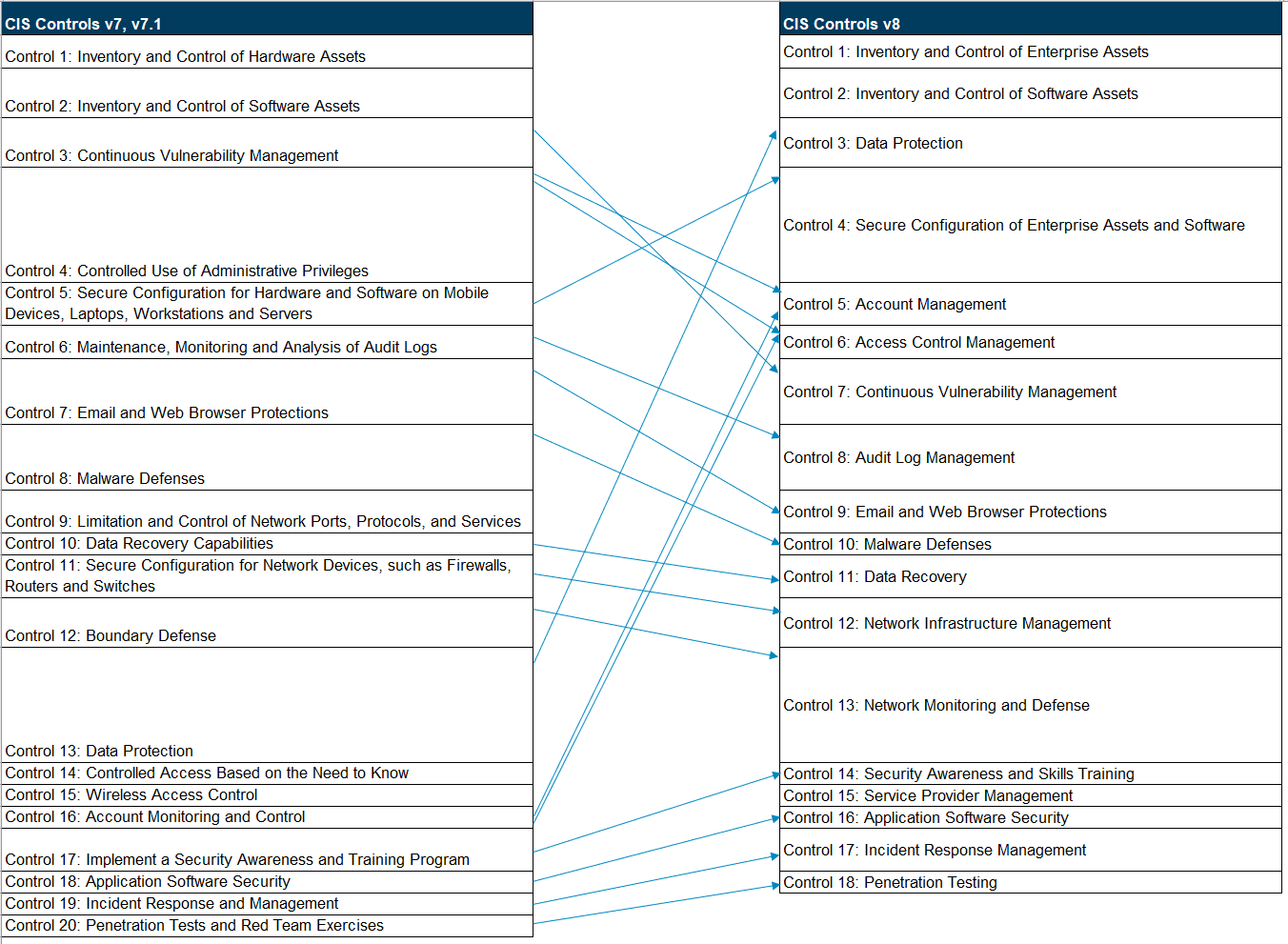
Service Provider Management (control 15) is a_ new _addition, which takes into account the still increasing importance of cloud computing and software-as-a-service and the importance of supply chain security. Also noticeable, but plausible, is the shift of the control Data Protection to the front to position 3 and the increase in the priorities of the topics Account Management and Access Control Management. In sum, the changes at the level of the controls are not very extensive. In contrast, over 200 changes were made at the level of the Safeguards. Organizations already using the CIS controls should therefore look at the changes in detail. CIS provides a comprehensive compilation of all changes since the last version on its website.
The latest CIS controls have been amended with current topics and continue the principles already known from previous versions. Even more attention has been paid to focusing on the essentials and to including organizations of all types and sizes. The concept of Implementation Groups emphasizes the notion of basic cyber hygiene even more in the current version and defines a minimum standard for information security that is achievable even for small organizations with limited budgets and resources. In view of the likely developments, it may be assumed that measures described as advanced today will only suffice to achieve a minimum level of information security in the future.
Our experts will get in contact with you!

Tomaso Vasella

Tomaso Vasella

Tomaso Vasella

Tomaso Vasella
Our experts will get in contact with you!