Transition to OpenSearch
Rocco Gagliardi

This is our Experience with Security Frameworks
A security framework provides the skeleton on which to build security, or for us where to focus in our assessment, but they require a wealth of knowledge and considerable experience. Certainly, if last year checking NIST CSF PR.AC-3 compliance required knowledge of different technologies, now it is easier with ChatGPT:
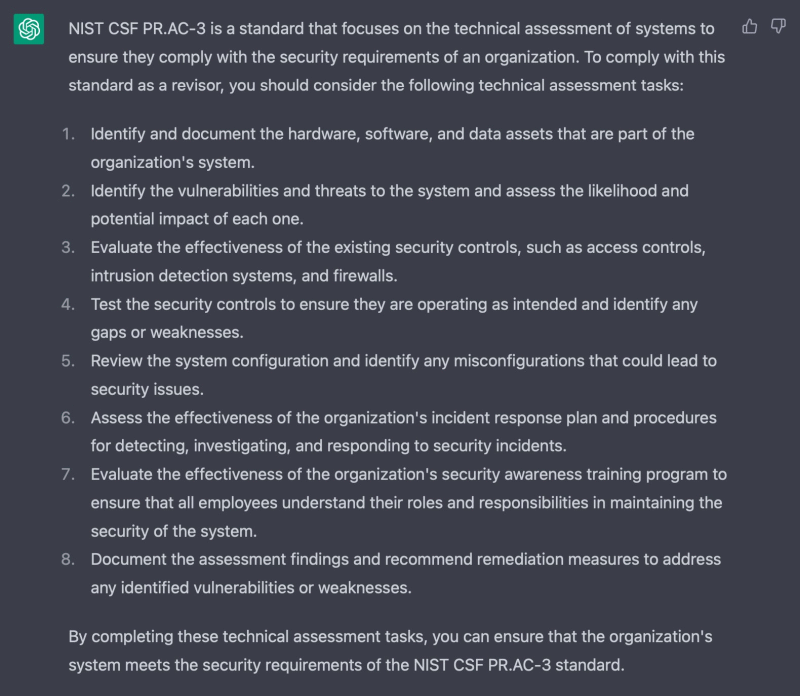
Or at least seems easier. If the list generated by ChatGTP may seem like a valid assessment pattern at first glance, we soon realize that the list is a reinterpretation of several points already present in the CSF, ordered in different ways. ChatGPT is a valid aid, but an aid. It does not replace – for the moment – an auditor.
We at scip AG have used the NIST-CSF as a basis for security assessment for a decade, although we now prefer, for most of our customers, the CIS CSC V8 but there are numerous cyber security frameworks in existence due to the complexity and constantly evolving nature of cyber threats, as well as the need for standardized best practices and guidelines to help organizations effectively manage and mitigate these risks.
In addition to the classic ISO27k, PCI-DSS, and COBIT, there are other models geared toward the cloud (CSA-CCM), healthcare (HITRUST), and the generic NIST (CSF or 800-53), and many others found in almost all of the most used framework rankings.
However, Secure Control Framework (SCF) is surprisingly absent from these lists.
Hackers share information on attack methods with other hackers, so why shouldn’t the good guys share information on how to best protect an organization?
Volunteers from various backgrounds in the cybersecurity industry worked and continue to work together to address issues related to privacy and governance, risk, and compliance (GRC). Specialists in auditing, engineering, architecture, responding to incidents, consulting, and other related fields. Expert-derived content is the final result, and it is this that makes up the SCF. A huge set of controls, offered free of charge to public.
I fell in love with SCF from the very first version and started using it in our projects in 2019. SCF is complex: As of today, version 2023.1, there are 1168 controls, in 33 domains. The controls are updated at least once a year. But if in 2019 there was only one big checklist with 900 controls, today additional definitions have been added that cover most of those areas left uncovered by other frameworks.
We can therefore find the Security and Privacy Principles the Integrated Control Management the Capability Maturity Model the Risk Management Model and the Privacy Principles.
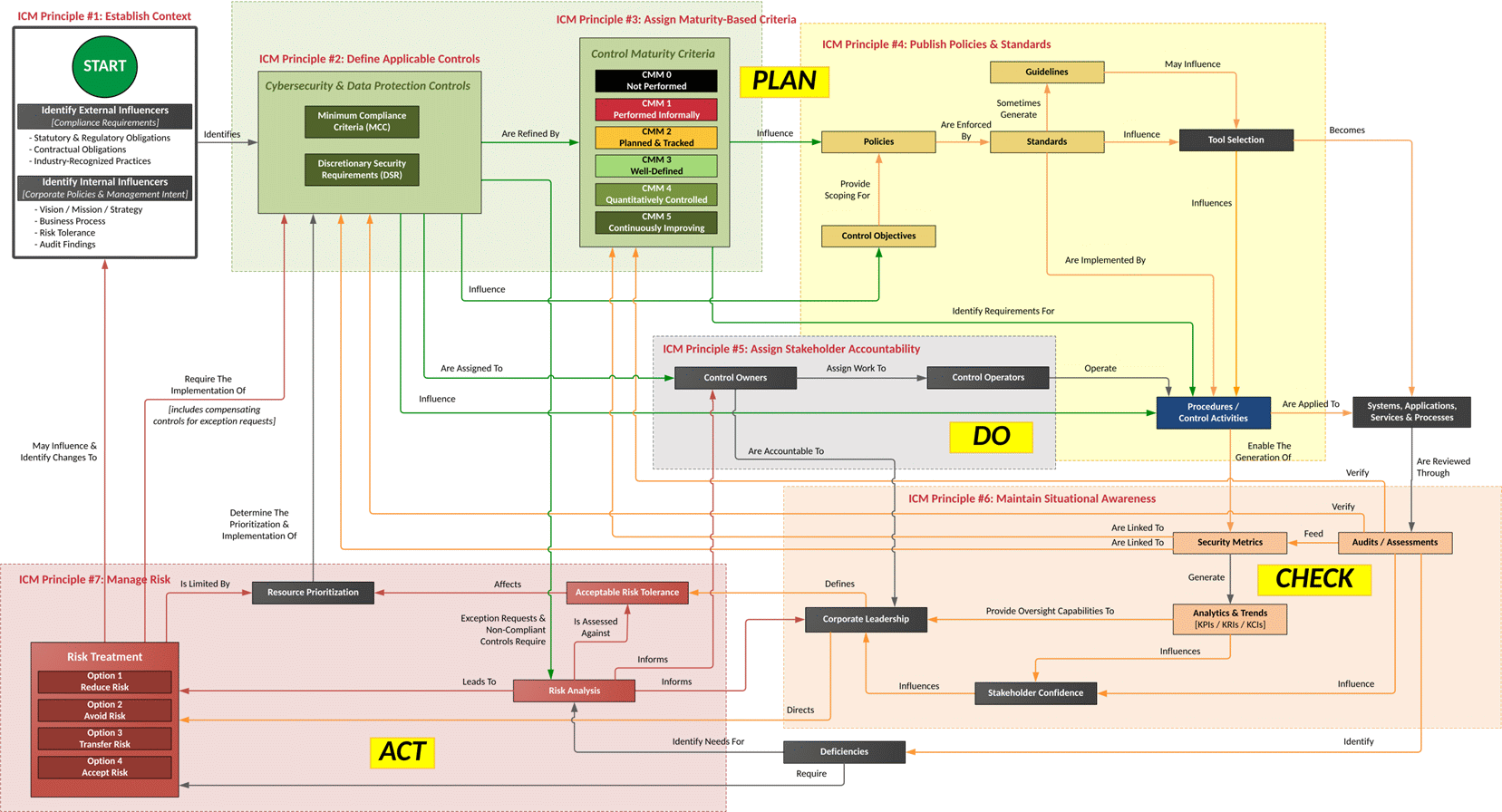
To use the SCF, in the 16 pages of the Integrated Control Management the approach to be used to make the best use of the framework is outlined; however, experience is required. Here we want summarize the strong points of SCF:
What is most appreciated, in addition to the numerous domains and controls that cover a wide range of cybersecurity topics, is the ability to filter them. Mapping controls to other standards (198 in total), organized by country, sector or specialty, allow to quickly see whether or not an organization comply with that specific standard or select only a subset of specific interest.
Same regarding threat and risk mapping. Each control has mapped which threat/risk it is exposed to, thus making the risk management process more effective.
SCF is well-structured, and with the inclusion of mappings to other systems such as ATT&CK, it can serve as a bridge between the numerous standards in the field of cybersecurity.
The selection of the security framework to utilize depends on a variety of criteria, as was already discussed. One of these three is always selected. These are some criteria that can aid in your decision.
| Framework | Focus | Scope | Strenght | Limitation |
|---|---|---|---|---|
| CIS CSC v8 | CIS Controls v8 is a tactical framework with concrete activities to improve cyber security. It presents a prioritized list of security measures based on actual attacks and incidents, structured into 18 cybersecurity best practices to assist organizations in enhancing their security posture and reducing cyber risk. | CIS Controls v8 is industry-specific and targeted for small and medium-sized businesses. CIS Controls v8 is industry-specific and geared at small and medium business. The CIS CSC v8 addresses a vast array of security controls, such as asset management, vulnerability management, access control, incident response, and data protection. | CIS CSC v8 is a prescriptive framework that describes precise procedures for enhancing cybersecurity based on actual risks and assaults, and gives practical assistance for creating effective, understandable security measures. It is a comprehensive framework that offers enterprises a thorough road map for enhancing their cybersecurity posture. | CIS CSC v8 may not be as comprehensive as other frameworks and may not cover all areas of security because it focuses primarily on technical controls and does not discuss governance, risk management, and compliance in great detail. |
| NIST CSF | The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is a set of guidelines for improving cybersecurity across critical infrastructure sectors. Is a high-level framework that identifies, protects, detects, responds to, and recovers from cyber threats, and provides a common language and methodology for managing and reducing cybersecurity risk. | NIST CSF may be used by any organization, regardless of size or industry. Covers five core functions: Identify, protect, detect, respond, and recover that are designed to help organizations understand and manage their cybersecurity risk. | NIST CSF is a framework that advises businesses on how to manage cybersecurity risks. Is a flexible framework that can be adapted to the unique needs of different organizations, and provides a common language and a standardized approach to cybersecurity, which makes it easier for organizations to communicate about their security posture. | NIST-CSF may require significant resources and expertise to implement, particularly for small organizations. The NIST CSF is not prescriptive, which means that organizations need to interpret and apply the guidelines in a way that makes sense for their specific context. This can make it difficult for organizations to know if they are implementing the framework correctly. |
| SCF | The Secure Controls Framework (SCF) focuses on internal controls. These are the cybersecurity and privacy-related policies, standards, procedures, technologies and associated processes that are designed to provide reasonable assurance that business objectives will be achieved and undesired events will be prevented, detected and corrected. | SCF can be used by any organization, regardless of size or industry. The SCF covers 33 major domains. Along with the domains, there are lists of principles, risks, threats and others which, together with a model and usage instructions, are designed to help organizations understand and manage their cybersecurity risks. | SCF provides a complete set of security controls that encompass both technical and organizational security issues. Important is the mapping of controls to multiple standards, which enables easy filtering and a check for conformity with other standards. | SCF is complex and challenging to implement, and may require significant resources and expertise. |
In summary, each framework has its own strengths and weaknesses. Organizations should consider their specific needs and resources when selecting a framework to implement. If the business is not particularly resourceful and wants to address the essentials of maintaining proper IT hygiene, CIS-CSC is a great option. SCF can be used in the future to improve IT posture or in businesses with the means and expertise to assess the current state of the greatest number of controls on the market.
Our experts will get in contact with you!

Rocco Gagliardi

Rocco Gagliardi

Rocco Gagliardi

Rocco Gagliardi
Our experts will get in contact with you!