Enhancing Data Understanding
Rocco Gagliardi
How to use Sigma Rules within Graylog
In 2017, the so-called Sigma rules were introduced and “archives” of definitions for quick implementation were created. Although Graylog v5 provides support for Sigma Rules, this feature is exclusively available in the paid version (Graylog Security). In the following, we explore utilizing Sigma Rules definitions within the Graylog Open version.
Sigma, introduced in 2017 by Florian Roth and Thomas Patzke, is an open, text-based, generic signature format that analysts can use to describe log events, making it simpler to write detection rules. Sigma, as a generic detection rule format, establishes a shared language for defenders, overcoming the obstacles they face when attempting to write rules in proprietary log analysis tools. Using the Sigma format, security analysts can share rules and then convert them to the tool’s native language.
Sigma standardizes detection rule formats across various security platforms, promoting collaboration by allowing easy sharing of rules on GitHub. This fosters knowledge exchange among security analysts of different levels, contributing to improved cybersecurity. Additionally, Sigma’s flexibility enables businesses to adapt their cybersecurity technology stack efficiently, avoiding vendor lock-in and promoting operational evolution.
Using Graylog Security, you can directly import Sigma Rules from the GitHub repository, but this feature is not available in the Graylog Open version. The process of importing rules configures filters, streams, and triggers for alerts that fulfill specific criteria. Alternatively, manual replicating this configuration can be achieved by incorporating search queries crafted into the Lucene language.
Take, for example, CVE-2023-34362, which exploits an SQL injection to gain access to the MOVEit Transfer’s database. For this vulnerability, there is a corresponding Sigma Rule. We have to find a method to convert the rule in Lucene query, configure a stream and alert on matched events.
The Sigma CLI is the simplest way to convert Sigma Rules into proprietary formats.
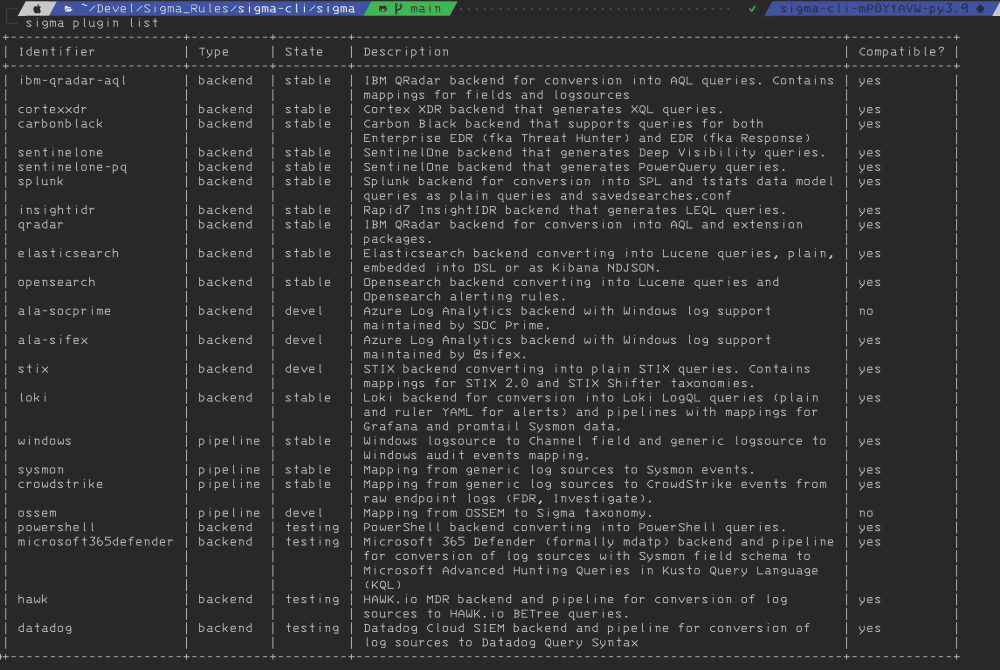
Once installed, the CLI facilitates the conversion of Sigma Rules into the Lucene query language of elasticsearch or opensearch.
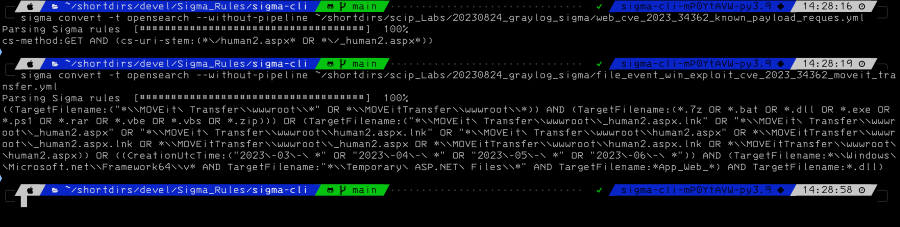
Once the query is defined, it is possibile to configure Graylog Open as usual. It’s evident that the logs need to be correctly parsed to extract the required fields.
Another effective way is the Uncoder AI. This tool translates Sigma rules into diverse query formats suitable for various platforms. With the application of AI, Uncoder AI enhances threat intelligence relevance, elevates detection engineering, and augments triage information. It’s advisable to explore Uncoder AI, particularly when facing a substantial number of rule engineering tasks. Its advanced capabilities swiftly generate rules from a free format collection of indicators of compromise (IOC).
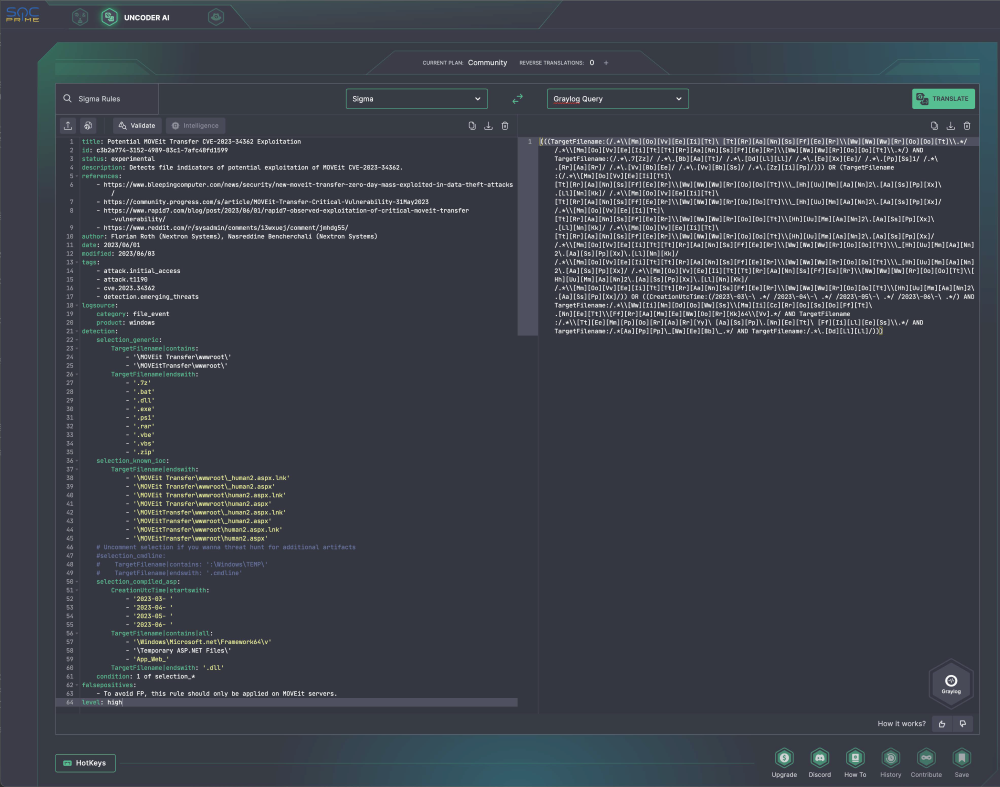
To conclude, Graylog demonstrates its effectiveness within targeted scenarios and in addressing complex log analysis tasks. The advent of Sigma rules in 2017 revolutionized the log analysis field, offering a uniform framework for formulating detection rules, promoting teamwork, and elevating cybersecurity strategies. Utilizing Sigma rules in Graylog can be achieved via Graylog Security’s advanced functionalities or, with some dedication, by adapting the Graylog Open version along with manual refinement to attain comparable outcomes.
Our experts will get in contact with you!

Rocco Gagliardi

Rocco Gagliardi

Rocco Gagliardi

Rocco Gagliardi
Our experts will get in contact with you!