Dynamic Analysis of Android Apps
Ralph Meier

Measures and tips for a Secure Home Network
This article is intended to show some tips on home network security and to support you when reinstalling your WLAN.
Most home routers only create a WLAN with the device name and use a predefined password in the installation process. This is either a standard password or an individual password printed on the router. For users who are not very concerned with the topic of network settings, this results in a single network to which all computers and smartphones are logically connected. But that’s not the end of the story: You might have a smart speaker, a smart TV, possibly a hub for smart home devices, and at some point a new kitchen appliance will come into the house that also has an internet connection. When guests visit, they sometimes also need internet access, so their devices are also added to the network.
If all devices are integrated into a single network, this can lead to various problems. On the one hand, one can quickly lose the overview of all devices connected to the network. On the other hand, all network participants see shared files if public shares or network drives exist and are configured incorrectly or not protected. Devices with different and partly unknown software versions enter the network and thus bring unknown security vulnerabilities with them.
All devices can communicate with each other because they are on the same network, making it easier for attackers to jump from an infected device to other devices, such as the personal computer. By mixing all devices, i.e. devices with private files and Internet of Things (IoT) devices, the creation of firewall rules becomes more difficult. IoT devices, for example, often need to be accessible from the internet in order to use the full range of functions.
The following are some basic home network security improvements.
When commissioning a new router, the default settings should be adjusted immediately. This means changing the password for the WLAN to a random sequence of upper and lower case letters, numbers and special characters with a minimum length of 12 characters. Since this password only has to be entered once per device, it can be longer.
The name of the network, the so-called SSID (Service Set Identifier), should not contain the model or manufacturer of the router used. It is also advisable to choose a name that is not related to your own household.
Next, the encryption method used for the wireless network should be set to the highest possible option, which at the time of this writing is WPA3.
Now check whether new updates are available for the router and activate the option to install future updates automatically.
The best solution would be to put these devices in their own virtual LAN (VLAN) and use WPA2 there. If the router does not support WPA3 or WPA2, it should be replaced with a newer model as soon as possible.
Many routers today have the option to set up a separate guest network. This is an independent subnet that has its own SSID and password. If you want to provide internet access to your guests, you should configure it this way.
This solves several of the problems listed above in one fell swoop. Some routers also offer a function that generates a QR code to enable easy connection to the guest network.
After the division between home network and guest network, the remaining configuration options of the router should be gone through and checked. Some routers offer various functions such as NAS functionality or an FTP server. The rule here is that if the functionality is not currently being used, it should be deactivated. This also applies to accessing the router’s administrator interface from the Internet. If this option is active, we recommend deactivating it.
By applying network segmentation, a network is divided into several subnets or VLANs. This is something for advanced users and often not feasible with standard routers.
The aim here is to divide a large flat network into small subnets with “similar” devices and thus reduce the attack surface.
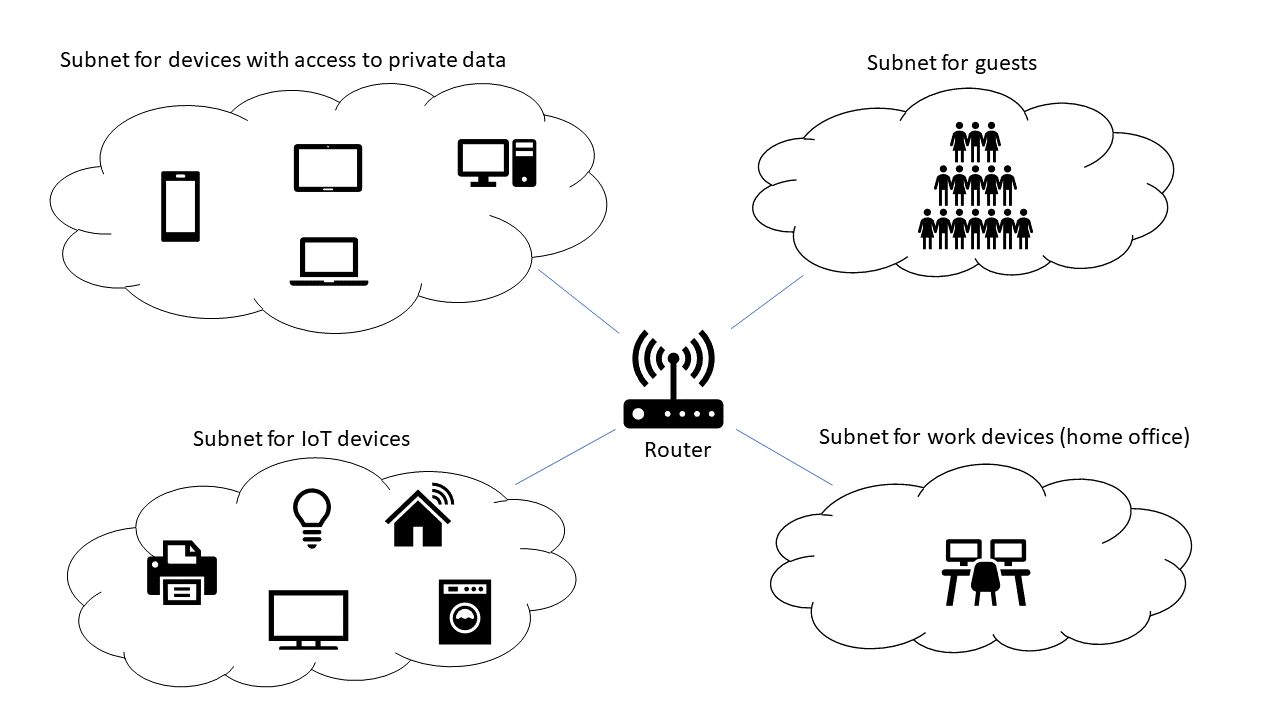
By similar devices, it is meant that all devices with private data or with access to private data, such as computers, tablets and smartphones, for example, enter a first subnet. Printers, televisions, IoT devices and their hubs go into another subnet. Then there is a subnet for guests and possibly another for working in the home office.
With such a subdivision, firewall rules can be introduced per network segment and thus also configured more efficiently and precisely. Connections from the first subnet can be allowed into the subnet with IoT devices and printers, while a connection request in the opposite direction can be blocked.
The introduction of different subnets also makes lateral movement in the event of a cyber attack more difficult or, depending on the configuration, impossible.
Before purchasing Internet-enabled products that are to be integrated into the home network or devices for network expansion, the following aspects should be considered:
For a secure home network, changing the default settings, using up-to-date software on routers and end devices and using secure passwords are essential. Good device management, a division into home network and guest network or even a more specific network segmentation provide additional security. It is also important to inform oneself intensively before buying in order to choose devices that have the desired functions and are compatible with each other. To avoid unintentional known vulnerabilities when re-integrating devices, a vulnerability database should be consulted in advance.
Our experts will get in contact with you!

Ralph Meier

Ralph Meier

Ralph Meier

Ralph Meier
Our experts will get in contact with you!