Specific Criticism of CVSS4
Marc Ruef

During our security checks it’s not unusual that auditors, clients and partners discuss vulnerabilities and risks. This discussion, assuming that it is civil and all people involved respect each other, is of great importance. Because during those discussions, the quality of the project itself as well as the overall understanding of the subject of information security will talked about.
Some of our clients are less versed in recognizing the real-life risks of an attack scenario. Sometimes, the technical understanding of the attack mechanism is lacking. Other times, it’s the understanding of the psychology of an attacker.
As an example: When we find reason to believe that a firewall component is used during one our of our network analyses, then we might classify this as a medium finding. Medium means that the vulnerability presents a means for an attacker to gain advantages in preparing an conducting an attack.
There are typical indicators in network traffic that hint at the use of a packet filter:
DROP, undesired packets are discarded without infoming the sender about the rule infraction. Usually, systems using no firewall functionality deploy a DENY rule. The packet is dropped and the sender is informed about the infraction. This usually happens with a TCP segment with set RST flag or an ICMP unreachable packet. In nmap, ports are thus labelled as CLOSED and not as FILTERED. If the switch --reason is enabled, the state identified will be explained.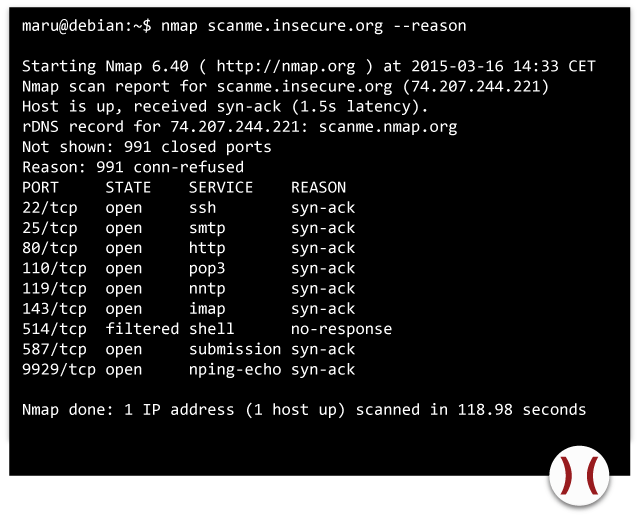
Where is this risk that comes from using this seemingly marginal information? As an attacker, it’s important to know that the target environment is using security component, which mechanisms are deployed and predicting how those mechanisms react. In case a packet filter can be identified, it’s reasonable to assume that certain communication is limited and certain activities are protocolled or that they cause an alert. Therefore, a highly professional attacker is keen on adapting various means, mainly the following:
The example of the packet filter in this article is just that, an example. Similar effects are observable in other seemingly unimportant analyses.
It’s part of an operator’s responsibility to mask the use of security mechanisms to shield them from detection or to at least make finding them difficult. This robs highly professional attackers of the possibility to adjust to their target environment easily. The chances that the mechanisms go undetected and therefore block intruders get higher. This should be the immediate goal for vulnerabilities that, at first glance, seem to be nothing but a minor risk. Every improvement in an environment is of advantage to its operators.
Our experts will get in contact with you!

Marc Ruef

Marc Ruef

Marc Ruef

Marc Ruef
Our experts will get in contact with you!