How to secure your online accounts
Ian Boschung

Basics of iOS pentesting
In this article, we will only work with non-jailbreaked devices. Certain security aspects can only be tested on jailbroken devices and a thorough pentest would include both kind of devices. Considering that this is an introduction article whose tools should be easy for everyone to try out, we will not cover this here.
iOS apps are delivered in IPA packages, which are similar to apk files on Android. The executable files inside an IPA are delivered and stored with a DRM (Digital Rights Management) called FairPlay. To get an unencrypted version of the executable, the following options exist:
For the rest of this article, the intentionally insecure app iGoat-Swift is used. The source code and the unencrypted IPA can be downloaded from github.
An IPA package is just a zip file that contains the apps executables, UI-Files and other resources. After unzipping it, we can list the contents of the iGoat app:
> file iGoat-Swift.ipa iGoat-Swift.ipa: Zip archive data, at least v1.0 to extract, compression method=stored > unzip -q iGoat-Swift.ipa -d iGoat-Swift-app > ls iGoat-Swift-app AppThinning.plist Payload > ls -lX iGoat-Swift-app/Payload/iGoat-Swift.app total 6276 drwxr-xr-x 3 iabo iabo 4096 Apr 18 2020 Frameworks -rw-r--r-- 1 iabo iabo 8 Apr 18 2020 PkgInfo drwxr-xr-x 2 iabo iabo 4096 Apr 18 2020 _CodeSignature -rwxr-xr-x 1 iabo iabo 5648352 Apr 18 2020 iGoat-Swift drwxr-xr-x 2 iabo iabo 4096 Apr 18 2020 SVProgressHUD.bundle -rw-r--r-- 1 iabo iabo 470543 Apr 18 2020 Assets.car -rwxr-xr-x 1 iabo iabo 595 Apr 18 2020 KRvWAssociates.html ... -rwxr-xr-x 1 iabo iabo 2961 Apr 18 2020 splash.html drwxr-xr-x 4 iabo iabo 4096 Apr 18 2020 Base.lproj -rw-r--r-- 1 iabo iabo 7512 Apr 18 2020 embedded.mobileprovision drwxr-xr-x 2 iabo iabo 4096 Apr 18 2020 CoreData.momd drwxr-xr-x 2 iabo iabo 4096 Apr 18 2020 AboutCell.nib ... drwxr-xr-x 2 iabo iabo 4096 Apr 18 2020 YapExerciseVC.nib -rw-r--r-- 1 iabo iabo 48407 Apr 18 2020 Assets.plist -rw-r--r-- 1 iabo iabo 81 Apr 18 2020 Credentials.plist -rw-r--r-- 1 iabo iabo 1517 Apr 18 2020 Info.plist -rw-r--r-- 1 iabo iabo 3058 Apr 18 2020 AppIcon29x29@2x.png ... -rw-r--r-- 1 iabo iabo 15151 Apr 18 2020 AppIcon60x60@3x.png -rwxr-xr-x 1 iabo iabo 324 Apr 18 2020 README.txt -rwxr-xr-x 1 iabo iabo 67 Apr 18 2020 Sentinel.txt
The important files in this folder are:
<appName> — In this case iGoat-Swift. The compiled, executable program. With the following command (macOS), the encryption status can be checked: > otool -l <appName> | grep -A 4 LC_ENCRYPTION_INFOInfo.plist — A file with information about the application, formatted as an xml and containing key/value pairs._CodeSignature/ — Contains a file with a signature over all files in the bundle to ensure the integrity of the applicationCoreData.momd — Place for data storage, usually in a SQLite database. Encryption is left to the applicatoin developer.PkgInfo — Contains some of the information of the Info.plist file in a special format. This file is optional and can be added to improve performance..lproj — Files used for internationalization.nib, .xib, .storyboard — Files with UI-DefinitionsFrameworks/, Plugins/ — Contain native libraries and frameworksWhen trying to get an overview of an application and its configuration, MobSF can be a great tool. Instead of going through the different files and using different tools to extract the information needed, MobSF does all this for you and shows you an overview. MobSF runs out of a docker container and provides a web interface. It can also do dynamic Analysis, but only when working together with proprietary, costly software to simulate iOS environments.
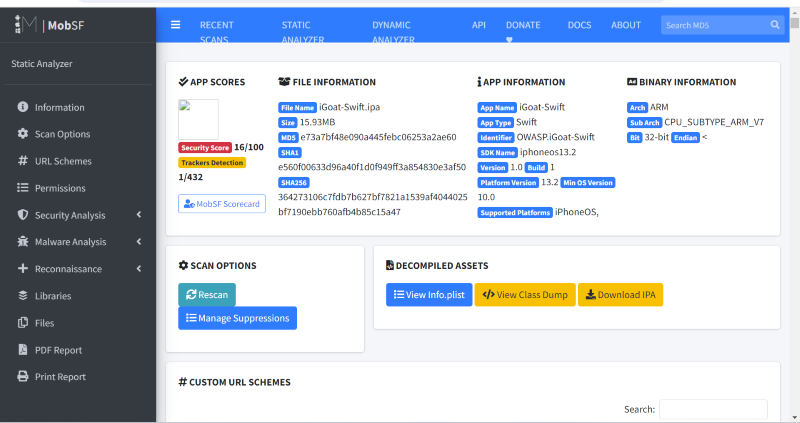
Decompiling and reverse engineering iOS apps is similar to other compiled languages like c. A short introduction about this topic can be found in this article. Basic reverse engineering includes string analysis using the string command and metadata extraction with the otool command (macOS only). For a deep dive into an applications code, full disassemblers/decompilers have to be used. The most famous tools for this are Ghidra, radare2 and IDA Pro (commercial). In comparison to Android Apps, reverse engineering is more tedious on iOS. The reason for this is the underlying programming language: The bytecode used by java retains more information than the assembly code an iOS app is delivered in.
Now that we know how to analyze an iOS IPA package, we can look at the second big area of testing: Dynamic Analysis, i.e. analyzing the application while it is running on a device. In this article, we will focus on the tool objection. The reason we use objection is that it offers a command line tool to automatically modify and resign an IPA with code that connects back to the objection cli (Command Line Interface). Patching an application means that it can be run on a non-jailbroken device. Note: Patching iOS applications only works on macOS.
To patch and run an IPA we follow the instructions on their website. After having connected objection to the patched application with the command objection explore, we can easily access a lot of information that we already saw during the static analysis but also some more information only available in a running app instance. The most important commands from the point of view of a pentester are the following:
ls to shows us the files in the package.OWASP.iGoat-Swifth.iabo on (iPhone: 16.0) [usb] # ls NSFileType Perms NSFileProtection Read Write Owner Group Size Creation Name ---------- ----- ---------------- ---- ----- -------------- -------------- --------- ------------------------- -------------------------------------- Directory 493 None True False _installd (33) _installd (33) 160.0 B 1970-01-01 00:00:00 +0000 WebkitCacheExerciseVC.nib Regular 420 None True False _installd (33) _installd (33) 81.0 B 2024-01-30 12:43:58 +0000 Credentials.plist Regular 420 None True False _installd (33) _installd (33) 463.0 B 2024-01-30 12:43:58 +0000 rutger.html ... Regular 420 None True False _installd (33) _installd (33) 327.0 B 2024-01-30 12:43:58 +0000 mansi.html Readable: True Writable: False
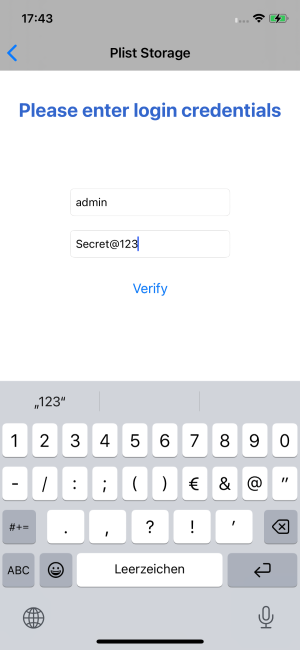
ios plist cat <filename>.plist shows the content of plist files. We can use this to solve the plist challenge in the iGoat app.OWASP.iGoat-Swifth.iabo on (iPhone: 16.0) [usb] # ios plist cat Credentials.plist
{
Password = "Secret@123";
User = admin;
}
ios nsuserdefaults get shows what data is stored in the NSUserdefaults storage. We can use this to solve the NSUserDefaults challenge in the iGoat app.OWASP.iGoat-Swifth.iabo on (iPhone: 16.0) [usb] # ios nsuserdefaults get
{
AKLastEmailListRequestDateKey = "2024-01-30 12:18:39 +0000";
AKLastIDMSEnvironment = 0;
AddingEmojiKeybordHandled = 1;
AppleLanguages = (
"de-CH"
);
PIN = 53cr3tP;
...
}ios keychain dump dumps the contents of the keychain, a special storage available to iOS applications. We can use this to solve the Keychain Usage challenge in the iGoat app.OWASP.iGoat-Swifth.iabo on (iPhone: 16.0) [usb] # ios keychain dump Note: You may be asked to authenticate using the devices passcode or TouchID Save the output by adding `--json keychain.json` to this command Dumping the iOS keychain... Created Accessible ACL Type Account Service Data ------------------------- ------------ ---- -------- ------- -------- ----- 2024-01-30 15:47:39 +0000 WhenUnlocked None Password iGoat SaveUser taoGi
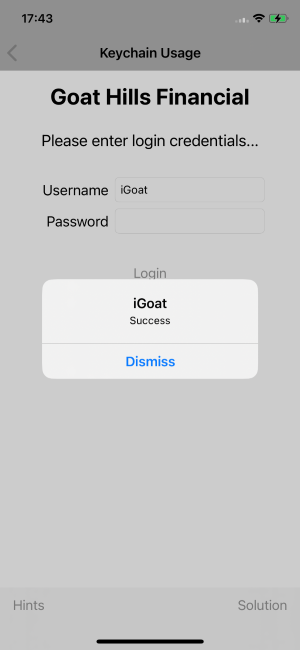
ios jailbreak simulate and ios jailbreak disable: Those commands are useful to test if the jailbreak detection of an app was implemented properly or not.Objection is also available for Android smartphones and offers a lot more advanced features such as method watching, hooking and even replacing a function with custom code.
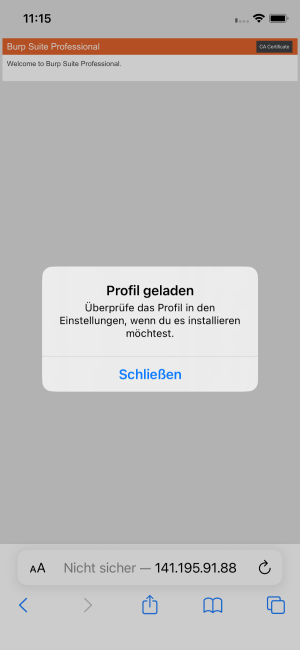
Many mobile applications connect to a webserver to exchange data with a central database. To analyse this traffic, similar tools as in website penetration testing can be used, for example Burp proxy. To intercept and introspect encrypted https traffic, the proxy needs to decrypt requests and thus the proxy’s certificate has to be trusted by the iOS device. Luckily, using Burp, it is easy to install the certificate in an iPhone. With the proxy listening, open safari on the target device and enter the proxy’s ip address. You should see a Burp welcome page. Click on install certificate on the top right and accept the popups. Next, open the settings app where you should see a new entry at the top. Choose trust certificate, enter your PIN and Burp is ready to go.
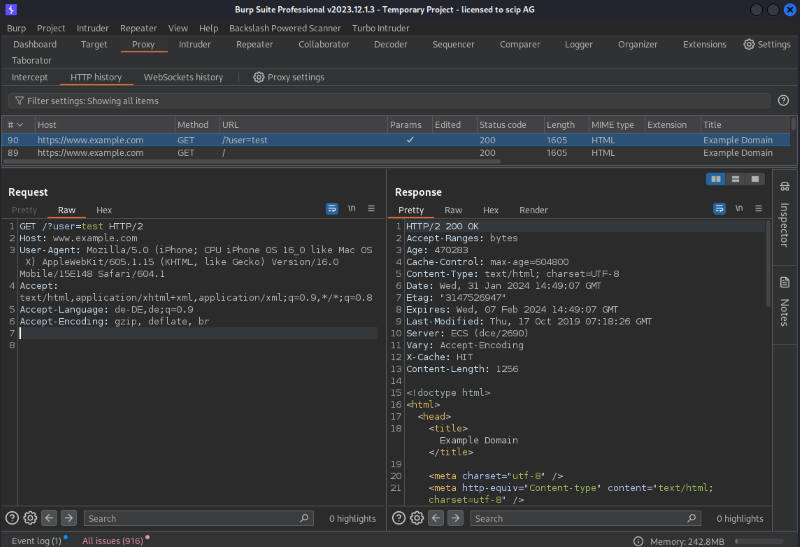
Depending on the application, this may not be enough to intercept the traffic with Burp: Certificate pinning is a security measure designed to mitigate this kind of attack and only accept a very specific server certificate. Depending on the details of how it is implemented, objection or a jailbreaked phone can be used to disable it. Alternatively, Brida is a tool to connect a patched iOS application with Burp.
Even without a jailbroken device, basic analysis and security testing of iOS applications is possible. There exist a lot of free and open source tools that each help to cover some test scenario. Intentionally vulnerable apps help demonstrating a tools abilities and practice the discovery and exploitation of vulnerabilities. One challenge that remains for security testers is to keep up to date with the changing environment: New iOS versions introduce new security measures which may break certain tools, some tools are not updated for a long time while new ones appear frequently.
Our experts will get in contact with you!

Ian Boschung
Our experts will get in contact with you!