Burp Bambdas & BChecks
Ralph Meier

Flipper Zero ideal for Attacking Wireless Peripherals
The use of wireless keyboards brings an increased attack surface and depending on the system, publicly known vulnerabilities are present, such as CVE-2019-13055. This issue is about recording the AES key material when a Logitech Unify device is first paired with a Unify adapter and decrypting the subsequently typed characters.
MouseJack is a collection of vulnerabilities involving keystroke injection and encryption bypassing. Officially, MouseJack is listed as CVE-2016-10761. A wide range of wireless keyboards and mice that communicate over the 2.4GHz frequency are affected. Peripherals that communicate exclusively via Bluetooth are excluded. The vulnerability was discovered by the company Bastille in 2016, they also list affected devices with manufacturer statements and a fix for the vulnerability where possible on their website.
For wireless peripherals such as mice or keyboards, there are no proprietary protocols that operate on the 2.4 GHz frequency. Accordingly, each manufacturer is responsible for the communication and the security used. When moving the mouse or typing, the movements or keystrokes are transmitted to the wireless receiver on the computer by means of packets, the exact implementation of which, as already mentioned, depends on the manufacturer. Normally, the user’s input is transmitted in encrypted form. The key is defined during the initial pairing between the input device and the wireless receiver. The encrypted transmission prevents the simple interception of foreign inputs.
The tested Unify adapters, which were affected by the MouseJack vulnerability, were initially delivered paired, but could be independently connected to new mice or keyboards. According to this, it made no difference whether the Unify adapter was paired exclusively with a mouse, a keyboard or both. This suggests that when only a mouse is used, it is not checked whether the commands received are also exclusively mouse movements or the pressing of mouse buttons. Therefore, it is also possible to make unintentional keystrokes on the target system when only using a wireless mouse.
When the MouseJack vulnerability was originally discovered by Bastille, it was noted that most manufacturers encrypt the keystrokes they receive, but the Unify adapters do not check that all user input received is encrypted. Therefore, the inputs are also received in unencrypted form. This simplifies the process enormously for attackers, as they do not have to worry about the key used, but only need the exact Unify adapter address to send the desired payload.
Since a Flipper Zero was used in the inspiration video that led to this article, the goal was to recreate this attack.
The test setup was a Windows notebook with a Logitech Unify adapter and a Logitech M525 mouse and later a Logitech K800 keyboard. To carry out the attack, a Flipper Zero with a NRF24L01+ WLAN radio module connected via GPIO pins was used. The firmware used on the Flipper Zero was a fork of the Flipper firmware from RogueMaster, because the necessary scripts for operating the NRF24L01+ wireless module via the GPIO pins are already available.
The wiring between Flipper Zero and NRF24L01+ WLAN radio module was implemented according to the linked scheme. After wiring, this looked like shown in the image.
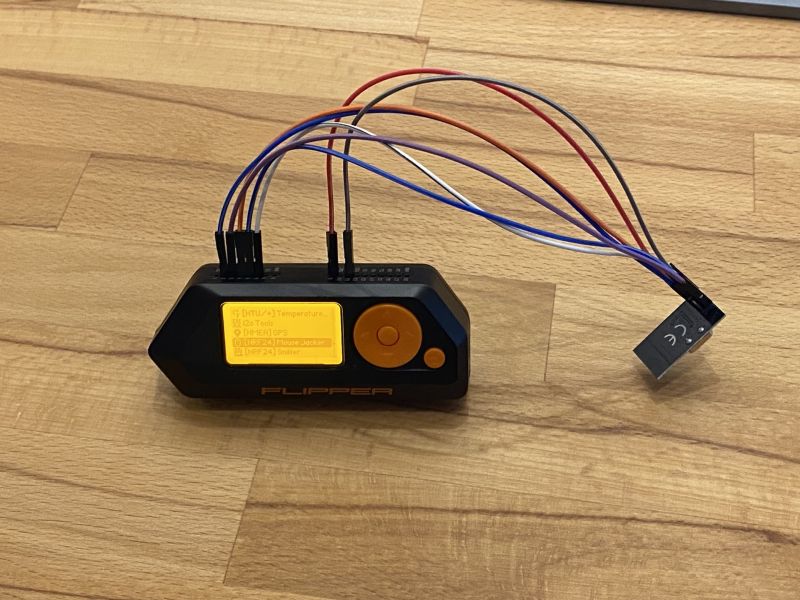
After connecting via the GPIO pins, the address of the Unify adapter can be found out with the NRF24 Sniffer Script and then attacked with the NRF24 MouseJack Script. The MouseJack script asks for a ducky script as payload at start, which is executed and sends the keystrokes unencrypted to the Unify adapter.
For example, the following ducky script can be used:
DELAY 1000 GUI r DELAY 500 STRING firefox.exe DELAY 500 ENTER DELAY 1500 CTRL l DELAY 500 STRING www.scip.ch DELAY 500 ENTER
Ducky Scripts are explained in more detail in the article Attacks via Peripheral Devices .
The small size of the Flipper Zero makes it much easier to attack wireless peripherals or other targets that require a certain physical proximity. The Flipper Zero fits easily into a jacket or shoulder bag, even with an additional module or the WLAN radio module shown above. This makes it much more inconspicuous in the event of an attack with physical proximity. In an open-plan office where several people use wireless peripherals that are affected by the MouseJack vulnerability, the probability of an inconspicuous, successful attack is very high.
Wireless devices have a higher attack surface and should therefore always be used with the current firmware and in sensitive areas a wired keyboard and mouse should be preferred for continuous operation. The MouseJack vulnerability is already more than seven years old at the time of this writing and is always present and exploitable when testing devices in one’s own environment. The Flipper Zero’s small form factor and support for a variety of radio frequencies, as well as its easy expandability via GPIO pins, make it perfectly suited for attacks on wireless targets with necessary physical proximity to the target device.
Our experts will get in contact with you!

Ralph Meier

Ralph Meier

Ralph Meier

Ralph Meier
Our experts will get in contact with you!