Specific Criticism of CVSS4
Marc Ruef

In the last 20 years, attacks on computer systems have assumed a level of professionalism that is sometimes astonishing. As well as technical developments, this has also led to enormous economic growth. Stolen data and compromised systems are traded in various markets, as a result of which trade in exploits is big business now. This article looks at the pricing structure observed in the exploit market.
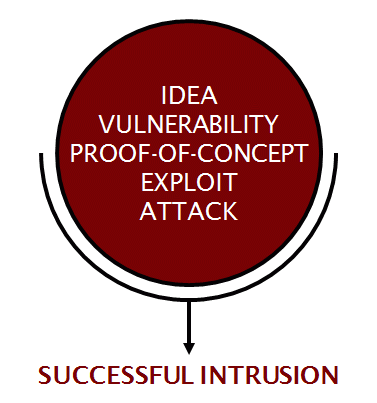
An exploit is a piece of software that takes advantage of a vulnerability in an automated manner. This puts it in a special class of attack tools. On the one hand, exploits are deployed openly in the course of legitimate security tests in order to prove the susceptibility of suspected vulnerabilities. On the other hand, they are also of interest to various attackers of dubious provenance who wish to obtain greater access.
Numerous different techniques and solutions exist that significantly hinder the exploitation of vulnerabilities. In programming, for instance, the following mechanisms can be used:
| Mechanism | Description |
|---|---|
| Validation | Verification of validity of entries |
| Sanitation | Transform and/or correct entries |
| Encoding | Transform entries to comply with encodings (e.g. with XSS) |
| Assertation | Establish expectations |
| Strong typification | Strict assessment by comparison (if, like, etc.) |
| DEP/NX/XD | Prevent code execution in attacks on data storage |
| /GS | Protect against buffer overflow attacks |
| ASLR | Random sorting of storage areas |
| Canaries | Terminate and separate storage areas |
In addition, more advanced security mechanisms are being added to modern environments all the time. Traditionally, these include:
| Solution | Description |
|---|---|
| Cryptographic mechanisms | Authenticate and protect data during storage and transfer |
| Anti-virus | Detect and repulse malware (viruses, Trojan horses, etc.) |
| Firewalls | Restrict and log network attacks |
| IDS | Detect attempted and successful attacks |
| IPS | Prevent envisaged or current attacks |
| DLP | Prevent outflow of data |
Consequently, development of exploits – particularly at a professional level – is associated with high costs, with reliable and powerful exploits fetching high prices on the market. For years now, deep-pocketed actors from the intelligence sector and organized crime have sent prices for high-end exploits soaring.
Purchase of an exploit takes advantage of a vulnerability without the need to (completely) understand it at a technical level. This means that purchasers of exploits, including attackers, can exploit vulnerabilities without technical knowledge.
In the 1990s, the trade in exploits was largely restricted to small circles, often in the IRC environment. Back then opportunities to buy and sell exploits would arise through contacts, with exploits largely traded among like-minded people. But these activities did not amount to a systematic market with a commercial foundation, due to the lack of importance of computer systems in general and exploits in particular.
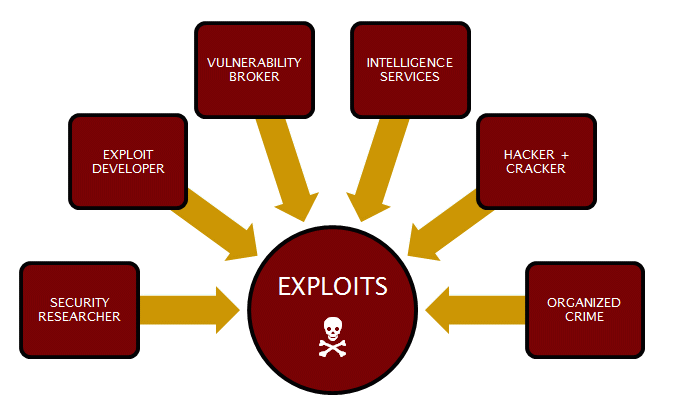
At the turn of the millennium, the first vulnerability brokers established themselves, coordinating the release of vulnerabilities and exploits, and selling and reselling. This gray market competes with a black market that takes places underground. Exploits are increasingly traded in markets in the dark net. As with other platforms, vendors can put exploits up for purchase. The price is set beforehand or determined by a bidding procedure.
In the broadest sense, vendors’ bug bounties also form part of the exploit market. After Netscape issued version 2.0 of its browser Navigator in 1995 it became the first company to reward the reporting of vulnerabilities. It took some time before other manufacturers incorporated this model into their quality assurance. Since then, a bug bounty program has been considered the done thing. It’s a step that puts one in the company of major companies such as Google, Facebook and Microsoft.
Not every manufacturer offers bug bounties and not every vulnerability found is remunerated. And the payments represent a fraction of the regular black market price, particularly since these programs are primarily concerned with vulnerabilities rather than exploits. To make big money with exploits, you need to focus on the black market. But with increased earning opportunities comes a greater risk of fraud and legal entanglements. The choice of whether to sell your wares underground or not is often a question of ethical principles and risk appetite.
Our research department has been monitoring the exploit market for more than 15 years. This has provided us with a wealth of findings into the composition of prices and changes in pricing over the course of time.
Using these observations as a basis, we have developed a model to calculate the price of exploits. This allows us to determine historical prices for past exploits, construct current pricing and predict future price developments. We always compare the results of our calculation model with currently observed prices in the market to track deviations and improve the workings of the model. Our price predictions prove to be particularly accurate, and in certain circles are used as a benchmark in price negotiations.
The algorithm developed by us reflects the high degree of complexity we have encountered in our years of research. For commercial reasons, only the basic details will be discussed here.
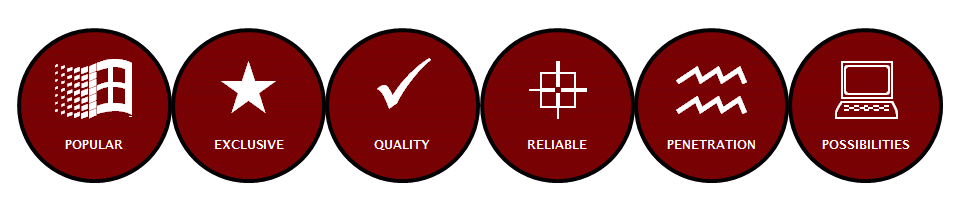
A handful of basic characteristics determine the initial price structure of an exploit. These include:
An exploit is considered zero-day when it has not yet been issued or addressed in public. When someone discovers a new vulnerability and is able to exploit it exclusively, this is considered a zero-day exploit. The value of an exploit is at its highest at this point, since its exclusivity and the possibility of successful exploitation are at their peak.
Regardless of the general characteristics listed above, the underlying price of a zero-day exploit is defined by the vulnerability class in question. The following table shows the identifiable classes in descending order. A remote code execution (RCE) employing access violation is generally worth more than a reflected cross site scripting (XSS) vulnerability.
| Pos. | Class | Examples |
|---|---|---|
| 1 | Access violation with code execution | buffer overflow, format string |
| 2 | Database access | SQL injection |
| 3 | File access | Direct access, directory traversal |
| 4 | Weak authentication | no authentication, weak password guidelines, standard password |
| 5 | Information disclosure | files, sources, products, storage, etc. |
| 6 | Web attacks | cross site scripting (XSS) and cross site request forgery (CSRF) |
| 7 | Weak encryption | no encryption, weak algorithm, weak code |
| 8 | Denial of service (DoS) | overload, wastage, recursivity, etc. |
| 9 | Spoofing | simulation of hosts, certificates, URLs, etc. |
| 10 | Race conditions | error with logical and/or temporal dependencies |
The basic price determined by the vulnerability class also forms the basis for other influencing factors. At this point, it should be noted that these basic prices have changed over the course of time. According to our calculations, the value of a given vulnerability released in the 1960s was less than 25% of the value of a 2016 release. In the 1990s, however, prices had already reached 80% of current values.
The structure of the attack must also be taken into consideration. To a large extent, the following attributes can serve as orientation:
For example, the value of an exploit falls by 30% if it can be executed only locally rather than through the network. Prices fall almost as steeply if complex authentication (e.g. multiple authentication) is required.
By contrast, prices increase if there is an opportunity to exert influence on the integrity (change) of the object under attack. A more modest increase arises if the intrusion relates solely to confidentiality (access). Destructive attacks with an influence on availability can not compete in cost terms. Here, there is a distinction between options that can be exercised only in a reduced context (e.g. affecting the web server only) and those that apply to the entire system.
Just as the popularity of the targeted product can influence the price, a vulnerability or its exploit can also come with its own popularity with a similar impact on price. A vulnerability may be the subject of extensive discussion in the mass media – Heartbleed and Poodle are two such instances. Attacks or exploits that are particularly innovative (e.g. ones that affect toy bears or bodycams) or ingenious may also accrue popularity. This popularity can have either a beneficial or detrimental impact on the price depending on the time at which it is measured and the information already in circulation.
Currently, we use about 100 data points to determine the zero-day price of an exploit. Those listed above exert the greatest influence on the price segment in question. However, the sum of many other factors not mentioned here can lead to results that may seem surprising at first glance.
Zero-day prices are static because they allow the price structure to be determined at that specific point in time. The passage of time and subsequent incidents can nonetheless have an impact on the price. Accordingly, our model is able to determine the current price as well. It can provide figures for historical, present and future points in time.
Most (but not all) incidents on the time axis push exploit prices down. Among the most significant incidents are:
All these incidents have a direct impact on the price of the exploit; they also alter the future erosion of the price regardless of the occurrence of further incidents. The price of an exploit inevitably changes over the course of time; for example, it falls faster as soon as a counter-measure is available (which in most companies means it has already been applied).
The change brought by the mere passage of time is the most complex to calculate, since a purely linear reduction in price can not be assumed. Ultimately, this change functions like a curve that must be adapted to reflect the basic, unchanging characteristics, the incidents to date and the time elapses between them.
Exploits play a major part in the cyber-security field. They represent tools that attackers can use to secure advantage for themselves. Complex attack scenarios result in exploits of complex development, which is why a market for these exploits has emerged. It allows actors to obtain exploits and carry out attacks without the need to process or even understand the technical background.
The price structure on the exploit market is influenced by various factors. In the first instance, it is the popularity of the targeted product and the exclusivity, quality and reliability of the exploit that determine the price.
The calculation of zero-day prices is based on static values; with determination of the current price, time factors (incidents and passage of time) must be taken into consideration. Thanks to sophisticated analysis, it is possible to determine the price of an exploit at every point in its lifecycle.
Our experts will get in contact with you!

Marc Ruef

Marc Ruef

Marc Ruef

Marc Ruef
Our experts will get in contact with you!