On January 1st, 2015, the Finma, the Swiss Financial Market Supervisory Authority, circular Operationelle Risiken Banken (translation: Operational Risks Banks) went into effect.
It appears to me that it’s time that we have a look at the implementation of the circular in connection with the requirements towards risk management when dealing with electronic customer data after banks have implemented various preparatory and implementationary measures.
Basically, the circulatory cements the Principles for the Sound Management of Operational Risk established by the Basel Committee for Banking Supervision. Among other things, the principles define the responsibility for management of operational risks at the highest level. They also demand that banks have a framework, a controlling mechanism and a technology infrastructure that allows the identification, limitation and surveillance of these risks adequately. So basically, you could say that the Circular offers nothing new from the standpoint of a responsible risk manager.
You could conclude that the Finma circular aims to establish a regulatory standard in Switzerland based on international standards. However, the intentions of the circular are more far-reaching than that due to the fact that operational risks covers an entire spectrum of events that range from legal incidents such as fraud to IT related incidents.
Due to the fact that incidents with electronic customer data have manifested not only in other countries but also in Switzerland, they have moved into the focus of interest. Therefore, Finma defines nine basic rules in Annex 3 of the circular. These basics seek to govern the management of risks in connection with confidentiality of electronic customer data of natural persons (private customers).
With this, Finma tries to apply lessons learned from a range of incidents that range from data theft at places such as HSBC Private Bank in Geneva, Credit Suisse, Bank Julius Bär, Hyposwiss to system manipulation within the bank itself to price fixing at Libor or foreign exchange deals.
Client Identifying Data
Regarding client identifying data (CID), the rulings of the circular are more detailed than when it concerns other risk areas. This relatively high degree of detailing was one of the main points of critique when it was presented as a draft to the interested finance institutions. Finma has taken this into account in the final version, but stuck to the basics of their regulatory concept.
Apart from the circular, bank-client confidentiality and data privacy regulation in Switzerland limit the access and transfer of certain data. These laws are applicable to data in any form – be it written, oral, electronic or of any other nature – that allow for a direct or indirect identification of current, former and potential clients, accounts of fiscal relationships.
Returning the to the topic of requirements towards risk management when dealing with electronic customer data, we would benefit from an overview of what types of CID there is.
Definition: Client Identifying Data
CID is information that allows the identification of a client or his relation to a financial institute. Therefore, we’re dealing with personal data according to the Federal Act on Data Protection, Article 3 regulation a.
There are three kinds of CID:
- Direct CID
- Characteristics: All unique identifiers that allow the direct identification of a client.
- Categories: Personal identification / Company identification / Electronic address data / Physical address data
- Examples: First name, last name, signature, e-mail address, social network IDs, private or business address, name of company
- Indirect CID
- Characteristics: Information that allows identification of a client only when combined with another bit of information
- Categories: Personal IDs in Public Registries / Customer identifiers / Career details
- Examples: Passport ID, ID Card, Social security number, Tax ID, Car number plates, customer number, IBAN/BIC, Account number, Safe deposit number, Contract numbers, User ID / Passwords, Card numbers (credit and debit cards), IP address (static, dynamic) / Career details
- Potentially indirect Client Identifying Data
- Characteristics: Information that only allows the identification of a client when combined with other information as well as other special circumstances
- Categories: Details of birth / details of family / details of living situation / professional profile / identifiers of company / non-identifying company details / details of personal relationships
- Examples: Day and month of birth, year of birth, nationality, age, gender, diplomatic status hobbies, memberships in professional, private or charity clubs, homeland, zip code, professional qualification, currency of account, credit rating, transaction data
Consequences of Use
The following overview shows which consequences the use of CID brings based on their type and sensitivity.
Direct and indirect CID
CID are always to be treated according to the Need to know / Need to have principle, regardless of whether they allow a direct or indirect identification of clients. The following points are to be adhered to and are of the utmost importance:
- No cross border data transfer
- No access to data unless they’ve been securely anonymized
- Data is only stored in encrypted form
- Data are only viewable by using a token or with prior consent of the client
Potentially Indirect CID
The sensitivity of potentially indirect CID can be divided into two categories:
- Personal identifiers
- Impersonal Identifiers
Their sensitivity varies from case to case, depending on the kind and amount of data, the application used to manage the data and the requirements towards the data such as the outsourcing relationship. To find a universally applicable rulebase is very difficult because it depends heavily on environment and the way the data is treated.
Some rules can be applied, though:
- Impersonal identifiers should never be show in a client context
- Data may be transferred cross border
- Watch out for toxic combinations: Combining one or more data points might lead to a pattern that allows for the identification of the client.
- The combinations and the possibility of them occurring must be investigated on a case to case basis
A violation of confidentiality of CID has occurred when CID has been exposed to unauthorized persons, regardless of whether they are team members of people from outside the company.
Most accidental violations of confidentiality of CID happen because team members are not aware of the proper treatment of CID. A term to note here are lack of risk awareness.
Violation of confidentiality can carry big risks. Among them are:
- Reputational damage for the financial institute
- Loss of clients or assets
- Legal measures concerning the financial institute
- Cost of court
- Payment of damages
- Disciplinary measures such as loss of job or prison sentences for those responsible
Challenges of Toxic Combinations
A toxic combination is the combination of data that allows for identification of clients in Switzerland by foreign interest parties that exploit insufficient or missing access controls or errors in processes. Accessing Swiss data from outside the country’s borders because of toxic combinations can lead to violation of Swiss law as well as regulatory presets.
Illustration of Toxic Combination
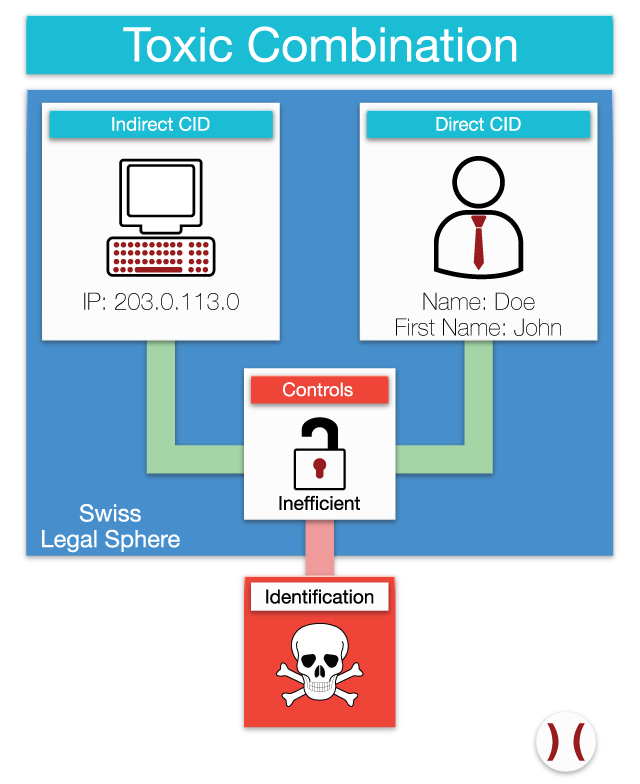
Strict and adequate division of CID is most likely the best way to ensure that users have no way of determining the identity of clients.
Toxic Combinations are highly likely to pose a challenge in the near future of regulations of financial institutes while said regulations will keep to become tighter.
There are first concepts on the horizon that deal with Toxic Combinations but the diversity, complexity of systems and environments as well as the factors of outsourcing and offshoring and the processes associated with all these things makes a pragmatic and risk based implementation difficult. On the other hand, these challenges could be used for a general overhaul of organizational and technological measures of protection. This could be a solid base for the adjustment of the business model as well as the processes.
General High Level Principles When Protecting CID
During the conceptual planning of the implementation of the Finma circular there need to be presets set and aspects respected.
- Clarity concerning the requirements on creation
- Which CID is stored in which applications?
- Need to Know
- Closer definition of Need to Know under the aspect of roles
- Closer definition of Need to Know under the aspect of functions
- Pay attention to Toxic Combinations
- Pay attention to other subject matters
The requirements should permeate all levels of hierarchy of a financial institute and should be addressed from the top down.
- Management: Attention & Awareness
- Definition of the CID mission
- Allocation of needed resources
- Communication
- Emphasis on importance of subject
- Team members: Attention & Awareness
- Information
- Workshops with key personnel
- Internal Controlling
- Assimilation of the requirements in the circular
- Updating of pre-existing CID processes
- Design of new CID processes
- Adaptation of guidelines concerning protection of client data
- IT
- Implementation revised need to know principle
- Conforming of standards
- Conforming of access rights
- Conforming of access concepts
The following overview is a possible and simplistic structure of the subjects that are to be dealt with:
- Types of Relevant Data: An official catalogue that categorizes client data has to, even if not complete, contain a number of categories that classify information about clients and their relationships. This catalogue needs to be organized by risk potential. In addition to that, the catalogue needs to be in harmony with pre-existing data classifications
- Relevant Forms of Data Revelation: Accessing or transferring the CID that fall under bank-client privilege can be done in different ways:
- E-Mail
- Data transfer
- Fax
- Portable memory
- Orally
- In writing
- Ruling: These methods must be regulated:
- Viewing by remote access such as online access to databases or applications
- Access by IT administrators
- Access by non-IT administrators
- Follow the Sun aspects
- Other aspects
- Protection of client data: Client data must be protected during its entire lifetime by adequate organizational and technological measures of security at all times. It needs to be protected against unauthorized revelation and use:
- Access concept and controls according to need to know and need to have principles and processes in order to ensure correct issuing and use of access rights
- Limiting electronic access to client data
- Limiting physical access to client data
- Disposal of client data that are not legally prohibited from being destroyed or are not bound to a law of conservation
- Implementation of confidentiality and security standards for external service providers that access client data and use it in any capacity, including the application of an adequate due diligence as well as surveillance of external service providers
- Need to Know and Need to Have for Legitimate Business Purposes: In order to implement the need to know principle, all access rights, excluding roles and functions, need to be assigned due to function. The challenge is to find a unified understanding of the need to know principle as well as the consistent application of it. The financial institute has to evaluate what meaning need to know carries internally and which employees get access to what CID based on their needs. Dealing with lists that contain CID is a very big task due to the fact that these lists often circulate outside the systematically manageable application and system environments. Access rights and confidentiality of these lists needs to be guaranteed without impacting efficiency, which poses quite the challenge that will need to be addressed in the future.
- Handing out Outsourcing Solutions: Protection of privacy and respecting client-bank privileges as well as the data protection act of Switzerland must be adhered to at any point in time. Outsourcing solutions and jobs including CID are not to be given out if the internal competences or resources are not adequate and when the security of the client data can’t be categorically guaranteed.
- Data revelation to third parties in countries outside Switzerland: Outsourcing solutions and delegation of jobs to third parties
- Confidentiality: Duties of all parties involved
- Cross Border Outsourcing Solutions: Informing of the client and possibility to end relationship
- Getting Approval: Necessary approval for cross border or external access to CID as well as transferring of CID to countries outside Switzerland or third parties before transfer happens.
- Implementation of Requirements towards Bulk Client Data: Bulk client data is CID that is statistically relevant compared to the entire population. Every financial institute has to decide what bulk data is based on its individual situation. This decision, however, needs to be understandable for auditors of the third party revision agency. Finma disagrees with the approach to define CID of two clients as Bulk Data. Therefore, Finma implies that each financial institute has to find its own definition and use that consistently.
- Control: Selection and surveillance of team members, list of key personnel. Financial institutes have to keep an up to date record of all key personnel. Finma points out the key personnel that has higher privileges which requires higher levels of security. This affects IT users with functional access to Bulk CID. What qualifies as key personnel has to be defined by every financial institute based on its individual criteria. To implement this into daily work is a delicate task seeing as it is not the goal of the list to claim all employees are generally suspected of being crooks.
Summary
The Finma circular demonstrates that the client-bank confidentiality will get better protection against external data theft if the circular is being observed. It is, however, only a guide and not a law. Regardless of the circular’s legal status, financial institutes need to take more note of these requirements. Despite the fact that the circulars are not legally binding, financial auditors are required to check banks for the adherence to the circulars. Therefore, the circulars have great impact on the operations of a financial institute. This includes enforcement that carries decisive power when court proceedings need judgment.
Considering the point at which the bank industry is currently at, it seems even more appropriate that banks change their paradigms to meet the guidelines the circular sets in terms of protection of CID. It is known that adapting to the guidelines is hard on resources and so is maintaining them on a day-to-day basis. Unfortunately, we observe that banks often see themselves close to the finish line but they’re really only at the start of the race. They often underestimate the complexity and act too lightly around this critical topic.
Here are the special challenges:
- Classifying and complete cataloguing of direct, indirect and potential CID including applications and systems
- Raised security requirements for privileged users
- Dealing with indirect CID and potential CID can lead to Toxic Combinations that can fall outside regular management
- Unclear or individual definitions of requirements such as CID where the meaningful definition and argumentation to auditors is something that is left to the financial institutions
- Cost/Benefit relation of some measures is questionable in everyday operations, leading to high costs for administration and other bureaucratic measures and might lead to inefficiency.
- Paradigm shifts need to happen with outsourcing partners, cloud services and others as well in order to enforce the need to know principle
- Data Growth and Data-Ownership.
- Cross-Border
- Individual aspects
However, there are a great many opportunities in the implementation of the circular’s guidelines that will benefit the financial institute greatly.
- Minimal standard for content that has been defined in both content and rules of engagement with electronic client data
- Risk based approach can be focused in both attention and resources to effective means of protection
- Possibilities of cleaning up access rights and create a more narrow definition of the need to know principle
- Basic socio-political discussion about and awareness of the most precious data and assets
- Controlling framework is tied into outsourcing providers
- Avoiding of regulatory arbitrage
- Strengthening of data protection with partners and third parties
About the Author
Flavio Gerbino has been in information security since the late 1990s. His main areas of expertise in cybersecurity are the organizational and conceptual security of a company.
Links





