Brain before post
Michèle Trebo

Impact of Cyber-Terrorism for Switzerland
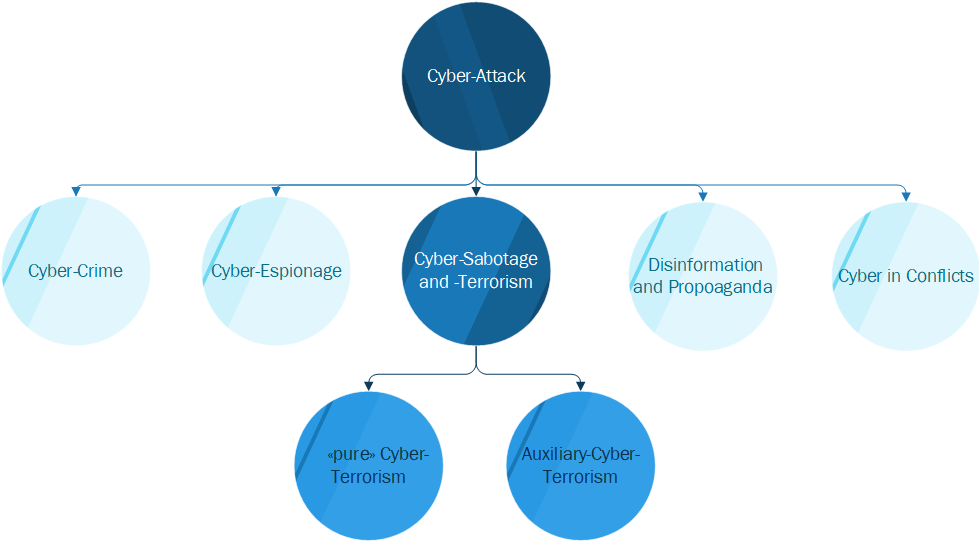
The cyber terrorism refers to a terrorist-motivated activity to disrupt or destroy the functioning of information and communication technologies in cyber space, which may also have physical consequences. The aim is to cause as much damage as possible, demonstrating power and intimidating and destabilizing an entire society. A distinction is made between “pure” cyberterrorism and auxiliary cyberterrorism. “Pure” cyber-terrorism refers to terrorist actions that use computer technologies and are virtual, whereas auxiliary cyber-terrorism uses IT (IT-supported assassinations, propaganda and communication structures for terror cells) but does not include virtual attacks. As digitization continues to grow, the risk of cyber attacks is also increasing in Switzerland.
1 Entirety of information and communication infrastructures (hardware and software) that exchange data with each other, collect, store, process or convert them into (physical) actions and the interactions between individuals, organizations and states that are made possible by this.
In mid-2021, TEN.info published a list of the world’s ten largest cyber attacks. At the top, the two computer worms NetSky and Sasser, which perpetrated DDoS attacks in 2005. In a Denial of Servive attack (DDoS), the target server, service, or network is overloaded with Internet traffic, disrupting the ability to reach the target.
Similar to when normal road traffic cannot reach its destination due to a traffic jam on the highway. The NetSky and Sasser computer worms affected computers of banks, travel companies, and public institutions worldwide, causing approximately $55 billion in damage. Another cyber attack was the WannaCry ransomware attack in 2017, in which cybercriminals extorted more than $4 billion using crypto-ransomware. Crypto-Ransomware encrypts data, making it unreadable. WannaCry exploited a vulnerability in the Microsoft Windows operating system and demanded a ransom in the form of bitcoins to decrypt the data. If the ransom of $300 was not paid, it was increased to twice that amount. If the victims did not pay within three days, they faced the permanent deletion of their data. Researchers disagree on whether anyone ever got their data back. The fact is that payment to the cybercriminals did not guarantee the release of the data. It is estimated that four billion dollars worth of damage occurred.
Also, at the top of the world’s largest cyber attacks is the “cyber heist of Bangladesh Bankhttps://indianexpress.com/article/explained/bangladesh-bank-robbery-north-korea-lazarus-heist-7375441/. In 2016, the SWIFT network was infiltrated using malware, triggering a total of 35 fraudulent transactions. Five of these transactions succeeded. Among them, $20 million was transferred to Sri Lanka and $81 million to the Philippines from the Federal Reserve Bank of New York, where Bangladesh maintained an account in dollars. The remaining 30 transactions for $850 million were identified as fraudulent in time and stopped. Of the total $101 million illegally obtained, $63 million could not be recovered. This cyber attack resulted not only in widespread loss of money, but also in economic damage and disruption around the world. Even though the aforementioned cyber-attacks were not based on a terrorist idea, they all had a great impact on society and caused considerable damage.
In 2016, the first person was charged with cyberterrorism in the United States. She was accused of stealing personal data of more than 1300 U.S. military and government personnel in 2015, along with her accomplices, and passing it on to the Islamic State. The list of this data was published shortly after in the name of the Hacking Division of the Islamic State (ISHD) under Kill List. However, it turned out that the data did not come from cyber attacks but from detailed open-source research. That same year, terrorist groups launched DDoS attacks, primarily targeting the Middle East. However, these attacks only caused websites to be briefly taken offline. The Tunisian Fallaga Team succeeded in defacing the UK National Health Service (NHS) website and displaying gruesome images of the Syrian civil war. Although concerns about potential cyberterrorism have increased in recent years due to the ever-growing digitization, cyber attacks that have caused major damage have rarely been attributed to terrorist organizations.
In the late 1990s, when the Internet was still considered anonymous, terrorist organizations used websites, forums, and other platforms to quickly and cheaply gain new followers. After the Islamic State proclaimed the caliphate in 2014, the number of terrorist organizations and their followers increased. The dissemination of information, advice, and texts was a breeze through encrypted messaging apps such as Telegram, and with it the radicalization of individuals from around the world. There is evidence that terrorist attacks were increasingly planned through social media, the darkweb, and as mentioned earlier, messaging apps. Attacks could be remotely controlled, so to speak, by the masterminds.
Even if cyber terrorism does not necessarily pose a major threat to Switzerland directly, Switzerland must prepare itself for the fact that cyber attacks will occur more frequently due to constantly evolving digitalization and consider how it can counteract or protect itself against them. Particularly in the event of a cyber attack on authorities, large companies or the healthcare system, Switzerland’s infrastructure could be brought to a standstill within a very short time, resulting in massive damage.
We are going to monitor the digital underground for you!

Michèle Trebo

Michèle Trebo

Michèle Trebo

Michèle Trebo
Our experts will get in contact with you!