Privacy Enhancing Technologies
Lucie Hoffmann

How to make your Cloud Secure
The agility and flexibility offered by the cloud is precisely what allows many companies to go live with services and infrastructures so quickly. Nevertheless, certain security aspects occasionally fall by the wayside. In addition, the cloud solutions in question may be tested with functions that are by no means critical. So someone with no more than a Microsoft Azure account might simply dock right into this or that server… And soon enough, everything has developed into a sizeable but often chaotic infrastructure. It is particularly unfortunate when, for example, tried and tested security concepts from the “old” on-prem infrastructure are simply forgotten or are not implemented in the rush towards cloud agility. To address these issues, this article offers some ideas on security and the cloud. Microsoft Azure Cloud will be used for reference purposes.
Using any type of cloud solution for a business requires a certain understanding of the concept. There are two ways to look at this:
This makes it relatively easy to answer the question raised in the title of this article: The cloud itself should be integrated as an asset into the existing cybersecurity framework, and existing security controls should be applied to the resources being operated in the cloud.
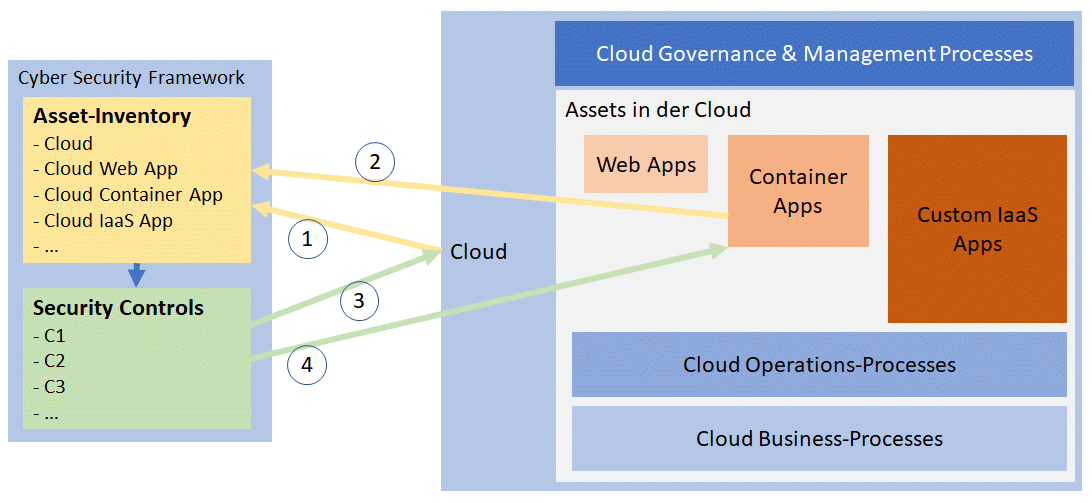
This perspective generally applies to the integration of the cloud into an existing IT governance and management model as well.
It should come as no surprise but is still worth mentioning that any cloud strategy should be clearly based on business requirements. The arguments for cost savings and flexibility are valid, but it takes more than that to define a cloud strategy. In short-term and medium-term planning, it is important to develop basic structures and concepts from the outset, in the right context and in the appropriate scope. Finally, this also determines the choice of the cloud provider(s) whose product portfolio should meet regulatory, business, IT and, of course, security requirements.
One major security concern to be considered with your cloud strategy is the issue of control. What level of control is necessary?
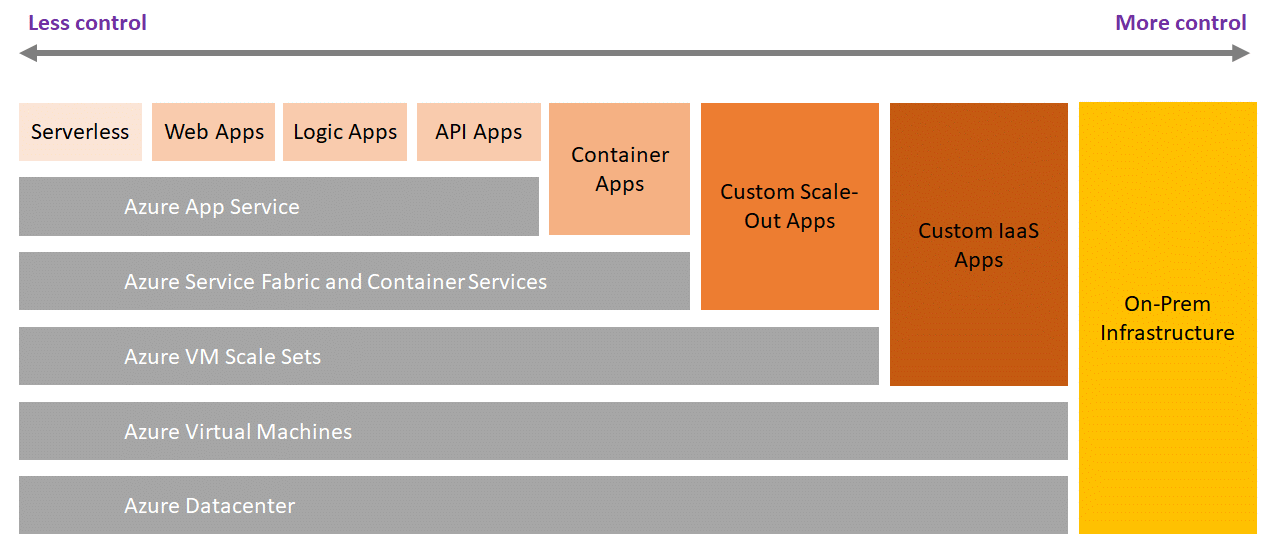
The question of control can, for example, be specifically applied to and grouped under data classification, the defined mission-critical processes and regulatory requirements in order to give the strategy a solid foundation.
During implementation, you can also determine whether a specific service is too critical for it to be securely operated in the cloud. One might then argue that many cloud providers offer comprehensive security features and can indeed operate critical processes in the cloud as well. It is true that Azure, for example, includes various security features. These should also be used selectively. One should also take advantage of “cloud intelligence” (a recognized attack pattern affecting one cloud tenant can be detected or prevented to protect all of the other tenants as well). However, here the issue shifts from control to trust.
And this is a key point: How much trust does a company place in its cloud provider versus how much control does the business case demand? In the case of “control vs. trust”, it is a good idea to make a well-informed decision, and it should be clearly reflected in the strategy.
Anyone who already has an IT governance model in place (e.g. COBIT) for their on-prem infrastructure will have an advantage. For more information on this topic, see our article on the discussion of General Controls within an organization. Ideally, existing governance processes can then be adapted for the cloud. Azure offers several features for implementing governance and management processes using the cloud, but they are of a more technical and operational nature. In the case of Azure, Microsoft’s own documentation on the topic is recommended:
On the strategic level, the existing governance processes and controls that are part of the on-prem infrastructure should be applicable here, too.
Cloud flexibility and agility are new factors that should be incorporated into cloud governance as well. In this context, it is also important that you give plenty of thought to the rapid cycles of new features offered by cloud providers, as well as the option of speedy deployment and removal of resources.
In addition to the regulatory requirements for data management in the cloud, data management should always be classified as well as assigned to an appropriate data owner, just as it would be with on-prem data. This is essential when choosing the cloud provider and when making the basic decision as to whether a given service (and its data) should even be put in the cloud in the first place. For more information on this topic, refer to our article Protecting business information.
The next important item is to set up the cloud according to a specific structure that is based on the cloud strategy and is managed using governance processes. Exactly how this structure will look depends on several factors, such as the type of business and its organization, the current management style and, not least, the structuring features offered by the cloud provider. For this, Azure offers a hierarchical structure with tenant, account and subscription levels.
In the interest of IT security, having a clear structure offers the benefit that the cloud environment is easier to understand and can be simplified to some extent in order to systematically implement and manage any security controls.
Ideally, these kinds of structures offer enough flexibility to effectively reap the benefits of the cloud while also offering a solid overall framework that makes it possible to quickly implement security controls and processes as standard, and to monitor them. In addition, considerations relating to the cloud security architecture should already be incorporated here.
“Cloud administrator” sounds very technical, but this is not necessarily the case. Because management and governance levels are both found in cloud environments, e.g. costs are monitored and managed, there should be clear definitions as to which tasks are assigned to which level (governance, management, operations) and which roles and responsibilities are associated with them.
Because the cloud must be accessible over the Internet (direct backbone connections are possible but still tend to be the exception), identity and access management considerations are crucial. The requirements, however, are just the same as those of other critical applications. Here it is important to develop an overview of the access methods that are possible and desirable. These can be expanded to include IT security requirements before being implemented.
A rough distinction should be made between governance, management and operations. The respective competencies should be clearly defined, although overlaps are possible. Because, for example, Azure is highly dependent on agility in creating and removing resources, it is important to define precisely where a competency starts and ends, as well as any overlap. It is also important that the actual account privileges defined within the cloud are well understood and applied. Azure offers various features, such as role-based access. The classic security principles of least-privileged and need-to-know should apply here as well.
Once you treat the cloud like an asset, you notice several parallels to applications. You can modify and utilize various parameters and processes, but the effect (if any) on the resources operated in the cloud is indirect. These features often fall within the domain of cloud administration or the previously mentioned hierarchy structures. So it makes sense to define which role is authorized to make administrative changes and which process is used to do so. Currently, Azure has no integrated change management workflow, but it does offer a resource lock to block resources or ensure changes can only be made with admin approval. This is designed to prevent such issues as accidental deletion of critical resources.
To monitor something you need to be able to measure it. Here again, the cloud should be treated as an asset. Neuralgic points should be logged and monitored, identifying who creates or deletes security groups, changes the structure, and so on. Azure offers a detailed activity log) on several levels, including an administrative category. It logs activities (create, delete, update and action) on the subscription level. Azure offers all of this “out-of-the-box”, but many of the alerts have to be defined by the user and configured accordingly.
From an IT security perspective, alerts should be configured in such areas as:
Once you’ve considered cloud strategy and governance, the next step is to establish a sound, transparent cybersecurity framework (e.g. NIST or CIS) and security concepts. This is approached much like on-prem infrastructure.
It is important to include the cloud itself in the asset inventory along with all related processes and resources that are operated and used in the cloud. This means that a general cloud configuration, as well as the resources operated in it, can be hardened according to a security baseline and included in security monitoring.
In addition, cloud providers themselves offer a wide range of security features. This in turn means that you need to decide which security concepts to apply to specific resources, or whether these can be covered by the cloud’s built-in features alone or with internal products and concepts (question of control).
So it is a good idea to become familiar with the security features of the cloud provider and to define whether and how these can and must be used. It is important that these decisions are made consciously. At the same time, the agility of the cloud, or the fast creation and removal of resources, is one factor that should not be underestimated.
The following approach can be helpful here:
Cloud applications are ubiquitous. There is no one answer to the question of whether using them is a good idea from a security standpoint. Exposure on the Internet, entrusting control tasks to others – these have to be assessed at the business risk level. On the use-case level, you can specifically define which data and processes are actually outsourced to the cloud. These should be conscious decisions made by the managers of business, risk, IT and IT security issues.
Anyone who opts for the cloud should not set out without a cloud strategy rooted firmly in the specific business case. Existing IT governance and cybersecurity frameworks should be carried over and adapted, with the cloud itself and the resources operated in it treated as an asset.
Here it becomes apparent that the management and administration of the cloud itself are just as important as the management of the resources being operated within it. The agility of the cloud is one of its biggest advantages. At the same time, it is imperative that this does not result in chaos. However, this agility can be achieved with the right governance and management, much like on-prem infrastructures.
Our experts will get in contact with you!

Lucie Hoffmann

Yann Santschi

Michael Schneider

Andrea Hauser
Our experts will get in contact with you!