Microsoft Cloud Access Tokens
Marius Elmiger

How to detect Attackers faster with Honeytokens
An attacker enters the playing field of a defender as soon as a compromise usually of an endpoint has taken place. From now on, an attacker has different ways to explore the defenders playing field, imaginable as in the game Minesweeper, which probably only the older generation among you knows.
The task as a defender is to detect and block the attackers as quickly as possible before they can access critical data. To achieve this, defenders usually use a variety of security tools these days, which, among other functionality, collect logs from the endpoints. However, based on our red teams, we can say that although our actions were occasionally recorded, they mainly got lost in the noise. What could be the reason? One reason could be that we as Defenders tend to be not creative enough. We work through lists to make our systems safer but pay too little attention to the playing field of an attacker. Or quoting John Lambert (2015):
Defenders think in lists. Attackers think in graphs. As long as this is true, attackers win.
So how can we make the playing field more difficult for attackers? As a first step, attackers usually try to collect additional information about the IT environment. This action occurs either on the endpoint or over the network to services such as Active Directory, File servers, or other IT systems. One effective way to detect this attempt can be to utilise Honeytokens. To do this, we set out traps on our playing field, imaginable like the mines in Minesweeper.

It is essential to think like an attacker when placing Honeytokens, with the aim to provoke an early alert by an attackers actions. When triggered, it is up to the defender to react as quickly as possible to identify the involved entities and drive the attackers off the playing field.
Honeytokens are available in different variations. The following chapter describes one example by using an Active Directory Honeytoken.
Active Directory is ideal for attackers to gather information about the IT environment. Comparable to Google Maps, we search for a good restaurant or attractions, attackers look for a simple path in Active Directory to get to privileged objects. Various tools can be used to query information from Active Directory, such as dsquery.exe, dsa.msc, SharpHound, ADExplorer, PowerView and many more which we will not describe further in this article. We are more interested in the query itself. To query Active Directoy, LDAP or LDAPS is used. We could record the LDAP request, or more straightforward, we can record the property requests on domain controllers with the help of System Access Control Lists (SACL). SACL’s are generally underused compared to Discretionary Access Control List (DACL). Unlike a DACL that controls access to an object via SIDs, SACL allows access to an object’s audit ACE. An audit ACE describes whether particular actions on an object was successful or not. A recommended article for profound research on the subject of ACL’s is the An ACE Up the Sleeve document published by the company SpecterOps.
From the two existing SACL categories, Object Read and Object Write, we will only use the Object Read category to record Active Directory property access. The procedure to create a Honeytoken account and assign the correct SACLs is as follows:
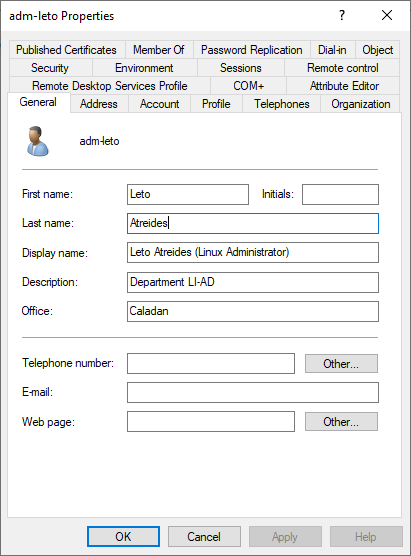
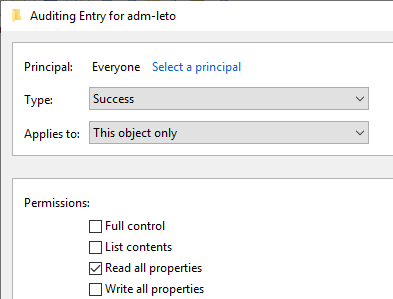
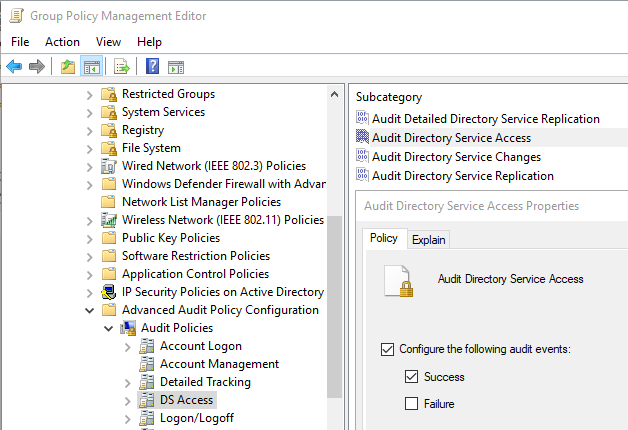
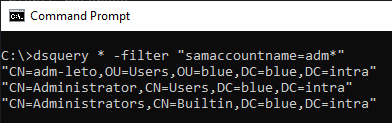
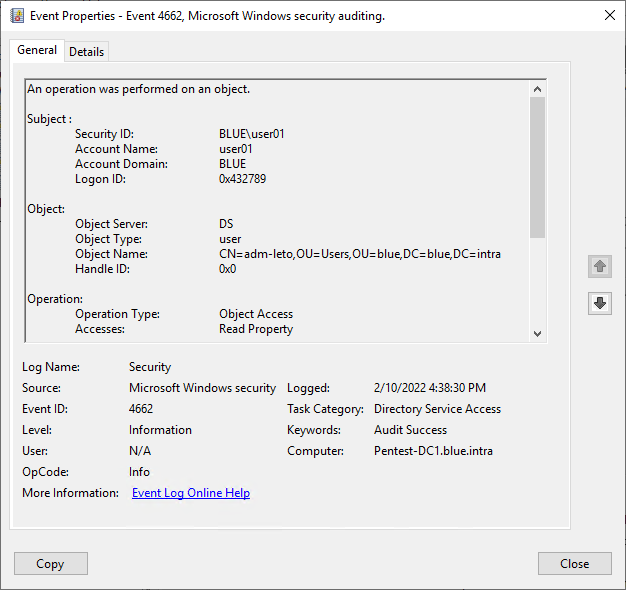
With the above Honeytoken, you should from now on be able to spot attackers when they read out the entire Active Directory or, in our example, search specifically for adm* accounts. However, it should be noted that false positives can occur if the Honeytoken account was created in an OU where legitimate administrators often run queries or by 3rd party applications such as an identity management system. Alert exceptions may therefore be necessary to avoid false positives.
In Windows, there are a variety of Securable Objects such as:
SACLs can be set on all these objects. Files are ideal for Honeytokens and generate, like in the example above, the same event if visited. As a start for the file names, you can orient yourself on the PowerView function Find-InterestingDomainShareFile, which by default searches for file names such as pass, sensitive, secret, admin, login or unattend*. xml.
Numerous websites describe different types of Honeytoken implementation. Following are some links to tap into an endless well of Honeytoken creativity:
Creating effective traps in your IT environment requires both an attacker’s mindset and creativity. As we learned, Honeytokens can be designed for nearly every scenario and can give you the chance to tip off an attacker in the early stage of an attack. This initial signal can help you identify and stop an attack more quickly. You should create several Honeytokens in your environment by layering them according to the attack stages of an attacker. Important to say is that Honeytoken should not endanger your environment. Therefore, we are not recommending assigning privileged access rights to Honeytokens. As with everything in IT, test your Honeytokens if they are working as expected. At last, you should not only rely on Honeytokens. However, it is an effective technique that a defender can use to increase the attackers dilemma.
Our experts will get in contact with you!

Marius Elmiger

Marius Elmiger

Marius Elmiger

Marius Elmiger
Our experts will get in contact with you!