Burp Bambdas & BChecks
Ralph Meier

How to analyse Android apps with Frida
Frida is a toolkit for dynamically analysing Android devices or rather their installed apps and running processes. The core of Frida is written in C and offers the option of injecting QuickJS into the target process. QuickJS is a small, embeddable JavaScript engine that complies with the ECMAScript 2023 language specification. Frida works best with a rooted device, but there are also ways to perform tests or analysis with a non-rooted device. In the article on the introduction to iOS Mobile Application Testing there is an example with Objection but for iOS, which works without jailbreak or root. Frida can be used to gain access to the memory (RAM and main memory) of the target device, overwrite methods from apps, hook into a method, intercept or manipulate inter-process communication (IPC) and bypass various protection mechanisms such as root detection or certificate pinning.
Frida offers three different modes:
This is the most common mode and includes the functionality of attaching or hooking into an existing app at startup and embedding additional logic/code. Frida-Core provides the necessary functionality by integrating GumJS as a shared library into existing software and thus establishing bidirectional communication and removing it again at the end. In addition, frida-core also provides basic functionality: Listing installed apps, running processes and connected devices. Frida-server is the required counterpart on the mobile device, which is copied to it and started. The running frida server provides the functionality of frida-core via an open TCP port.
This mode is selected for non-jailbroken iOS devices or non-rooted Android devices. In this case, the frida-gadget is integrated into the app to be analysed. It can then be interacted with using Frida-based tools such as frida-trace. This mode includes the Objection tool, which is illustrated in the article iOS Mobile Application Testing – An Introduction.
This mode includes the autonomous execution of scripts from the file system using frida-gadget without external communication.
Installation is easiest with a rooted Android device that is connected to the computer via a cable. This variant works as follows:
sudo apt install adbpip install frida-tools pip install fridaadb start-serveradb devices -l to check whether the device is connected to the computeradb root and then adb shell adb shell and privilege it with su to a root shell sessionadb push frida-server /data/local/tmp/ chmod 755 /data/local/tmp/frida-server/data/local/tmp/frida-server & in the ADB shell. adb shell "su -c /data/local/tmp/frida-server &"The device can then be accessed using Frida. Here are some helpful commands:
Query active processes
frida-ps -U
Query running applications
frida-ps -Ua
Query installed applications
frida-ps -Uai
Terminate a process
frida-kill <PID>
At the end of the analysis, the ADB server should be terminated by adb kill-server.
Now that we have learnt what Frida is, what modes there are and how Frida is installed, here are some examples of how it is used.
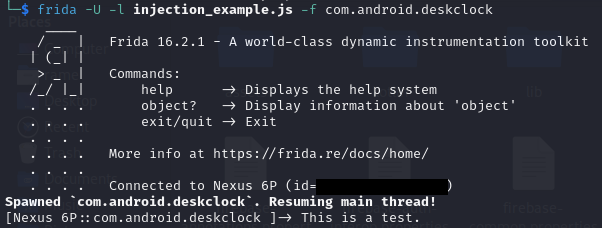
As a first example, we will use the JavaScript file injection_example.js with a simple console output:
Java.perform(() => {
console.log("This is a test.");
});We can inject these into a running process with the following command:
frida -U -l injection_example.js Clock
With the following command it is possible to start a process and inject the desired code into it:
frida -U -l injection_example.js -f com.android.deskclock
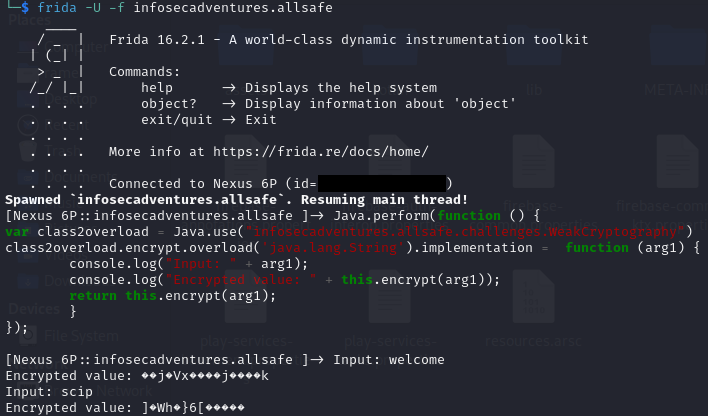
With the following code, the encrypt method of the WeakCryptography class is overwritten and extended by two console outputs and then the original encrypt method is called so that the app continues to function as intended.
Java.perform(function () {
var class2overload = Java.use("infosecadventures.allsafe.challenges.WeakCryptography")
class2overload.encrypt.overload('java.lang.String').implementation = function (arg1) {
console.log("Input: " + arg1);
console.log("Encrypted value: " + this.encrypt(arg1));
return this.encrypt(arg1);
}
});This code is injected into the running process after the app is started using Frida.
The Allsafe App used is an intentionally vulnerable Android app with various challenges for learning Android app testing, also in conjunction with Frida.
Frida operates a CodeShare Repository , which contains a variety of useful scripts, for example to bypass protection mechanisms such as certificate pinning, root detection, Wi-Fi checks, intercept communication, hook into methods or perform static analyses. The source code can be viewed in the respective projects and can either be copied out or executed directly with the parameter --codeshare and the entry of the desired project using Frida on the console. When executing with the codeshare parameter, the fingerprint below the source code should be compared with the one in the console. In addition, all code should be checked before execution in order to prevent unwanted side effects.
The protection mechanism for detecting a rooted device is often used to partially or completely restrict the functionality of the app in the event of detection. To bypass this on a rooted Android device for an analysis, there are already existing, detailed injection scripts on the Frida CodeShare repository. fridaantiroot is currently the best-known injection script and can be used as follows:
frida -U -f infosecadventures.allsafe -l anti_root.js frida -U --codeshare dzonerzy/fridantiroot -f infosecadventures.allsafe
However, it is possible that the fridaantiroot injection script does not work against the protection mechanism used. In this case, a way would have to be found manually by decompiling and extending it in the injection script or creating a new script.
There are several ways to bypass an imposed certificate pinning protection mechanism. You can decompile the APK file, remove or adapt the code responsible for certificate pinning, recompile the APK and then sign it. A second way, which requires less effort, is to use an injection script with a certificate pinning bypass to circumvent the protection mechanism. There are already a number of certificate pinning bypass projects in Frida’s CodeShare repository, some of which are very sophisticated and can bypass several different protection mechanisms. The two most popular projects at the time of writing are Universal Android SSL Pinning Bypass with Frida and frida-multiple-unpinning. The first project allows you to inject your own certificate, while the second project supports a larger number of certificate pinning variants, including many rather old methods. This allows you to quickly check whether certificate pinning in the Android app can be easily bypassed.
Dynamic analyses of apps are a good extension to an existing static analysis and can help to confirm bugs and bring additional vulnerabilities to light. Frida is a comprehensive toolkit with different modes, which can be used on rooted/jailbroken devices and with the embedded mode also with regular devices. With the Frida toolkit you can easily inject code into a running process, hook into a method and overwrite existing methods of an app. There is a huge CodeShare repository with a large number of existing Frida injection scripts for many different analyses or bypassing protection mechanisms.
Our experts will get in contact with you!

Ralph Meier

Ralph Meier

Ralph Meier

Ralph Meier
Our experts will get in contact with you!