From crisis to opportunity
Michèle Trebo

Methods for collecting, analyzing and interpreting publicly available information
Open Source Intelligence Investigation is a systematic approach to collecting, analyzing and assessing information from publicly available sources. These sources include a variety of media and platforms, including news websites, academic publications, government documents, social media, forums, blogs, and other online and offline resources. The term open source refers to information provided by individuals or groups with no expectation of privacy. This does not necessarily mean that this information is free or without copyright protection, but that it is accessible without the use of covert methods. Unlike other intelligence methods, which may rely on covert operations or informants, OSINT relies exclusively on freely available information. A key feature of OSINT investigations is the use of advanced technologies and analytical tools to sift through vast amounts of data and extract valuable insights from a sea of data.
The UK Government’s CONTEST counter-terrorism strategy includes four main strategies that can be applied to OSINT investigations.
Monitoring public data sources, social media and platforms to identify potential risks, threats or harmful trends at an early stage. The aim is to take preventive measures before these risks escalate.
Collection and analysis of data from various public sources to identify illegal activities, undesirable trends or networks and take countermeasures. This can also be used for the legal prosecution of criminal offenses or to identify fraud.
Proactive identification and assessment of vulnerabilities, whether in infrastructures, processes or technologies, based on publicly available information. The aim is to protect against potential threats.
Use of public data to model and predict possible risk scenarios. This enables preparation for various eventualities and the development of response plans.
The CONTEST strategy demonstrates the central role of OSINT investigations in modern security strategies. Through the systematic use of publicly available sources, OSINT provides a comprehensive approach ranging from prevention to tracking, protection and preparedness. It emphasizes the importance of both proactive and reactive response to threats, with each strategy having specific goals and methods to ensure security.
The methods used vary depending on the objective of the investigation. For example, social media monitoring can provide security-related insights, while satellite imagery can reveal geographical changes. The choice of OSINT methodology depends heavily on the specific question and may require a combination of different techniques.
Self-protection is the focus of OSINT investigations. Measures such as the use of VPNs, private browsing modes and various pseudonyms protect identity. System updates and anti-virus software provide protection against potential threats. When collecting data, legal regulations and local laws should be taken into account in order to respect copyright and data protection rights. Digital activities leave traces, so it is advisable to minimize them and ensure discretion. Unrecognized links and attachments harbor potential dangers. The use of trustworthy sources of information and continuous training on current security standards support efficient investigations.
A structured OSINT investigation is important for several reasons.
Ideally, the research process should be started with the option that requires the least effort and at the same time offers the highest probability of productive results.
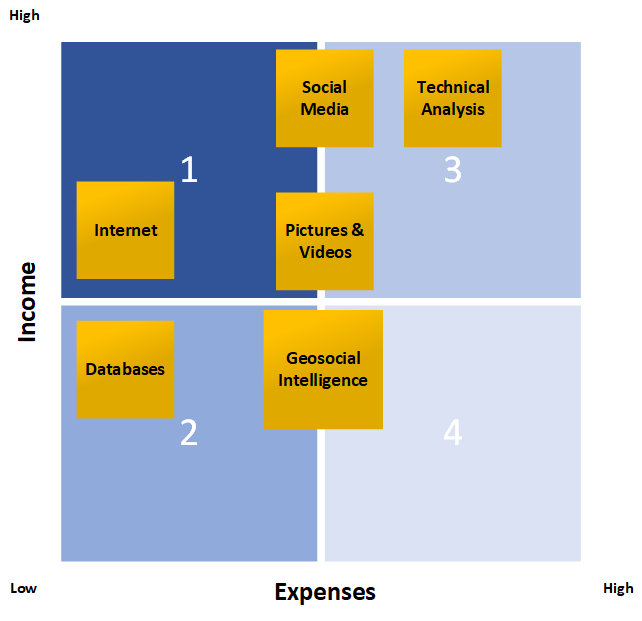
This structure may vary depending on the research objective and is not exhaustive.
The data landscape is diverse. You come across structured data, which is available in an organized form, and unstructured data, which is available in its raw form, such as text or images. There is a wealth of tools and techniques for data collection, from simple manual searches to advanced web crawlers and automated data retrieval systems. Once data has been acquired, the effective processing and analysis of this information is of primary importance. Advanced techniques such as natural language processing can be implemented to enable in-depth analysis of text data. Furthermore, data modeling techniques can be used to identify complex relationships and patterns within the acquired data structures. Beyond data analysis, however, the provenance of the data is of crucial relevance. Ethics and data protection play a central role in this context. A high degree of integrity and care should always be taken when acquiring data in order to avoid compromising the privacy of individuals.
The successful conduct of OSINT investigations requires a critical awareness of the validation of information sources. Unverified or erroneous data can lead to misleading analyses, which is why the credibility of the information collected must be constantly checked. Given the ever-growing flood of data, the importance of specialized tools and techniques is becoming increasingly clear. This is where machine learning comes into play, as it enables large amounts of information to be sifted through efficiently and relevant patterns to be identified. These advanced analysis techniques are crucial for gaining precise insights from the wealth of data and thus creating a sound basis for decision-making.
Backing up requires a careful approach to ensure the integrity and usability of the data. Here are some important points that should be taken into account:
Correctly securing digital data is crucial to ensure that it is valid and usable in a legal context.
Open Source Intelligence Investigation offers a comprehensive approach to collecting, analyzing and evaluating information from publicly accessible sources. In an increasingly networked and digitized world, OSINT has established itself as a crucial tool in information gathering and analysis. It uses a wide range of sources, from traditional news media to social networks. The focus of OSINT is on the use of freely accessible information, without the use of covert methods, unlike other intelligence methods. Advanced technologies and analytical tools are used to sift through vast amounts of data and extract valuable insights. The UK government’s CONTEST strategy demonstrates the application of OSINT in the Prevent, Pursue, Protect and Prepare areas, emphasizing its central role in modern security strategies. Methods for collecting, analyzing and interpreting publicly available information are considered crucial. Not only technical aspects are important, but also ethical considerations and the critical examination of the authenticity and reliability of each source of information. The OSINT investigation process requires self-protection, a structured approach and compliance with ethical and legal principles. Effective OSINT investigations are characterized by various factors, including the proactive identification of potential risks, the collection and analysis of data from various sources and the identification of vulnerabilities. The methods vary depending on the objective of the investigation and require careful handling of data protection and legal regulations. Another important aspect is securing the collected data. Early backup, documentation of the data backup chain and the use of appropriate tools are key components to ensure the integrity and usability of the data. Collaboration with data experts and compliance with legal regulations are equally crucial.
Our experts will get in contact with you!

Michèle Trebo

Michèle Trebo

Michèle Trebo

Michèle Trebo
Our experts will get in contact with you!