Security Testing
Tomaso Vasella

It all started with a video game. Ubisoft has released their video game Watch Dogs at the end of May. It’s one of the year’s most anticipated titles and has gotten rave reviews. In the video game, a hacker named Aiden Pearce wants to find the people responsible for the murder of his niece and exact vengeance upon them. He uses a smartphone to hack everything the city in the game has to offer.
Currently, there’s a lot of buzz surrounding the game. The online tech-magazine Motherboard, run by the same people who run VICE.com, has a documentary series directly tied into the game’s marketing that has the premise of Everything can be hacked.
In the latest episode, dated May 29th 2014, we can watch a car getting hacked. It set loose a rather interesting chain reaction of media copying one another as well as neglecting one crucial fact. This news is not new.
This gained traction in mainstream media, because after all, a lot of people drive cars and a lot of people are not particularly keen on having their car hacked because when out of control, you’re barrelling down a road while being trapped inside a contraption that is give or take one and a half tons of metal. CNN Money picked it up and reported that car manufacturers use outdated code and ancient if any security measures to secure their cars’ computers. Some are up to speed, others aren’t and some make valiant effort.
This story, in turn, was picked up by Swiss newspaper and online magazine 20 Minuten which published a more or less exact translation of the CNN Money article. In addition, they merged information from an undated article of the German car magazine Auto Motor und Sport into it.
It is this article that first mentions that this news is not news. Because while the current trail of the story did in fact start off with a video game, the story itself is about a year old. And it’s much bigger than just Cars can be hacked. In fact, it shows us that there are forces out there that are actively trying to hinder publication of vulnerability, albeit with a somewhat valid reason in this particular case.
In 2013, Dutch researchers Roel Verdult and Baris Ege of the Radboud University Nijmegen worked together with Flavio D. Garcia of the University of Birmingham on a talk titled Dismantling Megamos Crypto: Wirelessly Lockpicking a Vehicle Immobilizer and wanted to present their research that is based on an accepted academic paper to the public at the 22nd Usenix Security Symposium in August 2013.
Megamos Crypto is a system that acts as a so-called Vehicle Immobilizer. It’s a last line of defence that forbids the car to start when there’s an unauthorized person – in this case, someone without the genuine car key – sitting inside the car, trying to drive off with it. Verdult, Ege and Garcia are technically able to forge a highly sophisticated car key and start a car without proper authentication.
Manufacturers take a great many precautions so that their cars don’t get stolen, as evidenced by the existence of systems like Megamos Crypto, which appears to be a simple single-factor authentication based on machine interaction. The car remotely communicates with the car key and shows it a Key Value. The car key responds with a Proof Key and only then the car is allows its engine to be started. Drivers don’t even notice it happening.
The exact details of Megamos Crypto and how the code can be circumvented are under wraps, the reasons for this we will get into in a minute. However, the researchers compare the complexity and the practicality of the attack with the attack that can be performed against cars secured with Hitag2. Details on how this work can be learned here. The catches:
All in all, the researchers freely admit to their method not being a very practical one. In short, their method only manages to outsmart Megamos Crypto which is only a Vehicle Immobilizer and bypasses no other security measures.
Megamos Crypto is also out of date and used in many luxury cars such as Porsche, Audi, Bentley and Lamborghini.
Being responsible researchers, Verdult, Ege and Garcia notified all parties affected by their research. They were not exactly thrilled to hear that their 96bit encryption system is compromised and that someone with a brick, a screwdriver and a very sophisticated computer system as well as knowledge of the car’s owner could steal their cars with what they probably consider to be relative ease.
So Volkswagen sued the researchers. The outcome: The researchers were not allowed to publish their accepted scientific paper on the subject and they were forbidden by the London High Court to present their findings at Usenix.
The court, represented by Justice Birss, recognized that this might be interpreted as an attack on free speech, the hindrance of academic progress as well as the protection of financial interests by the people who have financial stakes involved. Justice Birss went on record with the following statement concerning the case:
I recognise the high value of academic free speech, but there is another high value, the security of millions of Volkswagen cars.
Thus, millions of cars operate on vulnerable code and Volkswagen has made no announcements in the past year concerning the improvement of their code.
Despite the injunction, Verdult held his presentation at Usenix, albeit in a censored version. And this is it.
Any modern car’s computer systems are roughly the same. Exact specifications vary from model to model, from type to type. Generally, all cars seem to run on the same basic architecture though, which is based on a Controller Area Network Bus (CAN Bus). They have been first developed in 1983 and have undergone several versions since then. They were designed by Bosch to reduce the amount of cable in cars that used to take up around two kilometres of space.
In the general frame of this CAN Bus, the car’s systems are divided into several zones. Again, the number of zones vary between car makes and models.
Researcher Felix Domke has drawn up a very basic architecture of his car’s CAN Bus architecture indicating the zones that his car uses.
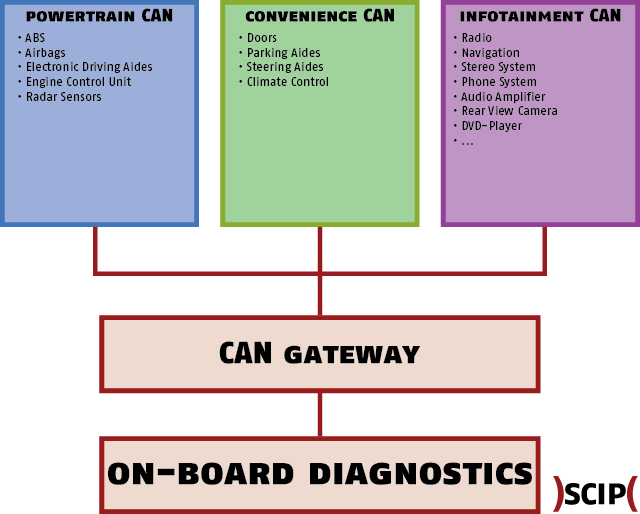
These zones should not communicate with each other. Basically, this means that if you’re able to access Infotainment CAN, which is by far the easiest to access due to its basic nature, there should not be a way to send signals to or receive signals from the Powertrain CAN or the Convenience CAN. Similarly, if you access one of the other two CANs, you can’t access the Infotainment CAN.
All of these CANs access the On-Board Diagnostics (OBD-II) via a CAN Gateway, where the data is being analysed and interpreted.
However, researchers have proven that all the CANs in the graphic can be accessed and thus, signal injection and hijacking is possible. What has not currently been done is a remote exploitation of a car without prior physical access to the car’s cockpit, since most, if not all, CAN Buses are housed near the cockpit and can only be accessed via the cockpit.
Similarly, remote exploitation has not been publicized, even with prior access to the car. However, Spanish researchers Alberto Garcia Illera and Javier Vazquez Vidal have shown a prototype of a device that allows a local attacker to perform a variety of actions by connecting a specifically crafted piece of hardware and connecting it to the car. It is theoretically possible to supplement this device – named the Car Hacking Tool (CHT) – with a 3G-Enabler which would make the remote sending and receiving of packets in the CAN possible.
Moving past the ignition systems of a car, there’s a number of other sensors that can actually be hacked and have been hacked in the past. Authorities on this subject appear to be the previously mentioned Chris Valasek and his colleague Charlie Miller. They have successfully executed attacks on the steering, the braking, the car’s acceleration system as well as its displays.
During the testing of their attack scenarios, Valasek and Miller have used a 2010 Ford Escape and a 2010 Toyota Prius. They built their own connector in order to communicate with the vehicles and had to have a wired connection to the driving car for their hacks to work.
Despite all this, they were able to display arbitrary values on the speedometer and alter readouts on the manual-looking gauges on the dashboard such as speed and RPM. In addition to all that, they managed to overload the car’s systems which then disables all steering assistance.
In the Ford, the PSCM ECU completely shuts down. This causes it to no longer provide assistance when steering. The wheel becomes difficult to move and will not move more than around 45% no matter how hard you try. This means a vehicle attacked in this way can no longer make sharp turns but can only make gradual turns.
While they managed to influence the steering of the car, there’s no practical use of it besides being able to crash the car into an obstacle. They cannot remote control the car as of yet.
By sending an invalid speed with one Ecom cable and the coupled servo angle / current gear combo on another Ecom cable we could steer the wheel at any speed. The precision of the steering is not comparable to that during auto-parking, but rather consists of forceful, sporadic jerks of the wheel, which would cause vehicle instability at any speed (but would not be suitable for remote control of the automobile).
They did not only manage to execute successful attacks on the car’s system, but they were able to physically influence the driver, too. Valasek and Miller were able to access the diagnostic mode on the Prius and forced the seatbelt tightening system, which is used to get the driver in an upright position in case of an accident, to reel the seatbelt back in.
This isn’t even close to everything that Miller and Valasek were able to do. For a complete list, see the link above. The two researchers have come to the following conclusion:
Automobiles have been designed with safety in mind. However, you cannot have safety without security. If an attacker (or even a corrupted electronic control unit) can send controller area network packets, these might affect the safety of the vehicle:
Hackers never stop at just influencing things slightly. They’re trying to push things as far they can be pushed. This past December, Felix Domke alias tmbinc has managed to run his own code on a car. To achieve this, he has integrated Python into his car’s dashboard (ignore the certificate error as it is deliberate on the part of the Chaos Computer Club).
To get all this done, he accessed the car’s systems by using the Bluetooth kit to hack into the central dashboard system which runs on the same technology as Valasek and Miller’s test car. He then discovered that cars run on Linux and managed to install Python on it.
He didn’t do anything with it, but seeing as it’s possible to not only inject your own code into a car, but also have your own software run on your car’s system, the possibilities are given for malicious software to infect cars.
While pretty much every system on modern cars can be compromised with relative ease, it’s nowhere near at a level where it’s sophisticated. Attacks affecting everything from brakes to steering to airbags and display control have not yet been conducted remotely.
This does not mean a remote attack is impossible, just that it has not been done yet. Theoretically, a device known as the Car Hacking Tool can be extended to have a 3G-Module and then it would be ready for remote use.
In order to hack a car, an attacker needs to at least have had access to the cockpit of the car, mechanical knowledge and the right set of tools.
Our experts will get in contact with you!

Tomaso Vasella

Eric Maurer

Marius Elmiger

Eric Maurer
Our experts will get in contact with you!