Security Testing
Tomaso Vasella

How to use OWASP Maryam
Of course, we’re not the only ones to do so and the OWASP project provides several tools that can help with this task. In this article, we will take a first look at one of them, OWASP Maryam.
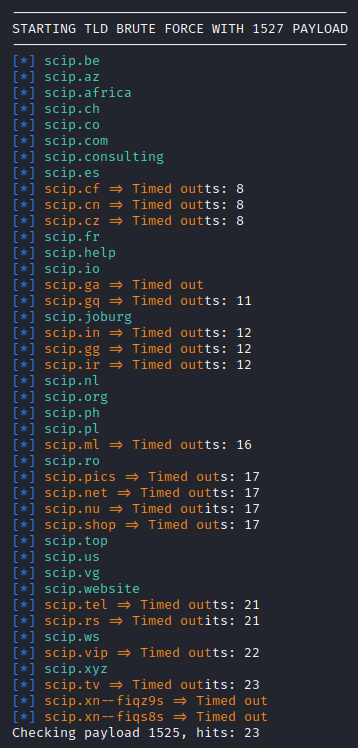
Maryam is a modular framework, based on recon-ng, with an interface that is reminiscent of Metasploit, with many different modules for different tasks. These are grouped for overview into 4 different categories. Footprint has tools that help with discovering information about a target on a technical, network-based level. This ranges from dnsbrute, which replicates functionality from tools like sublist3r to find as many subdomains of a given domain as possible, over tldbrute, which attempts to find all top-level-domain variants of a domain, to crawl_pages, which lets you search through webpages for specific strings and regexes.
Search is a collection of commandline interfaces to a large number of search engines and websites. This includes such obvious sites as Google or Bing, but also a tool called sanctionsearch that searches the US Office of Foreign Assets Control’s sanctions list. With these, one can automate searching for additional information based on links and keywords found either through the footprint tools, or for example from the OSINT tools. While all the information found through OWASP Maryam is technically OSINT, this category has a few advanced search tools. Crawler goes over a website and extracts links, usernames, email addresses and similar information that it can find, while suggest lists the suggested terms of queried search engines. email_search can search for exposed email addresses in search engine results and so on.
The last category is IRIS, which is an experimental meta-search engine that one day should make it easier to organise all the data acquired from the other modules.
Of course, tools like tldbrute can generate quite a bit of noise. Checking our own domain, you get a surprising amount of hits – none of which are associated with scip. Certainly, the novelty domains responding with a domain squatter’s website are to be expected, but in the case of a multinational company, this would allow an attacker to easily find all the websites for different national branches. With any luck, one of them might still use a vulnerable library and offer an entry into the network of the company. Sometimes, however, all you can find is humorous name clashes, such as several accounts for a MrUEF instead of our own Marc Ruef, or the Society for Computers in Psychology, which we can confirm is not run by our colleague Marisa Tschopp – although perhaps it should be…
Still, the tools that Maryam provides to explore a target network on a technical level work quite well and while it is worthwhile to supplement them with other tools or at least other wordlists, they are a convenient collection. They do not replace an nmap scan, but they can provide some targets for nmap.
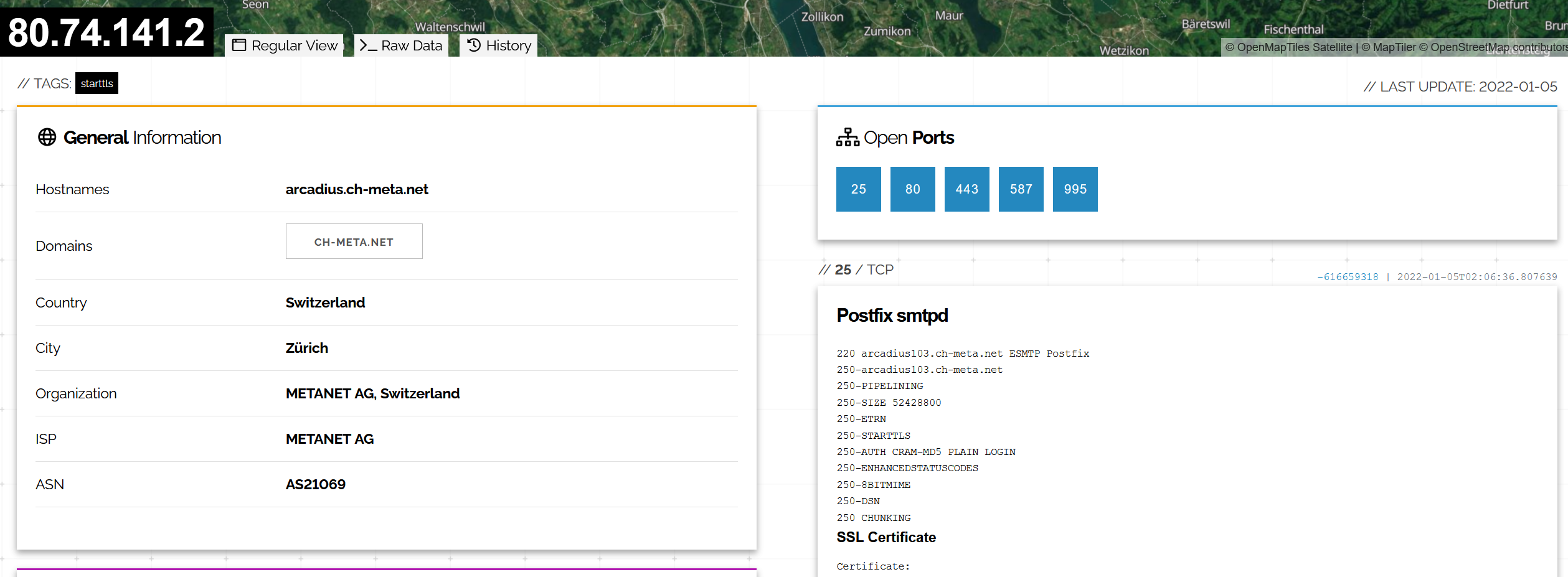
The biggest omission from OWASP Maryam’s documentation, however is that there seems to be no integration of Shodan. The integration exists, though it requires an API key, it is simply not documented or listed in Maryam’s module list and we discovered it through a closed GitHub issue where it had been added. Shodan already aggregates a lot of information about servers that can be found through scans and is a logical extension of Maryam’s capabilities. In particular, the way that Shodan can lead to further targets by listing certificate information or showing a hostname or IP in the cache of another server is a natural fit for OWASP Maryam. In one of our engagements, we found through Shodan that some servers of our client had ended up on the distributed hash tables (DHT) of the Torrent filesharing protocol. That might be entirely benign, as many Linux distributions utilise this technology to provide installation images, but it was definitely something the client needed to investigate further.
However, Maryam can do more than just help prepare a technical engagement, where a network gets attacked. In particular the OSINT category as well as some of the search tools like the Twitter or LinkedIn search can find a lot of connections and more personal information about individuals. Of course, the point of this is to prepare a spearphishing or similar social engineering attack by providing you with the ability to find names and personal information about employees and ex-employees. IRIS also includes the ability to do sentiment analysis on the obtained data, allowing you to find people who write positively or negatively about your target. Or at least, it will in the future.
Maryam also contains tools to search for information on compromised accounts which could help you get more direct access to someone. However, it seems like not all parts of OWASP Maryam are equally maintained, as the tool to search for an email in the Have I Been Pwned service is broken, for example. While these errors are clearly in the minority, combined with the very sparse documentation, it is clear that the project could use more people and developers.
OWASP Maryam is already a very useful tool for gathering and assembling data, as well as simplifying automation of these recon tasks. However, the project still has a ways to go to improve discoverability for people to easily fully utilize it. Currently, learning to use it is a rough experience, useful though the tool is.
It is great to see just how much tooling the OWASP project provides and to see that continue to grow and improve. Coupled with the efforts to provide testing and development processes and standards, the OWASP project continues to be one of the best resources for IT security.
Our experts will get in contact with you!

Tomaso Vasella

Eric Maurer

Marius Elmiger

Eric Maurer
Our experts will get in contact with you!