Foreign Entra Workload Identities
Marius Elmiger

Understanding the Fundamentals of Tiering
This first article in a two-part series discusses the importance of containment using the Microsoft Credential Tier model as an example. The second part covers the implementation, identifying Tier 0 objects, and measuring and visualizing the progress of an Active Directory Credential Tier implementation.
Andy Robbins from SpecterOps, during one of his presentation Attacking and Defending Azure with BloodHound, made a statement that deserves attention: “For over 20 years, the same or similar Tactics, Techniques, and Procedures (TTP) have been consistently employed to compromise enterprises relying on Active Directory.” Why does this persist? Active Directory is a widely used Identity Provider (IdP) and can be found in almost all IT environments. Due to its popularity and age, vulnerabilities in this service are well-documented and manifest in various ways, including legitimate protocol abuse, misconfiguration, suboptimal management practices, permission misuse, neglecting updates or hardening recommendations, and more.
The challenges surrounding IdPs are not unique to Active Directory; other IdPs like AWS, Entra ID, and GCP face similar hurdles. Major players like Google, Microsoft, and Amazon have yet to completely solve the difficulties of securely operating these systems. Simply adding more security tools to the mix does not effectively solve the root cause. Instead, the focus should be on fundamental prevention methods. In the blog post Defenders Mindset John Lamberts states, “Defenders think in lists. Attackers think in graphs. As long as this is true, attackers win.” This highlights the need for a shift in perspective, emphasizing the importance of understanding the adversary’s tactics and adopting a proactive, strategic approach to security. Unless we change our mindset for securing IT environments, we will be stuck in the same discussions as adversaries keep using the same tactics, techniques, and procedures to compromise IT environments.
A highly effective strategy for enhancing Active Directory’s security involves analysing existing attack paths and assessing the impact of their removal. For in-depth insights into this approach, refer to the articles The Attack Path Management Manifesto by Andy Robbins and Attack Path Analysis – Gaining an Advantage Over Adversaries by me. However, it is essential to attain a security standard for an Active Directory environment. Otherwise, removed attack paths may resurface. To establish a defined state, a security model known as Credential Tiering becomes indispensable. The upcoming chapter will explain the concept of Tiering and its significance as a fundamental element in securing an identity-centric environment such as Active Directory.
A Tier-Model is a framework that categorizes identities and the resources they access into various tiers based on their value or importance. Tiering requires the implementation of security controls to maintain separation between these tiers. Additionally, it defines rules for segregation, specifies fundamental controls that must be in place, and acknowledges the possibility of additional controls. There are different types of Tier-Models depending on the environment, such as on-premises infrastructure, Active Directory, Microsoft Cloud, AWS, Business-Critical-Applications and so forth. The fundamental concept of a tier-model is coming from the Bell-LaPadula security model, which aims to preserve data confidentiality and the Biba-Model, which focuses on data integrity.
A more detailed explanation if tiering is helpful can be found in the following two articles, which were published in 2012 and 2014 by Micosoft: Mitigating Pass-the-Hash (PtH) Attacks and Other Credential Theft Techniques_English.pdf and Mitigating-Pass-the-Hash-Attacks-and-Other-Credential-Theft-Version-2.pdf. These documents discussing Active Directory attacks and are providing holistic planning strategies that, when combined with the Windows security features, will provide a more effective defense against credential theft attacks. We highly recommend reading these two significant papers. In the paper from 2014, Microsoft explains tiering as a way to prevent an entire IT environment from being compromised by the loss of a single asset. The analogy used is that of large ships having compartments to limit the damage caused by a leak. By designing IT environments in a similar way, the loss of confidentiality, integrity, or availability of one or several assets can be contained and prevented from affecting the rest of the environment. Followed by the analogy is the containment model presented and called Tiering Model Designed for Active Directory. In this article, we will refer to the model as the Microsoft Credential Tier model. This model has three tiers of administrative privilege, but in certain cases, extra tiers may be required. However, additional tiers must be added cautiously and should not introduce unnecessary tiering violations.
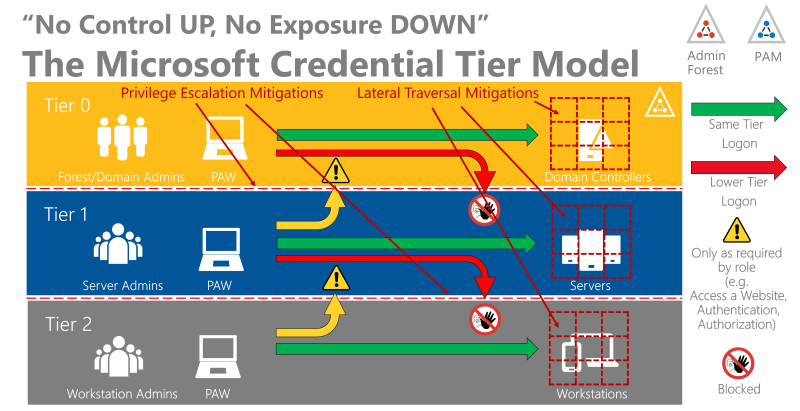
The model aims to block attackers from gaining higher privileges with stolen credentials. Microsoft describes the following rules for the model:
To be able to make a tier assignment, a holistic view of each individual service and Active Directory permission must be taken. The following question must always be answered: Does a control-up or exposure-down risk arise? For example: Domain controller virtual machines are operated by the solution System Center Configuration Manager (SCCM). SCCM is operated by Tier-1 administrators. This creates a control-up risk resulting in a tiering violation. This example introduced the dependency chain paradigm. Additional upstream risks to a domain controller could include:
And translated into a not-finished graph. PS: It is a valuable exercise to extend the below graph to visualize the dependency chain to important IT components.
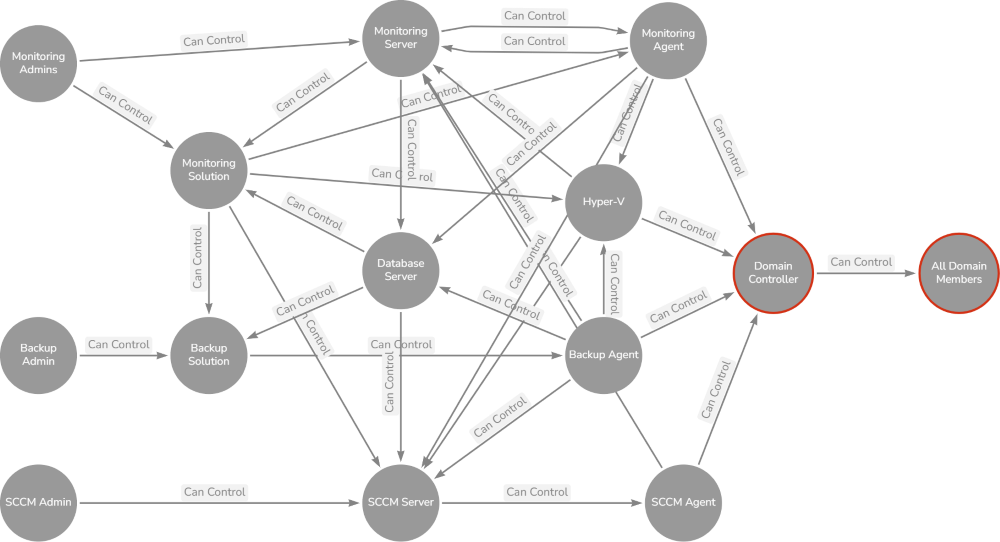
All of the above identified upstream risks can lead to a downstream control of all business data, accounts and devices that are directly or indirectly managed by Active Directory. Based on this revelation each identified tiering violation must be addressed. Various mitigation options are available:
| Option | Description |
|---|---|
| A | Demote AD objects and/or applications to a lower Tier (i.e, PAM for Tier-1 and Tier-2) |
| B | Independent Tier 0, Tier 1 and Tier 2 objects and or applications (i.e, Dedicated SCCM installation for Tier-0, Tier-1 und Tier-2) |
| C | Application Role-based access control (RBAC) separation – Robust internal RBAC security model is required (i.e, Tier 1 manages SCCM – Tier 2 administrators have only access to the Tier-2 clients and software packages) |
| D | Move AD objects and/or applications to the specific tier (i.e, Active Directory Certificate Services must be moved to Tier 0) |
| E | Encryption of higher tier data if it needs to be stored on lower tier components. The private key remains in the higher tier |
Another way to identify tiering violations can be done via the following method:
The following drawing serves as the use case example:
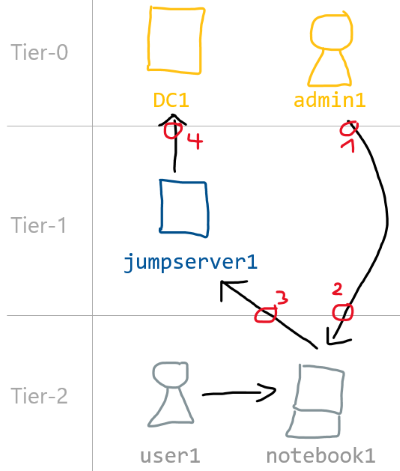
The drawing shows four tiering violations:
By the way this is a common management pattern we often encounter during assessments or red team engagements. Internally we call the server jumpserver1 credential harvester and is often one of our targets. Back to the topic of what we can do to mitigate the control-up and the exposure-down tiering violations. From our five options presented above we should go for option B:
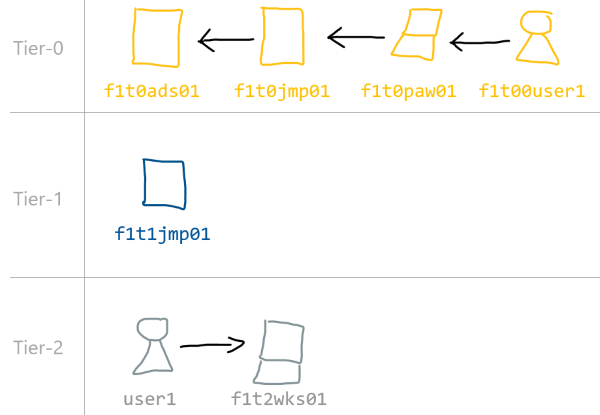
Every entity in a tiering should follow a strict naming convention. This provides several advantages, particularly in terms of auditing. Following an example for user accounts:
| Shortname | Description |
|---|---|
| f | AD Forest |
| 1-9 | Forest Number |
| t | Tier |
| 0-2 | Tiers |
| 0-2 | Level of access: 0=Tier administrator, 1=Server Admins, 2=Admin on particular servers or clients |
If none of the mitigation options can be implemented, analyses should be performed to determine how the exploitation of tiering violations can be made more difficult or at least be detected. If nothing is feasible, the risk should be formally accepted and documented, along with its potential consequences in case of an incident.
To mitigate the lateral traversal threat within each tier, there must be dedicated privileged users who are granted access to objects for administrative tasks. An example of this is a server administrator who is granted access to the servers and services to perform regular maintenance and monitoring tasks. However, there will also be a need for privileged access to manage these server administrator. This access will be performed by a tier administrator. An other example in the form of a use case:
To minimise the lateral traversal risk for user1 multiple admin accounts are necessery:
In this case user1 should have three different admin accounts. A Privileged Access Management (PAM) solution may be used to minimize the number of dedicated admin accounts. However, we frequently encounter PAM setups that appear to be costly security by obscurity solutions. They often imply that users may have initially undergone an seperate access management approval process, but subsequently, they can obtain temporary elevated privileges without the need for Multi-Factor Authentication (MFA) or an approval process, regardless of the device they are using. Consequently, it is crucial for PAM solutions to strictly adhere to the above discussed tier model restrictions to avoid tiering violations.
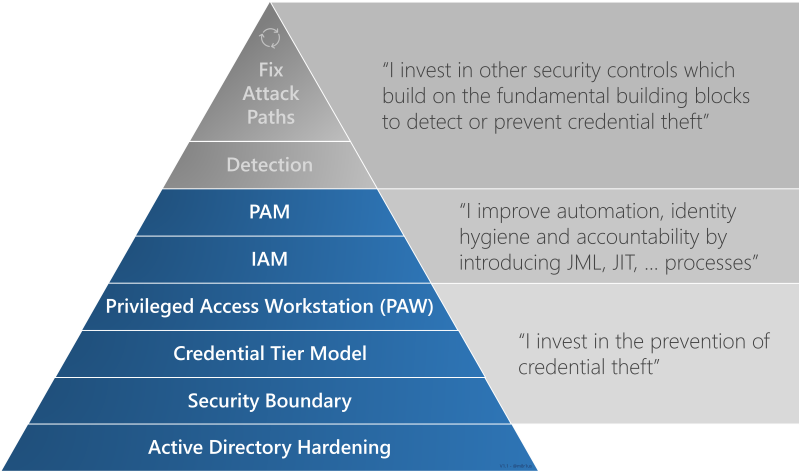
Certainly, there are other essential aspects that contribute to a successful Credential Tier implementation. These include for example security boundaries, Privileged Access Workstation (PAW), hardening, access-management and automation. The following simplified Credential Tiering Hierarchy of Needs is modeled after Maslows Hierarchy of Needs and the Incident Response Hierarchy of Needs. It outlines the phases organizations can follow to enhance the segregation of entities and subsequently make credential theft more difficult for adversaries. The capabilities at the bottom serve as essential prerequisites for effectively implementing the capabilities above them, including those associated with the Credential Tier model.
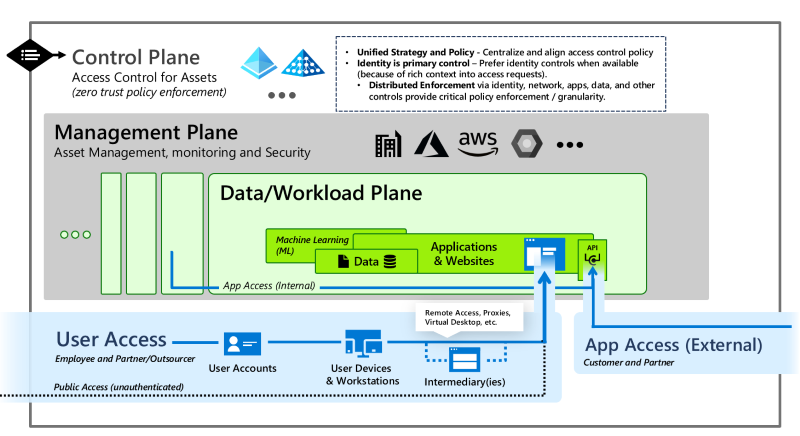
According to Microsoft the Enterprise Access Model replaces the Active Directory credential tier model which was designed to prevent unauthorized privilege escalation in an on-premises Windows Server Active Directory setup. The Enterprise Access Model should encompass all elements from the Active Directory credential tier model while addressing the access management requirements of a modern enterprise, including on-premises, multiple clouds, internal and external user access, and more. In the new model the Control Plane is the equivalent of Tier 0, whereas the Management Plane and the Data/Workload Plane are Tier 1. Access to the planes in Tier 0 and Tier 1 should happen from Privileged Access Workstations (PAW), separate from regular User Access and App Access from devices in Tier 2. Outlined in the Securing Priviled Access articel. To summaries nothing has changed, the challenges of segregation are absolutly the same. Maintaing a secure posture for Active Directory is difficult, mainting a secure posture for the Microsoft Cloud or general Clouds are even more challenging. The article Microsoft Cloud Security – The Top-10 Riskiest Configurations outlines what we see during cloud environment assessment. Most of the outlined risks can be addressed with Credential Tiering.
The second article addresses this question. The article provides guidance on how the transition to a credential tiered environment might look like. It also presents a method for measuring security improvements during this process.
In order to enhance security in an identity-centric environment, Credential Tiering is a fundamental component. It can help prevent security breaches that could compromise the confidentiality, integrity, or availability of the entire environment. It’s important to consider the significance of upstream risks and their potential impact on downstream controls. Tiering is an enduring concept that cannot be easily replaced by cloud solutions or other tool-based methodologies. Hence, it is essential to understand the value of segregation and start applying it to identity-centric solutions. Implementing Tiering may require significant effort as it addresses the issue comprehensively and the involvment of multiple teams. However, starting in phases, such as focusing on the most privileged entities first, can significantly enhance security and make it already more difficult for an adversary to gain widespread access rights.
We are going to monitor the digital underground for you!

Marius Elmiger

Marius Elmiger

Marius Elmiger

Marius Elmiger
Our experts will get in contact with you!