You want more?
Further articles available here

Hackers and Crackers know your Password Choices
In 2016, the Italian email hosting service LiberoMail revealed an attack resulting in exfiltration of many database records. Not well implemented security measures exposed user and passwords in clear text along with the address and some other user’s details. The LiberoMail users database was breached.
I decided to take a look at the data, clean them up (in addition to the security problem, they also had a data normalization problem), put everything in a database and run some queries on it.
The data set consists of approx. 700,000 records, not all with complete fields. In many cases, for example, the age has been extrapolated from the user name, from the e-mail address or even from the password itself.
| Measure | Value |
|---|---|
| Total records | 700,517 |
| Records without passwords | 33,332 |
| Records without information | 97,569 |
| Italian users | 696,023 |
| Other users | 4,994 |
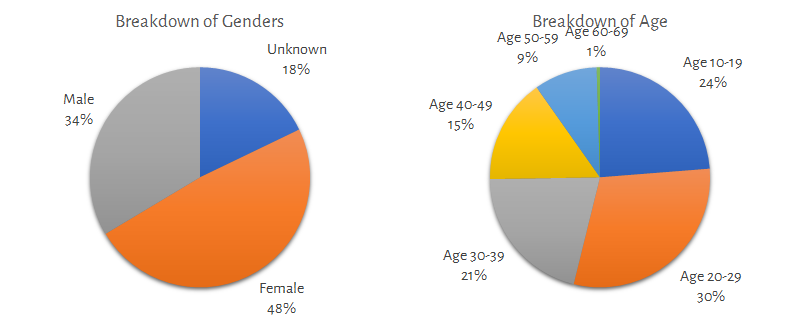
The gender (declared by user) and the age distribution are reported in the next charts:
Using our self-developed tools, we cleaned and normalized the raw-data and put the results in a relational DB.
For the analysis, we identified following characteristics:
Following charts shows how the password length varies if compared with gender, age, and region.
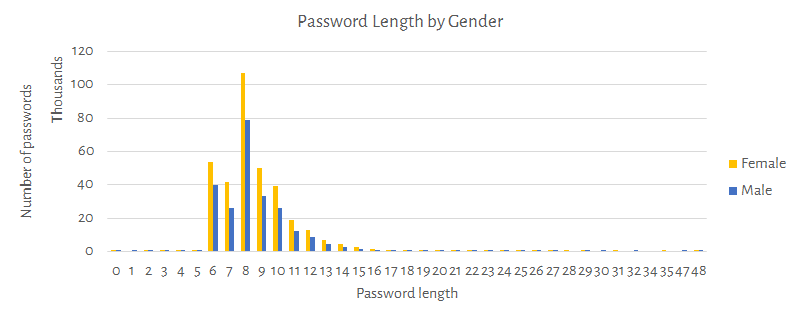
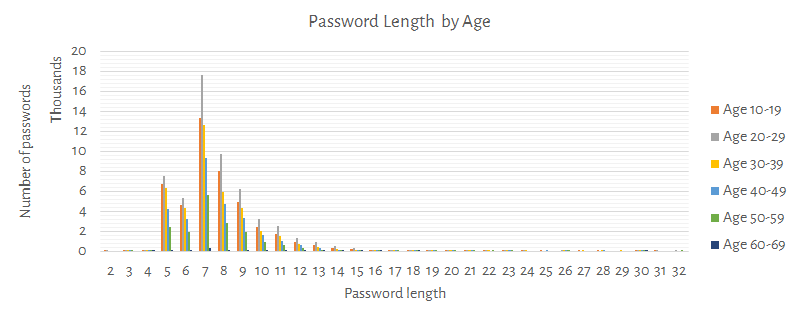
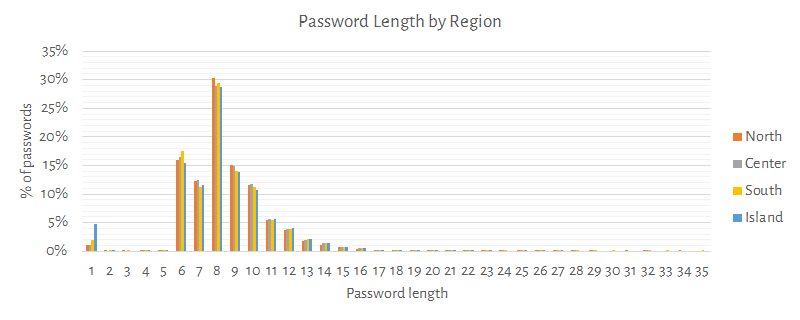
Remarks:
Following charts shows how the password complexity varies if compared with gender, age, and region (one point for each lowercase-, uppercase-, number-, punctuation-category).

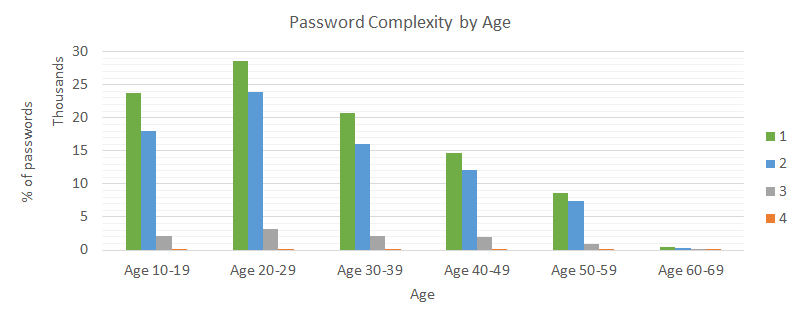
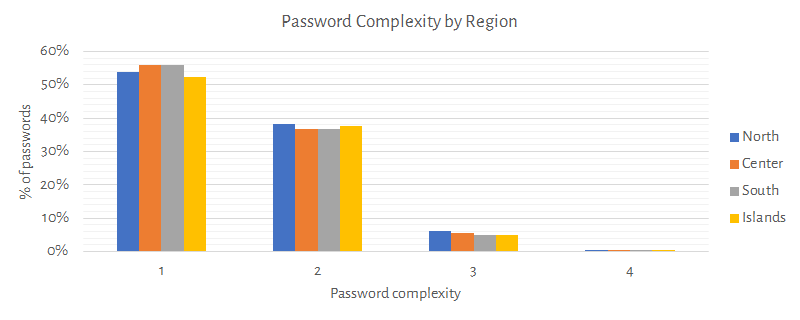
Remarks:
Following chart shows how the password length and complexity are related.
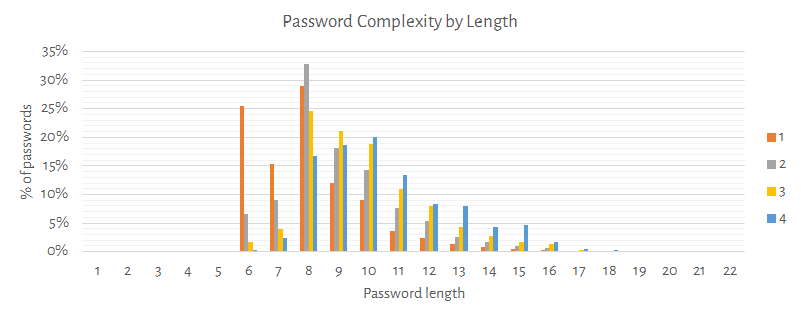
Remarks:
Following chart shows how the user makes use of common names (most Italian used first and last names), aggregated by gender and region.
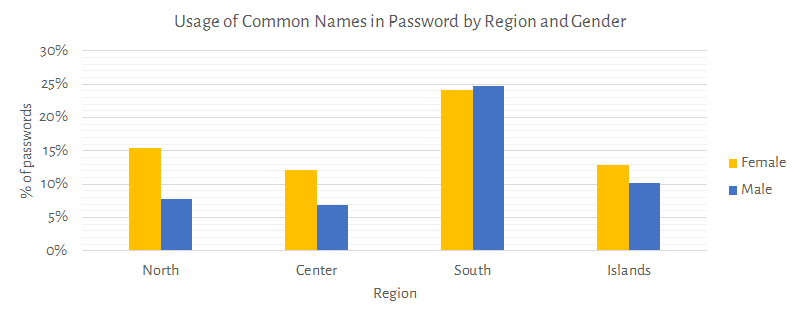
Remarks:
Following charts shows how the female and male users uses the specific passwords juventus, napoli, amoremio, 123456.
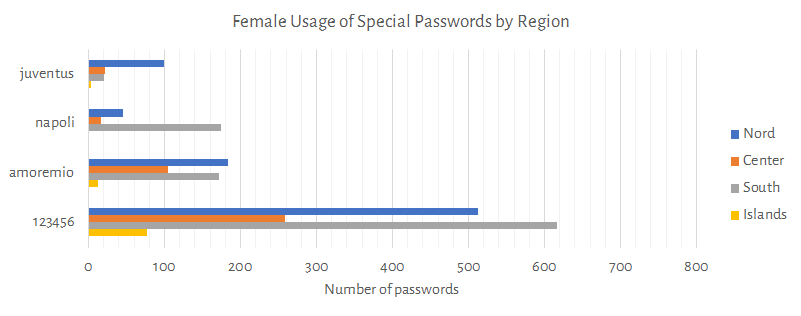
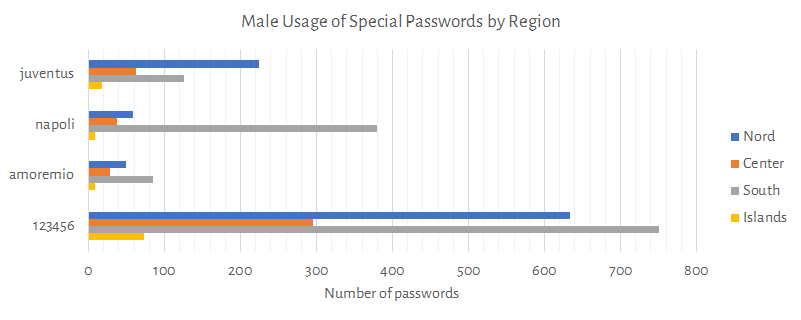
Remarks:
123456juventus and napoli are well diveded by North/SouthFollowing charts shows the top 20 passwords and the top 20 passwords containing a common name.
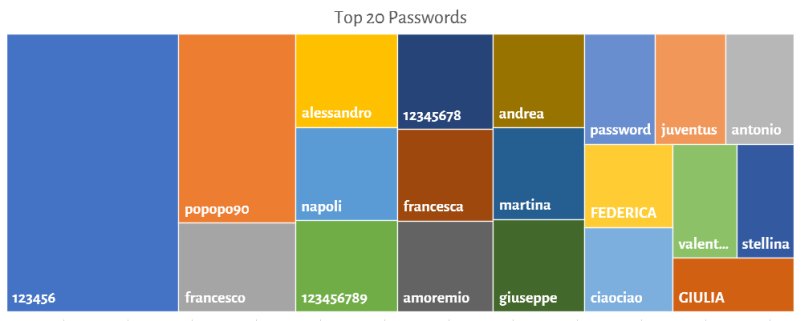
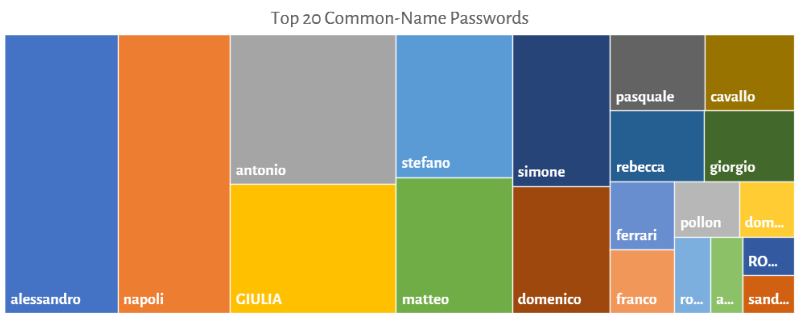
Remarks:
popopo90 is the phonetic transcription of the stadium anthem of the Football World Championship Italia 90Women seem to have safer passwords than men, even if in the north they exaggerate with the use of common names. Nice as usual the diatribes between Juventus and Napoli that remind us how in Italy football is always a protagonist.
The conclusion is to use at least dual-factor authentication for any of your accounts containing sensitive data. That means for every account.
Our experts will get in contact with you!

Rocco Gagliardi

Rocco Gagliardi

Rocco Gagliardi

Rocco Gagliardi
Our experts will get in contact with you!