Burp Bambdas & BChecks
Ralph Meier
How to protect your BIOS
For the purpose of this article, we will not go into the details of the start-up process of a computer, but will focus on the BIOS, the UEFI, their differences and hardening possibilities.
The BIOS was initially designed for 32-bit systems, but due to the requirements of new hardware, a successor had to be developed that would work better with 64-bit systems. In the 1990s, Intel developed the Itanium architecture together with HP, which was the first to use the Extensible Firmware Interface (EFI) developed by Intel. With the EFI, the memory and processing limitations of the BIOS due to 16-bit compute mode, limited system memory and tedious programming in assembly language were eliminated. Intel brought EFI version 1.10 to the UEFI Forum, an industry consortium consisting of chipset, hardware, firmware and operating system manufacturers. It was in this industry consortium that the Unified Extensible Firmware Interface (UEFI) was born, and to this day the development of UEFI standards are managed by it. Since the mid-2010s, UEFI has been considered as standard and is sometimes also referred to as UEFI BIOS. Like BIOS, UEFI is installed on the mainboard by the mainboard manufacturer. The operating system must support UEFI, otherwise interaction is not possible. For Windows, this was done in 2008 with Windows Vista Service Pack 1.
Until UEFI support was available in the desired operating system, the Compatibility Support Module (CSM) of the UEFI could be activated, whereby operating systems without UEFI support could continue to be used on mainboards that already used UEFI. CSM emulated the BIOS and was responsible for backwards compatibility for older hardware, older operating systems and also 32-bit systems. It should not be used on 64bit systems with UEFI support, as otherwise certain UEFI functionalities are lost. Thus, CSM, if the option is available in UEFI, should be disabled before installing a 64Bit operating system. In 2020, CSM was then removed from UEFI.
The following table shows an overview of some of the differences between the BIOS and the UEFI:
| Differences | BIOS | UEFI |
|---|---|---|
| Developed for | 32Bit systems | 64Bit systems |
| Supports boot media | < 2 Terabyte | < 9.4 Zettabyte |
| User interface | DOS style | Modern GUI with mouse control |
| Partition table | Master Boot Record | GUID partition table |
In addition, UEFI has the ability to download hardware drivers from the internet. It is faster than BIOS and includes some improved security features, which are mentioned in the chapter UEFI Hardening. Since Windows 8, the product key of Windows is stored in UEFI and no longer has to be typed from a sticker on the computer when reinstalling.
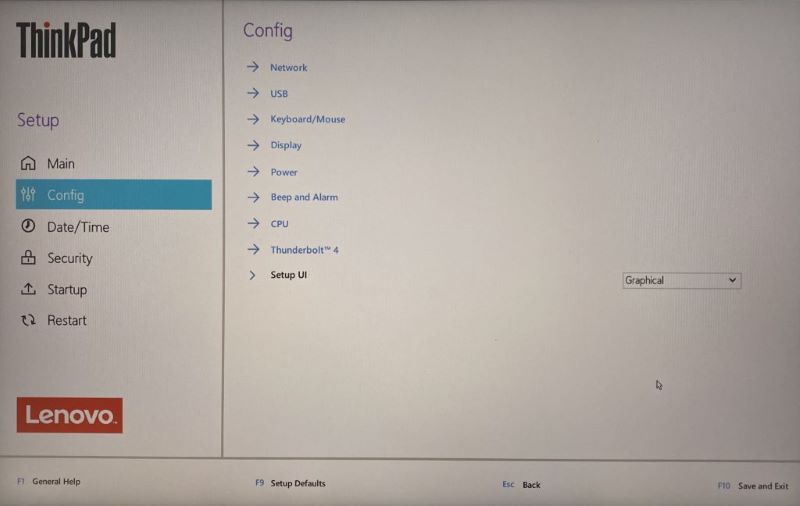
In the UEFI, there are various configuration options such as enabling and disabling access to the various I/O interfaces of the unit. This allows I/O ports that are present but never needed by the user to be disabled. If they are needed at a later time, they can be easily re-enabled in the UEFI. There are more configuration options in the network section, such as Wake On Lan (WOL) settings, UEFI IPv4/IPv6 Network Stack, MAC Address Pass Through, various USB and Thunderbolt settings, mouse and keyboard settings, display settings, power supply settings and standby settings. In addition, the system date and time can be adjusted, which can be the case if the CMOS battery is old or empty at start-up. In this case, it should be replaced with a new CMOS battery. Various passwords can be set, such as a supervisor password, which must be defined in order to be able to enter the UEFI and edit changes. A power-on password, hard disk passwords, a minimum password length and other configurations can also be set. In the UEFI, you can define which interfaces or storage media can be used for booting and also for their boot order. It contains various virtualisation settings, which differ depending the hardware. There are other security configuration options besides setting various passwords, such as memory protection. More information are held in the chapter UEFI Hardening down below. Since the UEFI is structured differently depending on the product or motherboard manufacturer, it may contain additional configuration options of its own. Mainboards that are primarily intended for gaming purposes often have configuration options for RGB lighting or overclocking.
In addition to the legacy BIOS and UEFI, there are other BIOS alternatives that have different purposes and were developed for other hardware.
The Universal Boot Loader (Das U-Boot) is mainly used for microcontrollers in the embedded systems area. It offers flexible configuration options during compilation. The behaviour can also be influenced during runtime via the command line. In its beginnings, U-Boot was developed for PowerPC. In the meantime, there are various projects for different processors, such as the ARMboot for ARM.
In 1999, the development of the free and open-source LinuxBIOS started, which was later renamed to today’s Coreboot. Coreboot focuses on initialising the necessary components for the boot process of the operating system and gives control to the operating system as early as possible. The focus of Coreboot is mainly on Linux distributions.
Google delivers its Chromebooks with Coreboot. For a few months now, the MSI PRO Z690-A mainboard has been offered with the Coreboot firmware Dasharo. This allows a PC to be operated without UEFI, even with Windows 11 installed. In addition to Coreboot, Dasharo also consists of an open-source UEFI part. With it, they achieve compatibility with numerous graphic cards with UEFI firmware, UEFI Secure Boot and the initialisation of the Trusted Platform Module (TPM).
Coreboot is also used for sensitive applications in the industrial sector or for server boards of the VPN service provider Mullvad. Distributions that are primarily focused on high security, such as Qubes OS, pay attention to the support of open-source BIOS such as Coreboot, among other things, in their hardware certification.
One disadvantage of Coreboot is that there are no uniform Coreboot images. This means that the coreboot firmware must be adapted for each mainboard, and this requires technical information that is often not publicly available. Therefore, firmware blobs are used so that Intel or AMD CPUs can, as an example, control the random access memory. Adding non open-source code decreases the trusted code base, which is one of the benefits of Coreboot. For this reason, the choice of compatible components is also limited. There is often no built-in update function when using Coreboot. This is because most mainboards are delivered with UEFI, and with the changeover from UEFI to Coreboot there’s no longer manufacturer updates provided. Specific mainboard functions or settings such as RGB lighting and overclocking functions are also missing in Coreboot.
If the UEFI is not properly protected, it is easy for an attacker with physical access to install a foreign operating system on the target computer, and thus read an unencrypted internal hard disk.
First, a strong and complex password should be set for the UEFI so that no changes can be made by unauthorised third parties. There are UEFIs with a read mode, which is accessible without a password, but only a limited view of the UEFI configuration is possible.
The Secure Boot option should be activated in the UEFI so that only signed boot loaders are booted. This has been supported in Windows since the introduction of Windows 8.
The UEFI should be regularly checked for updates and updated so that any vulnerabilities found can be quickly remedied. The programme for updating the UEFI can be downloaded either from the device manufacturer or the mainboard manufacturer, provided that the UEFI from the manufacturer is still used. In the case of Lenovo, the Lenovo System Update programme can be used for this.
If the option Botton Cover Tamper Detection is activated, the UEFI password is required for the boot process of a laptop as soon as a device cover is missing or has been opened. There are differences between devices and manufacturers, some distinguish between cover behind the laptop screen, cover around the laptop screen, keyboard cover and cover on the bottom of the device.
Input and output interfaces of the unit that are not used or needed should be deactivated, so that the attack vector is not unnecessarily increased.
In this category, it’s possible to define who is allowed to flash the UEFI; all users or exclusively users with the UEFI password. In addition, it can be defined whether a rollback to a previous UEFI version and the UEFI update via Windows is allowed.
These are security measures against buffer overflow attacks. The configuration options underneath such as Execution Prevention should be enabled.
The aim is to avoid direct memory access (DMA) attacks, which are side-channel attacks carried out via high-speed interfaces with direct system memory access, such as Thunderbolt, USB4 or PCI Express. Further details on DMA attacks can be found in the article Attacks via peripheral devices.
There are still some hardening configurations that are indirectly related to the UEFI or the start of the computer, but cannot be completely configured in the UEFI.
It is strongly recommended to use a hard disk encryption, in the case of Windows it would be their in-house Bitlocker. This works with the Trusted Platform Module (TPM), which can be additionally protected with a startup pin for enhanced protection.
Depending on the UEFI, it is possible to set other passwords apart from the UEFI password, such as passwords for hard disks or for computer start-ups.
In order to be able to perform a quick recovery after a misconfiguration of the UEFI, a flat CMOS battery or other failure of the UEFI, it is worthwhile to perform a UEFI backup. Depending on the UEFI used, this can be performed directly within, or alternatively with associated means.
The BIOS is not only the beginning of the computer start process, but at the same time an easy entry point for attackers with physical access to the target device. Therefore, it is important to keep the BIOS up to date and to apply sufficient hardening. UEFI password protection, active hard disk encryption and Secure Boot form a good foundation on which to build on with additional security settings. In the end, however, it is also a trade-off between security and usability for the individual user or their device administrator.
Our experts will get in contact with you!

Ralph Meier

Ralph Meier

Ralph Meier

Ralph Meier
Our experts will get in contact with you!