Enhancing Data Understanding
Rocco Gagliardi
How to stay one step ahead of attackers
Cyber Threat Intelligence (CTI) traditionally deals with compromise. It prefers to create databases of malicious IP addresses, corrupt file names and hashes. This is done primarily from the point of view of malware.
However, modern CTI can go one step further. By observing and evaluating actors, their activities and their relations to each other, it is possible to create profiles that in turn allow predictions of high accuracy.
Actors have a specific interest. Modern cybercriminals tend to implement the highest possible economic turnover as quickly as possible. And state actors are oriented towards their political goals. The attack scenario is different depending on the target. And accordingly, the means to be employed for this purpose vary.
Thus, the first step is to identify which possible scenarios are realistic in order to be able to recognize the interest that goes with them. For this purpose different sources can be included. There are different areas to be considered in both the Clearnet and the Darknet:
Attackers are interested in the following mechanisms on different levels:
| Mechanism | Examples |
|---|---|
| Technologies | TCP/IP, IPv6, Bluetooth, Blockchain |
| Product Categories | Operating system, smart phones, SCADA components |
| Products | Microsoft Windows, Apple iOS, Google Chrome |
| Vulnerabilities | CVE-2019-19781, CVE-2018-4878, CVE-2015-1641 |
| Group of Customers | Finance, insurance, health care |
| Customers | Company A, Company B, Company C |
Accordingly, the respective sources must be searched for activities that can be assigned to one of these categories. For this purpose, automated parsing can be used. For simplicity, this can be done on simple keywords. A simple example with highly efficient string matching:
function cti_identify_keywords($str){
//list of topcis+keywords
$triggers['tcpip'] = [ 'tcp/ip', 'ipv4', 'ipv6', 'tcp', 'udp', 'icmp' ];
$triggers['bluetooth'] = [ 'bluetooth', 'ble', '802.15.1', 'sdp', 'bnep' ];
//find matches
foreach($triggers as $keywords_k=>$keywords_v){
foreach($keywords_v as $keyword){
if(stripos($str, $keyword) !== FALSE){
$matches[$keywords_k][] = $keyword;
}
}
}
return $matches;
}As soon as one of these keywords occurs, the corresponding category, in this case for example the technology TCP/IP, can be identified as such. An extended implementation with regular expressions for the recognition of word boundaries is recommended to minimize false positives and thus increase quality.
We go one step further and use Natural Language Processing (NLP), which not only identifies individual terms but also allows us to find out their context. So we have to distinguish between the background of the following two statements, which can occur in a tweet or forum post:
(User A) How may I fix issue CVE-2019-19781?
(User B) Does anybody sell an exploit for CVE-2019-19781?
Although both statements are interested in the CVE-2019-19781 vulnerability in Citrix, the motivation for this is probably completely different. In the first example of user A, we are interested in a countermeasure (defense) and in the second example of user B, we are interested in exploiting (offense).
This distinction seems obvious and clear at first glance. However, it is not possible to deduce the true background immediately and without any doubt. User A may need additional information about countermeasures to optimize or successfully use an exploit. He would therefore be more likely to be assigned to the offensive area. And User B could be a professional penetration tester who needs access to an exploit in order to be able to perform a verification within the scope of a legitimate customer project and contribute to securing the vulnerability. He would thus be assigned to the more defensive area as far as possible.
Here, the analysis of the further course of a possible dialog/thread or the historical consideration of statements can be useful. It is not unusual for actors to have a more or less clear tendency to either offensive or defensive backgrounds. For this reason, we determine both the intentions of individual statements and the characterization of the actors themselves.
In doing so, actors can be attributed a certain degree of weight in terms of their quality. If, for example, a well-known figure from the iOS jailbreak scene discusses a weakness of Apple platforms, this should be given much more weight than if an unfamiliar daily newspaper reports on the topic of iOS. This allows a generic noise to be distinguished from concrete signals. Again, historical data must be taken into account and consistently assessed. Thus the quality of the database and thus the signal recognition can be consistently increased.
The recognition of intentions is important. A step further can be taken by assigning the activities to concrete actors or groups and their backgrounds. On the one hand, this can be done by means of corresponding user profiles. For example, the corresponding professional associations are published on LinkedIn profiles. Some users – for example in their Twitter bio – also note their origin. This makes it relatively easy to make a geographical assignment. In other cases, for example in certain forums or chat systems, the IP address of a user can be determined.
This immediately raises the question of whether such a geographical assignment of their concrete location or their geopolitical affiliation should take place. Or asked in another way:
A user born in Japan currently lives in Sweden but works for a US-American company. To which country is this actor now assigned?
We tend to document all data points (Japan, Sweden, USA). However, the geopolitical background should be in the foreground.
In a further step, the geopolitical relationships can be taken into account for an extended evaluation. For this purpose, a characterization of the individual groupings, in most cases states or regions, has to take place. This characterization can include, for example
It is becoming apparent, for example, that in a specific country the economic sector finance may be disproportionately represented and that it also accounts for a considerable portion of GDP. The system components used therein can be divided into two categories:
On the basis of this distinction, the typically used products can now be derived. Even with generic components, these are dependent on the respective industry, whereby a large differentiation by region/country can also be observed.
The characterization can now be put in relation to each other. The different actors maintain corresponding relationships with each other. With the example of states the following circumstances can now be determined:
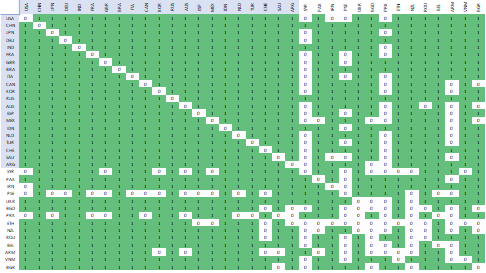
These peculiarities provide information about dependencies and power relations. A simple demonstration of such a view is provided by the relationship matrix in relation to messages. This makes it immediately clear which countries are in diplomatic disagreement with one another. As a rule, this is a clear sign of tensions that may sooner or later justify an attack in virtual space.
Cybersecurity defense has traditionally been forced to react. This leads to the fact that it is necessary to react under pressure to act. CTI is intended to turn this paradigm on its head, making active action possible thanks to anticipation.
In order to be able to do this, evaluations must be aimed for that can record current events and predict future developments. This evaluation can be centrist in various ways:
Let us take a Microsoft Patch Tuesday as an example. Usually about 100 new vulnerabilities are published and addressed at the same time as an official patch. Now it is interesting to see which vulnerability can attract the most interest. Usually two or three of these vulnerabilities are of particular interest. The gradient to the next vulnerability with increased interest is usually very large.
Typically, these vulnerabilities were vulnerabilities in popular and exposed products. In recent years, these were mainly Windows as operating system and Outlook as extended mail client. In the context of the Patchday on October 16, 2020 it was the following two publications that recorded large swings within 24 hours:
Especially with Microsoft vulnerabilities, the tightrope walk between the identification of offensive and defensive interests is rather difficult. A large part of the activities can be assigned to the latter, which is due to the high market penetration and the criticality of the corresponding infrastructures.
Typically, Microsoft shows that the major players are particularly interested in the offensive area. In this example too, it could be assigned that US actors are interested in the Outlook vulnerability and Chinese actors in the Windows vulnerability (see figure).
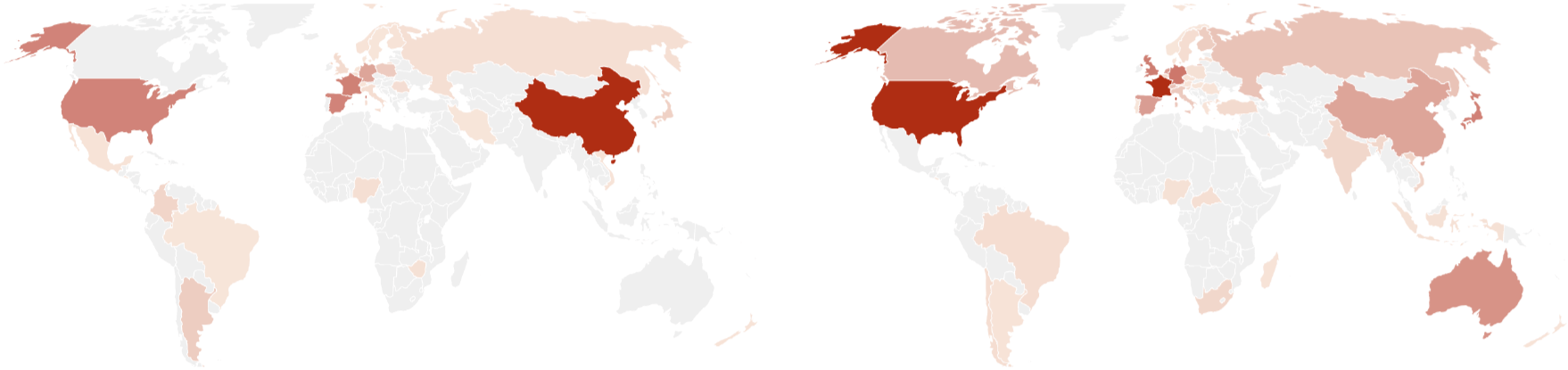
This is historically interesting because Chinese players have developed a rather unpopular penchant for vulnerabilities that require user interaction in recent months. This shows that they are willing to run classic phishing campaigns, which are rather avoided by the other big players due to their high complexity and error-proneness. It is therefore all the more surprising that the USA in particular is focusing on the weakness in Outlook, which brings with it precisely this unwelcome prerequisite.
If one looks at the weaknesses, the potential of the players and the historical findings, then various predictions for the future can be derived:
The information gathered so far can now be combined to calculate the real probability of an attack. The geopolitical, economic and technical aspects are taken into account. Normally target Y is understood as itself, but can of course be exchanged with any other target:
Now, combining this data results in the concrete probability of attack. If one of the questions can be answered with a clear No, the attack probability decreases to zero. And in the case of technical vulnerability, the impossibility of success is simultaneously declared.
It is important to remember that this linkage of data must be recalculated for each actor, each vulnerability and each change in the relationship between actors. Such an analysis is always merely a current inventory that loses its validity as time progresses.
Cyber Threat Intelligence (CTI) provides a proven means of detecting attacks in advance and thus reacting to them. This anticipation removes time pressure and creates an advantage.
The first step is to identify the interest in vulnerabilities in order to be able to assign them to the individual actors in a second step. By determining the relationships between actors, the corresponding probability of attack can then be calculated.
This form of CTI is new and so far unique. However, it is foreseeable that in the long term this tool can become a central tool of modern cybersecurity. Only in this way can one be one step ahead. And this is important in today’s world in order to survive in the digital space.
Our experts will get in contact with you!

Rocco Gagliardi

Marc Ruef

Rocco Gagliardi

Marc Ruef
Our experts will get in contact with you!