Over the course of renewing or updating their IT and network infrastructure many clients will make extensive use of IT infrastructure and network virtualization. During this process, there is a need to address the rising Intranet threat level. The traditional perimeter security paradigm alone is no longer sufficient.
Therefore a solution is in demand that allows segmenting the site network into many (typically 5 to some 100 in extreme cases) network zones. The traffic between these zones should be controlled in such a way that unwanted traffic is blocked and allowed traffic is intelligently analyzed to eventually stop malware from spreading. It should also stop attacks and attempts at using backdoors or remote control of the system.
By making extensive use of VLAN technology (IEEE 802.1q), it should be possible to invent a central point of intervention. This article wants to help generate a questionnaire with the goal to help customers to get an overview of vendors, products and technology best suitable to act as such central point of intervention.
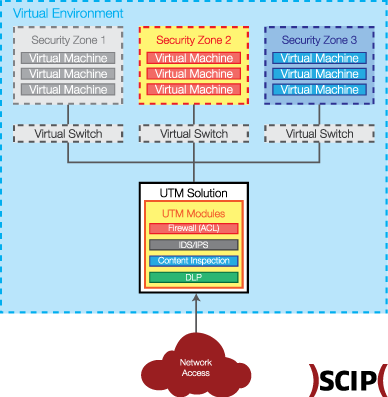
The following picture shows a rather generic overview of the architectural design of such solution:
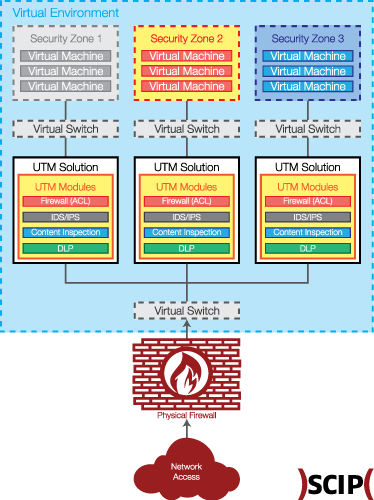
A more advanced version of the same architecture could look like this:
Background
The typical site, for which the envisioned solution is intended, will make heavy usage of hardware virtualization and IEEE 802.1q based network virtualization. VLANs will not only exist on top of the server virtualization platform but also within the site’s physical LAN infrastructure.
A central point of intervention is foreseen, where all VLANs connect to and all traffic between network zones can be controlled (see picture above). Depending on the site’s IT infrastructure and risk profile, the central point of intervention could materialize as a virtual or physical appliance. The products, which will be selected as standard, should be available in both shapes or at least allow for an easy integration into the highly virtualized infrastructure.
Overview
For the depicted IT and network environment, clients need an UTM gateway, which protects Intranet sites from each other and internally divides the site network into security zones. It also isolates failure and attacks within the single affected zone and provides alerts and information about incidents above a certain level of criticality.
All traffic that can be blocked on a basis of the IP protocol header should be blocked. For all other traffic it should be possible to decide if and what further inspection of the payload should be done. After such inspection further actions should be decided on, like blocking, alerts and/or logging.
Requirements
We define an UTM to be a network security device that at least fulfills the following requirements:
- UTM Intranet Gateway as virtual appliance or as physical appliance
- Packet filtering Firewall (context sensitive)
- Takes advantages of hypervisor technology (introspection)
- Includes IPS/DPS and content inspection engine
- Allows (layer 2) interface spec. in filtering/blocking/logging rules
- Malware detection (IPS/DPI, signature based)
- Malicious remote control detection (IPS/DPI, signature based)
- Attack and malware detection, heuristic/behavioral based
- Specify which protocols are known and supported for requirements 6, 7 and 8
- Specify how often and when (triggers) you deliver updates of signatures. How long will it take to deliver a dedicated update to mitigate a new high risk vulnerability?
- Allows application of IPS/DPI engine only on an as-needed basis (pre-selection packet filter)
- Allows flexible configurable logging rules
- Provide MITM HTTPS proxy, configurable (pre-selection packet filter). Note that HTTP can be analyzed with or without a proxy.
- IPS, allow the detection of encrypted data in arbitrary streams
- IEEE 802.1q support with at least 1000 VLANs
- Trunking with virtual and physical switches
- Bridging connections to vNICs, untagged min. 128 VLANs
- Routing between zones, please specify routing protocols
- Describes the possible high availability and load balancing options which your product provides
- Allows easy fall back to previous rule/configuration set(s). Allows to maintain several rule sets, with easy switching to active state.
- Update service: provides IPS/DPI compensating control rule packages for new high risk attack patterns
- Intelligent self-diagnosis to alert on conflicting and/or highly vulnerable rule sets
- Is it possible to manage many of such devices from a central location? If so, does it support three or more management centers with a formal handover process?
- Allows tamper safe logging, i.e. is it possible to configure logging in such a way that log entries, once written, cannot be deleted or changed.
- Allows to be tied into market leaders log analysis solutions
- Worldwide second and third level support availability
- Is it protected against self-lockout with remote management?
- Has detection and protection against unauthorized changes to its core operational modules (assured self-operation)
Costs
Because money is always important, we need to take a closer look to the possible costs you should ask to provide an example configuration of a physical appliance and a virtual appliance along with rough cost figures for the following two scenarios:
- Annual license cost or write-off (three years) for licenses which have to be bought
- Additional annual services costs (if any) for updates and third-level support
- Typical one-time installation and configuration charges
Costs for other mandatory or strongly suggested parts or services
Scenario 1: very small (XS)
- Two user access and general service zones with a total of 50 users and two VLANs with 100 Mbit/s connections. Three Servers with one (100Mb) NICs each.
- Three business application zones with a total three Servers with 1 (1Gb) NICs each.
- Three production control network zones comprised of one VLAN (100Mb) each. A total of 200 devices with one NIC (100 Mbit/s) each.
- One up-link connection to the backbone with 34 Mbit/s
- Needed throughput, firewall (packet filtering): Site-internal and up-link cross zones, aggregate 1 Gbit/s
- Needed throughput, IPS/DPI/IDS, aggregate 300 Mbit/s
Scenario 2: large (L)
- Redundant installation at 2 sites where all data center installations are duplicated
- Interconnection with a WAN link with 100 Mbit/s
- One up-link at each site with 100 Mbit/s throughput
- Five user access and general service zones with a total of 300 users and five VLANs with 1 Gbit/s connections
- Five Business application zones with a total of 15 servers (fully duplicated) with one active NIC at 1 Gbit/s each.
- Ten Production control network zones with a total of 500 devices connected (100 Mbit/s)
- Needed firewall (packet filtering) throughput, cross zones, aggregate 3 Gbit/s
- Needed IPS/DPI/IDS throughput, cross zones, aggregate 1 GBit/s
I hope this article will give you a hint on what to look out for your day-to day fight to secure your (virtual) environment.
About the Author
Andrea Covello has been working in information security since the 1990s. His strengths are in engineering, specializing in Windows security, firewalling and advanced virtualization.


