Transition to OpenSearch
Rocco Gagliardi

somewhere there. For me, configure an interface with plumb is a tiny moment of joy.
Sometime, however, I ask myself what is going on on my Mac. Specifically, I want (quick) answers to the following questions:
man or ddgo Internet?There are different possibilities, but since I fire frequently new terminals, I prefer to have the results as welcome screen. So I copied/pasted/modified/wrote some pieces of code and putted in my .bash_profile. Refer to my github repository for the code.
The small checks to execute at Bash start – or ad-hoc, using alias – are:
/etc/hosts to block connections to blacklisted hostsRefer to the scripts comments for an explanation of the control.
This give me a quick overview of my system status; even if not exhaustive, covers many important settings.
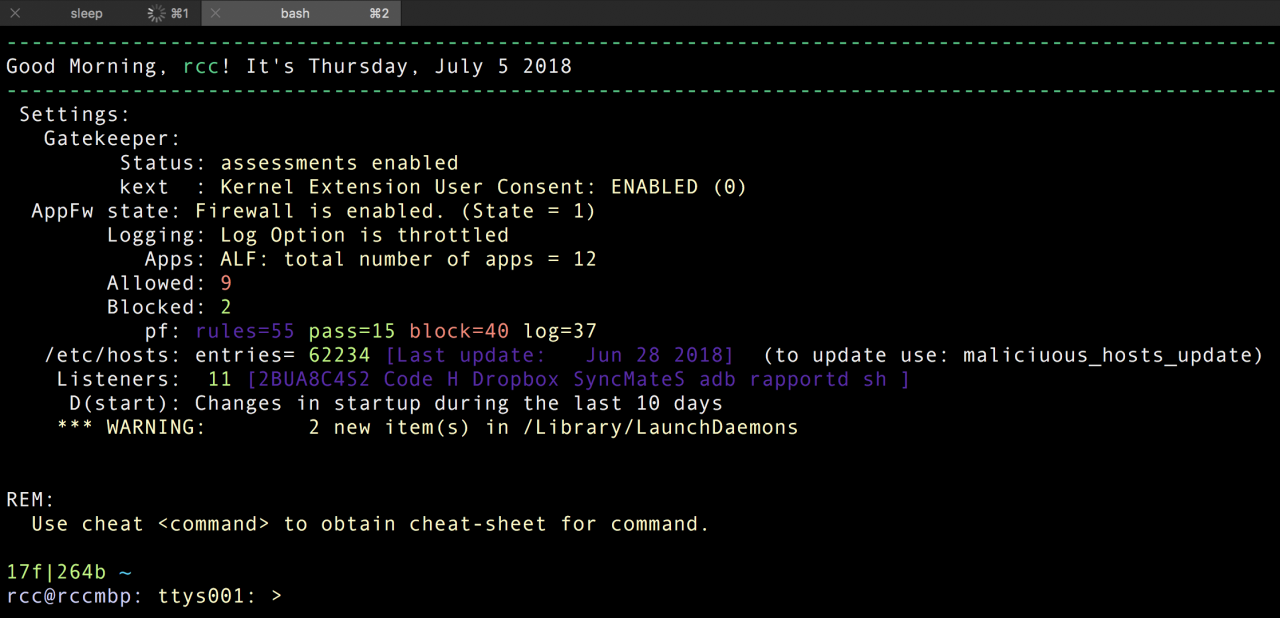
ALF is a very easy to use firewall and quickly gives an idea of our exposure, but if you want more control over your traffic, you need to use another tool. I used Little Snitch, then macOS (Lion) introduced pf and I looked at tools to configure them, like IceFloor and Murus.
pf provides a granular control over network traffic but it’s a programming language and requires some time. If you want to use pf, consider to start without GUI tools; once you manage the pf config, switch to the GUI. Consider also that we are dealing with a client (laptop) not with a server, so the policy will become complex if you want a user-friendly machine.
I use the pf as additional/ad-hoc firewall, for specific use cases:
Here I don’t want explain how pf works, just show some results: As you can see in the middle terminal, I can surf the log to find incoming/outgoing, pass/blocked connections just executing the pf.logsnoop or pf.lognav alias. pf.lognav requires the lnav installed.
In the example, I used hping to generate a packet with flags FSR set. Note that, even if rule 38 matches (FS), the drop comes from rule 40 (FR): pf is last match, if you don’t use special options. Using pf requires you to go in OpenBSD user mode. Note also the outgoing traffic.
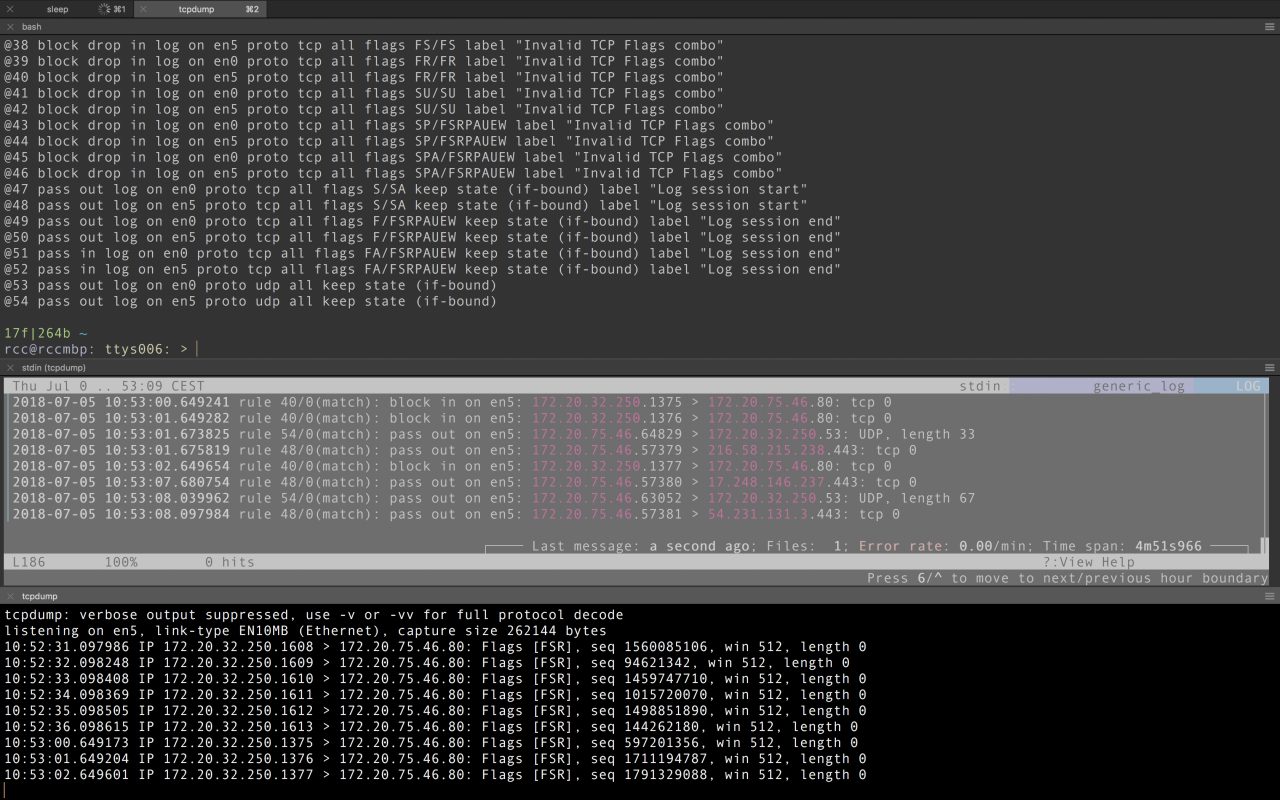
If you look at the pf.lognav or pf.logsnoop aliases, you will notice that both aliases do not tail a logfile, but snoop pseudo-devices that make all packets visible logged by pf.
Finally, this is a little but very useful tool: cheat. Basically, displays cheat-sheets – that you can create or update. Just put your my-cheat-file in the directory and read it with cheat my-cheat-file – Very useful if you can’t ddgo.
Do you want to stay secure with you macOS? Follow the simple steps documented by Apple.
Do you want to go deeper in the system or in the network? Use the command line tools, there are a lot already pre-installed.
If you want to play with pf, be careful: Do not shutdown Gatekeeper, things can quickly go wrong, very quickly, very wrong.
Our experts will get in contact with you!

Rocco Gagliardi

Rocco Gagliardi

Rocco Gagliardi

Rocco Gagliardi
Our experts will get in contact with you!