Brain before post
Michèle Trebo

In my 20+ years of experience in ICT Security (now known as Cybersecurity) I’ve fought many battles against bad intentions and prejudice. Sadly I must admit that cybersecurity still remains a difficult topic to handle for broad audience. Although our life has become incredibly “digitalized” in the past 25 years, people still forget that their digital identity is worth protecting.
I’m not only targeting privacy here. Our day-to-day tasks have become more and more “cyberized”: your payments, your clinical data, your social life, your tax declaration, your smart devices and finally even your car and home. The alternatives are slowly but surely fading away… Just an example: You may want to pay the old way, but you’ll have to add fees for each transaction. The trend is to force digital payments and in a (not so distant) future, cash transaction may disappear completely. So, be prepared to digitalize more and more your everyday tasks.
Usually I’m the first person asked when family, friends and people in my neighborhood get stuck on computer problems (and mostly are Cybersecurity related issues). Therefore I’d like to share some Cybersecurity hints that may help you protecting your digital identities and assets. Here is a list of essential strategies to follow (not only) for your personal use in every day’s life.
| Class | Mitigation Strategy | Risk |
|---|---|---|
| Authentication | Implement Multiple Two Factor Authentication (2FA) like Google Authenticator App or YubiKey on all services that supports it. And if the service you are using is not compliant, ask for a 2FA support statement. Here some well-known services that are making use of it: Apple, Google, Facebook & Dropbox. | Misuse of your digital identity that may lead to financial and reputation loss including possible legal prosecution |
| Encryption | You may have nothing to hide, but no one has the right to spy on you without a warrant signed by a judge. Therefore ensure you’re using encrypted connection whenever you use your browser, especially when using email or social media services – In general everything should be encrypted nowadays and be suspicious if not… always look for this sign (or equivalent) in your browser: | Privacy disclosure may lead to reputation loss, legal prosecution and lead to family issues |
| Compartmentalization / Segregation | Use a different device to accomplish critical and important tasks. The hassle and the possible financial loss will cost you much more than another device. Buy a notebook or tablet and use it for your e-banking transactions, payments and all other things you don’t want to share or compromise. Don’t use this device for email, messaging, gaming and generic web access (especially not for social media) | Misuse of your digital identity that may lead to financial and reputation loss including possible legal prosecution |
| Cloud Services | Activate Dual Factor authentication wherever supported here’s a short list of services that supports it: iCloud/appleID (Apple), LiveID (Microsoft), Facebook, Dropbox, Google Services (including Gmail) – You definitely need to activate this service, it is very easy to get your password if you’re not careful (I’d better say paranoid) and it takes only one take to compromise your identity. You can define trusted devices that will not require a second factor login after the first time | Misuse of your digital identity that may lead to financial and reputation loss including possible legal prosecution |
| Data Storage | Don’t trust any USB storage by default (especially USB sticks) if you have a trusted device make sure you use only storage you can trust yourself – use another computer device for sharing data that is not fully trusted – use your trusted storage (stick or whatever) to transfer data between your digital assets. | Malware infection, data loss or theft |
| Mobile Device | Encrypt your device storage and use a reasonable password for it (not a 4 PIN code) leverage the fingerprint sensor if available. Install only known good Apps, if you need to test and/or play buy another cheap mobile device: your smartphone is becoming your new wallet – it is worth protecting it, especially if used as an authenticator token (like with the Google Authenticator App) | Misuse of your digital identity that may lead to financial and reputation loss including possible legal prosecution |
| Messaging | If you really care about your privacy when communication with friends make sure to use on of those: Signal, Threema or wickr – Be aware of one thing: communication privacy depends not only on your device/environment security measures but also on the security measures of the receiver device/environment! Therefore if you want to have control on what you send you must use those tools. Here are some features that will explain my recommendation: thoroughly tested end-to-end encryption, assured person and device identification, APP authorization, message lifetime (you may define how long a message is displayed), screenshot detection… You see, it may not be perfect but it is much more than others offer by default… | Privacy disclosure may lead to reputation loss, legal prosecution and lead to family issues |
Probably the most effective strategy would be using a better authentication to your digital services and digital assets.
| Step | Description | Picture |
|---|---|---|
| Yubikey | I use YubiKey to authenticate myself to my workstation (MacBook), SSH servers and Google Services daily. Those keys are not too expansive and work well, virtually indestructable they cost 50 USD in single resale and you can order it via web-shop and get it shipped here in Switzerland for about 58 CHF (there is also a Fido U2F version supporting only like Google, Facebook, Dropbox and alike, that will cost less than half price – check here for more information). |  |
| Computer Login | This is how it looks like in action, on MacOS you login with your username/password and the system will send a challenge to the inserted key – otherwise the login will not succeed. Same behavior is supported on Windows and Linux. |  |
| Gmail Login | After the first login with username and password Gmail is requesting my Yubikey to continue. In case you lost your key you may request an SMS token to your mobile or use a code from a previous generated password list (that you keep in a safe place of course) – Finally you can use Google Authenticator as an option to a hardware Yubikey token. | 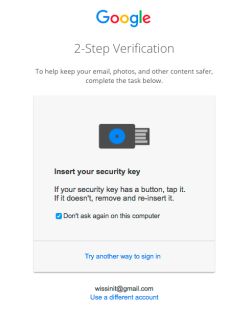 |
| Apple ID | If you need to login with your Apple ID (like here in iCloud) and your using an untrusted device like the one at your friend’s place or in the hotel lobby you’ll be requested to provide a two-factor verification mode… | 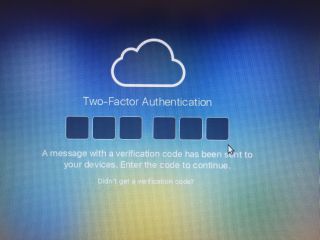 |
| Apple ID | …now on your trusted device like your iPhone or iPad for instance, you’ll get a request confirmation. You’ll see the Geo-Coordinates from where the request is coming (for plausibility check) and if you don’t recognize the request just don’t allow it. | 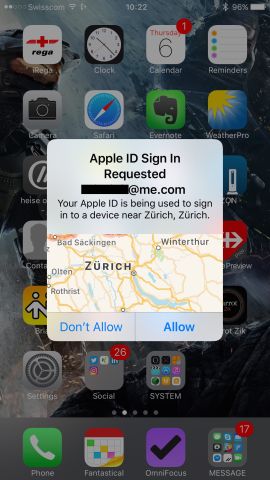 |
| Apple ID | …once allowed, you’ll get the verification code (6 numbers) to insert in your application or web interface. | 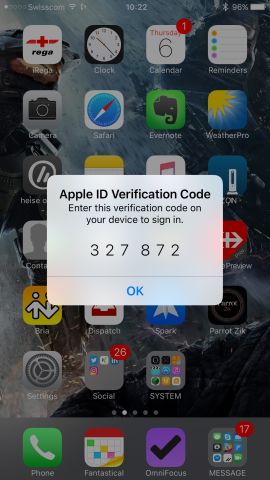 |
Digital Identities are here to stay. You may think you don’t need it, but you already have one. Take step to secure your digital life as you already do with all things you care. Ignorance is not bliss in this realm…
Our experts will get in contact with you!

Michèle Trebo

Ralph Meier

Tomaso Vasella

Eric Maurer
Our experts will get in contact with you!