Security Testing
Tomaso Vasella

Simple assessment of CIS Controls
But this can be the start of a difficult process. It takes investment, perhaps in hardware, software, staffing and expertise. If IT security has been neglected over a period of many years, it will take more than a few months to bring it up to speed. In other words, structures are required to guide the implementation of security controls and keep processes on track. Then it is up to management to allocate the appropriate resources – (ideally) over a period of several years. New budget items should therefore be transparent, and progress must be tangible. Otherwise, the initial euphoria will quickly be replaced by the monotony of day-to-day business.
Anyone using CIS Controls for this purpose, or planning to, now has a helpful resource. A few weeks ago, CIS released a new online tool called CIS CSAT which simplifies the assessment and management of CIS Controls. But most importantly, its lean website makes effective usage a more appealing experience.
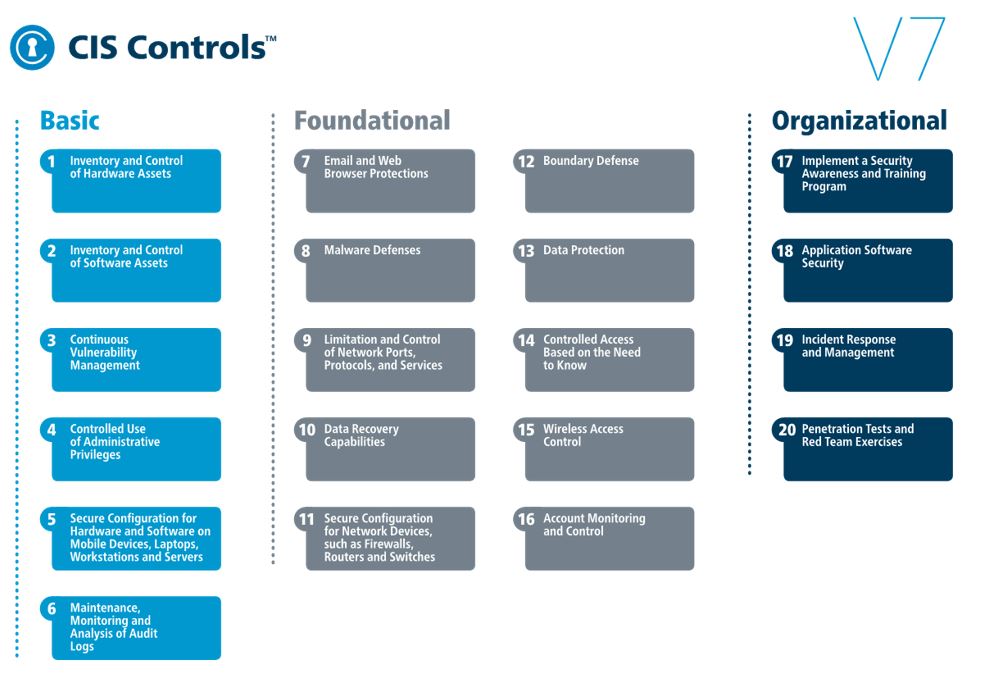
Currently in version 7, CIS Controls offers 20 controls, each of which includes between 5 and 13 sub-controls.
To find out more, visit the website.
The tool includes a minimal set of features, but these are more than enough to set up and operate an IT security framework. The main features include:
The first thing a company needs to establish before using the tool is whether it is happy with effectively shifting its IT security to the cloud.
This means placing your trust in CIS as the operator and Amazon (AWS US East Region) as the provider. If you want to be on the safe side you can use the platform anonymously without uploading identifying information, while still benefiting from the management and visualization features. An initial review suggests that this is quite simple.
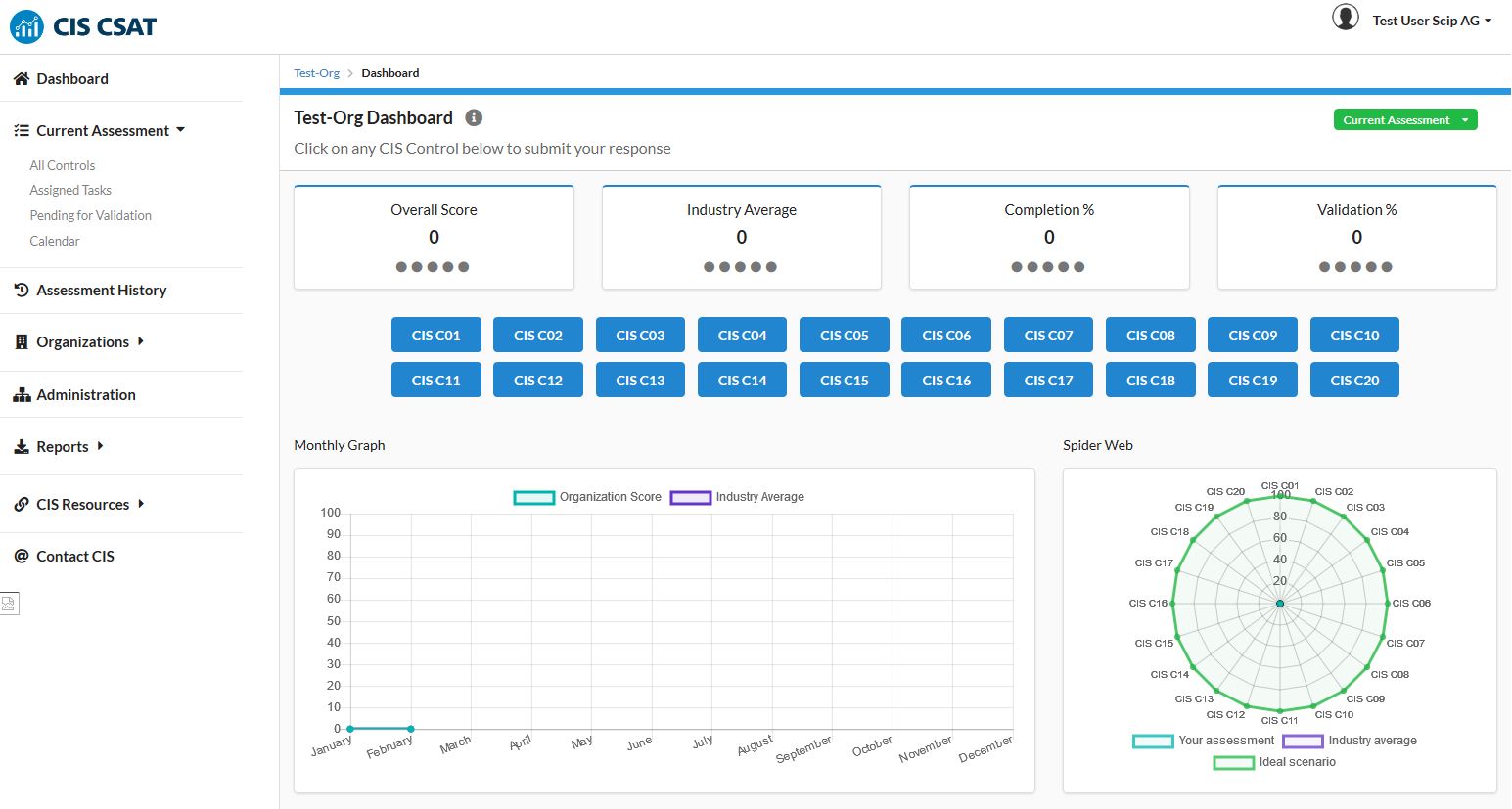
After signing in, you will see the dashboard for the current assessment. It will be empty at first. The dashboard provides a range of information and charts, without being too overwhelming.
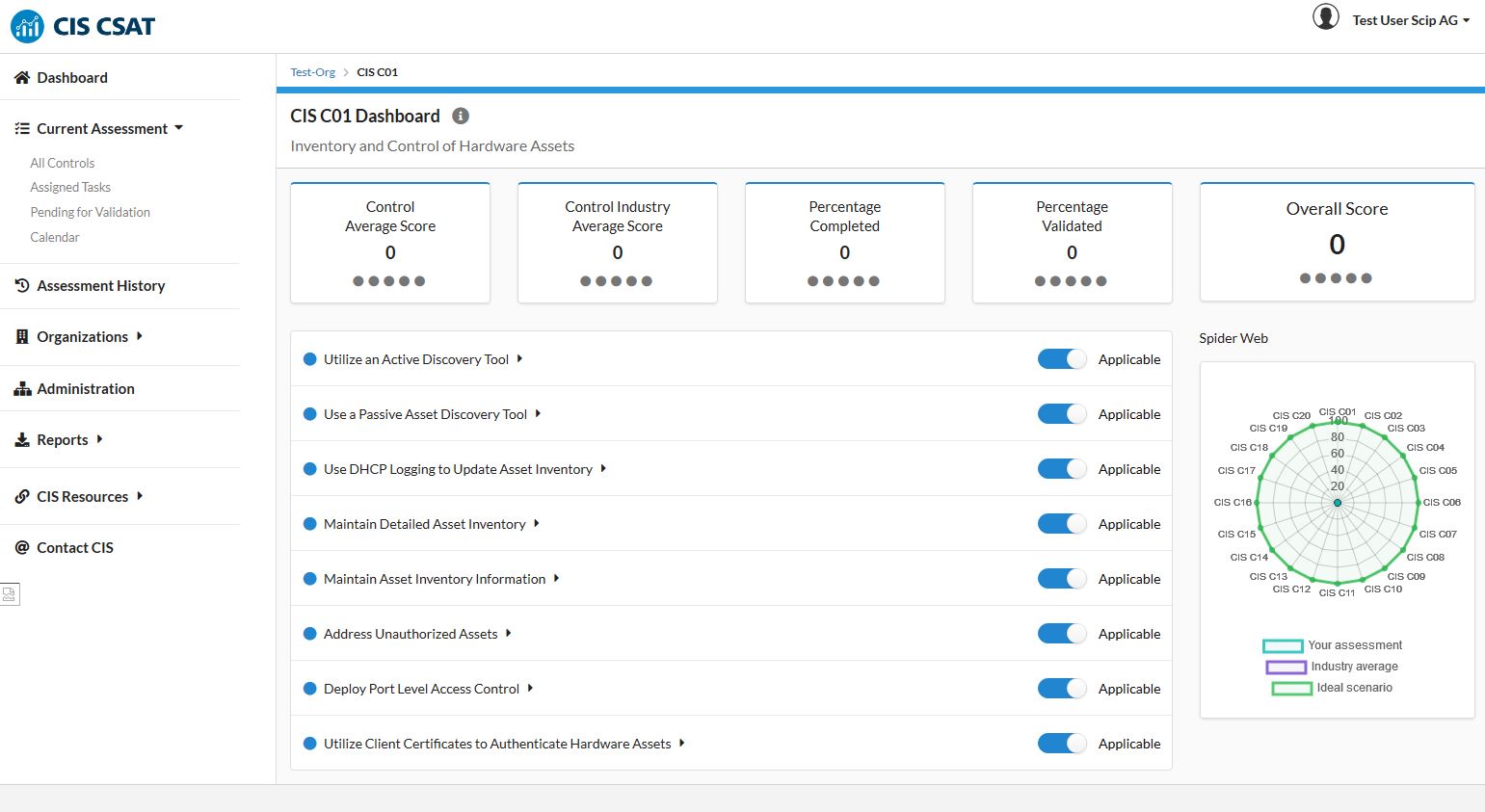
Clicking on one of the controls (blue buttons) takes you to the dashboard for the control. You will then see several figures, such as scoring and completeness status, as well as the list of sub-controls.
The next click takes you to the assessment form for the respective sub-control.
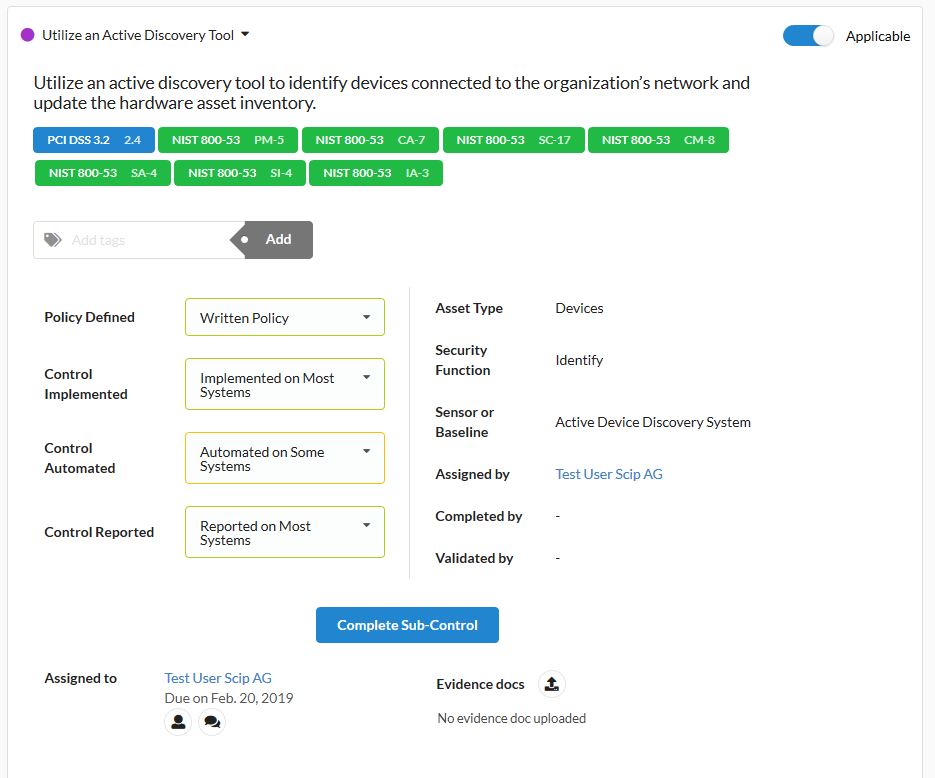
A brief introductory text provides information on the selected sub-control, followed by references to the corresponding PCI DSS and NIST controls, which can sometimes be convenient for further investigation of the controls and for compliance reports. The actual assessment is based on responses to the four questions in the drop-down menus, and carried out by clicking the Complete Sub-control button. The sub-control is then validated or sent back for reprocessing with an additional click. The user management interface allows other users to perform validation as well.
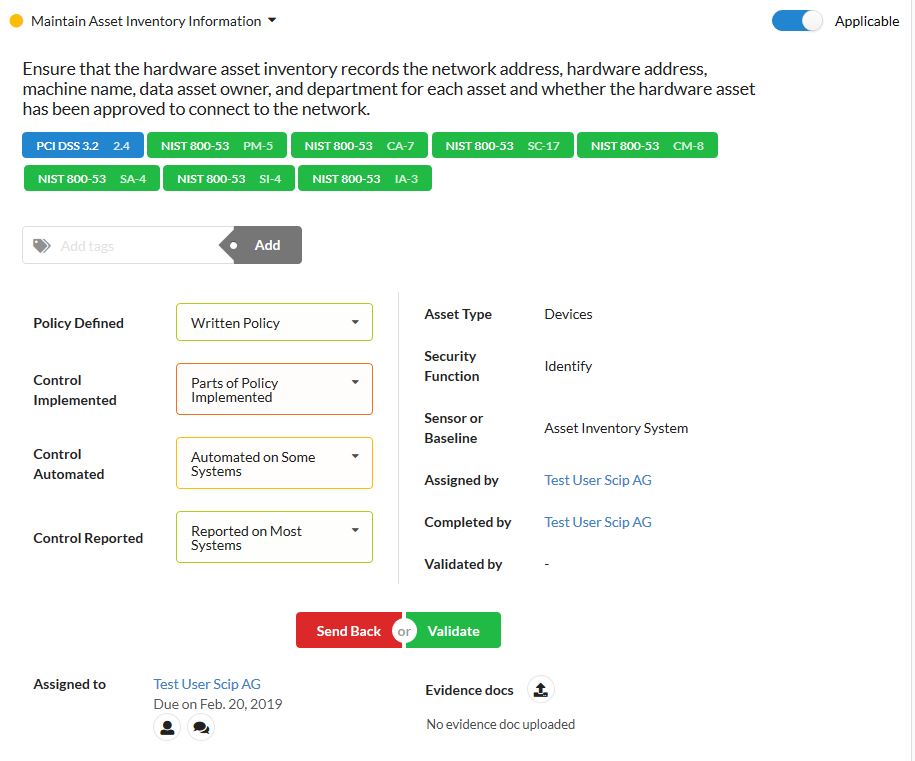
An audit trail makes the whole assessment process easily traceable.
Filling out all 171 sub-controls is somewhat time-consuming. The corresponding workflow is still a bit cumbersome, requiring a lot of scrolling and clicking. It would be nice to have a more streamlined process here.
Once all of the controls are assessed, the dashboard takes on more color and the user will see the desired overview. CSAT assesses all controls and presents them in a graphic visualization.
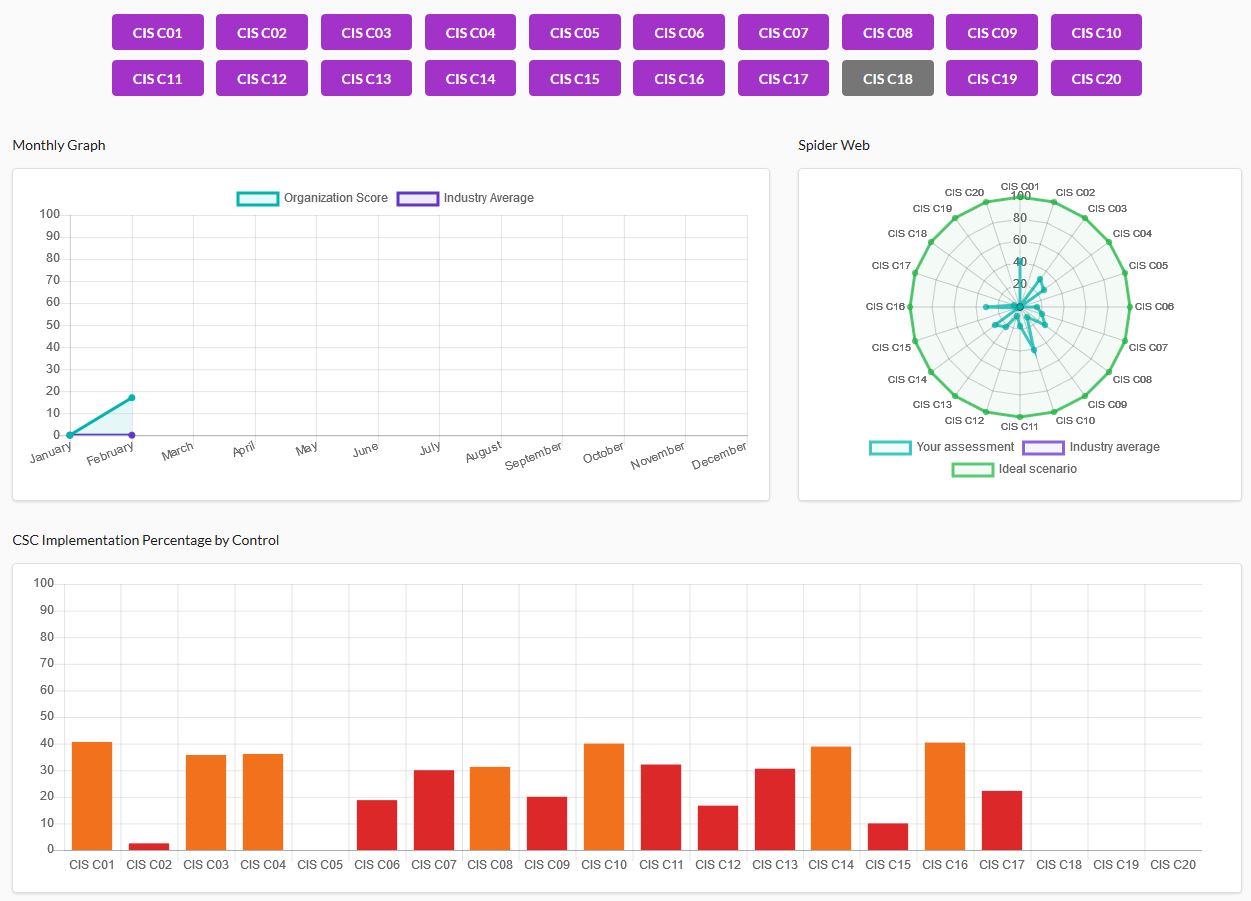
For example, a company without an IT security framework might see something like this in a first assessment.
These graphs can be exported to PowerPoint with a simple click and then used immediately to create reports for stakeholders.
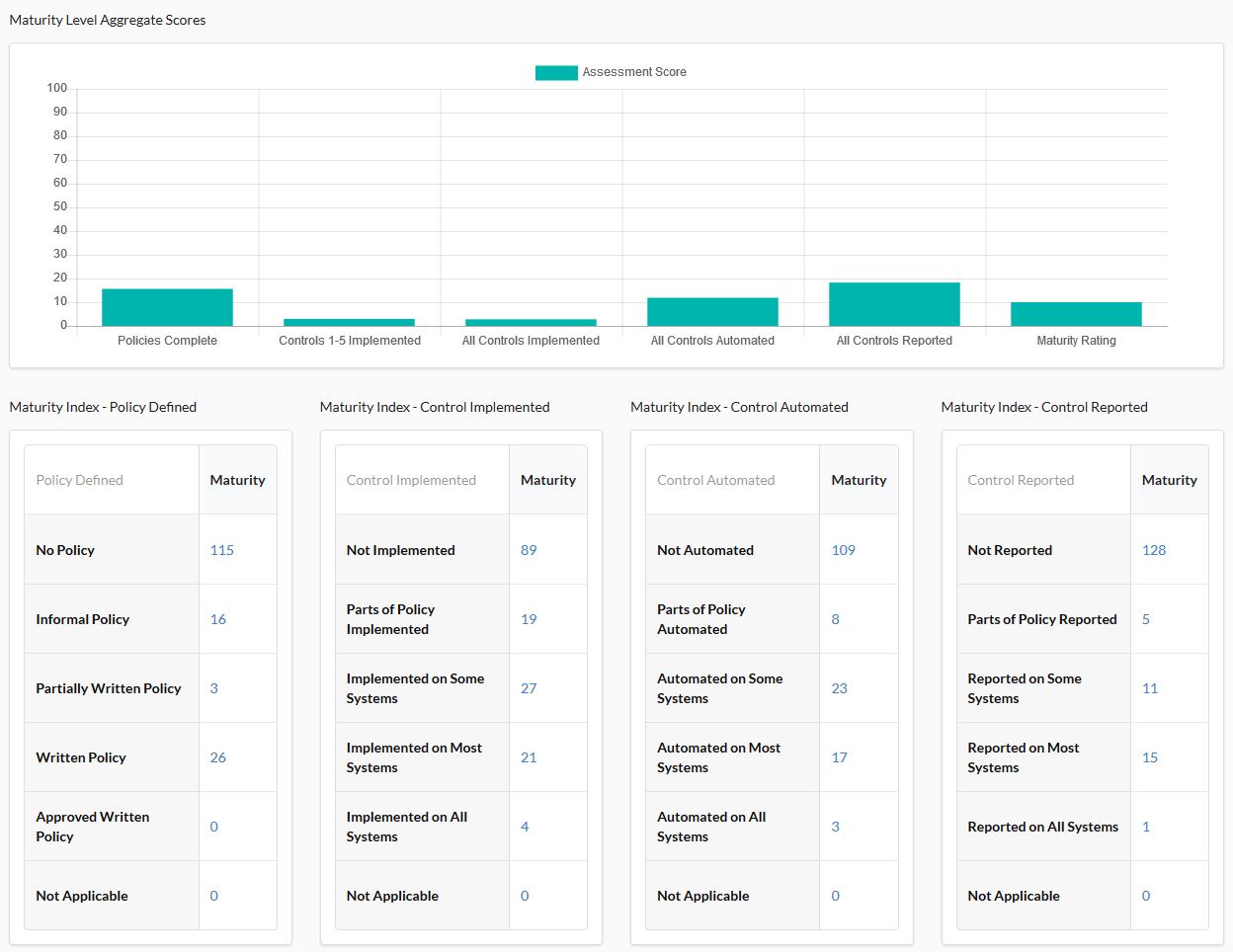
The assessment run is now complete and a current IT security status report is available.
This allows you to very effectively and precisely define where (control and sub-control) measures should and must be taken in specific areas (policy, implementation, automation, and reporting). You can add relevant projects – and there you have an IT security framework using CIS Controls.
It is a good idea to carry out a new assessment after a reasonable period of time to measure and depict progress in IT security. You can trigger this new assessment from the dashboard.
Oops – CSAT still has a gaping hole here. If you’re expecting the new assessment to draw data from the previous assessment you will be disappointed and instead discover the forms are blank for all controls. In other words, you have to fill everything in all over again. Completing all 170 sub-controls again for each assessment run is very laborious and impractical. You would expect that only controls/sub-controls where progress had been made would have to be updated, with all the others simply retaining their current state.
We have submitted this feature request to CIS. It is currently unclear if and when pre-population of the previous assessment run will be implemented.
CIS CSAT simplifies the management of CIS Controls, making it more attractive. The basic structure and feature set of the web application does this quite well. However, CIS should work on offering a smoother workflow for the assessment run.
Unfortunately, the absence of a pre-population feature, which uses data from the previous assessment, makes the tool very time-consuming to use, particularly when you have a lot going on in the area of IT security, or when you need to generate quarterly reviews, say. Hopefully CIS will implement this feature to make this effective security management tool a very simple and appealing tool.
An offline version would, of course, be a welcome addition which would cut out the step of anonymizing data for upload.
Our experts will get in contact with you!

Tomaso Vasella

Eric Maurer

Marius Elmiger

Eric Maurer
Our experts will get in contact with you!