Security Testing
Tomaso Vasella

How China uses its geopolitical factors in cyberspace
The following points are highlighted in this article:
China is a fascinating country. Think of the imposing great wall, the traditions and language, the culture, the people. In recent decades, China has not only developed into a global economic power, but is now also playing a leading role as a major technology player. Alibaba, Tencent, Baidu and TikTok have long been known beyond the country’s borders and have also become popular platforms in this country. However, China is constantly caught in the crossfire with other governments. Be it over the technological arms race with the USA or making headlines as a surveillance state and the persecution of dissidents. With over 1.4 billion people, China is the most populous and third largest country in the world in terms of area. The economy is growing rapidly, and cities such as Beijing and Shanghai are modern metropolises that are helping the country to achieve rapid technological growth.
| Population | 1.4 billion |
| Capital | Beijing |
| Surface | 9.6 million km2 |
| Time zone | CST (China Standard Time). Fun Fact: The time zone extends across the entire country |
| Languages and Dialects | Mandarin (68%), Cantonese (5%), Shanghainese, Hokkien, Tibetan, Uyghur, Mongolian |
| President | Xi Jinping |
| Form of government | Socialist People’s Republic |
| Government Party | Communist Party of the People’s Republic (80 million members) |
| Opposition party | No opposition parties |
| Administrative structure | Central government in Beijing, 22 provinces, 5 autonomous regions, Hong Kong & Macau Special Administration Zones |
But why does China in particular offer fertile ground for new technological developments that can keep up well (or even better) with international standards? Well, this question has to do with various circumstances, but is related to two fundamental factors, among others: Firstly, with the massive expenditure in AI systems, and secondly, the extensive data collection of their own population. The goal is clear: the country wants to become the world’s leading AI power by 2030. Investments of around 15 billion US dollars are planned, which corresponds to an increase of 50% within two years. China’s AI strategy, which was set out in the New Generation AI Development Plan, targets market development of around USD 150 billion and also aims to make AI army-ready.
The Chinese military PLA (Chinese People’s Liberation Army) also wants to introduce march missiles, unmanned aerial vehicles, control & command systems and the transfer of civilian AI companies to the army, which should accelerate China’s intelligent warfare. With command and control systems, Beijing has set itself the goal to centralize the planning and execution of air, space, cyberspace, sea and land operations. In addition, a cyber stronghold is to be established in Wuhan, where China will train experts in the field of cyber security for the army. In general, Wuhan is to become fertile ground for innovative start-ups and increasingly serve as a venue for national hacking competitions.
As the government has been collecting and analyzing data on its population for decades and has installed over one billion surveillance cameras in the country, it provides an ideal basis for training numerous algorithms and models. These massively favor China’s upswing in the face of AI technologies. The whole thing culminates in the so-called China’s Social Score System, in which the Chinese population is recorded and evaluated by the government’s extensive data collection.
But the eyes of the People’s Republic are not only focused on its own population: Other countries are also being targeted by the chinese government. National state actors are said to be spying on internationally relevant companies with targeted cyberattacks and espionage in order to find out the strategies of their competitors. In the Microsoft Digital Defense Report 2023, the US company lists various institutions that have been attacked by Chinese hackers. For example, the US defense and arms industry, various communication companies in the cloud and IT security sector as well as governmental companies are among their preferred targets. Of course, one could argue that the US has a certain self-interest in targeting China with such accusations in order to deflect attention from its own motives. However, an in-depth discussion of whether Washington is now attacking Beijing or vice versa is beyond the scope of this article.
Regardless of the tech arms race with the US, however, other countries are also in the sights of the Chinese government, as can be seen in the China Security and Risk Tracker analysis by Merics.
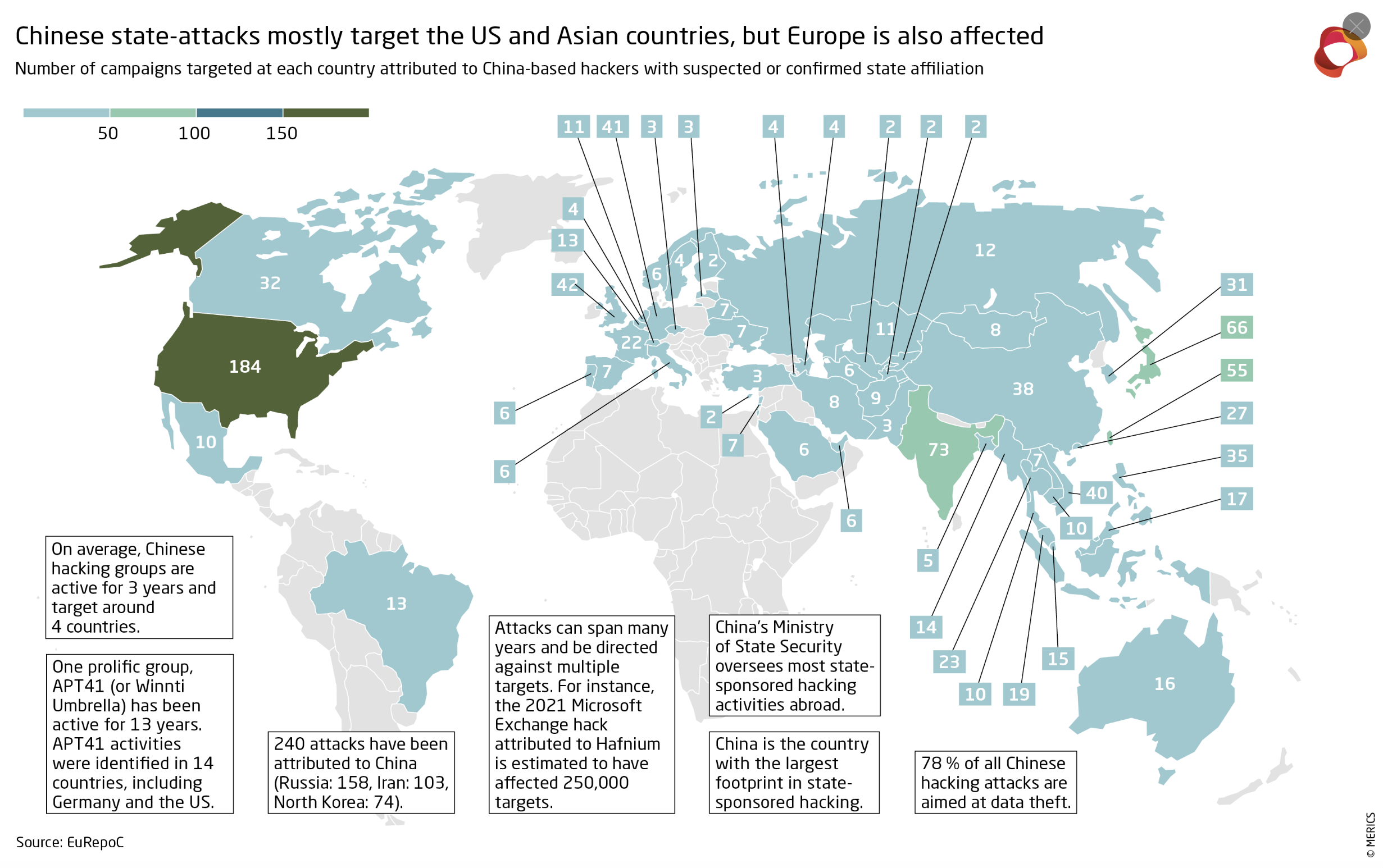
In the world of cyber security, we speak of differently motivated actors, all of whom pursue different goals. Nation-state threat actors have one vision above all: to better understand the plans and information of their adversaries and to gain a strategic advantage with the information advantage. Cyber espionage is therefore also a widespread tool for surveillance and spying in China.
On the one hand, these can be civilians working for the respective governments, intelligence services or the military. On the other hand, they can also be hacker groups that have been recruited by states and governments (or are financed by them). They are also known as ATPs, so-called Advanced Persistent Threats, which can be seen as a kind of project group within the intelligence service or the military. They collect information systematically and are usually involved in monitoring their targets over a longer period of time. Although they operate with complex instruments and specialized cyber know-how, their actions are anything but profitable, as they are primarily interested in procuring information and disrupting availability and the ability to act.
A Chinese hacker group does not necessarily have to have a direct connection to the government, but the evidence suggests that they are nevertheless linked to the PLA or the Ministry of State Security or the Ministry of Public Security. There are several ATPs operating in China. In 2023, these two groups in particular were active:
Raspberry Typhoon collects information thanks to targeted spear phishing campaigns in order to then spread its malware. Since the beginning of 2023, the group has been targeting ministries in the fields of trade and finance. Intelligence services are also among the potential interest groups of Raspberry Typhoon. Flax Typhoon, on the other hand, works with VPN-based solutions to gain access to networks at will in order to spy on its victims.
Before we explain individual geographical hotspots of conflict from China in more detail, it is important to clarify the following: it is never possible to know exactly whether these attacks actually originate from certain state groups or who exactly is behind various cyber attacks. This is because laying so-called false flags, is also a common tactic in the digital world in order to distract from the actual action. Let us now take a closer look at some examples that show that there is a valid connection between China’s geopolitical conflicts and its cyberattacks.
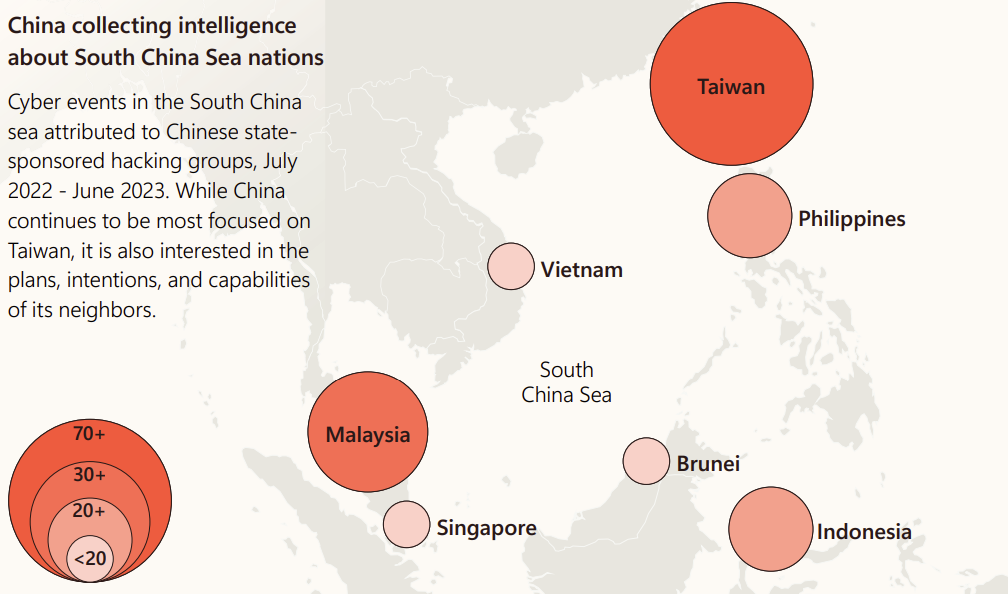
It is believed that China undertakes targeted cyberattacks on other governments, mainly to spread disinformation campaigns and obtain information through cyber espionage. This is no different in Taiwan. The territorial dispute with the island nation in particular is extremely contentious and has been going on for more than 70 years. It is probably one of the biggest areas of friction between China and the USA, and although Taiwan is actually an independent country, it has only been officially recognized by 12 states to date. Apart from geographical considerations, China also has a further economic interest in Taiwan being officially integrated into the People’s Republic. Taiwan is still the world leader in the production of semiconductors, which are used for the production of computer chips. The long-standing territorial disputes in the South China Sea remain unresolved, as many countries in the region claim the same sea areas and islands for themselves. This uncertain situation is an additional motivation for China to intervene not only in Taiwan but also in countries such as Malaysia and Indonesia in order to secure its influence there.
If you take a closer look at the chart below, you will notice that Chinese cyber events between July 2022 and June 2023 extend to various regions in the South China Sea, and are not just focused exclusively on Taiwan.
It is not just the South China Sea that is being targeted: The USA also recorded significantly more cyberattacks last year, which could be attributed to the Chinese government. Above all, China is said to be expanding its espionage activities on the USA in order to advance a so-called new Silk Road, with the associated regional policy. It is interesting to note the geographical location of the western Pacific island of Guam, which is 12,000 kilometers away from Washington D.C., but officially belongs to the USA as a foreign territory. Guam is home to the US Andersen Air Force Base and also serves as a naval base for the US Navy. Should a conflict between China and the USA actually occur, Guam could become an important geographic hub, especially as the island would also be quickly accessible by opposing actors.
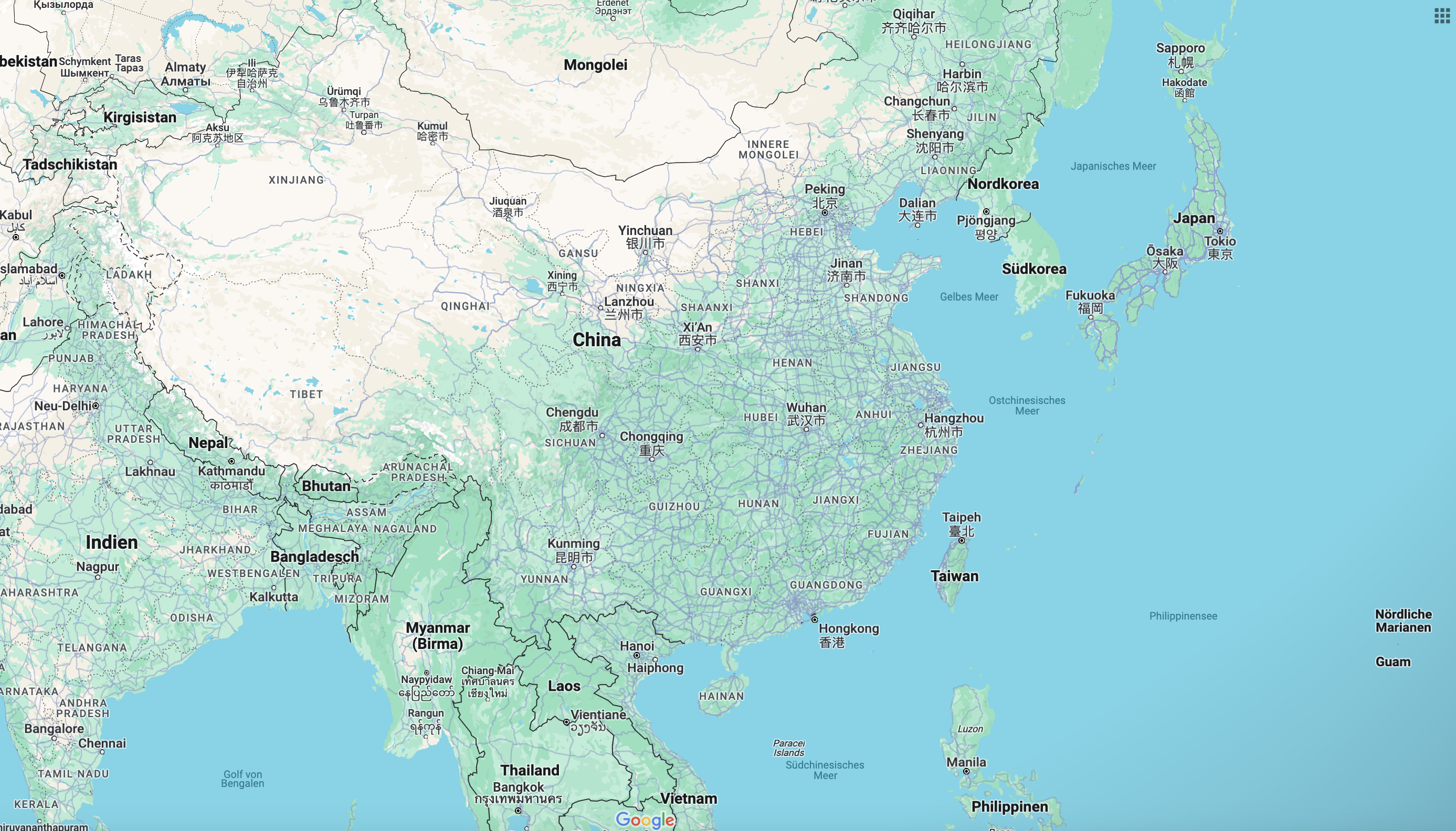
China is also fighting with its northern neighbor Russia over disputed territories. Towards the end of summer 2023, the People’s Republic redrawn its national borders, reassigning the north-eastern island of Bolshoi Ussuriysky to itself, even though the region belongs to Russia. This is about 100 km2 of new territory; however, the claim to ownership of the island was never confirmed by the Russian side. This raises the question of whether the territorial conflict on the Amur River could lead to a new crisis between China and Russia. However, as the Kremlin has been generously supplied with cars and electronics by Beijing since the war against Ukraine, it is not expected that Putin will stand up to Xi. It remains to be seen how long the game between the two rulers will last.
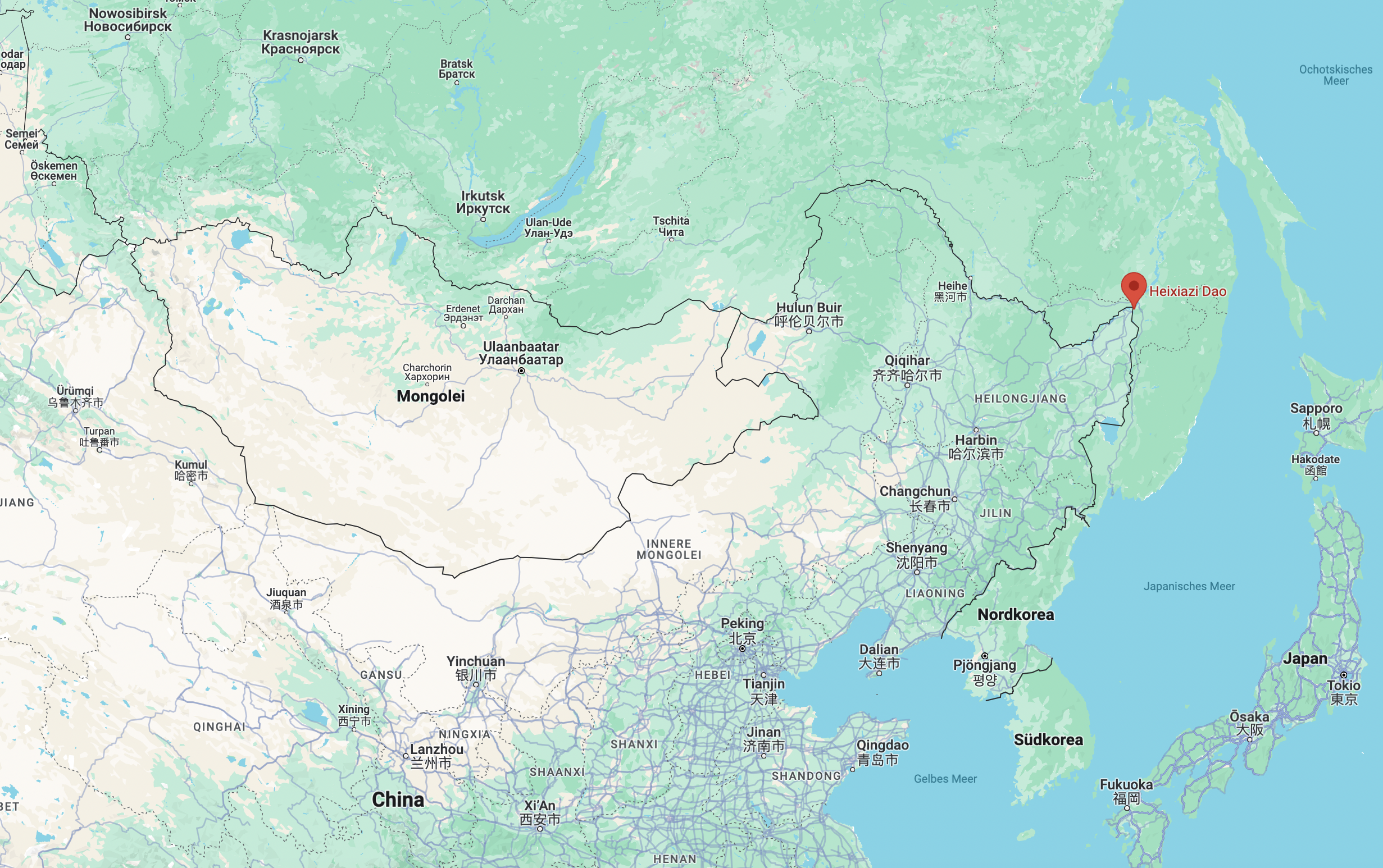
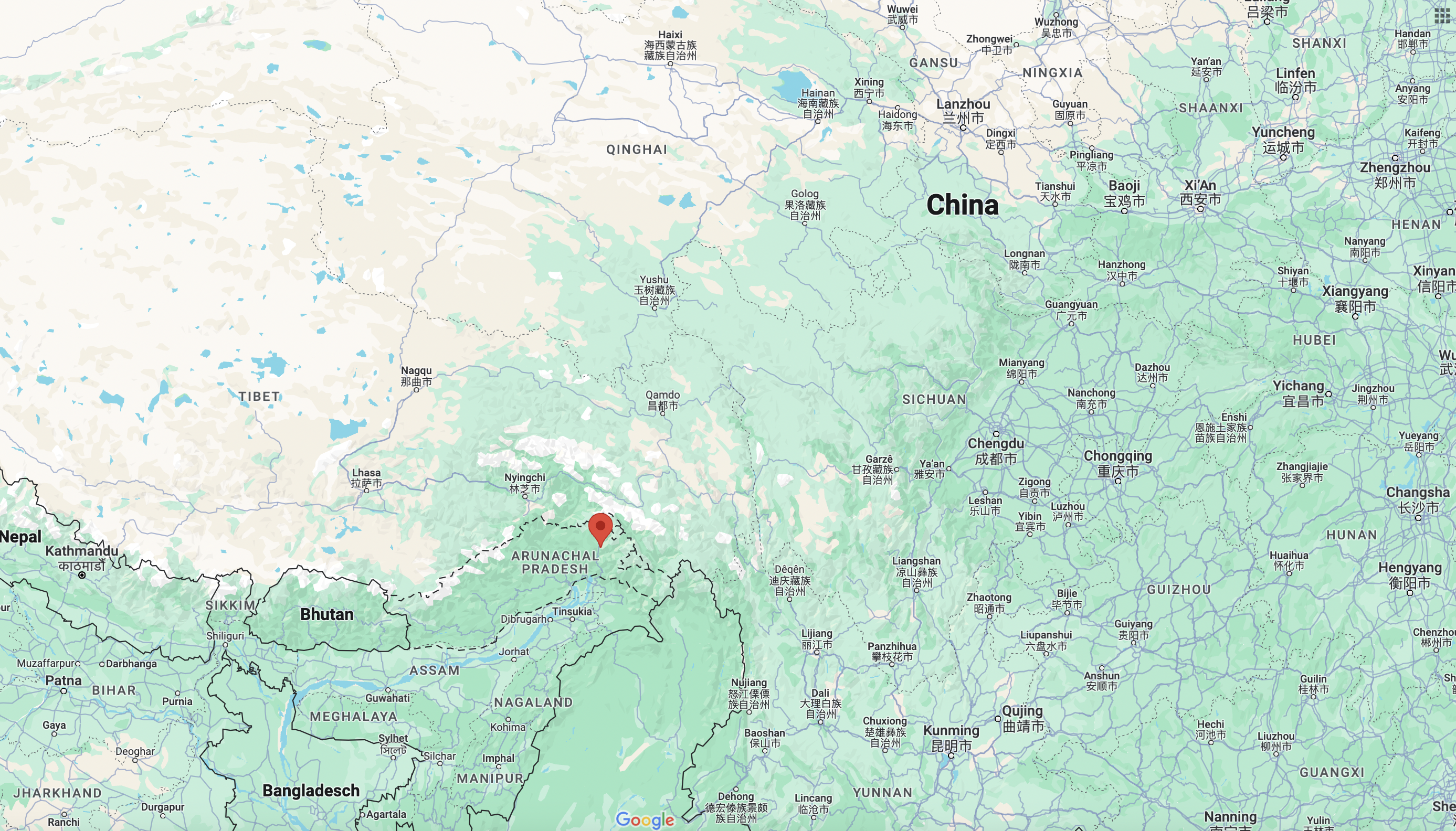
As part of the internally desired new map, the Chinese government has also claimed 3500 km2 of the border with India for itself. The state of Arunachal Pradesh was renamed South Tibet by the Chinese government. The mountainous region of Aksai Chin, which is located to the west of Tibet, is also claimed by China.
The African continent is increasingly becoming the focus of China’s disinformation campaign. In its Cybersecurity Forecast for 2024, Google assumes that the reason for espionage activities on African institutions is primarily resource-related. Rare minerals are used for high-end technical devices such as smartphones, TVs, laptops and hybrid and electric cars and are therefore essential for the associated production. China could therefore strengthen its economic and strategic position in Africa. By financially supporting authoritarian regimes, China would have another tactic to further spread its disinformation campaign.
In addition, the headquarters of the African Union was built and technologically equipped in Addis Ababa, Ethiopia, with the help of the Chinese government. The African Union has set itself the goal of securing sustainable peace, security and prosperity for the entire continent through cooperation. Between 2013 and 2018, the AU was the victim of several targeted cyberattacks that may have originated in China, and a similar picture is emerging in Burundi and Nigeria.
Nation-state threat actors, as in the case of China, are definitely a matter to be taken seriously. The year 2024, with its decisive events such as the Paris Olympics, the European Parliament elections, the presidential elections in the USA and elections in countries such as Taiwan, South Korea, Russia, Indonesia and India, will certainly provide ideal digital targets. The situation is currently coming to a head in Taiwan in particular, as presidential and parliamentary elections will be held on the island on January 13, 2024. It is therefore obvious that Xi Jinping wants to exert pressure on society there due to his aspirations for reunification. However, China’s geopolitical interests in the South China Sea would be reason enough to keep a closer eye on cyber incidents from the People’s Republic with regard to its election program in Taiwan.
In addition, Xi Jinping has set himself the goal with Made in China 2025 of relying more heavily on domestic innovation to boost the country’s own tech scene and make it a top tech high-end producer. Combined with the country’s AI efforts, we will also see Chinese activities in the areas of cyber espionage, dissident persecution and the dissemination of false information in 2024. At least that’s what Google predicts in its Cybersecurity Forecast for 2024.
However, nation-state threats do not stop in Beijing: Russia, Israel and North Korea have also been in questionable territorial disputes for decades. The current crises in the Middle East and Ukraine are exemplary of how physical conflicts have long since been transformed into digital warfare and aggression. And although China may be pursuing different goals than Russia or other states, with its numerous geographical friction areas, illegal annexation of border areas and the madness for geographical and political power, China’s state actors are unlikely to make any friends in the long term.
Our experts will get in contact with you!

Tomaso Vasella

Eric Maurer

Marius Elmiger

Eric Maurer
Our experts will get in contact with you!