Enhancing Data Understanding
Rocco Gagliardi

An Information Technology Security Assessment is a set of methods, procedures, and documents to find vulnerabilities and risks in an organization and assure that adequate security controls are well managed. Does it mean that you can walk through a company, fill a questionnaire, and write something in a fancy form?
Not really. Assessing an object is basically an easy job: Execute a check-list and confirm if it’s compliant or not. But what if the object is a complex organization and you don’t have months of time?
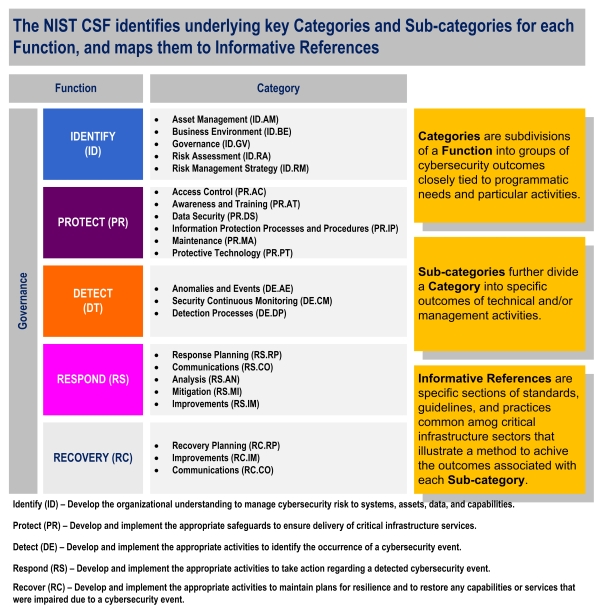
Many tools exist to support the auditor in his job; my favorite, with an optimal balance between complexity and completeness, is the NIST Cybersecurity Framework, or NIST-CSF.
CSF was originally built to provide guidance of critical enterprises. However, the contents of the NIST CSF are applicable to any firm, business, and enterprise with an interest in its own cybersecurity.
The CSF includes implementation tiers that support a high-level measurement of organizational cybersecurity and create a view of security that is measurable and organized by risk.
The five framework core functions are explained below. These functions are not intended to form a serial path, or lead to a static desired end state. Rather, the functions can be performed concurrently and continuously to form an operational culture that addresses the dynamic cybersecurity risk.
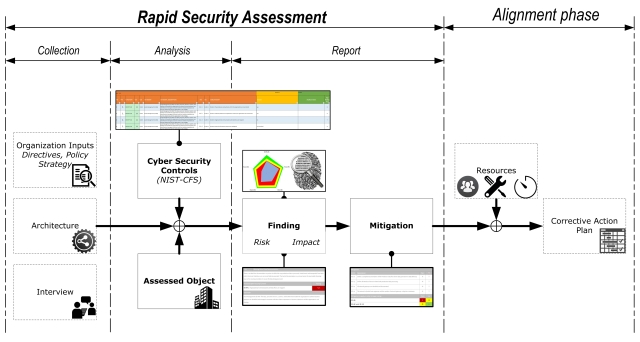
A security assessment is a long sequence of reading documents, decoding infrastructure and processes, identification of gap between the list of controls in place and those required by legal or technical standards, checking if the process are in place and well managed, checking if the systems are configured as documented, documenting the differences, and reporting them. Even the sampling check and documentation of a single server may take days.
In most case, however, for an identification of the problem areas it is not necessary to go deep since first meeting. It is useful to quickly check different aspects of the organization and, with experience, it is possible to drive the corrective action plan in an efficient manner. But, if you are quick, you are also prone to errors. During assessment you are normally finger-pointing at people and this may have consequences on those people, not always enjoyable.
The assessment must be rapid but also complete and coherent, and the results must be measurable.
We try to measure the quantity and the quality of the controls in place with following steps:
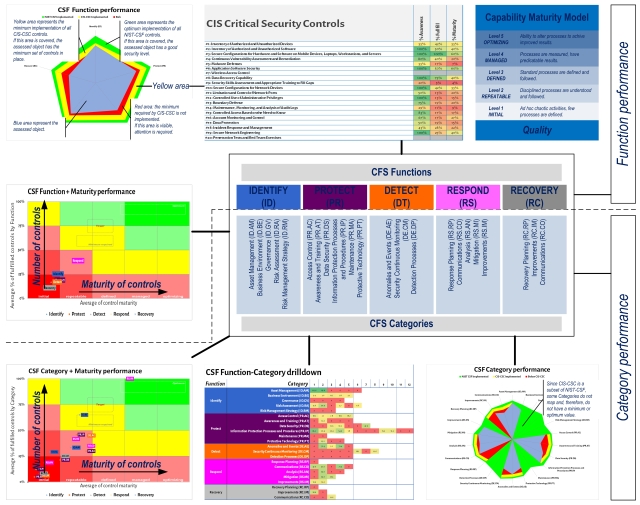
Once a lot of information are collected, it is time to analyze them and prioritize problems. How to assign a G-Y-R code to each inspected control and measure the result? The NIST-CSF has a lot of controls, and not every organization has the resource to manage them.
We decided to set the absolute minimum at the CIS Critical Security Controls. The CIS-CSC are a recommended set of actions for cyber defense that provide specific and actionable ways to stop today’s most pervasive and dangerous attacks.
Mapping the CIS-CSC to NIST-CSF, makes possible to separate the performance of each control in the NIST-CSF in different areas:
Defined the metric, with some code and database relations, it is possible to get values/trends/performances from the data, and support our judgment with a more solid and understandable reason.
Here some examples of figures extracted:
A security assessment is a long sequence of actions that may take a lot of resource to produce results. Assessing a company is a complex and delicate problem, involving not only technical but also human aspects. We developed the rapid security assessment to produce fast and reliable results to help organizations to efficiently drive investments and efforts and to make the right tactic and strategic decision to improve they security posture.
Our experts will get in contact with you!

Rocco Gagliardi

Rocco Gagliardi

Rocco Gagliardi

Rocco Gagliardi
Our experts will get in contact with you!