Specific Criticism of CVSS4
Marc Ruef

During a penetration test we were confronted with rather unique requirements:
The requests should be performed as efficiently as possible without triggering an alarm in the system.
Because the target’s infrastructure was not maintained by our client (also our target) but by one of their external partners, we were not to involve the third party in our security testing. At that point, we didn’t know about the ideal timing behaviour of our requests. But this would play a crucial role in our mission in order to perform automated requests during an early phase of the testing. So we found ourselves at crossroads.
Efficiency vs. Camouflage
In order to best gauge our possibilities of access we gathered information relating to the detection of many requests (typically during a portscan or a flooding). We defined the threshold using two values:
To find this data for commonly used products, we used the following sources:
In the following table, the number of requests (Req) per second (Sec). in order to get a unified number that can be compared, we complied the value nr/1S, the number of requests (nR) per second (1S). The arithmetic average of this number is 85.928.
| Product | Req | Sec | nR/1S | |
|---|---|---|---|---|
| Aolynk Broadband Router | ▼ | 5 | 1 | 5 |
| Astaro Firewall | ▲ | 100 | 1 | 100 |
| Avira Internet Security | ▼ | 50 | 5 | 10 |
| Billion BiPAC | ▲ | 100 | 1 | 100 |
| Bullguard Internet Security | ▼ | 6 | 0.6 | 10 |
| Checkpoint Firewall-1 | ▼ | 30 | 20 | 1.5 |
| Checkpoint Safe@Office | ▼ | 30 | 20 | 1.5 |
| Checkpoint UTM-1 | ▼ | 30 | 20 | 1.5 |
| Checkpoint VPN-1 | ▼ | 30 | 20 | 1.5 |
| Checkpoint ZoneAlarm | ▼ | 30 | 20 | 1.5 |
| Cisco ASA/PIX | ▼ | 8 | 120 | 0.07 |
| cPanel lfd | ▼ | 11 | 260 | 0.04 |
| Deerfield VisNetic Firewall | ▼ | 3 | 10 | 0.3 |
| Inmon Traffic Sentinel | ▼ | 5 | 600 | 0.01 |
| Juniper JunOS | ▲ | 10 | 0.01 | 2000 |
| Juniper IDP | ▼ | 20 | 120 | 0.17 |
| Juniper ScreenOS | ▼ | 10 | 5 | 2 |
| Logsurfer+ | ▼ | 100 | 300 | 0.33 |
| McAfee Sidewinder | ▼ | 5 | 30 | 0.17 |
| Microsoft ISA | ▼ | 10 | 60 | 0.17 |
| Microsoft TMG | ▼ | 10 | 60 | 0.17 |
| Outpost Firewall | ▼ | 8 | 1 | 8 |
| Port Scan Attack Detector | ▼ | 5 | 5 | 1 |
| scanlogd | ▼ | 7 | 3 | 2.33 |
| Snort | ▼ | 5 | 60 | 0.08 |
| SonicWALL | ▲ | 300 | 1 | 300 |
| Sophos Endpoint Protection | ▼ | 3 | 0.3 | 10 |
| Sophos UTM | ▼ | 3 | 0.3 | 10 |
| Watchguard Edge | ▼ | 10 | 1 | 10 |
| Zyxel Zywall | ▼ | 30 | 60 | 0.5 |
Some factors stood out. All of them didn’t make our work easier:
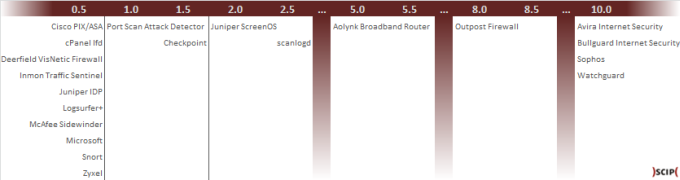
A reliable guideline for the threshold of port scan detection is the standard value of Checkpoint products. Thirty requests over twenty seconds is a maximum average of 1.5 packets per second, which is the median of the values in this article.
If you are confronted with the same paradoxical requirements as we were then you should go for approximately 1.3 packets per second in order to remain undetected. The offset of 0.2 was chosen as a buffer in order to be absolutely safe and undetected. Using nmap we enabled the switch —max-rate 1.3 in order to maintain that rate.
However, this view is only capable of dealing with standard settings of any product. The further recommendations by vendors, clients and experts as well as the settings that end up being used have to be looked at on an individual basis.
Our experts will get in contact with you!

Marc Ruef

Marc Ruef

Marc Ruef

Marc Ruef
Our experts will get in contact with you!