Dynamic Analysis of Android Apps
Ralph Meier
How to use Bambdas and BChecks
The name Bambdas is a combination of Burp and Lambda. Bambdas enables users of Burp Suite to easily extend their tool or its functionality directly on the graphical user interface using pieces of Java code. PortSwigger wants to offer a possibility to extend Burp in all aspects by users. Previously, this was only possible by developing Burp extensions, which required more development expertise, such as the knowledge of build tools like Maven or Gradle.
Bambdas were introduced with the release of Burp Suite Release 2023.10.3. Bambdas were first introduced in the Proxy tab and thus enable the filtering of HTTP traffic. Thus, PortSwigger first brought an extension of the HTTP history filter. At this point, a Bambda is applied to an HTTP history item (requestResponse item) and can therefore query, filter and highlight all properties of the requests made and the associated responses. Regular expressions could be used in the previous HTTP history filter, but Bambdas are much more powerful and feature-rich. It is now also possible to convert a regularly configured filter into a Bambda and extend it with Java code. In Bambda mode, existing Bambdas can be inserted, imported from files or developed directly in the editor and saved later. At the time of this article, Bambdas were already published in the WebSockets Histroy Filter and in the filter function in the Logger Tab in an Early Adopter Version of Burp Suite. The stable release will probably follow in the coming weeks.
Bambdas in the Proxy HTTP Traffic Filter can be used to filter and highlight specific endpoints, requests with input fields, special headers or other anomalies from all history items. This makes it easy to narrow down special cases and then analyse them individually. As Bambdas are made from Java code, there is the possibility of exceptions during execution. In the case of exceptions, this is displayed in Burp and more detailed information including StackTrace is displayed when the Bambda filter is opened.
Bambdas can be used, for example, to hide requests that contain /resources/ or /image/ in the request path respectively the URL. At the same time, interesting history items such as those that have /api in the request path can be coloured green and those that contain /graphql can be coloured yellow. In the following example, history items that contain .js in the request path are additionally coloured magenta.
String requestPath = requestResponse.request().pathWithoutQuery();
if(requestPath.isBlank()){
return false;
}
if(requestPath.contains("/resources/") || requestPath.contains("/image/")){
return false;
}
if(requestPath.contains("api")){
requestResponse.annotations().setHighlightColor(HighlightColor.GREEN);
}
if(requestPath.contains("graphql")){
requestResponse.annotations().setHighlightColor(HighlightColor.YELLOW);
}
if(requestPath.contains(".js")){
requestResponse.annotations().setHighlightColor(HighlightColor.MAGENTA);
}
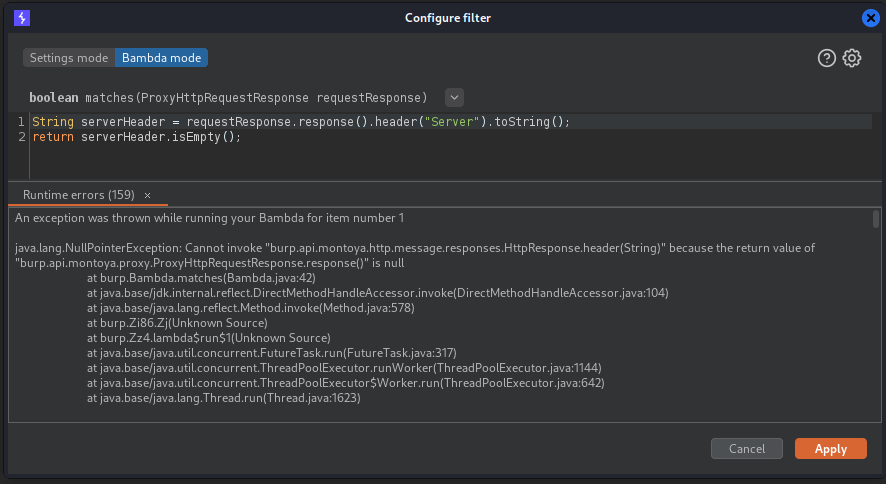
return true;Bambdas can also be used to filter server response headers used, such as Server or X-Powered-By. You can then manually check whether the result is a disclosure of information.
// in case of no response
if (!requestResponse.hasResponse()) {
return false;
}
var response = requestResponse.response();
// Header Server or X-Powered-By is present
if (response.hasHeader("Server") || response.hasHeader("X-Powered-By")){
String headerServer = response.headerValue("Server");
if(headerServer==null || headerServer.isBlank()){
return false;
}
} else {
return false;
}
return true;Further examples can be found in the Introduction from PortSwigger to Bambdas. PortSwigger also maintains its own Github Repository for Bambdas, which users are welcome to expand.
In future, PortSwigger would like to integrate the expandability of Burp using Bambdas at additional locations as in the central search function. Enable pre-filtering for intruder attacks and integrate Bambdas into the capture filter for the logger and HTTP listeners. The aim is to be able to combine several simple Bambdas to perform complex tasks in one tool.
The integrated scanner in Burp Suite already comes with a large number of scan checks for a wide range of known vulnerabilities such as SQL injections, cross-site scripting, XML injections and many more. With BChecks, the integrated scanner can be easily extended with customised checks directly in Burp Suite itself. Product-specific vulnerabilities are often not included in the scan checks supplied and can therefore be added using BChecks.
BChecks have been added with the 2023.6.2 release of Burp Suite. These are located within the Extensions tab and can be imported, created and modified there. In the last stable release before the publication of this article (2023.11.1.3), Syntax highlighting was added to the BChecks Editor. PortSwigger also maintains a Github Repository for BChecks. With the early adopter release 2023.12.1 a formatting function for BChecks was added, this can be done by right-clicking in the editor.
BChecks can be used to create scan checks for product-specific vulnerabilities that are not yet included in Burp Suite, some examples can be found in the PortSwigger article. BChecks can also be used to detect server response headers that are not set ideally, the following example is about the configuration of the HTTP Strict-Transport-Security header:
metadata:
language: v2-beta
name: "HSTS Header Check"
description: "Checks used HTTP Strict-Transport-Security Header"
tags: "passive"
author: "rame"
given response then
if "Strict-Transport-Security" in {latest.response.headers} then
if ({latest.response.headers} matches "Strict-Transport-Security:\s*max-age\s*=\s*([3-9]{1}[0-9]{7,})") then
if not({latest.response.headers} matches "preload") and
not({latest.response.headers} matches "includeSubDomains") then
report issue:
severity: low
confidence: firm
detail: "Unsecure HSTS Header in use: no includeSubDomains and no preload set."
remediation: "Include \"includeSubDomains; preload\" in HTTTP Strict-Transport-Security Header."
else if not({latest.response.headers} matches "preload") then
report issue:
severity: low
confidence: firm
detail: "Unsecure HSTS Header in use: no preload set"
remediation: "Include \"preload\" in HTTTP Strict-Transport-Security Header."
else if not({latest.response.headers} matches "includeSubDomains") then
report issue:
severity: low
confidence: firm
detail: "Unsecure HSTS Header in use: no includeSubDomains set"
remediation: "Include \"includeSubDomains\" in HTTTP Strict-Transport-Security Header."
end if
else then
if not({latest.response.headers} matches "preload") and
not({latest.response.headers} matches "includeSubDomains") then
report issue:
severity: medium
confidence: firm
detail: "Unsecure HSTS Header in use: max-age too short, no includeSubDomains and no preload set."
remediation: "Set HTTTP Strict-Transport-Security to max-age=63072000; includeSubDomains; preload."
else if not({latest.response.headers} matches "preload") then
report issue:
severity: medium
confidence: firm
detail: "Unsecure HSTS Header in use: max-age too short and no preload set."
remediation: "Include \"preload\" and increase max-age in HTTTP Strict-Transport-Security Header."
else if not({latest.response.headers} matches "includeSubDomains") then
report issue:
severity: medium
confidence: firm
detail: "Unsecure HSTS Header in use: max-age too short and no includeSubDomains set."
remediation: "Include \"includeSubDomains\" and increase max-age in HTTTP Strict-Transport-Security Header."
end if
end if
else then
report issue:
severity: medium
confidence: firm
detail: "No HTTP Strict Transport Header in use"
remediation: "Set HTTTP Srict Transport Security to max-age=63072000; includeSubDomains; preload"
end ifThe BCheck Definition Reference from PortSwigger can help enormously with the development of BChecks, as it contains a good overview of the possibilities and information about the necessary parts of a BCheck. Further examples can be found in the BChecks Repository of PortSwigger.
Release 2023.10.2.2 of Burp Suite includes the option to test BChecks. The testing of created or imported BChecks takes place in the BChecks Editor. To do this, history items from the HTTP proxy history are added to the BChecks Editor as test cases via Send to BCheck editor, which can now be found in the right-click context menu in the HTTP proxy history. The BCheck can then be applied to the selected test cases in the BCheck editor using Run Test. The result can then be viewed in the Audit items, Event Log, Logger tabs and the vulnerabilities created from the BCheck in the Issue activity tab. This testing method was introduced to find out why false positives arise from a BCheck and to improve and simply retest it.
Nothing is currently known about the future development and expansion of BChecks.
With BChecks, you can quickly develop and use your own checks for product-specific vulnerabilities. The introduction of Bambdas in Burp helps users to control the filtering of history items more precisely and to implement their personal preferences in the highlighting simply and automatically through the Bambdas created. The introduction of Bambdas in other places is very promising and encourages small automations and customisations without the development of dedicated extensions. In addition to Bambdas and BChecks, Burp Suite also supports macros, which Andrea has addressed in the article Burp Macros – How to use them correctly.
Our experts will get in contact with you!

Ralph Meier

Ralph Meier

Ralph Meier

Ralph Meier
Our experts will get in contact with you!