Security Testing
Tomaso Vasella

This is how you secure your Microsoft Teams
Microsoft Teams is a solution that combines video conferencing, online meetings, notes and file sharing. Teams is integrated in Microsoft 365 (M365, formerly known as Office 365) and is part of most M365 subscriptions. Teams is one of the most popular applications for virtual meetings, mainly due to the widespread use of M365.
The following sections provide an overview of the most important terms and the possibilities for users and administrators to securely use Teams.
The meaning of the terms used in connection with teams is unfortunately not always easy to understand intuitively and is sometimes not used consistently in the Microsoft documentation. A summary of the most important terms is therefore helpful.
For users who organize or participate in Teams meetings, mainly the participant roles are interesting:
A distinction is made between the following participant types:
Many security relevant settings for teams are set centrally by the Teams administrator or the M365 administrator. As a user, you can still take a few precautions to make it difficult for unwanted people to attend the meeting.
The creator of a meeting (organizer) can control who can attend Teams meetings directly and who has to wait for admission in the lobby first. After a meeting has been created, the organizer can make settings for the lobby using the meeting options:
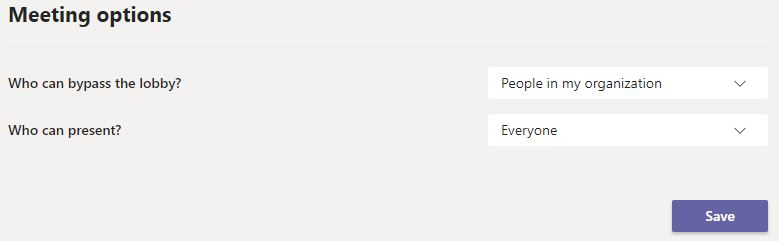
If a participant is in the lobby, another participant with the necessary rights must allow the participant to join the meeting. The table below summarizes what the available lobby settings do:
| Setting | User types joining the meeting directly | User types going to the lobby |
|---|---|---|
| People in my organization |
|
|
| People in my organization and trusted organizations |
|
|
| Everyone |
|
In addition, it can be defined who in the meeting is allowed to act as presenter. The possibilities of presenters and attendees are the following:
| Actions | Presenters | Attendees |
|---|---|---|
| Speak and share their video | Y | Y |
| Participate in meeting chat | Y | Y |
| Change settings in meeting options | Y | N |
| Mute other participants | Y | N |
| Remove other participants | Y | N |
| Share content | Y | N |
| Admit other participants from the lobby | Y | N |
| Make other participants presenters or attendees | Y | N |
| Start or stop recording | Y | N |
| Take control when another participant shares a PowerPoint | Y | N |
Because Teams is closely linked to SharePoint, OneNote, Exchange and other services, the general security of M365 is of particular importance. For example, it is recommended to activate two-factor authentication for all users and to limit the rights of the users to the minimum required. In addition, Teams offers various specific settings for administrators through the Teams Admin Center and in part also in the Teams app. An overview of the security features built into Teams can be found at Microsoft. The most important central settings for Teams administrators are described in the following sections.
For each defined team, settings for the permissions and for the channels can be made, which should be restricted as much as possible.
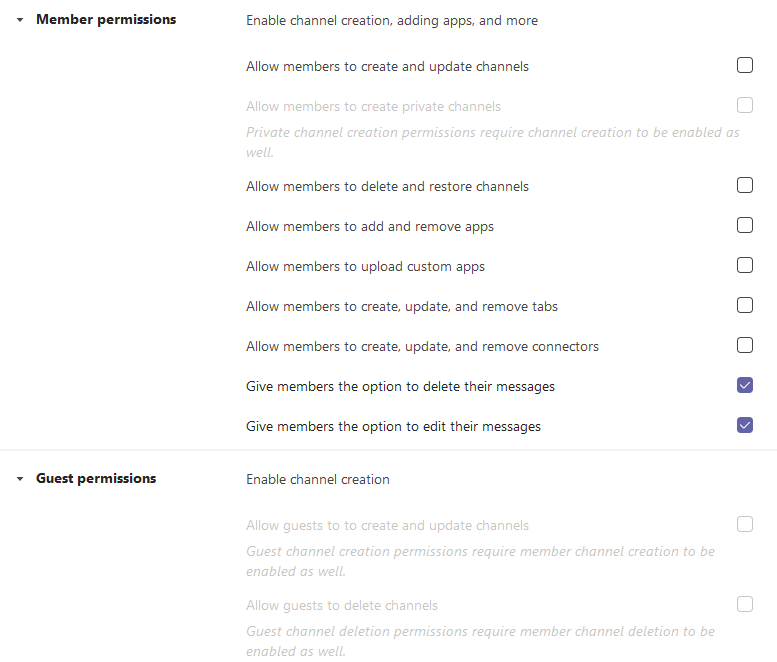
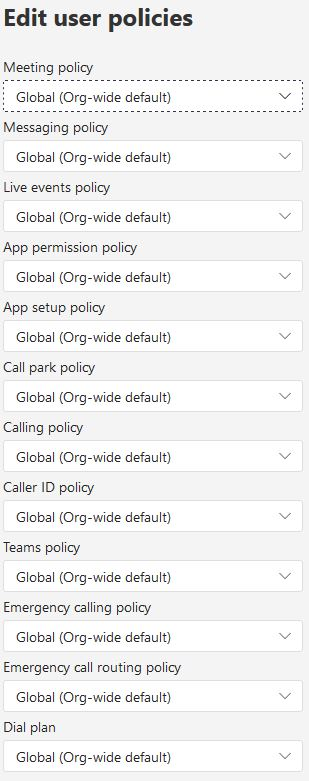
Using Teams policies, various aspects can be centrally defined for meeting users. As with all settings, it is advisable to deactivate features that are not required.
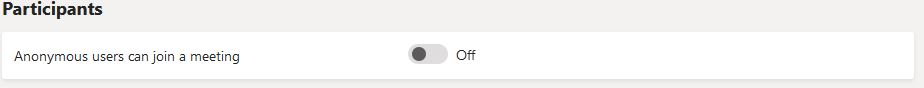
The meeting settings allow to define whether anonymous participants are allowed to Teams meetings. If possible, this should be deactivated.
Apps can be used within Teams. The app permission policies control which apps are available to Teams users in the organization. Here, too, it is advisable to allow as little as necessary.
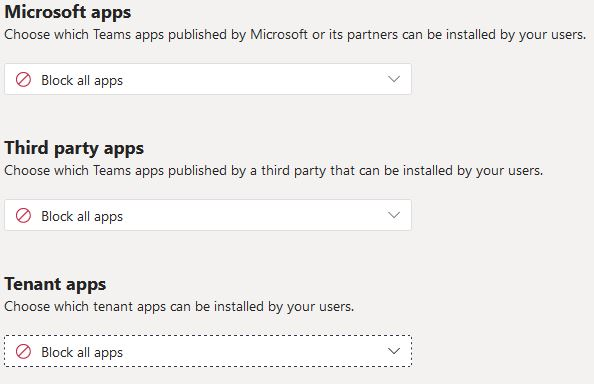
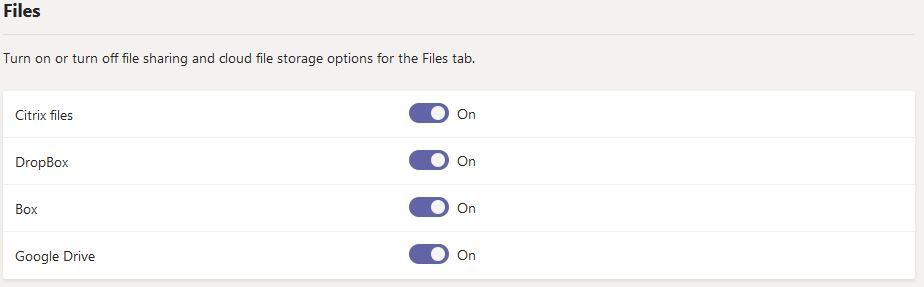
An administrator can define in the Teams settings which third-party cloud storage services are available to Teams users. These options are made available to the user directly inside the Teams app. It is recommended to disable these options.
Securing teams may seem easy at first, but it can become complex at least for the team administrators, since various settings of M365 and teams overlap and the terms used by Microsoft are not always intuitively understandable. It is therefore essential for administrators to take a close look at the security aspects of M365 and as a consequence also at those of the Azure Active Directory. For users, once again this saying applies: Trust is good, control is better – especially with regard to unexpected meeting participants and the content they share.
Our experts will get in contact with you!

Tomaso Vasella

Tomaso Vasella

Tomaso Vasella

Tomaso Vasella
Our experts will get in contact with you!