Specific Criticism of CVSS4
Marc Ruef

Electronics and computers have been around for many years, but it has only recently become clear just how the market can be conquered by offering customer-centric solutions. The mass popularity of today’s smartphones is down to their simplicity and accessibility. When you hold one of these devices in your hand, you feel at ease, because it gives you an intuitive way to achieve your goals.
Smart homes are designed to replicate this very same effect inside our homes, transforming an apartment or house into a large system that can automatically learn what its inhabitants’ needs are and respond to them accordingly. Is glare from the sun making it hard to see the picture on the TV? The smart home activates the sun blinds. And once the whole family is sitting in front of the television, the comfort ventilation will be increased by 10% in the living room. So, the forecast says there’ll be snow after midnight? The heating system starts to gradually increase the flow temperature at 8 pm. Have the kids taken an iced tea out of the refrigerator? A new pack will be ordered in the next four days.
This type of integration – ideally installed by a specialized building technician – can greatly improve convenience and comfort. Intelligently positioned sensors, interconnected in a cleverly devised logic, can simplify and improve many things, turning a home into a powerful computer that is literally brought to life. It listens to input, processes data and performs tasks. In the age of spam and viruses, however, it is obvious that this technology also harbors security risks.
Wherever automation comes into play, problems can occur. Automation means that they can sometimes gain a foothold more quickly and have a more lasting effect. If the sensor for the fully automatic detection of sunlight is broken, you might have to wear sunglasses in your living room during the day until it can be repaired.
Worse yet, someone might deliberately launch an attack and manipulate the system. The refrigerator might be authorized to automatically place an order when you have run out of iced tea, but what happens if someone hacks into the internal network and orders a million boxes of iced tea? These shenanigans can be time-consuming, costly and result in legal action.
What is particularly striking, however, is the veritable professionalization of cybercrime seen in recent years. Hackers want to make money quickly and with as little effort as possible. Ordering iced tea is probably a less likely target because is not very lucrative due to commercial limitations.
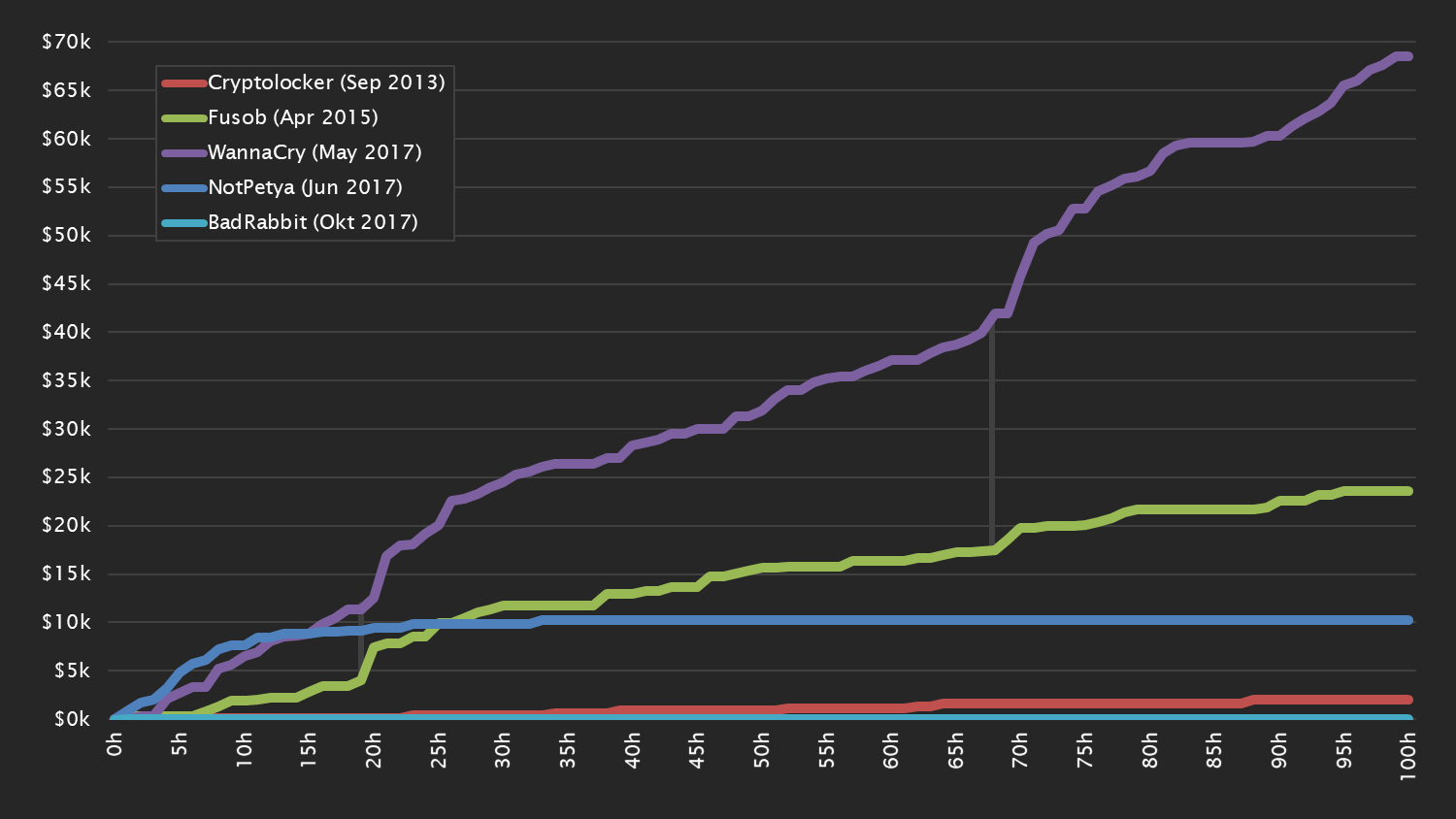
Ransomware offers a much more promising opportunity. If a computer is infected with ransomware, its data is encrypted, rendering it completely unusable. It can only be decrypted again if a ransom is paid to the ransomware developers. The most widespread of piece of ransomware, WannaCry, extorted USD 300 per infection and made USD 70,000 in the first 100 hours.
This principle could by all means be easily applied to smart homes, too. Instead of encrypting the data, heating systems could be hijacked and disabled. A 1000 dollar payment might be required to turn the heat back on – a lucrative business that can quickly make money, especially during the colder season.
Makers of IoT systems tend to ignore security concerns for a variety of reasons. First, it costs money to develop and integrate security mechanisms. Skimping on investment in this area increases competitiveness.
Add to this that the creativity of hackers is sometimes underestimated. For example, nobody would be interested in hacking a solar panel, right? Wrong! There will always be someone out there with the most outlandish of reasons and abstruse ways of taking advantage of people.
And finally, people often falsely assume that exotic systems cannot be manipulated or require considerable effort to do so. But just because there is no keyboard or monitor does not mean that they do not contain conventional computers. The technologies are often the same or only selectively modified, making it possible to use conventional techniques to attack even these seemingly exotic products. This aspect is also frequently underestimated when it comes to medical products.
Product manufacturers must rise to the challenge of ensuring cybersecurity. No matter whether it is a well-established heating manufacturer or budding smart device startup, both consumers and government agencies must hold them accountable and call for basic security requirements. There are decades of experience in traditional computer and network security to draw from here.
Likewise, building engineers must be trained in the secure installation and management of smart homes. This knowledge must find its way to property owners and tenants as well, because, ultimately, they are the ones who live inside their smart homes and who are directly exposed to the risks.
It is important for smart components to be as sound, modular and autonomous in their operation as possible. A successful attack on a sun blind system must not affect the heating system. The clear separation of components must be both physical and logical. This can be implemented through strict network segmentation and by only allowing interactions between the components when they are actually required – an approach that has also been essential for security in the automotive industry.
The systems must be regularly updated with patches and bug fixes so that any identified vulnerabilities can be fixed. This process must be as simple as possible in order to prevent any unnecessary administrative activities for this during operation. A good product supplier will also guarantee this kind of support for their product long into the future.
Complexity is the greatest enemy of security. The accessibility of systems over the internet and the connection of individual products poses security risks. Attackers can exploit the new possibilities afforded by smart homes to cause direct or indirect damage. Guarding against this requires a systematic approach.
Our experts will get in contact with you!

Marc Ruef

Marc Ruef

Marc Ruef

Marc Ruef
Our experts will get in contact with you!